- Title Page
- Introduction & Preface
- Logging into the FireSIGHT System
- Using Objects and Security Zones
- Managing Devices
- Setting Up an IPS Device
- Setting Up Virtual Switches
- Setting Up Virtual Routers
- Setting Up Aggregate Interfaces
- Setting Up Hybrid Interfaces
- Using Gateway VPNs
- Using NAT Policies
- Getting Started with Access Control Policies
- Blacklisting Using Security Intelligence IP Address Reputation
- Tuning Traffic Flow Using Access Control Rules
- Controlling Traffic with Network-Based Rules
- Controlling Traffic with Reputation-Based Rules
- Controlling Traffic Based on Users
- Controlling Traffic Using Intrusion and File Policies
- Understanding Traffic Decryption
- Getting Started with SSL Policies
- Getting Started with SSL Rules
- Tuning Traffic Decryption Using SSL Rules
- Understanding Intrusion and Network Analysis Policies
- Using Layers in Intrusion and Network Analysis Policies
- Customizing Traffic Preprocessing
- Getting Started with Network Analysis Policies
- Using Application Layer Preprocessors
- Configuring SCADA Preprocessing
- Configuring Transport & Network Layer Preprocessing
- Tuning Preprocessing in Passive Deployments
- Getting Started with Intrusion Policies
- Tuning Intrusion Rules
- Tailoring Intrusion Protection to Your Network Assets
- Detecting Specific Threats
- Limiting Intrusion Event Logging
- Understanding and Writing Intrusion Rules
- Blocking Malware and Prohibited Files
- Logging Connections in Network Traffic
- Working with Connection & Security Intelligence Data
- Analyzing Malware and File Activity
- Working with Intrusion Events
- Handling Incidents
- Configuring External Alerting
- Configuring External Alerting for Intrusion Rules
- Introduction to Network Discovery
- Enhancing Network Discovery
- Configuring Active Scanning
- Using the Network Map
- Using Host Profiles
- Working with Discovery Events
- Configuring Correlation Policies and Rules
- Using the FireSIGHT System as a Compliance Tool
- Creating Traffic Profiles
- Configuring Remediations
- Using Dashboards
- Using the Context Explorer
- Working with Reports
- Understanding and Using Workflows
- Using Custom Tables
- Searching for Events
- Managing Users
- Scheduling Tasks
- Managing System Policies
- Configuring Appliance Settings
- Licensing the FireSIGHT System
- Updating System Software
- Monitoring the System
- Using Health Monitoring
- Auditing the System
- Using Backup and Restore
- Specifying User Preferences
- Importing and Exporting Configurations
- Purging Discovery Data from the Database
- Viewing the Status of Long-Running Tasks
- Command Line Reference
- Security, Internet Access, and Communication Ports
- Third-Party Products
- glossary
- Understanding Connection and Security Intelligence Data
- Viewing Connection and Security Intelligence Data
- Working with Connection Graphs
- Changing the Graph Type
- Selecting Datasets
- Viewing Information About Aggregated Connection Data
- Manipulating a Connection Graph on a Workflow Page
- Drilling Down Through Connection Data Graphs
- Recentering and Zooming on Line Graphs
- Selecting Data to Graph
- Detaching Connection Graphs
- Exporting Connection Data
- Working with Connection and Security Intelligence Data Tables
- Searching for Connection and Security Intelligence Data
- Viewing the Connection Summary Page
Working with Connection & Security Intelligence Data
As managed devices monitor traffic generated by the hosts on your network, they can generate logs of the connections they detect. Various settings in access control and SSL policies give you granular control over which connections you log, when you log them, and where you store the data. In most cases, you can log a connection at its beginning or its end, or both.
When you log a connection, the system generates a connection event . You can also log a special kind of connection event, called a Security Intelligence event , whenever a connection is blacklisted (blocked) or monitored by the reputation-based Security Intelligence feature.
Connection logs, called connection events , contain data about the detected sessions. You should log connections according to the security and compliance needs of your organization; you can log any connection except those that are fast-pathed at the device level before they reach access control.
In addition to the logging that you configure, the system automatically logs most connections where the system detects a prohibited file, malware, or intrusion attempt. Unless you disable connection event storage entirely, the system saves these end-of-connection events to the Defense Center database for further analysis. For detailed information on configuring connection logging, see Logging Connections in Network Traffic.

Note Although you can log connections using any appliance and license, the information available for any individual connection or Security Intelligence event depends on several factors, including licenses. For more information, see License and Model Requirements for Connection Logging.
To supplement the connection data gathered by your managed devices, you can use records generated by NetFlow-enabled devices to generate connection events. This is especially useful if you have NetFlow-enabled devices deployed on networks that your FireSIGHT System managed devices cannot monitor.

Note Because NetFlow data collection is not linked to access control, you do not have granular control over which NetFlow connections you want to log. FireSIGHT System managed devices detect records exported by NetFlow-enabled devices, generate unidirectional end-of-connection events based on the data in those records, and finally send those events to the Defense Center to be logged in the database. NetFlow records cannot generate Security Intelligence events, nor be logged to an external server. For more information, see Understanding NetFlow.
For more information on working with connection and Security Intelligence events, see:
Understanding Connection and Security Intelligence Data
Connection logs, called connection events , contain data about the detected sessions. The information available for any individual connection event depends on several factors, but in general includes:
- basic connection properties: timestamp, source and destination IP address, ingress and egress zones, the device that handled the connection, and so on
- additional connection properties discovered or inferred by the system: applications, requested URLs, or users associated with the connection, and so on
- metadata about why the connection was logged: which access control rule (or other configuration) in which policy handled the traffic, whether the connection was allowed or blocked, details about encrypted and decrypted connections, and so on
Various settings in access control and SSL policies give you granular control over which connections you log, when you log them, and where you store the data. You can log any connection that your access control and SSL policies can successfully handle, which may require specific appliance models or licensed capabilities. You can enable connection logging in the following situations:
- when a connection is blacklisted (blocked) or monitored by the reputation-based Security Intelligence feature
- when an encrypted session is handled by an SSL policy
- when a connection is handled by an access control rule or the access control default action
In addition to the logging that you configure, the system automatically logs most connections where the system detects a prohibited file, malware, or intrusion attempt. Unless you disable connection event storage entirely using the system policy, regardless of your other logging configurations, the system saves these end-of-connection events to the Defense Center database for further analysis.
Also, when you enable Security Intelligence logging, blacklist matches automatically generate Security Intelligence events as well as connection events. A Security Intelligence event is a special kind of connection event that you can view and analyze separately, and that is also stored and pruned separately. For detailed information on configuring connection logging, including Security Intelligence blacklisting decisions, see Logging Connections in Network Traffic.

