About Device Management
Use the Firepower Management Center to manage your devices.
About the Firepower Management Center and Device Management
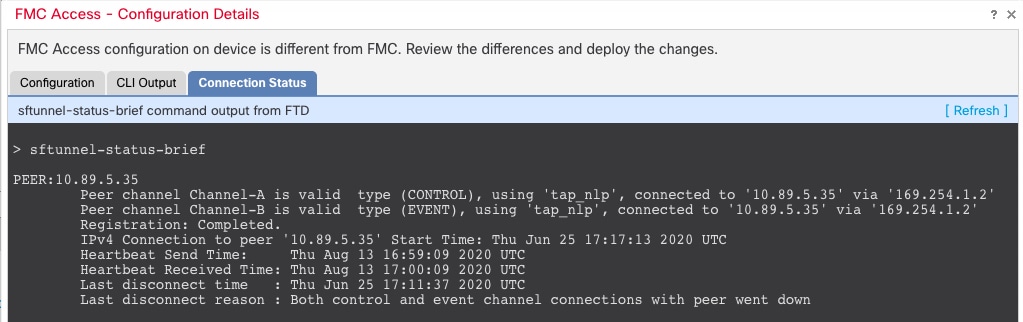
When the Firepower Management Center manages a device, it sets up a two-way, SSL-encrypted communication channel between itself and the device. The Firepower Management Center uses this channel to send information to the device about how you want to analyze and manage your network traffic to the device. As the device evaluates the traffic, it generates events and sends them to the Firepower Management Center using the same channel.
By using the Firepower Management Center to manage devices, you can:
-
configure policies for all your devices from a single location, making it easier to change configurations
-
install various types of software updates on devices
-
push health policies to your managed devices and monitor their health status from the Firepower Management Center
The Firepower Management Center aggregates and correlates intrusion events, network discovery information, and device performance data, allowing you to monitor the information that your devices are reporting in relation to one another, and to assess the overall activity occurring on your network.
You can use a Firepower Management Center to manage nearly every aspect of a device’s behavior.
 Note |
Although a Firepower Management Center can manage devices running certain previous releases as specified in the compatibility matrix available at http://www.cisco.com/c/en/us/support/security/defense-center/products-device-support-tables-list.html, new features are not available to these previous-release devices. |
What Can Be Managed by a Firepower Management Center?
You can use the Firepower Management Center as a central management point in a Firepower System deployment to manage the following devices:
-
ASA FirePOWER modules
-
NGIPSv devices
-
Firepower Threat Defense (physical hardware and virtual)
When you manage a device, information is transmitted between the Firepower Management Center and the device over a secure, SSL-encrypted TCP tunnel.
The following illustration lists what is transmitted between a Firepower Management Center and its managed devices. Note that the types of events and policies that are sent between the appliances are based on the device type.
