Wireless Device Provisioning Overview
The following sections provide information about how to provision various Cisco wireless devices.
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
The following sections provide information about how to provision various Cisco wireless devices.
Controllers and access points are designed for use in many countries with varying regulatory requirements. The radios within the access points are assigned to a specific regulatory domain at the factory (such as -E for Europe), but the country code enables you to specify a particular country of operation within that regulatory domain (such as FR for France or ES for Spain). Configuring a country code ensures that each radio’s broadcast frequency bands, interfaces, channels, and transmit power levels are compliant with country-specific regulations.
Cisco DNA Center provisions controllers with country codes according to the site they are assigned. In the case of controllers, they can be assigned to more than one site. So, they can be assigned more than one country code. During provisioning, Cisco DNA Center assigns sites to the controller along with the sites’ country codes. For example, a controller that manages both India and US sites is assigned the IN and US country codes.
When access points are provisioned, they are assigned to a floor. If the access point is a ROW AP, Cisco DNA Center gets the country code for the site and assigns it to the AP. Any additional APs on the same floor are assigned the same country code.
The country code information is displayed on the Device 360 window for controllers and access points.
For a complete list of country codes supported per product, see https://www.cisco.com/c/dam/assets/prod/wireless/wireless-compliance-tool/index.html.
Make sure that you have defined the following global network settings before provisioning a Cisco Wireless Controller:
Network servers, such as AAA, DHCP, and DNS.
For more information, see Configure Global Network Servers.
Device credentials, such as CLI, SNMP, HTTP, and HTTPS.
For more information, see Configure Global CLI Credentials, Configure Global SNMPv2c Credentials, Configure Global SNMPv3 Credentials, and Configure Global HTTPS Credentials.
IP address pools.
For more information, see Configure IP Address Pools.
Wireless settings, such as SSIDs, wireless interfaces, and wireless radio frequency profiles.
For more information, see Configure Global Wireless Settings.
Make sure that you have the Cisco Wireless Controller in your inventory. If not, use the Discovery feature to discover the controller.
Make sure that the Cisco Wireless Controller is added to a site. For more information, see Add a Device to a Site.
You cannot reuse any pre-existing VLANs on devices. Provisioning fails if Cisco DNA Center pushes the same VLAN that already exists on the device.
You cannot make any configuration changes to the wireless controller that is being managed by the Cisco DNA Center manually. You must perform all configurations from the Cisco DNA Center GUI.
Ensure the prerequisite is met. For more information, see Prerequisites for Provisioning a Cisco AireOS Controller.
|
Step 1 |
Click the menu icon ( The window is displayed with the discovered devices listed. |
||
|
Step 2 |
Expand the Global site in the left pane, and select the site, building, or floor that you are interested in. The available devices in the selected site is displayed in the Inventory window. |
||
|
Step 3 |
From the DEVICE TYPE list, click the WLCs tab, and from the Reachability list, click the Reachable tab to get the list of wireless controllers that are discovered and reachable. |
||
|
Step 4 |
Check the check box next to the device name that you want to provision. |
||
|
Step 5 |
From the Actions drop-down list, choose . The Assign Site window is displayed. |
||
|
Step 6 |
Click Choose a site to assign a site for the wireless controller. |
||
|
Step 7 |
In the Add Sites window, check the check box next to the site name to associate the wireless controller, and click Save. |
||
|
Step 8 |
Click Apply. |
||
|
Step 9 |
Click Next. The Configuration window is displayed. |
||
|
Step 10 |
Select a role for the wireless controller: Active Main WLC or Guest Anchor WLC. |
||
|
Step 11 |
Click Select Primary Managed AP Locations to select the managed AP location for the wireless controller. |
||
|
Step 12 |
In the Managed AP Location window, check the check box next to the site name. You can either select a parent site or the individual sites. If you select a parent site, the children under that parent site automatically gets selected.
|
||
|
Step 13 |
Click Save. |
||
|
Step 14 |
Under Interface and VLAN Configuration, click + Add and configure the interface and VLAN details for an active main wireless controller. Interface and VLAN configuration is applicable for nonfabric wireless controller provisioning only. The Configure Interface and VLAN window is displayed. |
||
|
Step 15 |
From the Interface Name drop-down list, choose the interface name. |
||
|
Step 16 |
In the VLAN ID field, enter a value for the VLAN. |
||
|
Step 17 |
In the Interface IP Address field, enter a value for the interface IP address. |
||
|
Step 18 |
In the Interface Net Mask (in bits) field, enter the subnet mask for the interface. |
||
|
Step 19 |
In the Gateway IP Address field, enter the gateway IP address. |
||
|
Step 20 |
From the LAG/Port Number drop-down list, choose the link aggregation or the port number. |
||
|
Step 21 |
Click OK. |
||
|
Step 22 |
(Optional) For a guest anchor wireless controller, change the VLAN ID configuration by changing the VLAN ID under Assign Guest SSIDs to DMZ site. |
||
|
Step 23 |
Under Mobility Group, click Configure to configure the wireless controller as the mobility peer. |
||
|
Step 24 |
In the Configure Mobility Group slide-in pane, from the Mobility Group Name drop-down list, you can either add a new mobility group by clicking +, or choose a mobility group from the existing mobility groups. Information about the existing mobility peers is loaded from the intent available in the Cisco DNA Center.
|
||
|
Step 25 |
In the RF Group Name text box, enter a name for the RF group. |
||
|
Step 26 |
Under Mobility Peers, click Add to configure the wireless controller as a mobility peer. |
||
|
Step 27 |
In the Add Mobility Peer slide-in pane, configure the following: |
||
|
Step 28 |
Click Configure Mobility. |
||
|
Step 29 |
To reset the mobility group name and the RF group name, you can do one of the following:
This automatically sets the RF Group Name to default and removes all peers. After provisioning, the mobility on the device is set and the device is removed from all other peers. |
||
|
Step 30 |
Click Next. The Model Configuration window is displayed. |
||
|
Step 31 |
In the Devices pane, you can either search for a model config design by entering its name in the Find field, or expand the device and select a model config design. The selected model config design appears in the right pane. |
||
|
Step 32 |
Check the check box next to the Design Name that you want to provision, and click Configure to edit the model config design. You cannot edit all the configurations at this step. |
||
|
Step 33 |
After making the necessary changes, click Apply. |
||
|
Step 34 |
Click Next. The Advanced Configuration window is displayed, which is where you can enter the values for predefined template variables. |
||
|
Step 35 |
Search for the device or the template in the Devices panel. |
||
|
Step 36 |
Enter a value for the predefined template variable in the wlanid field. |
||
|
Step 37 |
Click Next. |
||
|
Step 38 |
Click Deploy to provision the controller. |
||
|
Step 39 |
In the Provision Devices window, do the following to preview the CLI configuration: |
||
|
Step 40 |
Provision the secondary controller. |
||
|
Step 41 |
The Status column in the Device Inventory window shows SUCCESS after a successful deployment. After provisioning, if you want to make any changes, click Design, change the site profile, and provision the wireless controller again. |
||
|
Step 42 |
After the devices are deployed successfully, the Provision Status changes from Configuring to Success. |
||
|
Step 43 |
In the Device Inventory window, click See Details in the Provision Status column to get more information about the network intent or to view a list of actions that you need to take. |
||
|
Step 44 |
Click See Details under Device Provisioning. |
||
|
Step 45 |
Click View Details under Deployment of network intent, and click the device name. |
||
|
Step 46 |
Expand the Configuration Summary area to view the operation details, feature name, and the management capability. The configuration summary also displays any errors that occurred while provisioning the device. |
||
|
Step 47 |
Expand the Provision Summary area to view details of the exact configuration that is sent to the device. |
Cisco Wireless Controller High Availability (HA) can be configured through Cisco DNA Center. Currently, both the formation and breaking of wireless controller HA is supported; switchover options are not supported.
The Discovery and Inventory features of wireless controller 1 and wireless controller 2 must be successful. The devices must be in the Managed state.
The service ports and the management ports of wireless controller 1 and wireless controller 2 must be configured.
The redundancy ports of wireless controller 1 and wireless controller 2 must be physically connected.
The management address of wireless controller 1 and wireless controller 2 must be in the same subnet. The redundancy management address of wireless controller 1 and wireless controller 2 must also be in the same subnet.
Manually configure the following boot variables on the wireless controller:
config t
boot system bootflash::<device_iosxe_image_filename>
config-register 0x2102
show boot. (IOSXE cli)
BOOT variable = bootflash:<device_iosxe_image_filename>,12;
Configuration register is 0x2102
|
Step 1 |
Click the menu icon ( The window is displayed with the discovered devices listed. |
||
|
Step 2 |
Check the check box next to the controller name that you want to configure as the primary controller. |
||
|
Step 3 |
From the Actions drop-down list, choose . The High Availability slide-in pane is displayed. |
||
|
Step 4 |
Enter the Redundancy Management IP and the Peer Redundancy Management IP address in the respective text boxes. The IP addresses used for redundancy management IP and peer redundancy management IP should be configured in the same subnet as the management interface of the Cisco Wireless Controller. Ensure that these IP addresses are unused IP addresses within that subnet range. |
||
|
Step 5 |
From the Select Secondary WLC drop-down list, choose the secondary controller.
|
||
|
Step 6 |
Click Configure HA. |
||
|
Step 7 |
To verify the HA configuration, on the window, click the device that you configured as a HA device. |
||
|
Step 8 |
Click the Wireless Info tab. The Redundancy Summary displays the Sync Status as In Progress. When Cisco DNA Center finds that HA pairing succeeded, the Sync Status changes to Complete. This is triggered by the inventory poller or manual resynchronization. By now, the secondary wireless controller (wireless controller 2) is deleted from Cisco DNA Center. This flow indicates a successful HA configuration on the wireless controller. |
Cisco wireless controller 1 and wireless controller 2 are configured with redundancy management, redundancy units, and SSO. The wireless controllers reboot in order to negotiate their role as active or standby. Configuration is synced from active to standby.
On the Show Redundancy Summary window, you can see these configurations:
SSO is enabled.
The wireless controller is active.
The wireless controller is in hot standby.
The management port of the active wireless controller is shared by both the controllers and will be pointing to the active controller. The user interface, Telnet, and SSH on the standby wireless controller will not work. You can use the console and service port interface to control the standby wireless controller.
Cisco DNA Center sends the following commands to configure Cisco Wireless Controller HA.