Tip General information about connection events also pertains to Security Intelligence events, unless otherwise noted. For more information on Security Intelligence, see Blacklisting Using Security Intelligence IP Address Reputation.
The following sections provide additional details on the kinds of information available about detected connections:
- Understanding Connection Summaries
- Understanding Connection and Security Intelligence Data Fields
- Information Available in Connection and Security Intelligence Events
Understanding Connection Summaries
The FireSIGHT System aggregates connection data collected over five-minute intervals into connection summaries, which the system uses to generate connection graphs and traffic profiles. Optionally, you can create custom workflows based on connection summary data, which you use in the same way as you use workflows based on individual connection events.
Note that there are no connection summaries specifically for Security Intelligence events, although corresponding end-of-connection events can be aggregated into connection summary data.
To be aggregated, multiple connections must:
- represent the end of connections
- have the same source and destination IP addresses, and use the same port on the responder (destination) host
- use the same protocol (TCP or UDP)
- use the same application protocol
- either be detected by the same Cisco managed device, or be exported by the same NetFlow-enabled device
Each connection summary includes total traffic statistics, as well as the number of connections in the summary. Because NetFlow-enabled devices generate unidirectional connections, a summary’s connection count is incremented by two for every connection based on NetFlow data.
Note that connection summaries do not contain all of the information associated with the summaries’ aggregated connections. For example, because client information is not used to aggregate connections into connection summaries, summaries do not contain client information.
Long-Running Connections
If a monitored session spans two or more five-minute intervals over which connection data is aggregated, the connection is considered a long-running connection . When calculating the number of connections in a connection summary, the system increments the count only for the five-minute interval in which a long-running connection was initiated.
Also, when calculating the number of packets and bytes transmitted by the initiator and responder in a long-running connection, the system does not report the number of packets and bytes that were actually transmitted during each five-minute interval. Instead, the system assumes a constant rate of transmission and calculates estimated figures based on the total number of packets and bytes transmitted, the length of the connection, and what portion of the connection occurred during each five-minute interval.
Combined Connection Summaries from External Responders
To reduce the space required to store connection data and speed up the rendering of connection graphs, the system combines connection summaries when:
- one of the hosts involved in the connection is not on your monitored network
- other than the IP address of the external host, the connections in the summaries meet the aggregation criteria listed in Understanding Connection Summaries: protocol, application protocol, detecting device, and so on
When viewing connection summaries in the event viewer and when working with connection graphs, the system displays
external
instead of an IP address for the non-monitored hosts.
As a consequence of this aggregation, if you attempt to drill down to the table view of connection data (that is, access data on individual connections) from a connection summary or graph that involves an external responder, the table view contains no information.
Understanding Connection and Security Intelligence Data Fields
Supported Devices: feature dependent
Supported Defense Centers: feature dependent
Each connection table view or connection graph contains information about the connections or connection summaries you are viewing, including timestamps, IP addresses, geolocation information, applications, and so on. Security Intelligence event views contain the same general information as connection event views, but list only connections with assigned Security Intelligence Category values.

Note The information available for any individual connection or Security Intelligence event depends on several factors, including licenses and appliance model. For more information, see License and Model Requirements for Connection Logging.
The following list details the connection data logged by the FireSIGHT System. For a discussion of the factors that determine the information logged in any individual connection or Security Intelligence event, see the next section: Information Available in Connection and Security Intelligence Events.
The access control policy that monitored the connection.
The access control rule or default action that handled the connection, as well as up to eight Monitor rules matched by that connection.
If the connection matched one Monitor rule, the Defense Center displays the name of the rule that handled the connection, followed by the Monitor rule name. If the connection matched more than one Monitor rule, the event viewer displays how many Monitor rules it matched, for example,
Default Action + 2 Monitor Rules
.
To display a pop-up window with a list of the first eight Monitor rules matched by the connection, click N Monitor Rules .
The action associated with the access control rule or default action that logged the connection:
–
Allow
represents explicitly allowed and user-bypassed interactively blocked connections.
–
Trust
represents trusted connections. Note that the system logs TCP connections detected by a trust rule differently depending on the appliance.
On Series 2, virtual devices, and Cisco NGIPS for Blue Coat X-Series, TCP connections detected by a trust rule on the first packet only generate an end-of-connection event. The system generates the event one hour after the final session packet.
On Series 3 appliances, TCP connections detected by a trust rule on the first packet generate different events depending on the presence of a monitor rule. If the monitor rule is active, the system evaluates the packet and generates both a beginning and end-of-connection event. If no monitor rule is active, the system only generates an end-of-connection event.
–
Block
and
Block with reset
represent blocked connections. The system also associates the
Block
action with connections blacklisted by Security Intelligence, connections blocked by an SSL policy, connections where an exploit was detected by an intrusion policy, and connections where a file was blocked by a file policy.
–
Interactive Block
and
Interactive Block with reset
mark the beginning-of-connection event that you can log when the system initially blocks a user’s HTTP request using an Interactive Block rule. If the user clicks through the warning page that the system displays, any additional connection events you log for the session have an action of
Allow
.
–
Default Action
indicates the connection was handled by the default action.
– For Security Intelligence-monitored connections, the action is that of the first non-Monitor access control rule triggered by the connection, or the default action. Similarly, because traffic matching a Monitor rule is always handled by a subsequent rule or by the default action, the action associated with a connection logged due to a monitor rule is never
Monitor
.
The application protocol, which represents communications between hosts, detected in the connection.
The risk associated with the application traffic detected in the connection:
Very High
,
High
,
Medium
,
Low
, or
Very Low
. Each type of application detected in the connection has an associated risk; this field displays the highest of those. For more information, see Table 45-2.
The business relevance associated with the application traffic detected in the connection:
Very High
,
High
,
Medium
,
Low
, or
Very Low
. Each type of application detected in the connection has an associated business relevance; this field displays the lowest (least relevant) of those. For more information, see Table 45-2.
Category, Tag (Application Protocol, Client, Web Application)
Criteria that characterize the application to help you understand the application's function. For more information, see Table 45-2.
The client application and version of that client detected in the connection.
If the system cannot identify the specific client used in the connection, this field displays
client
appended to the application protocol name to provide a generic name, for example,
FTP client
.
The number of connections in a connection summary. For long-running connections, that is, connections that span multiple connection summary intervals, only the first connection summary interval is incremented.
The number of connections that match the information that appears in each row. Note that the Count field appears only after you apply a constraint that creates two or more identical rows.

