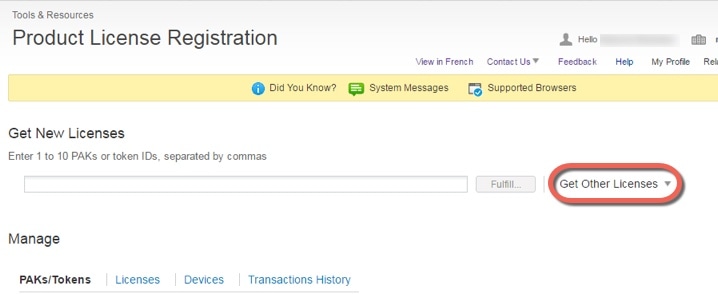
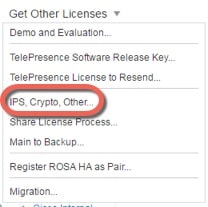
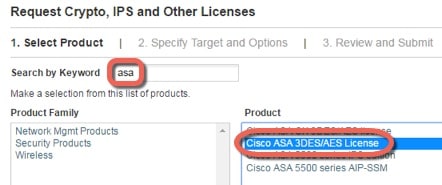
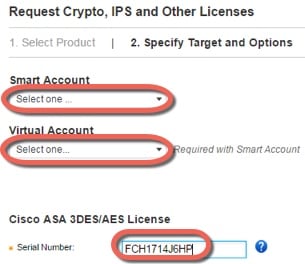
About PAK Licenses
A license specifies the options that are enabled on a given ASA. It is represented by an activation key that is a 160-bit (5 32-bit words or 20 bytes) value. This value encodes the serial number (an 11 character string) and the enabled features.
Preinstalled License
By default, your ASA ships with a license already installed. This license might be the Base License, to which you want to add more licenses, or it might already have all of your licenses installed, depending on what you ordered and what your vendor installed for you.
Permanent License
You can have one permanent activation key installed. The permanent activation key includes all licensed features in a single key. If you also install time-based licenses, the ASA combines the permanent and time-based licenses into a running license.
Time-Based Licenses
In addition to permanent licenses, you can purchase time-based licenses or receive an evaluation license that has a time-limit. For example, you might buy a time-based Secure Client Premium license to handle short-term surges in the number of concurrent SSL VPN users.
Time-Based License Activation Guidelines
-
You can install multiple time-based licenses, including multiple licenses for the same feature. However, only one time-based license per feature can be active at a time. The inactive license remains installed, and ready for use. For example, if you install a 1000-session Secure Client Premium license, and a 2500-session Secure Client Premium license, then only one of these licenses can be active.
-
If you activate an evaluation license that has multiple features in the key, then you cannot also activate another time-based license for one of the included features.
How the Time-Based License Timer Works
-
The timer for the time-based license starts counting down when you activate it on the ASA.
-
If you stop using the time-based license before it times out, then the timer halts. The timer only starts again when you reactivate the time-based license.
-
If the time-based license is active, and you shut down the ASA, then the timer stops counting down. The time-based license only counts down when the ASA is running. The system clock setting does not affect the license; only ASA uptime counts towards the license duration.
How Permanent and Time-Based Licenses Combine
When you activate a time-based license, then features from both permanent and time-based licenses combine to form the running license. How the permanent and time-based licenses combine depends on the type of license. The following table lists the combination rules for each feature license.
 Note |
Even when the permanent license is used, if the time-based license is active, it continues to count down. |
|
Time-Based Feature |
Combined License Rule |
|---|---|
|
Secure Client Premium Sessions |
The higher value is used, either time-based or permanent. For example, if the permanent license is 1000 sessions, and the time-based license is 2500 sessions, then 2500 sessions are enabled. Typically, you will not install a time-based license that has less capability than the permanent license, but if you do so, then the permanent license is used. |
|
Unified Communications Proxy Sessions |
The time-based license sessions are added to the permanent sessions, up to the platform limit. For example, if the permanent license is 2500 sessions, and the time-based license is 1000 sessions, then 3500 sessions are enabled for as long as the time-based license is active. |
|
All Others |
The higher value is used, either time-based or permanent. For licenses that have a status of enabled or disabled, then the license with the enabled status is used. For licenses with numerical tiers, the higher value is used. Typically, you will not install a time-based license that has less capability than the permanent license, but if you do so, then the permanent license is used. |
Stacking Time-Based Licenses
In many cases, you might need to renew your time-based license and have a seamless transition from the old license to the new one. For features that are only available with a time-based license, it is especially important that the license not expire before you can apply the new license. The ASA allows you to stack time-based licenses so that you do not have to worry about the license expiring or about losing time on your licenses because you installed the new one early.
