Rate Filter Overview
|
Type |
Module (basic) |
|
Usage |
Context |
|
Instance Type |
Singleton |
|
Enabled |
|
Rate-based attacks attempt to overwhelm a network or host by sending excessive traffic to a network or host, causing it to slow down or deny legitimate requests. You can use rate-based prevention to change the action of an intrusion rule in response to excessive matches on that rule.
The rate_filter detects when too many matches for a rule occur
within a given interval. You can use this feature
on managed devices deployed inline to block rate-based attacks for a specified time,
then revert to a rule state where rule matches only generate events and do not drop
traffic.
You can configure the rate_filter to respond to any intrusion
rule, but the rule you specify must be enabled for rate_filter to
detect an attack and respond. For example, to establish a defense against a DDOS/SYN
flood attack, enable rule 135:1 (TCP SYN received), and configure the
rate_filter to alert on excessive triggers of rule
135:1.
Rate-based attack prevention identifies abnormal traffic patterns and attempts to minimize the impact of that traffic on legitimate requests. You can identify excessive rule matches in traffic going to a particular destination IP address or addresses or coming from a particular source IP address or addresses. You can also respond to excessive matches for a particular rule across all detected traffic.
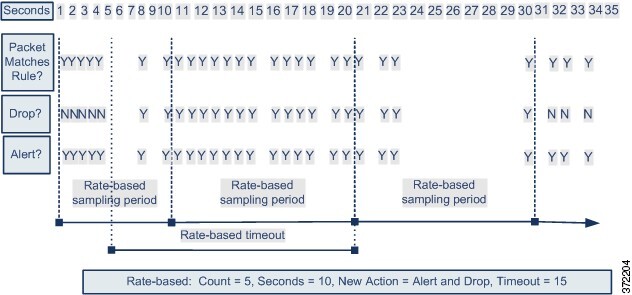
The following diagram shows an example where an attacker is attempting to access a host. Repeated attempts to find a password trigger a rule which has rate-based attack prevention configured. The rate-based settings change the rule attribute to Drop and Generate Events after rule matches occur five times in a 10-second span. The new rule attribute times out after 15 seconds.
After the timeout, note that packets are still dropped in the rate-based sampling period that follows. If the sampled rate is above the threshold in the current or previous sampling period, the new action continues. The new action reverts to Generate Events only after a sampling period completes where the sampled rate was below the threshold rate.
You can define multiple rate-based filters on the same rule as well as on different rules. In an intrusion policy with multiple rate-based filters defined, the first filter listed in the policy has the highest priority. When two rate-based filter actions conflict, the action of the first rate-based filter is carried out.
The configuration parameters you set for the rate_filter apply
to all traffic throughout your deployment. However, the system maintains a separate
counter for the number of matches within the sampling period for each unique connection
your system monitors. The system also applies changes to an action on a per-connection
basis.
 Note |
Rate-based actions cannot enable disabled rules or drop traffic that matches disabled rules. |
 Feedback
Feedback