About User Accounts for Devices
You can add custom user accounts on managed devices, either as internal users or, for the FTD, as external users on a LDAP or RADIUS server. Each managed device maintains separate user accounts. For example, when you add a user to the FMC, that user only has access to the FMC; you cannot then use that username to log directly into a managed device. You must separately add a user on the managed device.
Internal and External Users
Managed devices support two types of users:
-
Internal user—The device checks a local database for user authentication. For more information about internal users, see Add an Internal User at the CLI. The FTD, NGIPSv, and ASA FirePOWER support internal users.
-
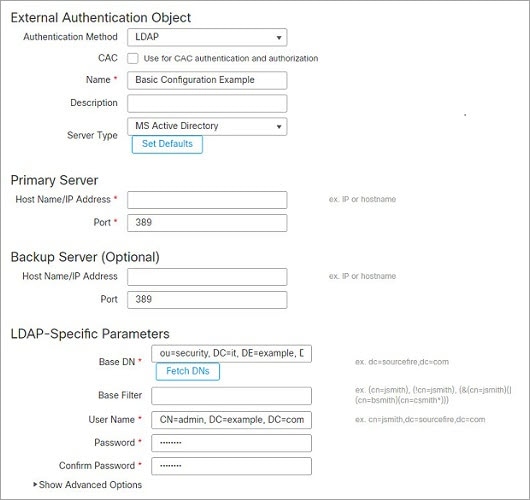
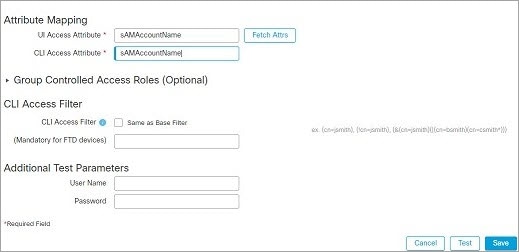
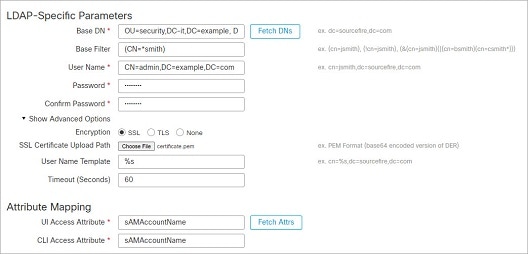
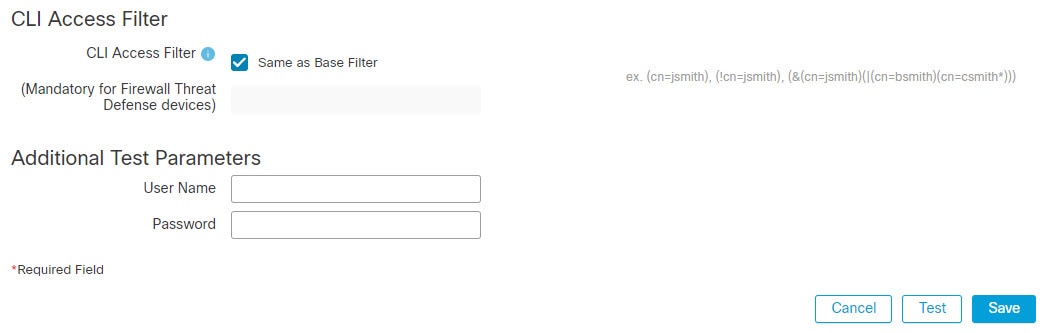
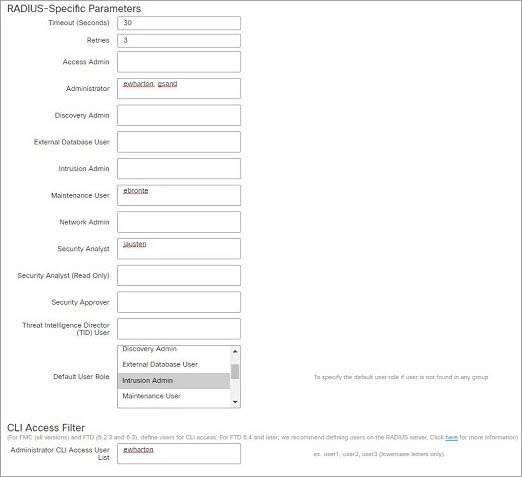
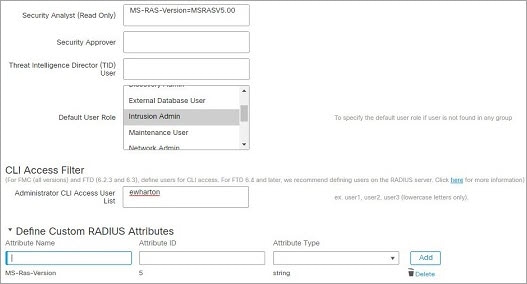
External user (FTD only)—If the user is not present in the local database, the system queries an external LDAP or RADIUS authentication server. For more information about external users, see Configure External Authentication for the FTD. Only the FTD supports external users.
CLI Access
Firepower devices include a Firepower CLI that runs on top of Linux. You can create internal users on devices using the CLI. You can establish external users on FTD devices using the FMC. For detailed information about the management UIs, see Firepower System User Interfaces.
 Caution |
Users with CLI Config level access can access the Linux shell
using the expert command,
and obtain
|
CLI User Roles
On managed devices, user access to commands in the CLI depends on the role you assign.
- None
-
The user cannot log into the device on the command line.
- Config
-
The user can access all commands, including configuration commands. Exercise caution in assigning this level of access to users.
- Basic
-
The user can access non-configuration commands only. Only internal users and Firepower Threat Defense external RADIUS users support the Basic role.

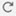 )
)

 Feedback
Feedback