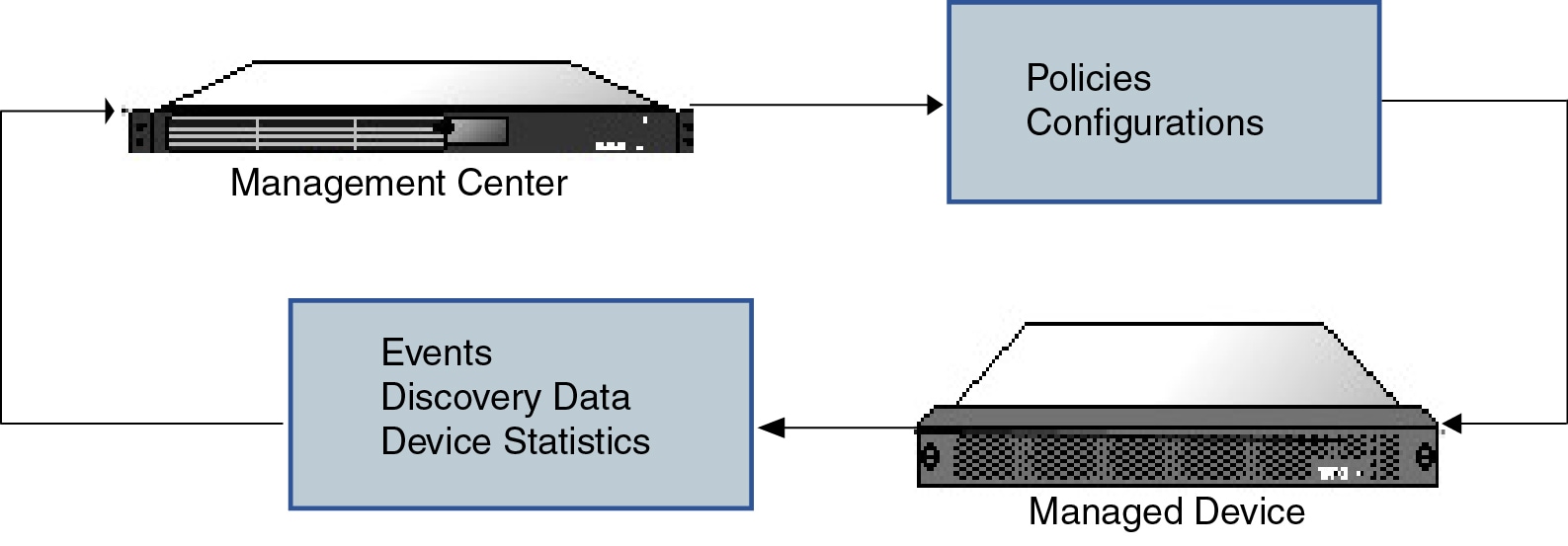
Beyond Policies and Events
In addition to deploying policies to devices and receiving events from them, you can also perform other device-related tasks on the Firepower Management Center.
Backing Up a Device
You cannot create or restore backup files for NGIPSv devices or ASA FirePOWER modules.
When you perform a backup of a physical managed device from the device itself, you back up the device configuration only. To back up configuration data and, optionally, unified files, perform a backup of the device using the managing Firepower Management Center.
To back up event data, perform a backup of the managing Firepower Management Center.
Updating Devices
From time to time, Cisco releases updates to the Firepower System, including:
-
intrusion rule updates, which may contain new and updated intrusion rules
-
vulnerability database (VDB) updates
-
geolocation updates
-
software patches and updates
You can use the Firepower Management Center to install an update on the devices it manages.
About Device Management Interfaces
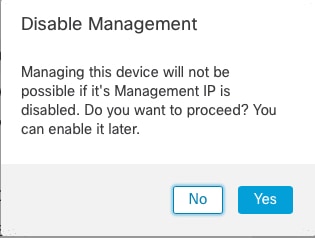
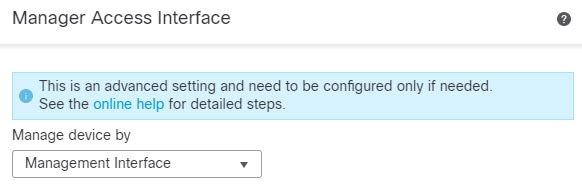
Each device includes a single dedicated Management interface for communicating with the FMC. You can optionally configure the device to use a data interface for management instead of the dedicated Management interface.
You can perform initial setup on the management interface, or on the console port.
Management interfaces are also used to communicate with the Smart Licensing server, to download updates, and to perform other management functions.
Management Interfaces on Managed Devices
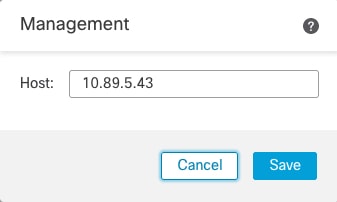
When you set up your device, you specify the FMC IP address that you want to connect to. Both management and event traffic go to this address at initial registration. Note: In some situations, the FMC might establish the initial connection on a different management interface; subsequent connections should use the management interface with the specified IP address.