Note If you create a custom workflow and do not add the Count column to a drill-down page, each connection is listed individually and packets and bytes are not summed.
The managed device that detected the connection or, for connections exported by NetFlow-enabled devices, the managed device that processed the NetFlow data.
The file events, if any, associated with the connection. Instead of a list of files, the Defense Center displays the view files icon ( ) in this field. The number on the icon indicates the number of files (including malware files) detected or blocked in that connection.
) in this field. The number on the icon indicates the number of files (including malware files) detected or blocked in that connection.
Click the icon to display a pop-up window with a list of the files detected in the connection, as well as their types and if applicable, their malware lookup dispositions.
Note that neither the DC500 Defense Center nor Series 2 devices support network-based malware file detection.
For more information, see Viewing Files Detected in a Connection.
The date and time the first or last packet of the session was seen.
The HTTP referrer, which represents the referrer of a requested URL for HTTP traffic detected in the connection (such as a website that provided a link to, or imported a link from, another URL).
Ingress Interface or Egress Interface
The ingress or egress interface associated with the connection. Note that, if your deployment includes an asynchronous routing configuration, the ingress and egress interface may belong to the same interface set.
Ingress Security Zone or Egress Security Zone
The ingress or egress security zone associated with the connection.
Initiator Bytes or Responder Bytes
The total number of bytes transmitted by the session initiator or the session responder.
Initiator Country or Responder Country
When a routable IP is detected, the country associated with the host IP address that initiated the session, or with the session responder. An icon of the country’s flag is displayed, as well as the country’s ISO 3166-1 alpha-3 country code. Hover your pointer over the flag icon to view the country’s full name.
Note that the DC500 Defense Center does not support this feature.
The host IP address (and host name, if DNS resolution is enabled) that initiated, or responded to, the session responder. So that you can identify the blacklisted IP address in a blacklisted connection, host icons next to blacklisted IP addresses look slightly different.
Initiator Packets or Responder Packets
The total number of packets transmitted by the session initiator or the session responder.
The user logged into the session initiator.
The intrusion events, if any, associated with the connection. Instead of a list of events, the Defense Center displays the view intrusion events icon ( ) in this field.
) in this field.
Click the icon to display a pop-up window with a list of intrusion events associated with the connection, as well as their priority and impact. For more information, see Viewing Intrusion Events Associated with a Connection.
Whether or not the event triggered an indication of compromise (IOC) against a host involved in the connection. For more information on IOC, see Understanding Indications of Compromise.
The NetBIOS domain used in the session.
NetFlow Destination/Source Autonomous System
For connections exported by NetFlow-enabled devices, the border gateway protocol autonomous system number for the source or destination of traffic in the connection.
NetFlow Destination/Source Prefix
For connections exported by NetFlow-enabled devices, the source or destination IP address ANDed with the source or destination prefix mask.
NetFlow Destination/Source TOS
For connections exported by NetFlow-enabled devices, the setting for the type-of-service (TOS) byte when connection traffic entered or exited the NetFlow-enabled device.
For connections exported by NetFlow-enabled devices, the interface index for the interface where connection traffic entered or exited the NetFlow-enabled device.
The network analysis policy (NAP), if any, associated with the generation of the event.
The reason or reasons the connection was logged, in the following situations:
–
User Bypass
indicates that the system initially blocked a user’s HTTP request, but the user chose to continue to the originally requested site by clicking through a warning page. A reason of
User Bypass
is always paired with an action of
Allow
.
–
IP Block
indicates that the system denied the connection without inspection, based on Security Intelligence data. A reason of
IP Block
is always paired with an action of
Block
.
–
IP Monitor
indicates that the system would have denied the connection based on Security Intelligence data, but you configured the system to monitor, rather than deny, the connection.
–
File Monitor
indicates that the system detected a particular type of file in the connection.
–
File Block
indicates the connection contained a file or malware file that the system prevented from being transmitted. A reason of
File Block
is always paired with an action of
Block
.
–
File Custom Detection
indicates the connection contained a file on the custom detection list that the system prevented from being transmitted.
–
File Resume Allow
indicates that file transmission was originally blocked by a Block Files or Block Malware file rule. After a new access control policy was applied that allowed the file, the HTTP session automatically resumed. Note that this reason only appears in inline deployments.
–
File Resume Block
indicates that file transmission was originally allowed by a Detect Files or Malware Cloud Lookup file rule. After a new access control policy was applied that blocked the file, the HTTP session automatically stopped. Note that this reason only appears in inline deployments.
–
SSL Block
indicates the system blocked an encrypted connection based on the SSL inspection configuration. A reason of
SSL Block
is always paired with an action of
Block
.
–
Intrusion Block
indicates the system blocked or would have blocked an exploit (intrusion policy violation) detected in the connection. A reason of
Intrusion Block
is paired with an action of
Block
for blocked exploits and
Allow
for would-have-blocked exploits.
–
Intrusion Monitor
indicates the system detected, but did not block, an exploit detected in the connection. This occurs when the state of the triggered intrusion rule is set to
Generate Events
.
If the protocol in the connection is DNS, HTTP, or HTTPS, this field displays the host name that the respective protocol was using.
The metadata identifying the virtual firewall group through which the traffic passed. Note that the system only populates this field for ASA FirePOWER devices in multiple context mode.
Security Intelligence Category
The name of the blacklisted object that represents or contains the blacklisted IP address in the connection. The Security Intelligence category can be the name of a network object or group, the global blacklist, a custom Security Intelligence list or feed, or one of the categories in the Intelligence Feed. Note that this field is only populated if the
Reason
is
IP Block
or
IP Monitor
; entries in Security Intelligence event views always display a reason. For more information, see Blacklisting Using Security Intelligence IP Address Reputation.
Note also that neither the DC500 Defense Center nor Series 2 devices support this feature.
The IP address of the NetFlow-enabled device that exported the data for the connection. If the connection was detected by a managed device, this field contains a value of FireSIGHT .
Source Port/ICMP Type or Destination Port/ICMP Code