Cisco DNA Center sends the following commands to wireless controller 1:
config interface address redundancy-management 198.51.100.xx peer-redundancy-management 198.51.100.yy
config redundancy unit primary
config redundancy mode sso
Cisco DNA Center sends the following commands to wireless controller 2:
config interface address redundancy-management 198.51.100.yy peer-redundancy-management 198.51.100.xx
config redundancy unit secondary
config port adminmode all enable
config redundancy mode sso
Enter the following commands to verify the HA configuration from the wireless controller:
To check HA-related details: config redundancy mode sso
To check the configured interfaces: show redundancy summary
Ensure that the HA device in the existing deployment is configured outside of Cisco DNA Center.
|
Step 1 |
Click the menu icon ( The Inventory window is displayed with the discovered devices listed. |
|
Step 2 |
Check the check box next to the name of the wireless controller that has the HA feature that you want to disable. |
|
Step 3 |
From the Actions drop-down list, choose . The High Availability slide-in pane is displayed. High Availability slide-in pane shows the REDUNDANCY SUMMARY of selected wireless controller configured from outside Cisco DNA Center. |
|
Step 4 |
In the Warning window, click OK. A success message appears at the bottom of the screen indicating that the HA feature has been successfully disabled for the selected wireless controller. |
Make sure that you have Cisco APs in your inventory. If not, use the Discovery feature to discover APs. For more information, see Discover Your Network.
|
Step 1 |
Click the menu icon ( The Inventory window displays the device information that is gathered during the discovery process.
|
||
|
Step 2 |
Check the check box next to the AP that you want to provision. |
||
|
Step 3 |
From the Actions drop-down list, choose . |
||
|
Step 4 |
In the Assign Site step, configure the following parameters:
|
||
|
Step 5 |
In the Configuration step, configure the following parameters: |
||
|
Step 6 |
In the Summary step, review the device details, and click Deploy to provision the AP. The Provision Device slide-in pane appears. |
||
|
Step 7 |
In the Provision Device slide-in pane, do the following:
|
||
|
Step 8 |
You are prompted with a message that the creation or modification of an AP group is in progress and then a message that APs will reboot after provisioning. Click OK. The Last Sync Status column in the Inventory window shows SUCCESS for a successful deployment. |
You can enable Internet Control Message Protocol (ICMP) ping on APs that are in FlexConnect mode and in an unreachable state. Cisco DNA Center uses the ICMP to ping FlexConnect APs that are in unreachable state every 5 minutes to enhance reachability and then updates the reachability status in the Inventory window.
|
Step 1 |
Click the menu icon ( |
|
Step 2 |
Check the Enable ICMP ping for unreachable access points in FlexConnect mode check box to enable the ICMP ping. |
|
Step 3 |
Click Save. A success message is displayed: ICMP Ping status updated successfully. Cisco DNA Center starts pinging FlexConnect APs that are disassociated from Cisco Wireless Controllers but are reachable. You can view the reachability status in the Inventory window. |
|
Step 4 |
To view the reachability status, choose . |
|
Step 5 |
The Reachability column shows Ping Reachable when the device is reachable by the ICMP ping. |
The Cisco Mobility Express wireless network solution comprises at least one 802.11ac Wave 2 Cisco Aironet Series access point with an in-built, software-based wireless controller managing other APs in the network. The AP acting as the wireless controller is referred to as the primary AP. The other APs in the Cisco Mobility Express network, which are managed by this primary AP, are referred to as subordinate APs.
Design your network hierarchy with sites, buildings, floors, and so on. For more information, see Create, Edit and Delete a Site, Add, Edit, and Delete a Building, and Add, Edit, and Delete a Floor.
Define the device credentials, such as CLI, SNMP, HTTP, and HTTPS at the global level. The credentials that are defined at the global level are inherited by the sites. For more information, see Configure Global CLI Credentials, Configure Global SNMPv2c Credentials, and Configure Global SNMPv3 Credentials.
Create WLANs, interfaces, and RF profiles.
Configure the DHCP server with Option #43 or Option #60. This is the IP address of the Cisco DNA Center Plug and Play server. Using this IP address, the APs contact the PnP server and download the configuration.
Make sure that you have Mobility Express APs in the inventory. If not, discover them using the Discovery feature. For more information, see Discover Your Network Using CDP, Discover Your Network Using an IP Address Range, and About Inventory.
The APs should be in the factory reset state without any Cisco Wireless Controller configurations.
|
Step 1 |
The Cisco Mobility Express contacts the DHCP server and connects to the Cisco DNA Center Plug and Play server. |
||
|
Step 2 |
The DHCP server allocates the IP address with Option #43, which is the IP address of the Cisco DNA Center Plug and Play server. |
||
|
Step 3 |
The Mobility Express AP starts the PnP agent and contacts the PnP server.
|
||
|
Step 4 |
Find the unclaimed AP in the tab. The table lists all the unclaimed devices. The State column shows as Unclaimed. Use the Filter or Find option to find specific devices. You must wait for the Onboarding Status to become Initialized. |
||
|
Step 5 |
To claim the AP, check the check box next to the AP device name. |
||
|
Step 6 |
Choose in the menu bar above the device table. The Claim Devices window is displayed. |
||
|
Step 7 |
In the Site Assignment window, choose a site from the Site drop-down list. Claiming the selected AP to this particular site also applies the associated configurations. |
||
|
Step 8 |
Click Next. |
||
|
Step 9 |
To configure a device, click the device name in the Configuration window. |
||
|
Step 10 |
In the Configuration for device name window, assign the static IP details for the device:
|
||
|
Step 11 |
Click Save. |
||
|
Step 12 |
Click Next. The Summary window is displayed. |
||
|
Step 13 |
Click Claim in the Summary window. After the Mobility Express AP is claimed, the configured IP address is assigned to the Mobility Express AP. |
||
|
Step 14 |
(Optional) Add devices in bulk from a CSV file. For more information, see Add Devices in Bulk. When you bulk import Mobility Express APs through a CSV file, all the Mobility Express APs appear on the window. Based on the VRRP protocol, only one Mobility Express AP among the imported ME APs becomes the primary AP. The remaining APs become subordinate APs. After claiming the primary AP, you don't need to claim the subordinate APs. Cisco DNA Center does not clear the subordinate APs from the Plug and Play window. You must delete those subordinate APs manually from the window. |
||
|
Step 15 |
To provision the Cisco Wireless Controller, see Provision a Cisco AireOS Controller. |
With Cisco DNA Center, you can add and provision the Cisco Wireless Controller, which belongs to existing sites with pre-existing infrastructure.
Start by running a Discovery job on the device. All your devices are displayed on the Inventory window. For more information, see Discover Your Network and About Inventory.
The wireless controller should be reachable and in the Managed state on the Inventory window. For more information, see About Inventory.
|
Step 1 |
Click the menu icon ( The window is displayed with the discovered devices listed. |
||
|
Step 2 |
Click Filter and enter the appropriate values in the selected filter field. For example, for the Device Name filter, enter the name of the device. The data that is displayed in the Devices table is automatically updated according to your filter selection. |
||
|
Step 3 |
Check the check box next to the wireless controller device name that you want to provision. |
||
|
Step 4 |
From the Actions drop-down list, choose . The Site Assignment window opens and the Learn Device Configuration workflow begins.
|
||
|
Step 5 |
Associate a site to the controller in the Assign Site step:
|
||
|
Step 6 |
The Resolve Conflict step shows any conflicting configurations in Cisco DNA Center that you need to resolve. |
||
|
Step 7 |
Click Next. |
||
|
Step 8 |
The Design Object window lists all the learned configurations. |
||
|
Step 9 |
Choose to assign a site to the network profile. |
||
|
Step 10 |
In the Network Profiles window, configure the following:
|
||
|
Step 11 |
Click the menu icon ( |
||
|
Step 12 |
In the Summary window, review the configuration settings. |
||
|
Step 13 |
Click Deploy. |
||
|
Step 14 |
In the Provision Devices slide-in pane, do the following to preview the CLI configuration: |
The Cisco Catalyst 9800 Series Wireless Controller is the next generation of wireless controllers built for intent-based networking. The Cisco Catalyst 9800 Series Wireless Controller is Cisco IOS XE based and integrates the RF excellence from Aironet with the intent-based networking capabilities of Cisco IOS XE to create the best-in-class wireless experience for your organization.
The Cisco Catalyst 9800 Series Wireless Controller is built on a modular operating system and uses open, programmable APIs that enable automation of day-0 and day-N network operations.
The Cisco Catalyst 9800 Series Wireless Controller is available in multiple form factors:
Catalyst 9800-40 Wireless Controller.
Catalyst 9800-80 Wireless Controller.
Catalyst 9800-CL Cloud Wireless Controller: Deployable on private cloud (ESXi, KVM, Cisco ENCS, and Hyper-V) and manageable by Cisco DNA Center.
Catalyst 9800 Embedded Wireless Controller for Catalyst 9300 Series Switches, Catalyst 9400 Series Switches, and Catalyst 9500H Series Switches.
Cisco Catalyst 9800-L Wireless Controller: Provides seamless software updates for small- to mid-size enterprises. The Cisco Catalyst 9800-L Wireless Controller is available in two variations. You can choose between copper and fiber uplinks, which gives you flexibility in your network.
The following table lists the supported virtual and hardware platforms for the Cisco Catalyst 9800 Series Wireless Controller:
| Platform | Description |
|---|---|
|
Cisco Catalyst 9800-80 Wireless Controller |
Supports up to 6000 access points and 64,000 clients. Supports up to 80 Gbps throughput and occupies a 2-rack unit space. Modular wireless controller with up to 100-GE uplinks and seamless software updates. |
|
Cisco Catalyst 9800-40 Wireless Controller |
A fixed wireless controller with seamless software updates for mid-sized organizations and campus deployments. Supports up to 2000 access points and 32,000 clients. Supports up to 40 Gbps throughput and occupies a 1-rack unit space. Provides four 1-GE or 10-GE uplink ports. |
|
Cisco Catalyst 9800-CL Cloud Wireless Controller |
Cisco Catalyst 9800-CL Cloud Wireless Controller can be deployed in a private cloud or a public cloud as Infrastructure as a Service (IaaS). Cisco Catalyst 9800-CL Cloud Wireless Controller is the next generation of enterprise-class virtual wireless controllers built for high availability and security. A virtual form factor of Cisco Catalyst 9800-CL Cloud Wireless Controller for private cloud supports ESXi, KVM, Cisco ENCS, and Hyper-V hypervisors. |
|
Cisco Catalyst 9800 Embedded Wireless Controller for Catalyst 9000 Series Switches |
Cisco Catalyst 9800 Embedded Wireless Controller for Catalyst 9000 Series Switches bring the wired and wireless infrastructure together with consistent policy and management. This deployment model supports only Cisco SD-Access, which is a highly secure solution for small campuses and distributed branches. The embedded controller supports access points (APs) only in Fabric mode. |
|
Cisco Catalyst 9800-L Wireless Controller |
Cisco Catalyst 9800-L Wireless Controller provides seamless software updates for small to mid-size enterprises. The Cisco Catalyst 9800-L Wireless Controller is available in two variations. You can choose between copper and fiber uplinks, which gives you flexibility in your network.
|
The following table lists the host environments supported by the Cisco Catalyst 9800 Series Wireless Controller:
| Host Environment | Software Version |
|---|---|
|
VMware ESXi |
|
|
KVM |
|
|
NFVIS |
Cisco ENCS 3.8.1 and 3.9.1 |
The following table lists the Cisco Enterprise Network Function Virtualization Infrastructure Software (NFVIS) versions supported in Cisco DNA Center:
 Note |
Cisco Enterprise NFVIS devices support the N-1 to N upgrade path only. For example, upgrade from Cisco Enterprise NFVIS 3.11.x to Cisco Enterprise NFVIS 3.12.x only is supported. Upgrade from Cisco Enterprise NFVIS 3.11.x to Cisco Enterprise NFVIS 4.1.x is not supported. |
| Cisco Enterprise NFVIS Version | Enterprise Network Compute System Device Platform | Notes |
|---|---|---|
|
4.1.2 4.1.1 3.12.3 3.11.3 3.11.2 3.11.1 |
ENCS 5400 UCS-E UCS-C |
Cisco DNA Center supports the following NFVIS upgrade paths: NFVIS v3.11.1 > 3.11.2 > 3.11.3 > 3.12.3 > 4.1.1 > 4.1.2. Cisco Enterprise NFVIS 3.12.1 is not supported on any versions of Cisco DNA Center. Upgrade to Cisco Enterprise NFVIS 3.12.1 from Cisco Enterprise NFVIS 3.11.x using Cisco DNA Center is not supported. Upgrade to Cisco Enterprise NFVIS 3.12.2 from Cisco Enterprise NFVIS 3.12.1 using Cisco DNA Center is not supported. Upgrade to Cisco Enterprise NFVIS 3.12.2 from 3.11.2 is supported using Cisco DNA Center. Cisco Enterprise NFVIS 3.12.2 is supported on Cisco DNA Center. |
|
3.12.2 3.11.3 3.11.2 3.11.1 |
ENCS 5100 |
Cisco 5100 ENCS does not support Cisco Enterprise NFVIS 3.10.x. |
Install Cisco DNA Center.