If the FMC has a separate event-only interface, the managed device sends subsequent event traffic is sent to the FMC event-only interface if the network allows. In addition, some managed-device models include an additional management interface that you can configure for event-only traffic. Note that if you configure a data interface for management, you cannot use separate management and event interfaces. If the event network goes down, then event traffic reverts to the regular management interfaces on the FMC and/or on the managed device.
About Using the FTD Data interface for Management
You can use either the dedicated Management interface or a regular data interface for communication with the FMC. The FMC access on a data interface is useful if you want to manage the Firepower Threat Defense remotely from the outside interface, or you do not have a separate management network.
The FMC access from a data interface has the following limitations:
-
You can only enable manager access on one physical, data interface. You cannot use a subinterface or EtherChannel.
-
This interface cannot be management-only.
-
Routed firewall mode only, using a routed interface.
-
PPPoE is not supported. If your ISP requires PPPoE, you will have to put a router with PPPoE support between the Firepower Threat Defense and the WAN modem.
-
The interface must be in the global VRF only.
-
You cannot use separate management and event-only interfaces.
-
SSH is not enabled by default for data interfaces, so you will have to enable SSH later using the FMC. Because the Management interface gateway will be changed to be the data interfaces, you also cannot SSH to the Management interface from a remote network unless you add a static route for the Management interface using the configure network static-routes command.
-
High Availability is not supported. You must use the Management interface in this case.
Management Interface Support Per Device Model
See the hardware installation guide for your model for the management interface locations.
 Note |
For the Firepower 4100/9300 chassis, the MGMT interface is for chassis management, not for Firepower Threat Defense logical device management. You must configure a separate NIC interface to be of type mgmt (and/or firepower-eventing), and then assign it to the Firepower Threat Defense logical device. |
 Note |
For Firepower Threat Defense on any chassis, the physical management interface is shared between the Diagnostic logical interface, which is useful for SNMP or syslog, and is configured along with data interfaces in the FMC, and the Management logical interface for FMC communication. See Management/Diagnostic Interface for more information. |
See the following table for supported management interfaces on each managed device model.
|
Model |
Management Interface |
Optional Event Interface |
||||
|---|---|---|---|---|---|---|
|
NGIPSv |
eth0 |
No support |
||||
|
ASA FirePOWER services module on the ASA 5508-X, or 5516-X |
eth0
|
No support |
||||
|
ASA FirePOWER services module on the ISA 3000 |
eth0
|
No support |
||||
|
Firepower Threat Defense on the Firepower 1000 |
management0
|
No Support |
||||
|
Firepower Threat Defense on the Firepower 2100 |
management0
|
No Support |
||||
|
Firepower Threat Defense on the Firepower 4100 and 9300 |
management0
|
management1
|
||||
|
Firepower Threat Defense on the ASA 5508-X, or 5516-X |
br1
|
No support |
||||
|
Firepower Threat Defense on the ISA 3000 |
br1
|
No support |
||||
|
Firepower Threat Defense Virtual |
eth0 |
No support |
Network Routes on Device Management Interfaces
Management interfaces (including event-only interfaces) support only static routes to reach remote networks. When you set up your managed device, the setup process creates a default route to the gateway IP address that you specify. You cannot delete this route; you can only modify the gateway address.
 Note |
The routing for management interfaces is completely separate from routing that you configure for data interfaces. If you configure a data interface for management instead of using the dedicated Management interface, traffic is routed over the backplane to use the data routing table. The information in this section does not apply. |
You can configure multiple management interfaces on some platforms (a management interface and an event-only interface). The default route does not include an egress interface, so the interface chosen depends on the gateway address you specify, and which interface's network the gateway belongs to. In the case of multiple interfaces on the default network, the device uses the lower-numbered interface as the egress interface.