When you install an identical time-based license as one already installed, then the licenses are combined, and the duration equals the combined duration.
For example:
-
You install an 8-week 1000-session Secure Client Premium license, and use it for 2 weeks (6 weeks remain).
-
You then install another 8-week 1000-session license, and the licenses combine to be 1000-sessions for 14 weeks (8 weeks plus 6 weeks).
If the licenses are not identical (for example, a 1000-session Secure Client Premium license vs. a 2500-session license), then the licenses are not combined. Because only one time-based license per feature can be active, only one of the licenses can be active.
Although non-identical licenses do not combine, when the current license expires, the ASA automatically activates an installed license of the same feature if available.
Time-Based License Expiration
When the current license for a feature expires, the ASA automatically activates an installed license of the same feature if available. If there are no other time-based licenses available for the feature, then the permanent license is used.
If you have more than one additional time-based license installed for a feature, then the ASA uses the first license it finds; which license is used is not user-configurable and depends on internal operations. If you prefer to use a different time-based license than the one the ASA activated, then you must manually activate the license you prefer.
For example, you have a time-based 2500-session Secure Client Premium license (active), a time-based 1000-session Secure Client Premium license (inactive), and a permanent 500-session Secure Client Premium license. While the 2500-session license expires, the ASA activates the 1000-session license. After the 1000-session license expires, the ASA uses the 500-session permanent license.
License Notes
The following sections include additional information about licenses.
Secure Client Advantage, Secure Client Premier, and Secure Client VPN Only Licenses
The Secure Client Advantage or Premier license is a multi-use license that you can apply to multiple ASAs, all of which share a user pool as specified by the license. TheSecure Client VPN Only license applies to a specific ASA. See https://www.cisco.com/go/license, and assign the PAK separately to each ASA. When you apply the resulting activation key to an ASA, it toggles on the VPN features to the maximum allowed, but the actual number of unique users across all ASAs sharing the license should not exceed the license limit. For more information, see:
 Note |
The Secure Client Premier license is the only Secure Client Premier license supported for multiple context mode. Moreover, in multiple context mode, this license must be applied to each unit in a failover pair; the license is not aggregated. |
Other VPN License
Other VPN peers include the following VPN types:
-
IPsec remote access VPN using IKEv1
-
IPsec site-to-site VPN using IKEv1
-
IPsec site-to-site VPN using IKEv2
This license is included in the Base license.
Total VPN Sessions Combined, All Types
-
The Total VPN Peers is the maximum VPN peers allowed of both Secure Client and Other VPN peers combined. For example, if the total is 1000, you can allow 500 Secure Client and 500 Other VPN peers simultaneously; or 700 Secure Client and 300 Other VPN; or use all 1000 for Secure Client. If you exceed the total VPN peers, you can overload the ASA, so be sure to size your network appropriately.
VPN Load Balancing
VPN load balancing requires a Strong Encryption (3DES/AES) License.
Legacy VPN Licenses
Refer to the Supplemental end User License Agreement for Secure Client for all relevant information on licensing.
 Note |
The Secure Client Premier license is the only Secure Client license supported for multiple context mode; you cannot use the default or legacy license. |
Encryption License
The DES license cannot be disabled. If you have the 3DES license installed, DES is still available. To prevent the use of DES when you want to only use strong encryption, be sure to configure any relevant commands to use only strong encryption.
Total TLS Proxy Sessions
Each TLS proxy session for Encrypted Voice Inspection is counted against the TLS license limit.