The port, ICMP type, or ICMP code used by the session initiator or session responder.
The action associated with the SSL rule, default action, or undecryptable traffic action that logged the encrypted connection:
–
Block
and
Block with reset
represent blocked encrypted connections.
–
Decrypt (Resign)
represents an outgoing connection decrypted using a re-signed server certificate.
–
Decrypt (Replace Key)
represents an outgoing connection decrypted using a self-signed server certificate with a substituted public key.
–
Decrypt (Known Key)
represents an incoming connection decrypted using a known private key.
–
Do not Decrypt
represents a connection the system did not decrypt.
If the system fails to decrypt an encrypted connection, it displays the undecryptable traffic action taken, as well as the failure reason. For example, if the system detects traffic encrypted with an unknown cipher suite and allows it without further inspection, this field displays
Do Not Decrypt (Unknown Cipher Suite)
.
Click the lock icon ( ) to view certificate details. For more information, see Viewing the Certificate Associated with an Encrypted Connection.
) to view certificate details. For more information, see Viewing the Certificate Associated with an Encrypted Connection.
If encrypted traffic matches an SSL rule, this field displays the server certificate statuses. If undecryptable traffic matches an SSL rule, this displays
Not Checked
. For more information, see Controlling Encrypted Traffic by Certificate Status.
The error name and hexadecimal code if an error occurred during the SSL session; Success if no error occurred.
The SSL or TLS protocol version used to encrypt the connection.
The cipher suite used to encrypt the connection.
The SSL policy that handled the connection.
The SSL rule or default action that handled the connection, as well as the first Monitor rule matched by that connection. If the connection matched a Monitor rule, the Defense Center displays the name of the rule that handled the connection, followed by the Monitor rule name.
The hexadecimal Session ID negotiated between the client and server during the SSL handshake.
A hexadecimal hash value of the session ticket information sent during the SSL handshake.
The first ten debugging level flags for an encrypted connection. To view all flags, click the ellipsis ( ... ).
The messages exchanged between client and server during the SSL handshake. See http://tools.ietf.org/html/rfc5246 for more information.
The TCP flags detected in the connection.
The ending time of the five-minute interval that the system used to aggregate connections in a connection summary.
URL, URL Category, and URL Reputation
The URL requested by the monitored host during the session and its associated category and reputation, if available.
If the system identifies or blocks an SSL application, the requested URL is in encrypted traffic, so the system identifies the traffic based on an SSL certificate. For SSL applications, therefore, this field indicates the common name contained in the certificate.
Note that neither the DC500 Defense Center nor Series 2 devices support URL category or reputation data.
User agent application information extracted from HTTP traffic detected in the connection.
The web application, which represents the content or requested URL for HTTP traffic detected in the connection.
If the web application does not match the URL for the event, the traffic is probably referred traffic, such as advertisement traffic. If the system detects referred traffic, it stores the referring application (if available) and lists that application as the web application.
If the system cannot identify the specific web application in HTTP traffic, this field displays
Web Browsing
.
Information Available in Connection and Security Intelligence Events
Supported Devices: feature dependent
Supported Defense Centers: feature dependent
The information available for any individual connection, connection summary, or Security Intelligence event depends on several factors.
You can log any connection that your access control and SSL policies can successfully handle. However, many features require that you enable specific licensed capabilities on target devices, and many features are only available on some models.
For example, SSL inspection requires a Series 3 device. Other appliance models cannot inspect encrypted traffic; logged connection events do not contain information about encrypted connections. As another example, you cannot view geolocation data in connection events using a DC500. For more information, see License and Model Requirements for Connection Logging.
The system only reports information present (and detectable) in network traffic. For example, there could be no user associated with an initiator host, or no referenced host detected in a connection where the protocol is not DNS, HTTP, or HTTPS.
Detection Method: FireSIGHT System vs NetFlow
With the exception of TCP flags and NetFlow autonomous system, prefix, and TOS data, the information available in NetFlow records is more limited than the information generated by monitoring network traffic using managed devices. For more information, see Differences Between NetFlow and FireSIGHT Data.
Logging Method: Beginning or End of Connection
When the system detects a connection, whether you can log it at its beginning or its end (or both).depends on how you configure the system to detect and handle it; see Logging the Beginning or End of Connections.
Beginning-of-connection events do not have information that must be determined by examining traffic over the duration of the session (for example, the total amount of data transmitted or the timestamp of the last packet in the connection). Beginning-of-connection events are also not guaranteed to have information about application or URL traffic in the session, and do not contain any details about the session’s encryption.
Inspection Method: Associated SSL, File, and Intrusion Policies
Only encrypted connections handled by an SSL policy have SSL-related information in the connection log. Only connections logged by access control rules with associated file policies contain file information. Similarly, you must associate intrusion policies with either access control rules or the default action to view intrusion information in the connection log.
Connection Event Type: Individual vs Summary
Connection summaries do not contain all of the information associated with their aggregated connections. For example, because client information is not used to aggregate connections into connection summaries, summaries do not contain client information.
Keep in mind that connection graphs are based on connection summary data, which use only end-of-connection logs. If you logged only beginning-of-connection data, connection graphs and connection summary event views contain no data.
An advanced setting in the access control policy controls the number of characters the system stores in the connection log for each URL requested by monitored hosts in HTTP sessions. If you use this setting to disable URL logging, the system does not display individual URLs in the connection log, although you can still view category and reputation data, if it exists.
Also, not all connection events have a Reason , which is a field populated only in specific situations, such as when a user bypasses an Interactive Block configuration; see Reason.
The following table lists each connection event/Security Intelligence event field and whether the system displays information in that field, depending on the detection method, logging method, and connection event type. Note that, because Security Intelligence events are never aggregated, the Summary column refers only to connection event summaries.