At least one static route is recommended per management interface to access remote networks. We recommend placing each interface on a separate network to avoid potential routing problems, including routing problems from other devices to the FTD. If you do not experience problems with interfaces on the same network, then be sure to configure static routes correctly. For example, both management0 and management1 are on the same network, but the FMC management and event interfaces are on different networks. The gateway is 192.168.45.1. If you want management1 to connect to the FMC's event-only interface at 10.6.6.1/24, you can create a static route for 10.6.6.0/24 through management1 with the same gateway of 192.168.45.1. Traffic to 10.6.6.0/24 will hit this route before it hits the default route, so management1 will be used as expected.
Another example includes separate management and event-only interfaces on both the FMC and the managed device. The event-only interfaces are on a separate network from the management interfaces. In this case, add a static route through the event-only interface for traffic destined for the remote event-only network, and vice versa.
NAT Environments
Network address translation (NAT) is a method of transmitting and receiving network traffic through a router that involves reassigning the source or destination IP address. The most common use for NAT is to allow private networks to communicate with the internet. Static NAT performs a 1:1 translation, which does not pose a problem for FMC communication with devices, but port address translation (PAT) is more common. PAT lets you use a single public IP address and unique ports to access the public network; these ports are dynamically assigned as needed, so you cannot initiate a connection to a device behind a PAT router.
Normally, you need both IP addresses (along with a registration key) for both routing purposes and for authentication: the FMC specifies the device IP address when you add a device, and the device specifies the FMC IP address. However, if you only know one of the IP addresses, which is the minimum requirement for routing purposes, then you must also specify a unique NAT ID on both sides of the connection to establish trust for the initial communication and to look up the correct registration key. The FMC and device use the registration key and NAT ID (instead of IP addresses) to authenticate and authorize for initial registration.
For example, you add a device to the FMC, and you do not know the device IP address (for example, the device is behind a PAT router), so you specify only the NAT ID and the registration key on the FMC; leave the IP address blank. On the device, you specify the FMC IP address, the same NAT ID, and the same registration key. The device registers to the FMC's IP address. At this point, the FMC uses the NAT ID instead of IP address to authenticate the device.
Although the use of a NAT ID is most common for NAT environments, you might choose to use the NAT ID to simplify adding many devices to the FMC. On the FMC, specify a unique NAT ID for each device you want to add while leaving the IP address blank, and then on each device, specify both the FMC IP address and the NAT ID. Note: The NAT ID must be unique per device.
The following example shows three devices behind a PAT IP address. In this case, specify a unique NAT ID per device on both the FMC and the devices, and specify the FMC IP address on the devices.
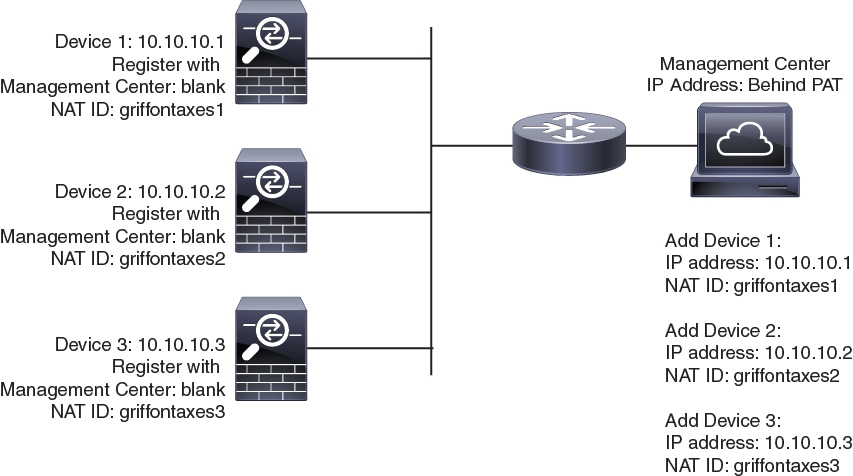
The following example shows the FMC behind a PAT IP address. In this case, specify a unique NAT ID per device on both the FMC and the devices, and specify the device IP addresses on the FMC.