Other applications that use TLS proxy sessions do not count toward the TLS limit, for example, Mobility Advantage Proxy (which does not require a license).
Some applications might use multiple sessions for a connection. For example, if you configure a phone with a primary and backup Cisco Unified Communications Manager, there are 2 TLS proxy connections.
You independently set the TLS proxy limit using the tls-proxy maximum-sessions command or in ASDM, using the Configuration > Firewall > Unified Communications > TLS Proxy pane. To view the limits of your model, enter the tls-proxy maximum-sessions ? command. When you apply a TLS proxy license that is higher than the default TLS proxy limit, the ASA automatically sets the TLS proxy limit to match the license. The TLS proxy limit takes precedence over the license limit; if you set the TLS proxy limit to be less than the license, then you cannot use all of the sessions in your license.
 Note |
For license part numbers ending in “K8” (for example, licenses under 250 users), TLS proxy sessions are limited to 1000. For license part numbers ending in “K9” (for example, licenses 250 users or larger), the TLS proxy limit depends on the configuration, up to the model limit. K8 and K9 refer to whether the license is restricted for export: K8 is unrestricted, and K9 is restricted. If you clear the configuration (using the clear configure all command, for example), then the TLS proxy limit is set to the default for your model; if this default is lower than the license limit, then you see an error message to use the tls-proxy maximum-sessions command to raise the limit again (in ASDM, use the TLS Proxy pane). If you use failover and enter the write standby command or in ASDM, use File > Save Running Configuration to Standby Unit on the primary unit to force a configuration synchronization, the clear configure all command is generated on the secondary unit automatically, so you may see the warning message on the secondary unit. Because the configuration synchronization restores the TLS proxy limit set on the primary unit, you can ignore the warning. |
You might also use SRTP encryption sessions for your connections:
-
For K8 licenses, SRTP sessions are limited to 250.
-
For K9 licenses, there is no limit.
 Note |
Only calls that require encryption/decryption for media are counted toward the SRTP limit; if passthrough is set for the call, even if both legs are SRTP, they do not count toward the limit. |
VLANs, Maximum
For an interface to count against the VLAN limit, you must assign a VLAN to it.
Shared Secure Client Premium Licenses (AnyConnect 3 and Earlier)
 Note |
The shared license feature on the ASA is not supported with AnyConnect 4 and later licensing. Secure Client licenses are shared and no longer require a shared server or participant license. |
A shared license lets you purchase a large number of Secure Client Premium sessions and share the sessions as needed among a group of ASAs by configuring one of the ASAs as a shared licensing server, and the rest as shared licensing participants.
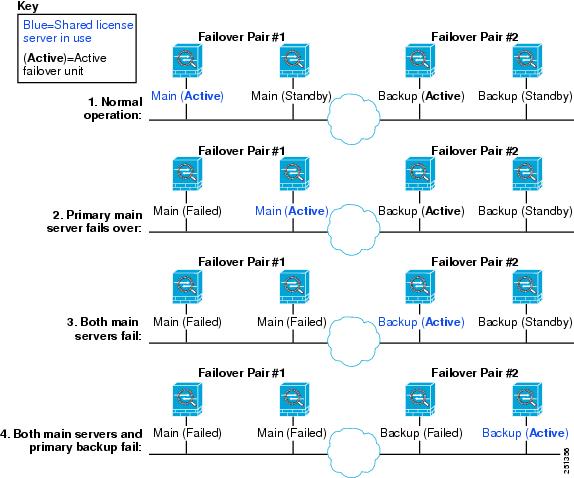
Failover
With some exceptions, failover units do not require the same license on each unit. For earlier versions, see the licensing document for your version.