For more information, see the Cisco DNA Center Installation Guide.
For information on software image upgrade, see Software Image Upgrade Support for Cisco Catalyst 9800 Series Wireless Controller.
Log in to the Cisco DNA Center GUI and verify that the applications you need are in the Running state.
Click the menu icon (![]() ) and choose .
) and choose .
Integrate Cisco Identity Services Engine with Cisco DNA Center. After integration, any devices that Cisco DNA Center discovers along with relevant configurations and data are pushed to Cisco ISE.
Discover the Cisco Catalyst 9800 Series Wireless Controller.
You must enable NETCONF and set the port to 830 to discover the Cisco Catalyst 9800 Series Wireless Controller. NETCONF provides a mechanism to install, manipulate, and delete configurations of network devices.
For more information, see Discover Your Network Using CDP or Discover Your Network Using an IP Address Range.
You must add the wireless management IP address manually.
While performing discovery using the Cisco Discovery Protocol (CDP) or an IP address range in the Discovery window, choose Use Loopback from the Preferred Management IP drop-down list to specify the device's loopback interface IP address.
Make sure that the discovered devices appear in the Device Inventory window and are in the Managed state.
For more information, see About Inventory and Display Information About Your Inventory.
You must wait for the devices to move to a Managed state.
To verify the Assurance connection with the Cisco Catalyst 9800 Series Wireless Controller, use the following commands:
Trustpoint DNAC-CA
Subject Name:
cn=kube-ca
Serial Number (hex): 00E***************
Certificate configured.
Trustpoint sdn-network-infra-iwan:
Subject Name:
cn=sdn-network-infra-ca
Serial Number (hex): 378***************
Certificate configured.Telemetry subscription brief
ID Type State Filter type
-----------------------------------------------------
1011 Configured Valid tdl-uri
1012 Configured Valid tdl-uri
1013 Configured Valid tdl-uri #show telemetry internal connection
Telemetry connection
Address Port Transport State Profile
---------------------------------------------------------
IP address 25103 tls-native Active sdn-network-infra-iwanNetwork-Assurance : True
Server Url : https://10.***.***.***
ICap Server Port Number : 3***
Sensor Backhaul SSID :
Authentication : UnknownConfigure a TACACS server while configuring authentication and policy servers.
Configuring TACACS is not mandatory if you have configured the username locally on the Cisco Catalyst 9800 Series Wireless Controller.
Design your network hierarchy by adding sites, buildings, and floors so that later you can easily identify where to apply design settings or configurations.
You can either create a new network hierarchy, or if you have an existing network hierarchy on Cisco Prime Infrastructure, you can import it into Cisco DNA Center.
To import and upload an existing network hierarchy, see Import Your Site Hierarchy to Cisco DNA Center.
To create a new network hierarchy, see Create, Edit and Delete a Site and Add, Edit, and Delete a Building.
Add the location information of APs, and position them on the floor map to visualize the heatmap coverage.
For more information, see Work with APs on a Floor Map.
Define network settings, such as AAA (Cisco ISE is configured for Network and Client Endpoint), NetFlow Collector, NTP, DHCP, DNS, syslog, and SNMP traps. These network servers become the default for your entire network. You can add a TACACS server while adding a AAA server.
For more information, see Network Settings Overview, Configure Global Network Servers, and Add AAA server.
Create a wireless radio frequency profile with the parent profile as custom.
For more information, see .
Create IP address pools at the global level.
Cisco DNA Center uses IP address pools to automate the configuration and deployment of SD-Access networks.
To create an IP address pool, see Configure IP Address Pools.
You must reserve an IP address pool for the building that you are provisioning. For more information, see Reserve IP Address Pools.
Create enterprise and guest wireless networks. Define the global wireless settings once; Cisco DNA Center then pushes the configurations to various devices across geographical locations.
Designing a wireless network is a two-step process. First, you must create SSIDs, and then associate the created SSID to a wireless network profile. This profile helps you to construct a topology, which is used to deploy devices on a site.
For more information, see Create SSIDs for an Enterprise Wireless Network and Create SSIDs for a Guest Wireless Network. For information about other wireless settings, see Configure Global Wireless Settings.
Configure the backhaul settings. For more information, see Manage Backhaul Settings.
Configure the following in the Policy window for the Cisco Catalyst 9800 Series Wireless Controller:
Create a virtual network. The virtual network segments your physical network into multiple logical networks.
Create a group-based access control policy and add a contract. For more information, see Create Group-Based Access Control Policy.
Configure high availability.
For more information, see Configure High Availability for the Cisco Catalyst 9800 Series Wireless Controller.
Provision the Cisco Catalyst 9800 Series Wireless Controller with the configurations added during the design phase.
For more information, see Provision a Cisco Catalyst 9800 Series Wireless Controller.
Configure and deploy application policies on the Cisco Catalyst 9800 Series Wireless Controller.
For more information, see Create an Application Policy, Deploy an Application Policy, and Edit an Application Policy.
 Note |
You must provision Cisco Catalyst 9800 Series Wireless Controller devices before deploying an application policy. |
For Cisco Catalyst 9800 Series Wireless Controller devices, two different policies with different business relevance for two different SSIDs do not work. The last deployed policy always takes precedence when you are setting up relevance.
For Cisco Catalyst 9800 Series Wireless Controller devices, changing the default business relevance for an application does not work in FlexConnect mode.
You can apply an application policy only on a nonfabric SSID.
Discover the Cisco Catalyst 9800 Series Wireless Controller.
Enable NETCONF and set the port to 830 to discover Cisco Catalyst 9800 Series Wireless Controller. NETCONF enables wireless services on the controller and provides a mechanism to install, manipulate, and delete the configuration of network devices.
For more information, see Discover Your Network Using CDP, or Discover Your Network Using an IP Address Range.
Make sure that the devices appear in the device inventory and are in the Managed state.
For more information, see About Inventory and Display Information About Your Inventory.
|
Step 1 |
Click the menu icon ( The window is displayed with the discovered devices listed. |
|
Step 2 |
Import the Cisco Catalyst 9800 Series Wireless Controller software image from your local computer or from a URL. For more information, see Import a Software Image. |
|
Step 3 |
Assign the software image to a device family. For more information, see Assign a Software Image to a Device Family. |
|
Step 4 |
You can mark a software image as Golden by clicking the star for a device family or a particular device role. For more information, see Specify a Golden Software Image. |
|
Step 5 |
Provision the software image. Click the menu icon ( |
|
Step 6 |
In the Inventory window, check the check box next to the Cisco Catalyst 9800 Series Wireless Controller whose image you want to upgrade. |
|
Step 7 |
From the Actions drop-down list, choose . For more information, see Provision a Software Image. |
Configuring High Availability (HA) on the Cisco Catalyst 9800 Series Wireless Controller involves the following prerequisites:
Both the Cisco Catalyst 9800 Series Wireless Controller devices are running the same software version and have the active software image on the primary Catalyst 9800 Series Wireless Controller.
The service port and management port of Catalyst 9800 Series Wireless Controller 1 and Catalyst 9800 Series Wireless Controller 2 are configured.
The redundancy port of Catalyst 9800 Series Wireless Controller 1 and Catalyst 9800 Series Wireless Controller 2 are physically connected.
Preconfigurations such as interface configurations, route addition, ssh line configurations, netconf-yang configurations are completed on the Catalyst 9800 Series Wireless Controller appliance.
The management interface of Catalyst 9800 Series Wireless Controller 1 and Catalyst 9800 Series Wireless Controller 2 are in the same subnet.
The discovery and inventory of Catalyst 9800 Series Wireless Controller 1 and Catalyst 9800 Series Wireless Controller 2 devices are successful from Cisco DNA Center.
The devices are reachable and are in the Managed state.
|
Step 1 |
Click the menu icon ( The window is displayed with the discovered devices listed. |
||
|
Step 2 |
To view devices available in a particular site, expand the Global site in the left pane, and select the site, building, or floor that you are interested in. All the devices available in that selected site are displayed in the Inventory window. |
||
|
Step 3 |
From the Device Type list, click the WLCs tab, and from the Reachability list, click the Reachable tab to get the list of wireless controllers that are discovered and reachable. |
||
|
Step 4 |
In the Inventory window, click the desired Cisco Catalyst 9800 Series Wireless Controller name to configure as a primary controller. |
||
|
Step 5 |
Click the High Availability tab. The selected Catalyst 9800 Series Wireless Controller by default becomes the primary controller and the Primary C9800 field is grayed out. |
||
|
Step 6 |
From the Select Primary Interface and Secondary Interface drop-down lists, choose the interface that is used for HA connectivity. The HA interface serves the following purposes:
|
||
|
Step 7 |
From the Select Secondary C9800 drop-down list, choose the secondary controller to create a HA pair.
|
||
|
Step 8 |
Enter the Redundancy Management IP and Peer Redundancy Management IP addresses in the respective fields.
|
||
|
Step 9 |
In the Netmask field, enter the netmask address. |
||
|
Step 10 |
Click Configure HA. The HA configuration is initiated at the background using the CLI commands. First, the primary controller is configured. On success, the secondary controller is configured. Both the devices reboot once the HA is enabled. This process may take up to 2.5 minutes to complete. |
||
|
Step 11 |
After the HA is initiated, the Redundancy Summary under High Availability tab displays the Sync Status as HA Pairing is in Progress. When Cisco DNA Center finds that the HA pairing is successful, the SyncStatus becomes Complete. This is triggered by the inventory poller or manual resynchronization. By now, the secondary controller (Catalyst 9800 Series Wireless Controller 2) is deleted from Cisco DNA Center. This flow indicates successful HA configuration in the Catalyst 9800 Series Wireless Controller. |
||
|
Step 12 |
To manually resynchronize the controller, on the window, select the controller that you want to synchronize manually. |
||
|
Step 13 |
From the Actions drop-down list, choose Resync. |
||
|
Step 14 |
The following is the list of actions that occur after the process is complete:
|
High Availability (HA) allows you to reduce the downtime of wireless networks that occurs because of the failover of controllers. You can configure HA on Cisco Catalyst 9800 Series Wireless Controller through Cisco DNA Center.
|
Step 1 |
Use the following commands to configure HA on the primary controller for Cisco Catalyst 9800 Series Wireless Controller:
|
||
|
Step 2 |
Use the following commands to configure HA on the secondary controller for Catalyst 9800 Series Wireless Controller:
|
||
|
Step 3 |
Run the chassis clear command to clear or delete all the HA-related parameters, such as the local IP, remote IP, HA interface, mask, timeout, and priority.
|
||
|
Step 4 |
Use the following commands to configure HA on the primary controller for the Cisco Catalyst 9800-40 Wireless Controller and Cisco Catalyst 9800-80 Wireless Controller devices:
|
||
|
Step 5 |
Use the following commands to configure HA on the secondary controller for the Cisco Catalyst 9800-40 Wireless Controller and Cisco Catalyst 9800-80 Wireless Controller devices:
|
||
|
Step 6 |
Run the chassis clear command to clear or delete all the HA-related parameters, such as the local IP, remote IP, HA interface, mask, timeout, and priority.
|
Use the following commands to verify the high availability configurations from Cisco Catalyst 9800 Series Wireless Controller:
Run the config redundancy mode sso command to check the HA-related details.
