About TLS/SSL Oversubscription
TLS/SSL oversubscription is a state where a managed device is overloaded with TLS/SSL traffic. Any managed device can experience TLS/SSL oversubscription but only managed devices that support TLS crypto acceleration provide a configurable way to handle it.
When a managed device with TLS crypto acceleration enabled is oversubscribed, any packet received by the managed device is acted on according to the setting for Handshake Errors in the SSL policy's Undecryptable Actions:
-
Inherit default action
-
Do not decrypt
-
Block
-
Block with reset
If the setting for Handshake Errors in the SSL policy's Undecryptable Actions is Do Not decrypt and the associated access control policy is configured to inspect the traffic, inspection occurs; decryption does not occur.
Troubleshoot TLS/SSL Oversubscription
If your managed device has TLS crypto acceleration enabled, you can view connection events to determine whether or not the devices are experiencing SSL oversubscription. You must add at least the SSL Flow Flags event to the table view of connection events.
Before you begin
-
Configure an SSL policy with a setting for Handshake Errors on Undecryptable Actions page.
For more information, see Set Default Handling for Undecryptable Traffic.
-
Enable logging for your SSL rules as discussed in Logging Decryptable Connections with SSL Rules.
Procedure
|
Step 1 |
If you haven't done so already, log in to the Firepower Management Center. |
||||||
|
Step 2 |
Click . |
||||||
|
Step 3 |
Click Table View of Connection Events. |
||||||
|
Step 4 |
Click x on any column in the connection events table to add additional columns for at least SSL Flow Flags and SSL Flow Messages.
The following example shows adding the SSL Actual Action, SSL Flow Error, SSL Flow Flags, SSL Flow Messages, SSL Policy, and SSL Rule columns to the table of connection events. (Look in the Disabled Columns section of the dialog box.)  The columns are added in the order discussed in Connection and Security Intelligence Event Fields. |
||||||
|
Step 5 |
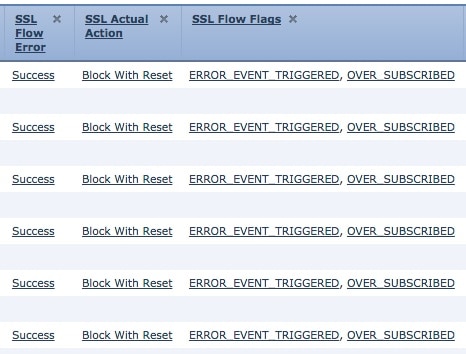
Click Apply. The following figure shows an example.
|
||||||
|
Step 6 |
If TLS/SSL oversubscription is occurring, log in to the managed device and enter any of the following commands:
|


 Feedback
Feedback