Tip In the table views of both connection events and Security Intelligence events, several fields are hidden by default, including the Category and Tag fields for each type of application, NetFlow-related fields, SSL-related fields, and others. To show a hidden field in an event view, expand the search constraints, then click the field name under Disabled Columns.
Viewing Connection and Security Intelligence Data
Supported Devices: feature dependent
Supported Defense Centers: feature dependent
To help you gain in-depth insight into connection data, the system can present connection data both graphically and in a tabular format. The page you see when you access connection data differs depending on the workflow you use. You can use one of the predefined workflows or create a custom workflow that displays only the information that matches your specific needs.
Security Intelligence events require a Protection license and appear in table form only. Security Intelligence data is not supported on Series 2 managed devices or on DC500 Defense Centers. You cannot create data graphs from Security Intelligence events, although their connection event counterparts are viewable in graph form. For interactive graphic views of Security Intelligence data, you can view the Security Intelligence section of the Context Explorer. See Understanding the Security Intelligence Section for more information.

Note The information available for any individual connection or Security Intelligence event depends on several factors, including licenses and appliance model. For more information, see License and Model Requirements for Connection Logging.
Each table view or graph contains information about the connections or connection summaries you are viewing, including timestamps, IP addresses, applications, and so on. The information available for any individual connection detected by the FireSIGHT System depends on several factors, including detection method and logging options. For more information, see Understanding Connection and Security Intelligence Data Fields and Information Available in Connection and Security Intelligence Events.

Tip The Connection Summary dashboard can provide you with an at-a-glance view of the connections logged by the system, and the Summary Dashboard displays Security Intelligence event data. For more information, see Using Dashboards.
To view connection or Security Intelligence data:
Access: Admin/Any Security Analyst
The first page of the default connection or Security Intelligence workflow appears. For connection events, there are two possibilities:
- The workflow page displays a graph . See Working with Connection Graphs for information on the actions you can perform.
- The workflow page displays a table . See Working with Connection and Security Intelligence Data Tables for information on the actions you can perform.
For Security Intelligence events, the workflow page displays a table .
To use a different workflow, including a custom workflow, click (switch workflow) by the workflow title. For information on specifying a different default workflow, see Configuring Event View Settings. If no events appear, you may need to adjust the time range; see Setting Event Time Constraints.
Working with Connection Graphs
One of the ways the system can present connection data is graphically. There are three different types of connection graphs: line graphs, bar graphs, and pie charts. Bar graphs and line graphs can display multiple datasets; that is, they can display several values on the y-axis for each x-axis data point.
You can manipulate connection graphs in various ways, including:
- changing the type of data that the graph displays
- switching between graph types
- constraining the graph so it shows data for specific time ranges, hosts, applications, ports, and devices
Because traffic profiles are based on connection data (see Creating Traffic Profiles), you can view traffic profiles as line graphs. You can manipulate these graphs in the same way as you would any other connection graph, with some restrictions.
You cannot create data graphs from Security Intelligence events, although their connection event counterparts are viewable in graph form. For interactive graphic views of Security Intelligence data, you can view the Security Intelligence section of the Context Explorer. See Understanding the Security Intelligence Section for more information.

Note To view traffic profiles, you must have Administrator access. Compare this with other connection graphs, which you can view with any Security Analyst or Administrator access.
When you view a connection graph, as described in Viewing Connection and Security Intelligence Data, you can perform the basic actions described in the following table.
Access: Admin/Any Security Analyst
find more information in Understanding Connection and Security Intelligence Data Fields. |
|
find more information in Setting Event Time Constraints. |
|
on a graph displaying connection data by initiator or responder, click either a bar on a bar graph or a wedge on a pie chart and select View Host Profile . |
|
find more information in Using Workflow Pages. |
|
find more information in Navigating Between Workflows. |
There are many other ways you can manipulate connection graphs as you perform in-depth analysis of connection data. For more information, see:
- Changing the Graph Type explains how to change between bar graphs and pie chart, and between standard line graphs and velocity graphs.
- Selecting Datasets explains how to display several values on the y-axis for each x-axis data point on line graphs and bar graphs.
- Viewing Information About Aggregated Connection Data explains how to get more information about the data points on a graph, or to display the host profile of a host whose statistics are being graphed.
- Manipulating a Connection Graph on a Workflow Page explains how to constrain the data that appears on a connection graph without advancing the workflow to the next page.
- Drilling Down Through Connection Data Graphs explains how to constrain the data that appears on a connection graph while advancing the workflow to the next page.
- Recentering and Zooming on Line Graphs explains how to recenter a line graph around any point in time.
- Selecting Data to Graph explains how to change the data displayed on a connection graph by changing its x- or y-axis.
- Detaching Connection Graphs explains how you can detach a connection graph into a new browser window and perform further analysis without affecting the default time range for the Defense Center.
- Exporting Connection Data explains how to export the connection data used to construct a graph as a CSV (comma-separated values) file.
Changing the Graph Type
There are three different connection graphs: line graphs, bar graphs, and pie charts. Line graphs plot data over time. For example, the following line graph displays the total number of connections detected on a monitored network over a one-hour time span. Traffic profiles are always displayed as line graphs.