Run the show chassis command to view chassis configurations about the HA pair, including the MAC address, role, switch priority, and current state of each controller device in the redundant HA pair.
Run the show ip interface brief command to view the actual operating redundancy mode running on the device, and not the configured mode as set by the platform.
Run the show redundancy states command to view the redundancy states of the active and standby controllers.
Run the show redundancy summary command to check the configured interfaces.
Run the show romvar command to verify high availability configuration details.
N+1 High Availability
Cisco DNA Center supports N+1 High Availability (HA) on Cisco AireOS wireless controllers and Cisco Catalyst 9800 Series Wireless Controllers.
Cisco AireOS wireless controllers have a dedicated stock-keeping unit (SKU) for their N+1 controllers. Cisco Catalyst 9800 Series Wireless Controllers don't have a dedicated SKU; the same model must be used for HA.
The N+1 HA architecture provides redundancy for controllers across geographically separated data centers with low-cost deployments.
N+1 HA allows Cisco Wireless Controllers to be used as backup controllers for multiple primary controllers. These wireless controllers are independent of each other and do not share configuration or IP addresses on any of their interfaces. When a primary wireless controller resumes operation, the APs fall back automatically from the backup wireless controller to the primary wireless controller if the AP fallback option is enabled.
Cisco DNA Center supports primary and secondary controller configurations for N+1 HA.
N+1 HA is configured at the AP level, not at the global level. Configurations are pushed directly to the AP.
 Note |
The primary and secondary controllers must be of the same device type. For example, if the primary device is a Catalyst 9800 Series Wireless Controller, the secondary device must also be a Catalyst 9800 Series Wireless Controller. |
APs with higher priority on the primary controller always connect first to the backup controller, even if they have to push out the lower priority APs.
The N+1 HA configuration has the following limitations:
Auto provisioning of a secondary controller is not supported because of the VLAN ID configuration.
You must reprovision the secondary controller manually with the latest design configuration if you made any changes to the primary controller.
Cisco DNA Center does not support fault tolerance.
Access Point Stateful Switch Over (AP SSO) functionality is not supported for N+1 HA. The AP Control and Provisioning of Wireless Access Points (CAPWAP) state machine is restarted when the primary controller fails.
Discover primary and the secondary controller by running the Discovery feature.
For more information, see Discover Your Network Using CDP, or Discover Your Network Using an IP Address Range.
Make sure that the wireless controllers are reachable and in the Managed state.
For more information, see About Inventory and Display Information About Your Inventory.
Verify the network connectivity between devices. If the primary controller goes down, the AP should be able to join the secondary controller through the N+1 configuration.
Create two buildings to manage the primary and secondary locations for both devices. For example, create two buildings, Building A and Building B, where Building A is the primary managed location for controller-1 and also the secondary managed location for controller-2, and Building B is configured only as a primary managed location for controller-2.
For more information, see Create, Edit and Delete a Site and Add, Edit, and Delete a Building.
Add and position APs on a floor map to get a coverage heatmap visualization during the design phase.
For more information, see Work with APs on a Floor Map.
Create two SSIDs and associate them as the backhaul SSIDs.
For more information, see Create SSIDs for an Enterprise Wireless Network and Create SSIDs for a Guest Wireless Network.
|
Step 1 |
Click the menu icon ( The window is displayed with the discovered devices listed. |
|
Step 2 |
Check the check box next to the desired controller to provision it as a primary controller. |
|
Step 3 |
From the Actions drop-down list, choose . The Assign Site window is displayed. |
|
Step 4 |
Click Choose a site to assign a primary managed AP location for the primary controller. |
|
Step 5 |
In the Choose a site window, select a site and click Save. |
|
Step 6 |
Click Next. The Configuration window is displayed, which shows the primary AP managed location for the primary device. |
|
Step 7 |
Add or update the managed AP locations for the primary controller by clicking Select Primary Managed AP Locations. |
|
Step 8 |
In the Managed AP Location window, check the check box next to the site name, and click Save. You can either select a parent site or the individual sites. |
|
Step 9 |
Configure the interface and VLAN details. |
|
Step 10 |
Under Configure Interface and VLAN area, configure the IP address and subnet mask details, and click Next. |
|
Step 11 |
In the Advanced Configuration window, configure values for the predefined template variables, and click Next. |
|
Step 12 |
In the Summary window, verify the managed AP locations for the primary controller and other configuration details, and click Deploy. |
|
Step 13 |
Click Now to deploy the device immediately. Click Later to schedule the deployment for a later time. |
|
Step 14 |
To provision the secondary controller, in the Inventory window, check the check box next to the desired controller to provision it as a secondary controller. |
|
Step 15 |
From the Actions drop-down list, choose . The Assign Site window is displayed. |
|
Step 16 |
Click Choose a site to assign the managed AP location for the secondary controller. The managed AP location for the secondary controller should be same as the managed AP location of the primary controller. |
|
Step 17 |
In the Choose a site window, check the check box next to the site name to associate the secondary controller, and click Save. |
|
Step 18 |
Click Next. The Configuration window is displayed, which shows the primary AP managed and secondary AP managed locations for the secondary device. |
|
Step 19 |
Add or update the managed AP locations for the secondary controller by clicking Select Secondary Managed AP Locations. |
|
Step 20 |
In the Managed AP Location window, check the check box next to the site name, and click Save. You can either select a parent site or the individual sites. |
|
Step 21 |
Configure the interface and VLAN details for the secondary controller. |
|
Step 22 |
Under the Configure Interface and VLAN area, configure the IP address and subnet mask details for the secondary controller, and click Next. |
|
Step 23 |
In the Advanced Configuration window, configure values for the predefined template variables, and click Next. |
|
Step 24 |
In the Summary window, verify the managed AP locations for the secondary controller and other configuration details, and click Deploy. |
|
Step 25 |
Click Now to deploy the device immediately. Click Later to schedule the deployment for a later time. |
|
Step 26 |
To verify the managed locations of the primary and secondary controllers, click the device name of the controllers that you provisioned on the window. |
|
Step 27 |
In the dialog box, click View Device Details. |
|
Step 28 |
In the device details window, click the Managed ap locations tab to view the primary and secondary managed location details. |
|
Step 29 |
Provision the AP for the primary controller. |
|
Step 30 |
On the window, check the check box next to the AP that you want to provision. |
|
Step 31 |
From the Actions drop-down list, choose . |
|
Step 32 |
In the Assign Site window, click Choose a Floor to select the floor from the primary managed location. |
|
Step 33 |
Click Next. The Configuration window is displayed. |
|
Step 34 |
By default, the custom RF profile that you marked as the default under is chosen in the RF Profile drop-down list. You can change the default RF Profile value for an AP by selecting a value from the RF Profile drop-down list. |
|
Step 35 |
Click Next. |
|
Step 36 |
In the Summary window, review the configuration details. |
|
Step 37 |
Click Deploy to provision the primary AP. |
|
Step 38 |
You are prompted with a message that creation or modification of an AP group is in progress. You are prompted with a message stating After provisioning AP(s) will reboot. Do you want to continue?. |
|
Step 39 |
Click OK. When deployment succeeds, the Last Sync Status column in the Device Inventory window shows SUCCESS. |
The mobility configuration in Cisco DNA Center allows you to group a set of Cisco Wireless Controllers into a mobility group for a seamless roaming experience of wireless clients.
By creating a mobility group, you can enable multiple wireless controllers in a network to dynamically share information and forward traffic when inter-controller or inter-subnet roaming occurs. Mobility groups enable you to limit roaming between different floors, buildings, or campuses in the same enterprise by assigning different mobility group names to different wireless controllers within the same wireless network.
Cisco DNA Center allows you to create mobility groups between various platforms, such as Cisco Catalyst 9800 Series Wireless Controller and Cisco AireOS Controllers.
The mobility configuration has the following guidelines and limitations:
You cannot select multiple controllers for configuring mobility on the Provision window.
You cannot create mobility groups with the group name as default. This resets the mobility and RF group names as default and deletes all the peers.
You cannot configure a mobility group name on the anchor controller.
You must reboot the wireless controller manually if there is a change to the virtual IP address when configuring mobility groups on Cisco AireOS Controllers.
Wireless controllers with the same mobility group name are automatically grouped into a single mobility group and added as peers to each other.
When configuring mobility groups on Cisco AireOS Controllers, if the wireless controllers do not have the IP address 192.0.2.1, Cisco DNA Center pushes the virtual IP address 192.0.2.1 to all the wireless controllers.
Do not explicitly add guest anchor controllers to the mobility group. The provisioned guest anchor controllers do not appear in the drop-down list while adding peers in the mobility configuration window.
If you provision a wireless controller as a guest anchor, ensure that it is not added to the mobility group.
Here is the workflow that you can follow to configure mobility on Cisco Wireless Controller:
To configure mobility, you must provision a wireless controller with the mobility group name, RF group name, and mobility peers.
The configuration that is applied during the wireless controller provisioning is automatically replicated to all the mobility peers configured in that group.
Resynchronize the wireless controllers to get the latest tunnel status.
The following use cases explain the steps to configure mobility between controllers.
This use case assumes that wireless controller 1, wireless controller 2, and wireless controller 3 are newly added to Cisco DNA Center with the mobility group name, "Default." These wireless controllers aren't yet provisioned.
Provision wireless controller 1 by configuring the mobility group name, RF group name, and adding wireless controller 2 and wireless controller 3 as peers.
Provision wireless controller 2.
In the Provision window, the mobility configuration is automatically populated for wireless controller 2 with the group name and peers.
Provision wireless controller 3.
After provisioning all the wireless controllers, resynchronize the wireless controllers to receive the latest tunnel status.
This use case assumes that wireless controller 1, wireless controller 2, and wireless controller 3 have already been added to Cisco DNA Center with different mobility group names. These wireless controllers are provisioned.
Provision wireless controller 1 by configuring the mobility group name, RF group name, and adding wireless controller 2 and wireless controller 3 as peers.
The mobility configuration is automatically replicated across other peers, such as wireless controller 2 and wireless controller 3.
After the successful provisioning of wireless controller 1, wireless controller 2 and wireless controller 3 are added as peers on the wireless controller 1.
On wireless controller 2, wireless controller 1 and wireless controller 3 are added as peers.