Management and Event Traffic Channel Examples
 Note |
If you use a data interface for management on an FTD, you cannot use separate management and event interfaces for that device. |
The following example shows the Firepower Management Center and managed devices using only the default management interfaces.
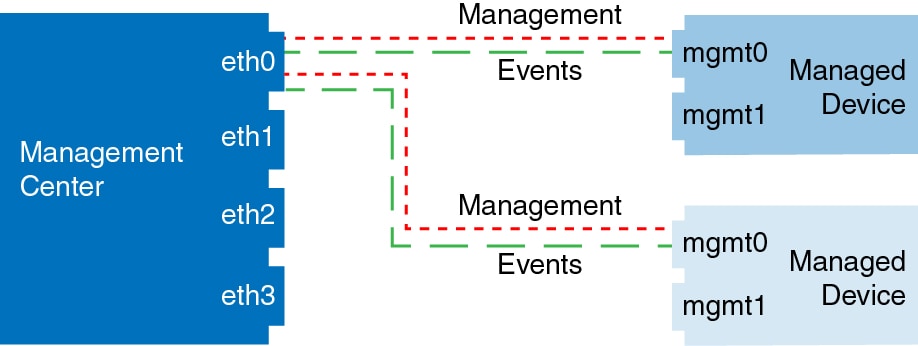
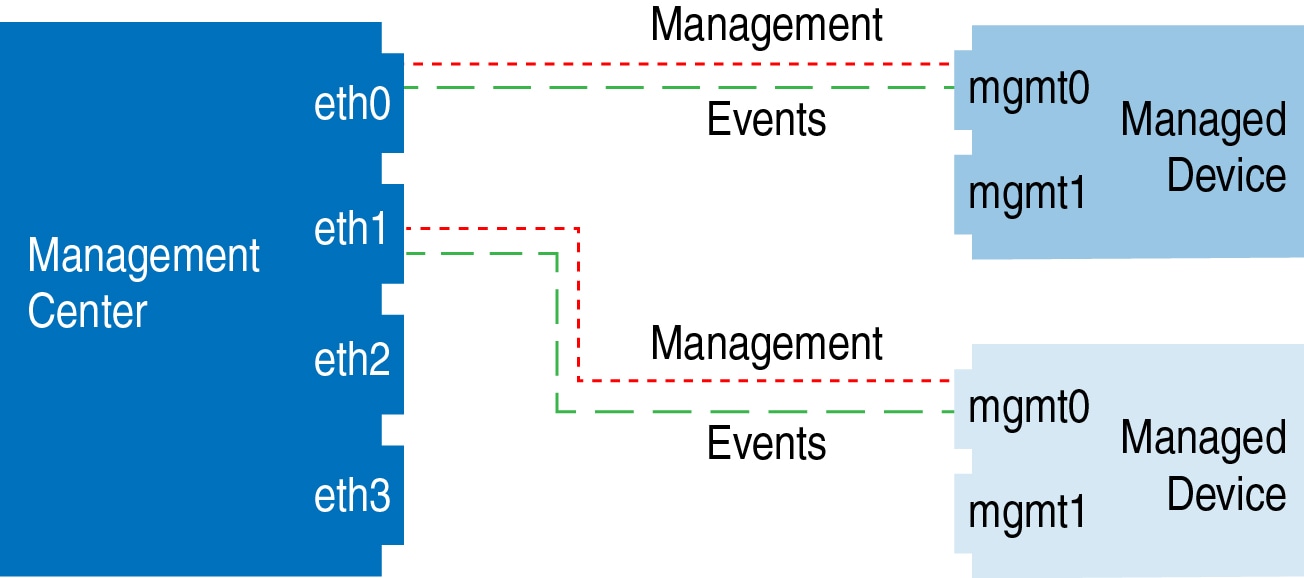
The following example shows the Firepower Management Center using separate management interfaces for devices; and each managed device using 1 management interface.