By default, line graphs appear in standard view . A standard line graph aggregates data over five minute intervals, plots the aggregated data points, and connects the points.
However, you can change a line graph from standard view to velocity view . A velocity line graph shows the rate of change between those data points. If you change the above graph to a velocity graph, the y-axis changes from indicating the number of connections to indicating the change in the number of connections over time.
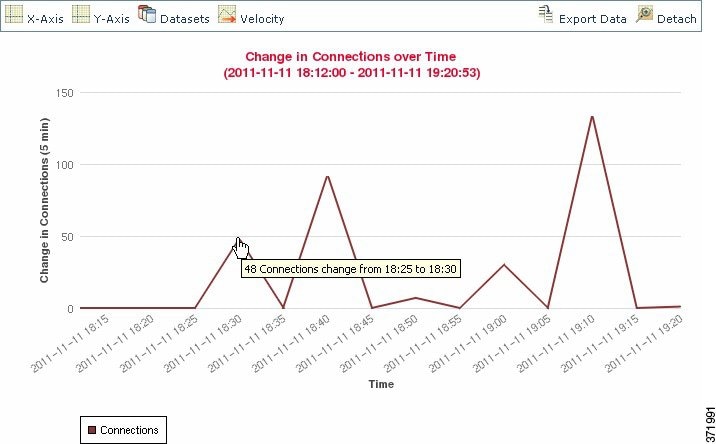
Bar graphs display data grouped into discrete categories. For example, a bar graph could show the number of connections detected on a monitored network for the 10 most active ports over a one-hour time span.
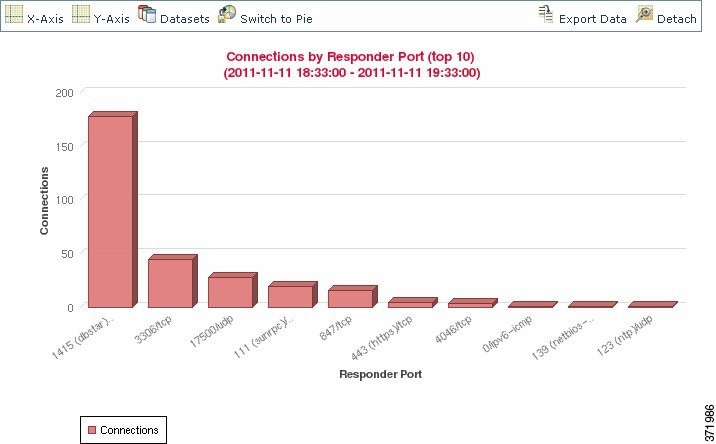
Pie charts , like bar graphs, also display data grouped into discrete categories. The following pie chart shows the same information as the bar graph above.

Follow the directions in the following table to switch between standard and velocity line graphs, and to switch between bar graphs and pie charts.
Access: Admin/Any Security Analyst
|
Note that pie charts cannot display multiple datasets; see Selecting Datasets. |
|
Selecting Datasets
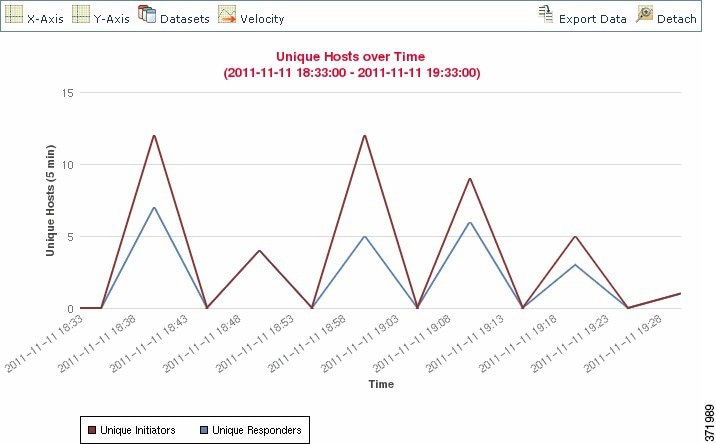
Both bar graphs and line graphs can display multiple datasets; that is, they can display several values on the y-axis for each x-axis data point. For example, you could display the total number of unique initiators and the total number of unique Pie charts can only display one dataset.
On line graphs, multiple datasets appear as multiple lines, each with a different color. For example, the following graphic displays the total number of unique initiators and the total number of unique responders detected on a monitored network over a one hour interval.
On bar graphs, multiple datasets appear as a set of colored bars for each x-axis data point. For example, the following bar graph displays the total packets transmitted on a monitored network, packets transmitted by initiators, and packets transmitted by responders.
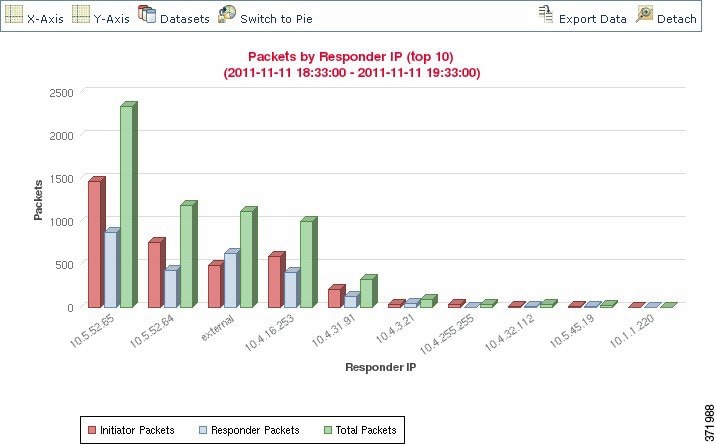
You cannot display multiple datasets on a pie chart. If you switch to a pie chart from a bar graph that has multiple datasets, the pie chart shows only one dataset, which is selected automatically. When selecting which dataset to display, the Defense Center favors total statistics over initiator and responder statistics, and favors initiator statistics over responder statistics. The following table describes the datasets you can display on the x-axis of a connection graph.
To select the datasets displayed on a connection graph:
Access: Admin/Any Security Analyst
Step 1 Click Datasets and select the datasets you want to graph.
The datasets you can select are described in the Dataset Options table.
Viewing Information About Aggregated Connection Data
Connection graphs are based on aggregated data over five-minute intervals, also called connection summaries . You can get more information about the specific connection summaries used to construct a connection graph. For example, on a graph of connections over time, you may want to know exactly how many connections were detected over a specific interval.
To get detailed information on aggregated connection data:
Access: Admin/Any Security Analyst
Step 1 Position your cursor over a point on a line graph a bar in a bar graph, or a wedge in a pie chart. A tooltip appears with detailed information about the data used to construct that portion of the graph.
Manipulating a Connection Graph on a Workflow Page
When you open a connection data workflow, the data is initially constrained only by a time range. You can constrain connection graphs with additional criteria without advancing the workflow to the next page.