On wireless controller 3, wireless controller 1 and wireless controller 2 are added as peers.
|
Step 1 |
Click the menu icon ( The window is displayed, which lists all the discovered devices. |
||
|
Step 2 |
Check the check box next to the Cisco Catalyst 9800 Series Wireless Controller name for which you want to configure mobility. |
||
|
Step 3 |
From the Actions drop-down list, choose . The Configure Mobility Group slide-in pane is displayed. For more information, see Mobility Configuration Overview. |
||
|
Step 4 |
From the Mobility Group Name drop-down list, you can either add a new mobility group by clicking +, or choose from the existing mobility groups. Information about the existing mobility peers is loaded from the intent available in Cisco DNA Center.
|
||
|
Step 5 |
In the RF Group Name field, enter a name for the RF group. |
||
|
Step 6 |
To enable Datagram Transport Layer Security (DTLS) data encryption, click the Data Link Encryption button on. |
||
|
Step 7 |
To enable or disable Cipher configuration for mobility, use the DTLS High Cipher Only toggle button. Cipher configuration is applicable for Cisco Catalyst 9800 Series Wireless Controller Release 17.5 or later. You must manually reboot the device for changes to take effect. |
||
|
Step 8 |
To manually reboot the device after making changes in the DTLS cipher configuration to take effect after provision, enable the Restart for DTLS Ciphers to take effect toggle button. |
||
|
Step 9 |
Under Mobility Peers, click Add to configure a mobility peer. |
||
|
Step 10 |
In the Add Mobility Peer slide-in pane, configure the following: |
||
|
Step 11 |
Click Configure Mobility. |
||
|
Step 12 |
You can reset the mobility group name and the RF group name using one of the following methods:
This step automatically sets the RF Group Name to default and removes all peers. After you provision, the mobility on the device is set and the device is removed from all other peers. |
Ciphersuites are a set of encryption and integrity algorithms designed to protect radio communication on your wireless LAN.
You can configure multiple DTLS (Data Datagram Transport Layer Security) Ciphersuites on Cisco Catalyst 9800 Series Wireless Controller, Cisco Catalyst 9800 Embedded Wireless Controller for Catalyst 9000 Series Switches, and Cisco Embedded Wireless Controller on Catalyst Access Points platforms running Release 17.5 or later.
You can configure DTLS Ciphersuites either at the global level or site level.
Make sure that the Device Controllability feature is enabled on the window.
Discover Cisco Catalyst 9800 Series Wireless Controllers in your network using the Discovery functionality so that the discovered devices are listed in the Inventory window.
|
Step 1 |
Click the menu icon ( |
|
Step 2 |
From the left hierarchy tree, choose Global to configure all sites with the same DTLS Ciphersuite configuration. From the left hierarchy tree, choose a site to configure DTLS Ciphersuites at the site level. The DTLS Ciphersuite configuration will be pushed to the controller available on that particular site. |
|
Step 3 |
Uncheck the Skip DTLS Ciphersuite Config check box to configure Ciphersuites as part of Device Controllability. |
|
Step 4 |
Configure either default Ciphersuites or custom Ciphersuites. By default, the Default Ciphersuite is selected. The Default Ciphersuite box shows the list of default Ciphersuites and these Ciphersuites are configured as default on the device. You cannot change the priority of these default ciphersuites. |
|
Step 5 |
To configure custom Ciphersuites, click the Custom button. Custom Ciphersuite overrides the default Ciphersuites with priority. |
|
Step 6 |
From the Version drop-down list, choose the DTLS version. Based on the DTLS version, Cisco DNA Center shows the available Ciphersuites. |
|
Step 7 |
Click the blue button next to the Ciphersuite if you do not want to apply any of the Ciphersuites. |
|
Step 8 |
To change the priority of Ciphersuites, drag each Ciphersuite. |
|
Step 9 |
Click Save. The message DTLS Ciphersuite Config Saved successfully is displayed. |
|
Step 10 |
To apply the Ciphersuite configuration, you must provision the device. For more information, see Provision a Cisco Catalyst 9800 Series Wireless Controller. |
The Rolling AP Upgrade feature is supported on the Cisco Catalyst 9800 Series Wireless Controller in an N+1 High Availability setup. This feature helps you upgrade software images on the APs associated with the Cisco Catalyst 9800 Series Wireless Controller in your wireless LAN network. To achieve the zero downtime, it is possible to upgrade APs in a staggered way using the N+1 Rolling AP Upgrade feature.
The primary controller identifies the candidate APs through the radio resource management neighbor AP map. The upgrade process starts with the software image downloading to the primary controller while the image is predownloaded to the candidate APs. After the candidate APs have been upgraded and rebooted, they join the secondary controller in a staggered manner. After all the APs have joined the secondary controller, the primary controller reboots. The APs rejoin the primary controller in a staggered manner after it is rebooted.
Here are the prerequisites for configuring the Rolling AP Upgrade feature:
An N+1 High Availability setup with two wireless controllers, one as the primary controller and the other one as the secondary.
The primary and the N+1 controllers have the same configuration and manage the same location in the network.
The N+1 controller is already running the Golden image so that Rolling AP Upgrade works with zero downtime.
Golden images are standardized images for network devices and Cisco DNA Center automatically downloads the images from Cisco.com. Image standardization helps in device security and optimal device performance.
The N+1 controller is reachable and in Managed state in Cisco DNA Center.
Both the controllers are part of the same mobility group, and a mobility tunnel is established between the primary and N+1 controller. The upgrade information between the primary and N+1 controllers are exchanged through the mobility tunnel.
 Note |
If you have a cyclic N+1 HA deployment, where wireless controller 1 is N+1 for wireless controller 2 and wireless controller 2 is N+1 for wireless controller 1, you cannot perform a rolling AP upgrade on both devices. Instead, one controller must go through a normal upgrade. You can perform a rolling AP upgrade on the other controller after the first controller is upgraded without the rolling AP upgrade. |
This procedure shows how to configure a Rolling AP Upgrade on Cisco Catalyst 9800 Series Wireless Controllers.
 Note |
N+1 Rolling AP Upgrade is supported on fabric and nonfabric deployments. |
|
Step 1 |
Install Cisco DNA Center. For more information, see the Cisco Digital Network Architecture Center Installation Guide. |
|
Step 2 |
Log in to the Cisco DNA Center GUI and verify that the applications you need are in the Running state. Click the menu icon ( |
|
Step 3 |
Discover the wireless controller using the Discovery feature. You must enable NETCONF and set the port to 830 to discover the Catalyst 9800 Series Wireless Controller. NETCONF provides a mechanism to install, manipulate, and delete the configurations on network devices. For more information, see Discover Your Network Using CDP or Discover Your Network Using an IP Address Range. |
|
Step 4 |
Make sure that the discovered devices appear in the Device Inventory window and are in the Managed state. For more information, see About Inventory and Display Information About Your Inventory. You must wait for devices to move to a Managed state. |
|
Step 5 |
Design your network hierarchy by adding sites, buildings, and floors so that later you can easily identify where to apply design settings or configurations. You can either create a new network hierarchy, or if you have an existing network hierarchy on Cisco Prime Infrastructure, you can import it into Cisco DNA Center. To import and upload an existing network hierarchy, see Import Your Site Hierarchy to Cisco DNA Center. To create a new network hierarchy, see Create, Edit and Delete a Site and Add, Edit, and Delete a Building. |
|
Step 6 |
Add the location information of APs, and position them on the floor map to visualize the heatmap coverage. For more information, see Work with APs on a Floor Map. |
|
Step 7 |
Provision the primary controller with the primary managed AP location, Rolling AP Upgrade enabled, and mobility group configured with the secondary controller as its peer. To do this, choose , and check the check box next to the primary controller name. |
|
Step 8 |
Configure the N+1 controller as the mobility peer in the Mobility Group configuration. For more information, see Mobility Configuration Overview. |
|
Step 9 |
Provision the N+1 HA controller by configuring the primary controller's primary managed AP location as the N+1 controller's secondary managed AP location. This configures the secondary controller as the N+1 controller. For more information, see Provision a Cisco Catalyst 9800 Series Wireless Controller. |
|
Step 10 |
Provision the APs that are associated with the primary controller. |
|
Step 11 |
Import the software images to the repository. For more information, see Import a Software Image. |
|
Step 12 |
Assign the software image to a device family. For more information, see Assign a Software Image to a Device Family. |
|
Step 13 |
Mark the software image as Golden by clicking the star for a device family or a device role. For more information, see Specify a Golden Software Image. |
|
Step 14 |
Before upgrading the image, make sure that the image readiness checks are successful for both devices. Also make sure that the status of the N+1 Device Check and the Mobility Tunnel Check has a green tick mark.
|
|
Step 15 |
Initiate the upgrade on primary controller. |
|
Step 16 |
On the Software Images window, check the check box next to the primary controller. |
|
Step 17 |
From the Actions drop-down list, choose . For more information, see Provision a Software Image. |
|
Step 18 |
To monitor the progress of the image upgrade, click In Progress in the Software Image column. The Device Status window displays the following information:
|
Before provisioning a Cisco Catalyst 9800 Series Wireless Controller make sure that you have completed the steps in Configure a Cisco Catalyst 9800 Series Wireless Controller in Cisco DNA Center.
|
Step 1 |
Click the menu icon ( The window is displayed, which lists all the discovered devices. |
||
|
Step 2 |
Check the check box next to the Catalyst 9800 Series Wireless Controller name that you want to provision. |
||
|
Step 3 |
From the Actions drop-down list, choose . |
||
|
Step 4 |
In the Assign Site window, click Choose a Site to associate with a site. |
||
|
Step 5 |
In the Choose a site slide-in window, check the check box next to the site name to associate a Catalyst 9800 Series Wireless Controller, and click Save. You can either select a parent site or the individual sites. If you select a parent site, all the children under the parent site are also selected. You can uncheck the check box to deselect an individual site. |
||
|
Step 6 |
Click Next. The Configuration window is displayed. |
||
|
Step 7 |
Select a role for the Cisco Catalyst 9800 Series Wireless Controller: Active Main WLC or Anchor. |
||
|
Step 8 |
Click Select Primary Managed AP Locations to select the managed AP location for primary controller. |
||
|
Step 9 |
Click Select Secondary Managed AP Locations to select the managed AP location for the secondary controller. |
||
|
Step 10 |
You can either select a parent site or the individual sites, and click Save. If you select a parent site, all the children under the parent site are also selected. You can uncheck the check box to deselect a particular site.
|
||
|
Step 11 |
For an active main wireless controller, you need to configure interface and VLAN details. |
||
|
Step 12 |
Under the Assign Interface area, do the following:
|
||
|
Step 13 |
Check the Skip AP Provision check box to skip configuring AP related commands while provisioning the Cisco Catalyst 9800 Series Wireless Controller. |
||
|
Step 14 |
Click Next. The Model Configuration window is displayed. |
||
|
Step 15 |
In the Devices pane, you can either search for a model config design by entering its name in the Find field, or expand the device and select a model config design. The selected model config design is displayed in the right pane. |
||
|
Step 16 |
Check the check box next to the Design Name that you want to provision, and click Configure to edit the model config design. You cannot edit all the configurations at this step. |
||
|
Step 17 |
After making the necessary changes, click Apply. |
||
|
Step 18 |
Click Next. The Advanced Configuration window is displayed, which is where you enter values for the predefined template variables. |
||
|
Step 19 |
Search for the device or the template in the Devices panel. |
||
|
Step 20 |
Enter a value for the predefined template variable in the wlanid field, and click Next. |
||
|
Step 21 |
In the Summary window, review the configuration settings and click Deploy. |
||
|
Step 22 |
Click Now to deploy the device immediately. Click Later to schedule the deployment for a later time. |
||
|
Step 23 |
To verify the configurations that are pushed from Cisco DNA Center to the device, use the following commands on the Cisco Catalyst 9800 Series Wireless Controller device:
|
||
|
Step 24 |
After the devices are deployed successfully, the Provision Status changes from Configuring to Success. |
||
|
Step 25 |
In the Inventory window, click See Details in the Provision Status column against a device to get more information about network intent or to view a list of actions. |
||
|
Step 26 |
Click See Details under Device Provisioning. |
||
|
Step 27 |
Click View Details under Deployment of network intent, and click the device name. |
||
|
Step 28 |
Click and expand the device name. |
||
|
Step 29 |
Expand the Configuration Summary area to view the operation details, feature name, and management capability. The configuration summary also displays any error that occurred while provisioning the device with the reasons for failure. |
||
|
Step 30 |
Expand the Provision Summary area to view details of the exact configuration that is sent to the device. |
||
|
Step 31 |
Provision the AP. |
With Cisco DNA Center, you can add and provision devices such as Cisco Wireless Controllers and Cisco Catalyst 9800 Series Wireless Controllers in the existing deployment.