Failover License Requirements and Exceptions
|
Model |
License Requirement |
||
|---|---|---|---|
|
ISA 3000 |
Security Plus license on both units.
|
 Note |
A valid permanent key is required; in rare instances on the ISA 3000, your PAK authentication key can be removed. If your key consists of all 0’s, then you need to reinstall a valid authentication key before failover can be enabled. |
How Failover Licenses Combine
For failover pairs, the licenses on each unit are combined into a single running cluster license. If you buy separate licenses for each unit, then the combined license uses the following rules:
-
For licenses that have numerical tiers, such as the number of sessions, the values from each unit’s licenses are combined up to the platform limit. If all licenses in use are time-based, then the licenses count down simultaneously.
For example, for failover:
-
You have two ASAs with 10 TLS Proxy sessions installed on each; the licenses will be combined for a total of 20 TLS Proxy sessions.
-
You have an ASA with 1000 TLS Proxy sessions, and another with 2000 sessions; because the platform limit is 2000, the combined license allows 2000 TLS Proxy sessions.
-
-
For licenses that have a status of enabled or disabled, then the license with the enabled status is used.
-
For time-based licenses that are enabled or disabled (and do not have numerical tiers), the duration is the combined duration of all licenses. The primary/control unit counts down its license first, and when it expires, the secondary/data unit(s) start counting down its license, and so on.
Loss of Communication Between Failover Units
If the units lose communication for more than 30 days, then each unit reverts to the license installed locally. During the 30-day grace period, the combined running license continues to be used by all units.
If you restore communication during the 30-day grace period, then for time-based licenses, the time elapsed is subtracted from the primary/control license; if the primary/control license becomes expired, only then does the secondary/data license start to count down.
If you do not restore communication during the 30-day period, then for time-based licenses, time is subtracted from all unit licenses, if installed. They are treated as separate licenses and do not benefit from the combined license. The time elapsed includes the 30-day grace period.
Upgrading Failover Pairs
Because failover pairs do not require the same license on both units, you can apply new licenses to each unit without any downtime. If you apply a permanent license that requires a reload, then you can fail over to the other unit while you reload. If both units require reloading, then you can reload them separately so that you have no downtime.
No Payload Encryption Models
You can purchase some models with No Payload Encryption. For export to some countries, payload encryption cannot be enabled on the ASA series. The ASA software senses a No Payload Encryption model, and disables the following features:
-
Unified Communications
-
VPN
You can still install the Strong Encryption (3DES/AES) license for use with management connections. For example, you can use ASDM HTTPS/SSL, SSHv2, Telnet and SNMPv3.
When you view the license, VPN and Unified Communications licenses will not be listed.
Licenses FAQ
- Can I activate multiple time-based licenses?
-
Yes. You can use one time-based license per feature at a time.
- Can I “stack” time-based licenses so that when the time limit runs out, it will automatically use the next license?
-
Yes. For identical licenses, the time limit is combined when you install multiple time-based licenses. For non-identical licenses (for example, a 1000-session Secure Client Premium license and a 2500-session license), the ASA automatically activates the next time-based license it finds for the feature.
- Can I install a new permanent license while maintaining an active time-based license?
-
Yes. Activating a permanent license does not affect time-based licenses.
- For failover, can I use a shared licensing server as the primary unit, and the shared licensing backup server as the secondary unit?
-
No. The secondary unit has the same running license as the primary unit; in the case of the shared licensing server, they require a server license. The backup server requires a participant license. The backup server can be in a separate failover pair of two backup servers.
- Do I need to buy the same licenses for the secondary unit in a failover pair?
-
No. Starting with Version 8.3(1), you do not have to have matching licenses on both units. Typically, you buy a license only for the primary unit; the secondary unit inherits the primary license when it becomes active. In the case where you also have a separate license on the secondary unit (for example, if you purchased matching licenses for pre-8.3 software), the licenses are combined into a running failover cluster license, up to the model limits.
- Can I use a time-based or permanent Secure Client Premium license in addition to a shared AnyConnect Premium license?
-
Yes. The shared license is used only after the sessions from the locally installed license (time-based or permanent) are used up.

Note
On the shared licensing server, the permanent Secure Client Premium license is not used; you can however use a time-based license at the same time as the shared licensing server license. In this case, the time-based license sessions are available for local Secure Client Premium sessions only; they cannot be added to the shared licensing pool for use by participants.
 Feedback
Feedback