Tip Constraining connection data in this manner changes the x-axis (also called the independent variable when viewing a pie chart) of the graph. To change the independent variable without constraining the connection data, use the X-Axis and Y-Axis menus. For more information, see Selecting Data to Graph.
Access: Admin/Any Security Analyst
Step 1 Click a point on a line graph, a bar on a bar graph, or a wedge on a pie chart.
Step 2 Select a View by... option.
You can constrain connection data based on any of the criteria listed in the X-Axis Functions table.
For example, consider a graph of connections over time. If you constrain a point on the graph by port, a bar graph appears, showing the 10 most active ports based on the number of detected connection events, but constrained by the ten-minute time span that is centered on the point you clicked.
If you further constrain the graph by clicking on one of the bars and selecting View by Initiator IP , a new bar graph appears, constrained by not only the same ten-minute time span as before, but also by the port represented by the bar you clicked.

Note Unless you are working with a detached graph, constraining connection data in this manner changes the time range. For more information on detached graphs, see Detaching Connection Graphs.
Drilling Down Through Connection Data Graphs
When you open a connection data workflow, the data is initially constrained only by a time range. You can constrain connection graphs while advancing the workflow to the next page.
To drill down in a connection data workflow:
Access: Admin/Any Security Analyst
Step 1 Click a point on a line graph, a bar on a bar graph, or a wedge on a pie chart.
You drill down to the next workflow page, constraining using the item you clicked:
- Clicking a point on a line graph constrains the time range on the next page to a 10-minute span, centered on the point you clicked.
- Clicking a bar on a bar graph or a wedge on a pie chart constrains the next page based on the criterion represented by the bar or wedge. For example, clicking on a bar that represents port use drills down to the next page in the workflow, which is constrained by the port represented by the bar you clicked.
Recentering and Zooming on Line Graphs
You can recenter line graphs around any point in time. You can recenter using either the default time range, or you can choose a different time range.

Note Unless you are working with a detached graph, recentering changes the default time range. For more information on detached graphs, see Detaching Connection Graphs.
To recenter using the default time range:
Access: Admin/Any Security Analyst
Step 1 Click the point on the line graph where you want to recenter the graph, and click recenter .
The graph is redrawn, centered on the point you clicked, with a time span that is the same length as your default time range.
To recenter using a different time range:
Access: Admin/Any Security Analyst
Step 1 Click the point where you want to recenter the graph and click Zoom .
Selecting Data to Graph
You can display different data on a connection graph by changing either the x-axis, the y-axis, or both.
Note that on a pie chart, changing the x-axis changes the independent variable and changing the y-axis changes the dependent variable. For example, consider a pie chart that graphs kilobytes per port. In this case, the x-axis is Responder Port and the y-axis is KBytes . This pie chart represents the total kilobytes of data transmitted over a monitored network during a certain interval. The wedges of the pie represent the percent of the data that was detected on each port. If you change the x-axis of the chart to Application Protocol , the pie chart still represents the total kilobytes of data transmitted, but the wedges of the pie represent the percentage of the data transmitted for each detected application protocol.
However, if you change the y-axis of the first pie chart to Packets , the pie chart represents the total number of packets transmitted over the monitored network during a certain interval, and the wedges of the pie represent the percentage of the total number of packets that was detected on each port.
Follow the directions in the following table to change the x-axis of a connection graph.
Follow the directions in the following table to change the y-axis of a connection graph.
Detaching Connection Graphs
If you want to perform further analysis on a connection graph, without affecting the default time range, you can detach the graph into a new browser window. You can perform all the same actions on detached connection graphs that you can on embedded connection graphs. You can also print a detached graph by clicking Print . Note that traffic profile graphs are, by default, detached graphs.

Tip If you are viewing a detached graph, click New Window to create another copy of the detached graph in a new browser window. You can then perform different analyses on each of the detached graphs.
Access: Admin/Any Security Analyst
Exporting Connection Data
You can easily share connection data with others by exporting it as a CSV (comma-separated values) file.

Tip You can also save a connection graph as an image by right-clicking on the graph and following your browser’s prompts.
Access: Admin/Any Security Analyst
A pop-up window appears, displaying a table view of the data on your graph.
Step 2 Click Download CSV File and save the file.
Working with Connection and Security Intelligence Data Tables
Supported Devices: feature dependent
Supported Defense Centers: feature dependent
The FireSIGHT System’s event viewer allows you to view connection data in a table, as well as manipulate the event view depending on the information relevant to your analysis. Viewing Security Intelligence events allows you to focus on connections with an identified Security Intelligence reputation. (Security Intelligence requires a Protection license and is not supported on Series 2 managed devices or DC500 Defense Centers.) The page you see when you access connection data differs depending on the workflow, which is simply a series of pages you can use to evaluate events by moving from a broad to a more focused view.