Start by running a Discovery job on the device. All your devices are displayed on the Inventory window. For more information, see Discover Your Network and About Inventory.
The wireless controller should be reachable and in Managed state on the Inventory window. For more information, see About Inventory.
To discover Cisco Catalyst 9800 Series Wireless Controller, you must enable NETCONF and set the port to 830. For more information, see Discovery Overview.
Design your network hierarchy by adding sites, buildings, and floors so that later you can easily identify where to apply design settings or configurations. You can either create a new network hierarchy or, if you have an existing network hierarchy on Cisco Prime Infrastructure, import it into Cisco DNA Center.
For more information about importing and uploading an existing network hierarchy, see Import Your Site Hierarchy to Cisco DNA Center.
For more information about creating a new network hierarchy, see Create, Edit and Delete a Site and Add, Edit, and Delete a Building.
|
Step 1 |
Click the menu icon ( The window is displayed with the discovered devices listed. |
||
|
Step 2 |
Click Filter and enter the appropriate values in the selected filter field. For example, for the Device Name filter, enter the name of the device. The data that is displayed in the Devices table is automatically updated according to your filter selection. |
||
|
Step 3 |
Check the check box next to the wireless controller device name that you want to provision. |
||
|
Step 4 |
From the Actions drop-down list, choose . The Site Assignment window opens and the Learn Device Configuration workflow begins.
|
||
|
Step 5 |
Follow Step 3 through Step 13 in Learn Device Configurations from Devices with Pre-Existing Infrastructure. |
||
|
Step 6 |
Click the menu icon ( |
||
|
Step 7 |
Click Filter to locate the device that you want to provision. The data that is displayed in the Devices table is automatically updated according to your filter selection. |
||
|
Step 8 |
Check the check box next to the wireless controller that you want to provision. |
||
|
Step 9 |
From the Actions drop-down list, choose . |
||
|
Step 10 |
Review the details in the Assign Site step, and click Next. |
||
|
Step 11 |
In the Configuration step, configure the following:
|
||
|
Step 12 |
In the Model Configuration step, configure the following.
|
||
|
Step 13 |
In the Advanced Configuration window, you can enter values for the predefined template variables.
|
||
|
Step 14 |
In the Summary window, review the configuration settings. (To make any changes, click Edit.) |
||
|
Step 15 |
To proceed, click Deploy. |
||
|
Step 16 |
In the Schedule window, click Now or Later to indicate when you want to start the configuration, and click Apply. |
||
|
Step 17 |
Provision the AP. For information, see Provision a Cisco AP—Day 1 AP Provisioning. |
The Cisco Embedded Wireless Controller on Catalyst Access Points (EWC-APs) is the next-generation Wi-Fi solution, which combines the Cisco Catalyst 9800 Series Wireless Controller with Cisco Catalyst 9100 Series Access Points, creating the best-in-class wireless experience for the evolving and growing organization.
Design your network hierarchy with sites, buildings, floors, and so on.
For more information, see Create, Edit and Delete a Site and Add, Edit, and Delete a Building.
Define the device credentials, such as CLI, SNMP, HTTP, and HTTPS at the global level. The credentials that are defined at the global level are inherited by the sites.
For more information, see Configure Global CLI Credentials, Configure Global SNMPv2c Credentials, and Configure Global SNMPv3 Credentials.
Create wireless SSIDs, wireless interfaces, and wireless Radio Frequency profiles.
For more information, see Create SSIDs for an Enterprise Wireless Network, Create SSIDs for a Guest Wireless Network, Create a Wireless Interface, and .
 Note |
For Cisco Embedded Wireless Controller on Catalyst Access Points, only Flex-based SSID creation is supported. |
Configure the DHCP server with Option #43 on the switch where the Cisco Embedded Wireless Controller on Catalyst Access Points is connected. This is IP address of the Cisco DNA Center Plug and Play server. Using this IP address, the APs contact the PnP server and download the configuration.
Make sure that you have the Cisco Embedded Wireless Controller on Catalyst Access Points in the inventory. If not, discover them using the Discovery feature. For more information, see Discover Your Network Using CDP, Discover Your Network Using an IP Address Range, and About Inventory.
The APs should be in the factory reset state without any Cisco Wireless Controller configurations.
The Cisco Embedded Wireless Controller on Catalyst Access Points is available in multiple form factors:
Cisco Embedded Wireless Controller on Catalyst 9115AX Access Points
Cisco Embedded Wireless Controller on Catalyst 9117AX Access Points
Cisco Embedded Wireless Controller on Catalyst 9120AX Access Points
Cisco Embedded Wireless Controller on Catalyst 9130AX Access Points
|
Step 1 |
The Cisco Embedded Wireless Controller on Catalyst Access Points contacts the DHCP server. In response, the DHCP server provides the IP address along with Option #43, which contains the IP address of the Cisco Plug and Play server. |
||
|
Step 2 |
Based on Option #43, the Cisco Embedded Wireless Controller on Catalyst Access Points turns on the Plug and Play agent and contacts the Cisco DNA Center Plug and Play server.
|
||
|
Step 3 |
Find the unclaimed Cisco Embedded Wireless Controller on Catalyst Access Points in the tab. The table lists all the unclaimed devices. The State column shows as Unclaimed. Use the Filter or Find option to find specific devices. You must wait for the onboarding status to become Initialized under the Onboarding State column. |
||
|
Step 4 |
To claim the Cisco Embedded Wireless Controller on Catalyst Access Points, check the check box next to the AP device name. |
||
|
Step 5 |
Choose in the menu bar above the device table. The Claim Devices window is displayed. |
||
|
Step 6 |
In the Site Assignment window, choose a site from the Site drop-down list. Claiming the selected AP to this particular site also applies the associated configurations. |
||
|
Step 7 |
Click Next. |
||
|
Step 8 |
To configure a device, click the device name in the Configuration window. |
||
|
Step 9 |
In the Configuration for device name window, assign the static IP details for the device. |
||
|
Step 10 |
Click Save. |
||
|
Step 11 |
Click Next. The Summary window is displayed. |
||
|
Step 12 |
Click Claim in the Summary window. After the Cisco Embedded Wireless Controller on Catalyst Access Points is claimed, the IP address configured is assigned to the Cisco Embedded Wireless Controller. The claimed device, which is a Cisco Embedded Wireless Controller with an internal AP, is now available under . |
||
|
Step 13 |
To provision the additional controller, see Provision a Cisco AireOS Controller. |
||
|
Step 14 |
To bulk import devices from a CSV file, see Add Devices in Bulk. |
||
|
Step 15 |
To add devices manually, see Add or Edit a Device. |
Design your network hierarchy by adding sites, buildings, and floors.
Discover the Cisco Catalyst 9800 Series Wireless Controller by running the Discovery feature and add it to the Inventory. Make sure that the device status is reachable and in the Managed state.
You must enable NETCONF and set the port to 830 to discover the Catalyst 9800 Series Wireless Controller. NETCONF provides a mechanism to install, manipulate, and delete the configurations of network devices.
Discover the Cisco AireOS Controllers and add it to the Inventory. Make sure that the device status is reachable and in the Managed state.
|
Step 1 |
Click the menu icon ( The Inventory window is displayed, which lists the discovered devices. |
||
|
Step 2 |
Check the check box next to the Cisco AireOS Controller. |
||
|
Step 3 |
From the Actions drop-down list, choose . |
||
|
Step 4 |
In the Assign Device to Site window, click Choose a Site. |
||
|
Step 5 |
In the Add Sites window, check the check box next to the site name to associate a Cisco AireOS Controller. |
||
|
Step 6 |
Click Save. |
||
|
Step 7 |
From the Actions drop-down list, choose . The Site Assignment window opens and the Learn Device Configuration workflow begins.
|
||
|
Step 8 |
In the Assign Site window, click Next. |
||
|
Step 9 |
The Resolve Conflict window shows any conflicting configurations in Cisco DNA Center that you need to resolve. Click Next. |
||
|
Step 10 |
In the Design Object window, click Next. |
||
|
Step 11 |
In the left pane, click Network. The right pane displays network configurations that were learned as part of the device configuration learning process, and shows the following information:
|
||
|
Step 12 |
Click Next. |
||
|
Step 13 |
In the left pane, click Wireless. The Wireless window displays the enterprise SSIDs, guest SSIDs, wireless interfaces, and RF profiles that are present on the device. |
||
|
Step 14 |
For an SSID with a preshared key (PSK), enter the passphrase key. |
||
|
Step 15 |
In the left pane, click Discarded Config. This displays the conflicting and the existing configurations on Cisco DNA Center. The discarded configuration entries are available under the following categories:
|
||
|
Step 16 |
Click Next. |
||
|
Step 17 |
The Network Profile window lists the network profile or site profile that is created based on the AP and WLAN combination. |
||
|
Step 18 |
Click Save. A success message is displayed. |
||
|
Step 19 |
Choose to view the SSID and interface configurations that Cisco DNA Center has learned from the Cisco AireOS Controller. |
||
|
Step 20 |
Choose to assign a site to the network profile. |
||
|
Step 21 |
In the Network Profiles window, click Assign Site to add sites to the selected profile. |
||
|
Step 22 |
In the Add Sites to Profile window, choose a site from the drop-down list, and click Save. |
||
|
Step 23 |
Click the Provision tab. |
||
|
Step 24 |
Check the check box next to the Cisco Catalyst 9800 Series Wireless Controller that you want to provision. |
||
|
Step 25 |
From the Actions drop-down list, choose Provision. |
||
|
Step 26 |
Click Choose a site to assign a site for the Cisco Catalyst 9800 Series Wireless Controller. |
||
|
Step 27 |
In the Choose a site window, check the check box next to the site name to associate a Catalyst 9800 Series Wireless Controller. |
||
|
Step 28 |
Click Next. The Configuration window is displayed. |
||
|
Step 29 |
Select a role for the Cisco Catalyst 9800 Series Wireless Controller as Active Main WLC. |
||
|
Step 30 |
Click Select Primary Managed AP Locations to configure a managed AP location for the primary controller. |
||
|
Step 31 |
In the Managed AP Location window, check the check box next to the site name. You can either select a parent site or the individual sites. If you select a parent site, the children under that parent site are automatically selected. |
||
|
Step 32 |
Click Save. |
||
|
Step 33 |
Click Next. |
||
|
Step 34 |
The Summary window shows the configurations that will be pushed to the Cisco Catalyst 9800 Series Wireless Controller from the Cisco AireOS Controller. |
||
|
Step 35 |
Click Deploy to provision the Cisco Catalyst 9800 Series Wireless Controller. |
||
|
Step 36 |
Click Now to deploy the device immediately. Click Later to schedule deployment for a later time and click Apply. |
||
|
Step 37 |
After the devices are deployed successfully, the Provision Status changes from Configuring to Success. |
||
|
Step 38 |
In the Device Inventory window, click See Details in the Provision Status column to get more information about the network intent or to view a list of actions that you need to take. |
||
|
Step 39 |
To manually resynchronize the Cisco Catalyst 9800 Series Wireless Controller, on the window, select the controller that you want to manually synchronize. |
||
|
Step 40 |
From the Actions drop-down list, choose Resync. |
||
|
Step 41 |
Provision the AP. |
Configure and Provision a Cisco Catalyst 9800 Embedded Wireless Controller for Catalyst 9000 Series Switches
|
Device Role |
Platforms |
|---|---|
|
Embedded Wireless Controller |
Cisco Catalyst 9300 Series Switches Cisco Catalyst 9400 Series Switches Cisco Catalyst 9500H Series Switches |
|
Fabric Edge |
Cisco Catalyst 9300 Series Switches Cisco Catalyst 9400 Series Switches Cisco Catalyst 9500H Series Switches Cisco Catalyst 3600 Series Switches Cisco Catalyst 3850 Series Switches |
|
APs |
Cisco 802.11ac Wave 2 APs:
Cisco 802.11ac Wave 1 APs
Cisco Catalyst 9105 Series Wi-Fi 6 Access Points Cisco Catalyst 9115 Series Wi-Fi 6 Access Points Cisco Catalyst 9117 Series Wi-Fi 6 Access Points Cisco Catalyst 9120 Series Wi-Fi 6 Access Points Cisco Catalyst 9124 Series Wi-Fi 6 Access Points Cisco Catalyst 9130 Series Wi-Fi 6 Access Points Cisco Catalyst 9136 Series Wi-Fi 6 Access Points |
On the Cisco Catalyst 9800 Series Wireless Controller, make sure that the following commands are present if the switch is already configured with aaa new-model:
aaa new-modelaaa authentication login default localaaa authorization exec default localaaa session-id commonThis is required for NETCONF configuration. These configurations are not required if you are using an automated underlay for provisioning.
