Restrictions on SLAs
This section lists the restrictions on SLAs.
The following are restrictions on IP SLAs network performance measurement:
-
The device does not support VoIP service levels using the gatekeeper registration delay operations measurements.
-
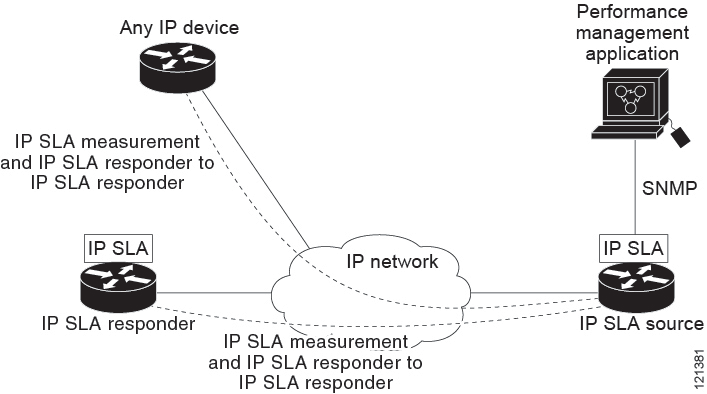
Only a Cisco IOS device can be a source for a destination IP SLAs responder.
-
You cannot configure the IP SLAs responder on non-Cisco devices and Cisco IOS IP SLAs can send operational packets only to services native to those devices.
-
Switches running the IP base or LAN base feature set support only IP SLAs responder functionality and must be configured with another device that supports full IP SLAs functionality

 Feedback
Feedback