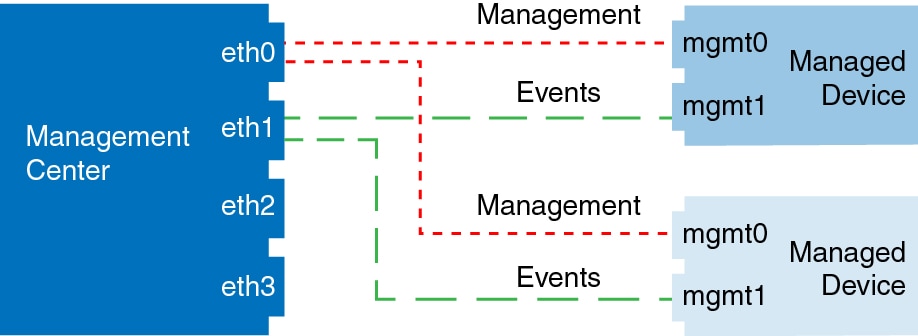
The following example shows the Firepower Management Center and managed devices using a separate event interface.
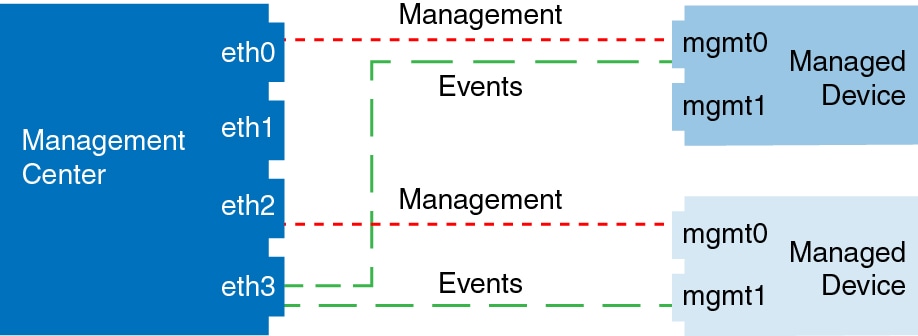
The following example shows a mix of multiple management interfaces and a separate event interface on the Firepower Management Center and a mix of managed devices using a separate event interface, or using a single management interface.
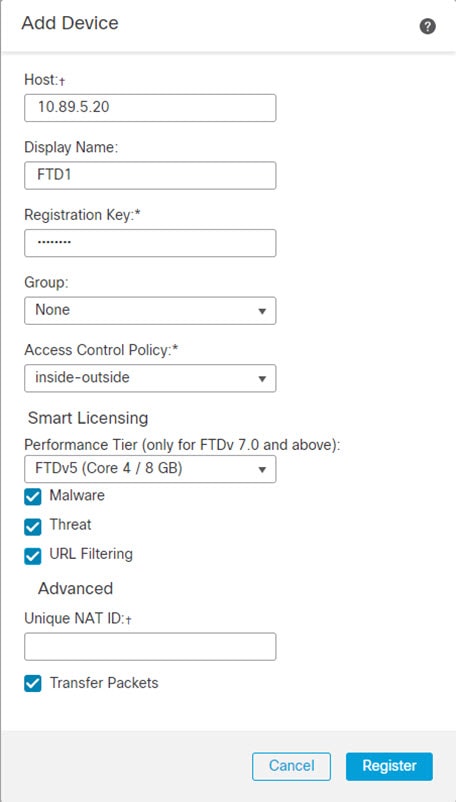
 )
)
 )
) )
) )
)

 )
)








 )
) )
)

 )
)

 Feedback
Feedback