Install Cisco DNA Center.
For more information, see the Cisco DNA Center Installation Guide.
Log in to the Cisco DNA Center GUI and verify that the applications you need are in the Running state.
Click the menu icon (![]() ) and choose .
) and choose .
Integrate Cisco Identity Services Engine with Cisco DNA Center. After Cisco ISE is registered with Cisco DNA Center, any device that Cisco DNA Center discovers, along with relevant configurations and other data, is pushed to Cisco ISE.
Discover Cisco Catalyst 9000 Series Switches and the edge switches.
You must enable NETCONF and set the port to 830 to discover Cisco Catalyst 9800 Embedded Wireless Controller for Catalyst 9000 Series Switches.
Do not enable NETCONF to discover the edge switches.
For more information, see Discover Your Network Using CDP and Discover Your Network Using an IP Address Range.
Change the Preferred Management IP to Use Loopback.
Make sure that the devices appear in the device inventory and are in Managed state.
For more information, see About Inventory and Display Information About Your Inventory.
Ensure that the devices are in the Managed state.
Design your network hierarchy, which represents your network's geographical location. You can create sites, buildings, and floors so that later you can easily identify where to apply the design settings or configurations.
You can either create a new network hierarchy, or if you have an existing network hierarchy on Cisco Prime Infrastructure, you can import it into Cisco DNA Center.
To import and upload an existing network hierarchy, see the Import Your Site Hierarchy to Cisco DNA Center.
To create a new network hierarchy, see the Create, Edit and Delete a Site and Add, Edit, and Delete a Building.
For a nonfabric network, add and position APs on a floor map to get heatmap visualization during the design phase.
For a fabric network, you cannot place APs on a floor map during the design time. The APs are onboarded after adding devices to a fabric network.
For more information, see Work with APs on a Floor Map.
Define network settings, such as AAA (Cisco ISE is configured for Network and Client Endpoint), NetFlow Collector, NTP, DHCP, DNS, syslog, and SNMP traps. These network servers become the default for your entire network.
You can configure up to six AAA servers on the Wireless window during the SSID creation.
For more information, see Network Settings Overview, Configure Global Network Servers, and Add AAA server.
Configure device credentials, such as CLI, SNMP, and HTTPs.
For more information, see Global Device Credentials Overview, Configure Global CLI Credentials, Configure Global SNMPv2c Credentials, Configure Global SNMPv3 Credentials, and Configure Global HTTPS Credentials.
Configure IP address pools at the global level.
To configure an IP address pool, see Configure IP Address Pools.
To reserve an IP address pool for the building that you are provisioning, see Reserve IP Address Pools.
Create enterprise and guest wireless networks. Define the global wireless settings once, and then Cisco DNA Center pushes the configurations to various devices across geographical locations.
Designing a wireless network is a two-step process. First, you must create SSIDs on the Wireless window. Then, associate the created SSID to a wireless network profile. This profile helps you to construct a topology, which is used to deploy devices on a site.
For more information, see Create SSIDs for an Enterprise Wireless Network and Create SSIDs for a Guest Wireless Network.
Configure the backhaul settings.
Configure the following on the Policy window:
Create a virtual network. The virtual network segments your physical network into multiple logical networks.
Create a group-based access control policy, and add a contract. For more information, see Create Group-Based Access Control Policy.
Provision Cisco Catalyst 9000 Series Switches and the edge node switches with the configurations added during the design phase.
Create a fabric site.
Add devices to the fabric network by creating a CP+Border+Edge or CP+Border.
Enable embedded wireless capabilities on the Cisco Catalyst 9800 Embedded Wireless Controller for Catalyst 9000 Series Switches.
Onboard APs in the fabric site.
After the devices are deployed successfully, the deploy status changes from Configuring to Success.
Before provisioning a Cisco Catalyst 9800 Embedded Wireless Controller on Catalyst 9000 Series Switches, ensure that you have completed the steps in Configure Cisco Catalyst 9800 Embedded Wireless Controller for Catalyst 9000 Switches.
This procedure explains how to provision embedded wireless on Cisco Catalyst 9300 Series Switches, Cisco Catalyst 9400 Series Switches, and Cisco Catalyst 9500H Series Switches.
|
Step 1 |
Click the menu icon ( The window is displayed with the discovered devices listed. |
|
Step 2 |
Check the check box next to the Catalyst 9000 Series Switch device and an edge switch that you want to associate to a site. |
|
Step 3 |
From the Actions drop-down list, choose . |
|
Step 4 |
In the Assign Device to Site step, do the following: |
|
Step 5 |
In the window, check the check box next to the device name that you want to provision. |
|
Step 6 |
To provision the edge switch, check the check box next to the edge switch that you want to provision. |
|
Step 7 |
To add devices to a fabric site, click the menu icon ( |
|
Step 8 |
Create a fabric site. For more information, see Add a Fabric Site. |
|
Step 9 |
Add an IP transit network. |
|
Step 10 |
Add devices and associate virtual networks to a fabric site. |
|
Step 11 |
Add the Cisco Catalyst 9000 Series Switch as a control plane, a border node, and an edge node or a control plane and a border node.
|
|
Step 12 |
To enable embedded wireless on the device, click the device that is added as a Edge, CP+Border+Edge or CP+Border, and click the Embedded Wireless. |
|
Step 13 |
In the Summary window, review the configuration settings, and click Save. |
|
Step 14 |
On the Modify Fabric step, click Now to commit the changes, and click Apply to apply the configurations. |
|
Step 15 |
In the Cisco DNA Center GUI, click the Provision tab. |
|
Step 16 |
Click the Fabric tab. A list of fabric sites is displayed. |
|
Step 17 |
Select the fabric site that was created, and click the Host Onboarding tab to enable IP pool for APs. |
|
Step 18 |
Select the authentication template that is applied for devices in the fabric site. These templates are predefined configurations that are retrieved from Cisco ISE. After selecting the authentication template, click Save. |
|
Step 19 |
Under Virtual Networks, click INFRA_VN to associate one or more IP pools with the selected virtual network. |
|
Step 20 |
Under Virtual Network, click the guest virtual networks to associate IP pools for the selected guest virtual network. |
|
Step 21 |
Check the IP Pool Name check box that was created for APs during the design phase. |
|
Step 22 |
Click Update to save the setting. The AP gets the IP address from the specified pool, which is associated with the AP VLAN and registers with the Cisco wireless controller through one of the discovery methods. |
|
Step 23 |
Specify wireless SSIDs within the network that hosts can access. Under the Wireless SSID section, select the guest or enterprise SSIDs and assign address pools, and click Save. |
|
Step 24 |
Manually trigger resynchronization by performing an Inventory > Resync to see the APs on Cisco DNA Center for embedded wireless. |
|
Step 25 |
Provision the AP. For more information, see Provision a Cisco AP—Day 1 AP Provisioning. |
|
Step 26 |
Configure and deploy application policies. For more information, see Create an Application Policy, Deploy an Application Policy, and Edit an Application Policy. Provision the Catalyst 9300 Series Switches and Cisco Catalyst 9500H Series Switches before deploying an application policy. Two different policies with different business relevance for two different SSIDs do not work. Always the last deployed policy takes precedence when you are setting up the relevance. Changing the default business relevance for an application does not work in FlexConnect mode. You can apply an application policy only on a nonfabric SSID. |
Inter-Release Controller Mobility (IRCM) supports seamless mobility and wireless services across different Cisco Wireless Controllers with different software versions.
Cisco DNA Center supports the guest anchor feature for the following device combinations:
Configuration of a Cisco AireOS controller as a foreign controller with a Cisco AireOS controller as an anchor controller.
Configuration of a Cisco AireOS controller as a guest anchor controller with a Cisco Catalyst 9800 Series Wireless Controller as a foreign controller.
Configuration of a Cisco Catalyst 9800 Series Wireless Controller as a foreign controller with a Cisco Catalyst 9800 Series Wireless Controller as an anchor controller.
Configuring IRCM on controller devices has the following limitations:
Configuration of a Cisco AireOS controller as a foreign controller and Cisco Catalyst 9800 Series Wireless Controller as an anchor controller is not supported.
Configuration of a fabric guest anchor is not supported.
Configuration of multiple anchor controllers and one foreign controller is not supported.
Only guest SSID is supported.
Broadcast of a nonguest anchor SSID in guest anchor mode is not supported.
Mobility tunnel is not encrypted.
Follow these steps to configure a guest anchor Cisco Wireless Controller.
|
Step 1 |
Design a network hierarchy, with sites, buildings, floors, and so on. For more information, see Create, Edit and Delete a Site. |
||
|
Step 2 |
Configure network servers, such as AAA, DHCP, and DNS servers. For more information, see Configure Global Network Servers and Add Cisco ISE or Other AAA Servers. |
||
|
Step 3 |
Create SSIDs for a guest wireless network with external web authentication and central web authentication along with configuring Cisco Identity Services Engine. |
||
|
Step 4 |
Discover the wireless controller using the Cisco Discovery Protocol (CDP) or an IP address range, and make sure that the devices are in the window and in the Managed state. For more information, see Discovery Overview. |
||
|
Step 5 |
Provision a foreign wireless controller as the active main wireless controller. See Provision a Cisco AireOS Controller.
|
||
|
Step 6 |
Choose the role for the wireless controller as guest anchor and provision the guest anchor controllers. For more information, see Provision a Cisco AireOS Controller.
|
||
|
Step 7 |
Configure device credentials, such as CLI, SNMP, HTTP, and HTTPS. For more information, see Configure Global CLI Credentials, Configure Global SNMPv2c Credentials, Configure Global SNMPv3 Credentials, and Configure Global HTTPS Credentials. |
Discover the Cisco Catalyst 9800 Series Wireless Controller and Cisco AireOS Controllers.
You must enable NETCONF and set the port to 830 to discover the Catalyst 9800 Series Wireless Controller. NETCONF provides a mechanism to install, manipulate, and delete the configurations of network devices.
For more information, see Discover Your Network Using CDP or Discover Your Network Using an IP Address Range.
Design your network hierarchy by adding sites, buildings, and floors so that later you can easily identify where to apply design settings or configurations.
To create a new network hierarchy, see Create, Edit and Delete a Site and Add, Edit, and Delete a Building.
Add the location information of APs, and position them on the floor map to visualize the heatmap coverage.
For more information, see Work with APs on a Floor Map.
Define network settings, such as AAA (Cisco ISE is configured for Network and Client Endpoint), NetFlow Collector, NTP, DHCP, DNS, syslog, and SNMP traps. These network servers become the default for your entire network. You can add a TACACS server while adding a AAA server.
For more information, see Network Settings Overview, Configure Global Network Servers, and Add AAA server.
Create SSIDs for a guest wireless network.
For more information, see Create SSIDs for a Guest Wireless Network.
The WLAN profile name of the foreign controller and anchor controller should be the same for mobility.
|
Step 1 |
Click the menu icon ( The window is displayed with the discovered devices listed. |
||
|
Step 2 |
Check the check box next to the Catalyst 9800 Series Wireless Controller that you want to provision as a foreign controller. |
||
|
Step 3 |
From the Actions drop-down list, choose . |
||
|
Step 4 |
In the Assign Site window, click Choose a Site to assign a site for the Catalyst 9800 Series Wireless Controller device. |
||
|
Step 5 |
In the Add Sites window, check the check box next to the site name to associate a Catalyst 9800 Series Wireless Controller. |
||
|
Step 6 |
Click Save. |
||
|
Step 7 |
Click Apply. |
||
|
Step 8 |
Click Next. |
||
|
Step 9 |
Select a role for the Catalyst 9800 Series Wireless Controller as Active Main WLC. |
||
|
Step 10 |
For an active main wireless controller, you need to configure interface and VLAN details. |
||
|
Step 11 |
Under the Assign Interface area, do the following:
|
||
|
Step 12 |
Click Next. |
||
|
Step 13 |
In the Summary window, review the configuration settings. |
||
|
Step 14 |
Click Deploy to provision the Catalyst 9800 Series Wireless Controller as a foreign controller. |
||
|
Step 15 |
On the window, check the check box next to the Cisco AireOS Controller that you want to provision as a guest anchor controller. |
||
|
Step 16 |
Repeat Step 3 through Step 8. |
||
|
Step 17 |
Select a role for the Cisco AireOS Controller as Guest Anchor. |
||
|
Step 18 |
For a guest anchor wireless controller, you need to configure the interface and VLAN details. |
||
|
Step 19 |
Repeat Step 11 through Step 14. |
Integrate the Meraki dashboard with Cisco DNA Center. See Integrate the Meraki Dashboard.
Create the SSID. See Create SSIDs for an Enterprise Wireless Network.
 Note |
The Meraki dashboard supports the following types of SSIDs:
For every SSID, you can choose an interface name. If you choose the Management interface in Cisco DNA Center and the VLAN ID is 0, the configuration is not supported in the Meraki dashboard and VLAN tagging is disabled in the Meraki dashboard. If you create a custom interface for the SSID in Cisco DNA Center, an AP tag is created with the custom interface name and VLAN ID in the Meraki dashboard. |
Create the network profile and assign it to the sites for which the SSID is provisioned.
 Note |
The Network Hierarchy in Cisco DNA Center corresponds to in the Meraki dashboard. We recommend that you choose Buildings in the Add Sites to Profile window in the workflow. |
 Note |
Cisco DNA Center creates the Meraki network and provisions the SSIDs to the network. The Meraki dashboard provisions the Meraki network configuration to the Meraki devices. |
This procedure explains how to provision SSIDs to Cisco Meraki devices managed by a Meraki dashboard.
|
Step 1 |
Click the menu icon ( The window is displayed with the discovered devices listed. |
||
|
Step 2 |
To view the Meraki dashboard, expand the Global site in the left pane, and select a building. All Meraki dashboards available in the selected building are displayed. |
||
|
Step 3 |
Check the check box next to the Meraki dashboard name that you want to provision. |
||
|
Step 4 |
From the Actions drop-down list, choose . The Assign Site window is displayed, which is where you can view the Meraki dashboard and the associated building. |
||
|
Step 5 |
To change the associated building, click Choose a site. |
||
|
Step 6 |
In the Choose a site window, select a building and click Save. |
||
|
Step 7 |
Click Next. The Configuration window is displayed. You can view the managed building in the primary location. |
||
|
Step 8 |
Click Select Secondary Managed AP Locations to select the secondary managed location for the Meraki dashboard. |
||
|
Step 9 |
In the Managed AP Location window, check the check box next to the building name. |
||
|
Step 10 |
Click Save. |
||
|
Step 11 |
Click Next.
|
||
|
Step 12 |
Click Deploy. |
||
|
Step 13 |
In the Provision Devices window, do the following to preview the CLI configuration: |
The following topics explain the components of remote teleworker sites and the procedure for provisioning remote teleworker devices.
The Cisco remote teleworker deployment is built around three main components: Cisco wireless controllers, Cisco OfficeExtend access points (APs) and a Corporate firewall. The following models are supported in this deployment:
Wireless Controllers: Cisco 5520 Wireless Controller, Cisco 8540 Wireless Controller, Cisco 3504 Wireless Controller2, Cisco Catalyst 9800-40 Wireless Controller, Cisco Catalyst 9800-80 Wireless Controller, and Cisco Catalyst 9800-L Wireless Controller.
Access Points: Cisco Aironet 1815T (Teleworker) Access Point, Cisco Aironet 1815I Access Point, Cisco Aironet 1815W Access Point, Cisco Aironet 1840I Access Point, Cisco Aironet 2800 Series Access Points, Cisco Aironet 3800 Series Access Points, Cisco Aironet 4800 Series Access Points, Cisco Catalyst 9115 Access Point, Cisco Catalyst 9120 Access Point, and Cisco Catalyst 9130 Access Point.
Cisco controllers are responsible for system-wide WLAN functions, such as security policies, intrusion prevention, RF management, quality of service (QoS), and mobility. They work in conjunction with Cisco APs to support business-critical wireless applications for teleworkers. Controllers provide the control, scalability, security, and reliability that network managers need to build a secure, scalable teleworker environment.
To allow users to connect their corporate devices to the organization's on-site wireless network, the remote teleworking solution offers the same wireless Secure Set Identifiers (SSIDs) at a teleworker's home as those that support data and voice inside the organization.
APs cannot act independently of controllers. As an AP communicates with the controller resources, it downloads its configuration and synchronizes its software or firmware image, if required. The AP establishes a secure Datagram Transport Layer Security (DTLS) connection to the controller, which offers remote WLAN connectivity using the same profile as at the corporate office. Secure tunneling allows all traffic to be validated against centralized security policies and minimizes the management overhead associated with home-based firewalls.
The controller should be placed in a demilitarized zone (DMZ) and the corporate firewall must allow CAPWAP control and data traffic through the firewall to the controller. The general configuration on the firewall is to allow CAPWAP control and CAPWAP management port numbers through the firewall. The UDP 5246 and 5247 ports need to be opened on the firewall for communication between the controller and the AP.
For the most flexible and secure remote teleworker configuration, deploy a dedicated controller pair in a dedicated to the Internet edge DMZ. Traffic from the Internet terminates in the DMZ versus in the internal network, while the remote AP is still directly connected to the internal network.
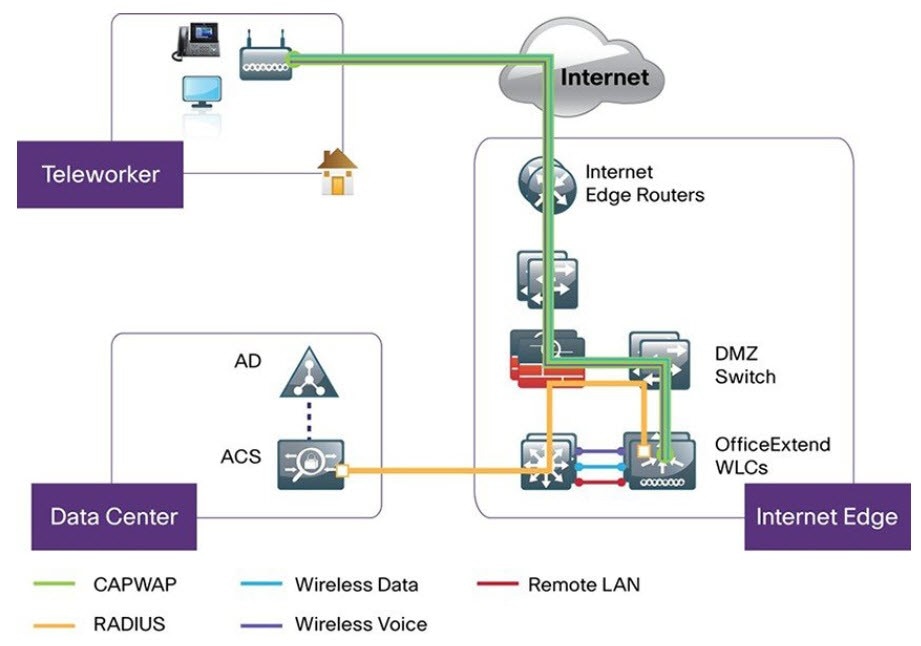
A remote teleworker site is a dedicated site that is used only to manage wireless controllers and remote teleworker access points (APs). To create a remote teleworker site, you need to enable the remote teleworker function on the site. Once enabled, the remote teleworker function cannot be independently disabled for a site, building, or floor within the site's hierarchy. The site can only manage remote teleworker functions.
In a teleworker site, switching is performed centrally from the controller. You cannot configure the network profile for Flex Connect with local switching.
Understand the supported devices that are used in a teleworker deployment.
Make sure that you have a Cisco wireless controller and Cisco APs in your inventory. If not, discover the devices or add them manually. For information, see Discover Your Network or Add a Network Device.
Configure global wireless network settings appropriate for your network. For information, see Configure Global Wireless Settings.
|
Step 1 |
Create a site to manage remote teleworker APs. See Create, Edit and Delete a Site. |
|
Step 2 |
Add buildings and floors. See Add, Edit, and Delete a Building. |
|
Step 3 |
Configure the wireless network settings for the remote teleworker site.
|
|
Step 4 |
Assign the controller to the site. See Add a Device to a Site. |
|
Step 5 |
Assign the APs to the site. See Add a Device to a Site. You can use serial numbers or MAC addresses but not a mixture of both, or you can upload a CSV file. |
|
Step 6 |
In the wireless network settings, add the APs to the authorized APs list. |
|
Step 7 |
Provision the controller. |
|
Step 8 |
After the Cisco Wireless Controller is provisioned, you can provision the APs. |