Note The information available for any individual connection or Security Intelligence event depends on several factors, including licenses and appliance model. For more information, see License and Model Requirements for Connection Logging.
The system-provided Connection Events and Security Intelligence Events workflows provide summary views of basic connection and detected application information, which you can then use to drill down to the table view of events.You can also create a custom workflow that displays only the information that matches your specific needs.
Using the event viewer, you can:
- search for, sort, and constrain events, as well as change the time range for displayed events
- specify the columns that appear (table view only)
- view the host profile associated with an IP address, or the user details and host history associated with a user identity
- view files (including malware files) and intrusions detected in connections
- view geolocation information associated with an IP address
- view the full text of a URL in a connection event
- view information about the certificate used to encrypt a session
- view encrypted session details
- view events using different workflow pages within the same workflow
- view events using a different workflow altogether
- drill down page-to-page within a workflow, constraining on specific values
- bookmark the current page and constraints so you can return to the same data (assuming the data still exists) at a later time
- create a report template using the current constraints
- delete events from the database
- use the IP address context menu to whitelist, blacklist, or obtain additional information about a host or IP address associated with a connection
Note that when you constrain connection events on a drill-down page, the packets and bytes from identical events are summed. However, if you are using a custom workflow and did not add a Count column to a drill-down page, the events are listed individually and packets and bytes are not summed.
Note that the Connection Events table view displays 1 of Many instead of how many pages of events are available if your system generates more than 25 connection events.
The following sections contain information on viewing and analyzing connection and Security Intelligence event tables:
- Understanding and Using Workflows provides detailed instructions on using the event viewer.
- Using Geolocation provides information on how to view and interpret geolocation information associated with connection and Security Intelligence events.
- Configuring Event View Settings explains how to change the default workflow for viewing connection and Security Intelligence event data.
- Understanding Connection and Security Intelligence Data Fields and Information Available in Connection and Security Intelligence Events provide details on the data in connection and Security Intelligence events.
- Working with Events Associated with Monitor Rules explains how to constrain connection events using Monitor rule criteria.
- Viewing Files Detected in a Connection explains how to view the files, including malware files, detected or blocked in a connection.
- Viewing Intrusion Events Associated with a Connection explains how to view the intrusion events associated with a connection.
- Viewing the Certificate Associated with an Encrypted Connection explains how to view details about the certificate used to encrypt a connection.
Working with Events Associated with Monitor Rules
When you view logged connections using the event viewer, the Defense Center displays the access control rule or default action that handled each connection, as well as up to eight Monitor rules matched by each of those connections.
If a connection matched one Monitor rule, the Defense Center displays the name of the rule that handled the connection, followed by the Monitor rule name. If the connection matched more than one Monitor rule, the event viewer displays how many Monitor rules it matched, for example,
Default Action + 2 Monitor Rules
.
You can constrain connection event views using matched Monitor rules, using either of the following:
- the access control rule or default action that handled the connection
- any individual Monitor rule matched by a connection
To constrain connection events using Monitor rule matching:
Access: Admin/Any Security Analyst
Step 1 Select Analysis > Connections > Events .
The first page of the default connection data workflow appears.
Step 2 Display the workflow you want to use for your analysis. Make sure the drill-down page or table view you are using shows the Access Control Rule field.
Step 3 How do you want to constrain the events?
- to constrain on the access control rule or default action that handled the connection, click the rule name or Default Action .
- to constrain on the only Monitor rule that matched a logged connection, click the Monitor rule name.
- to constrain on one of several Monitor rules that matched a logged connection, click an N Monitor Rules value. For example, click 2 Monitor Rules .
The Monitor Rules pop-up window for that connection event appears, listing the first eight Monitor rules matched by the connection. Click the Monitor rule name you want to use to constrain connection events.
Your events are constrained. If you were using a drill-down page, the event view advances to the next page in the workflow.
Viewing Files Detected in a Connection
License: Protection or Malware
Supported Devices: feature dependent
Supported Defense Centers: feature dependent
If you associate a file policy with one or more access control rules, the system can detect files (including malware) in matching traffic. Using the event viewer, you can see the file events, if any, associated with the connections logged by those rules.
Instead of a list of files, the Defense Center displays the view files icon ( ) in the
Files
column. The number on the icon indicates the number of files (including malware files) detected or blocked in that connection. Clicking on the icon does not drill down to the next workflow page or constrain connection events. Instead, it displays a pop-up window with a list of the files detected in the connection as well as their types, and if applicable, their malware dispositions.
) in the
Files
column. The number on the icon indicates the number of files (including malware files) detected or blocked in that connection. Clicking on the icon does not drill down to the next workflow page or constrain connection events. Instead, it displays a pop-up window with a list of the files detected in the connection as well as their types, and if applicable, their malware dispositions.
In the pop-up window, you can click:
- View File Events or View Malware Events to view details on all of the connection’s detected file or network-based malware events

Tip To quickly view file or malware events associated with one or more connections, select the connections using the check boxes in the event viewer, then select Malware Events or File Events from the Jump to drop-down list. You can view the connections used to transmit files in a similar way. For more information, see Navigating Between Workflows.
When you view associated events, the Defense Center uses your default workflow for that event type. For more information on file and malware events, see Working with File Events and Working with Malware Events. For more information on using the network file trajectory feature, see Working with Network File Trajectory.
Note that not all file and malware events are associated with connections, as follows:
- Endpoint-based malware events are not associated with connections. Those events are generated by FireAMP Connectors, instead of by the system inspecting network traffic.
- Many IMAP-capable email clients use a single IMAP session, which ends only when the user exits the application. Although long-running connections are logged by the system (see Long-Running Connections), files downloaded in the session are not associated with the connection until the session ends.
Note also that Series 2 and Cisco NGIPS for Blue Coat X-Series devices and the DC500 Defense Center do not support network-based advanced malware protection.
Viewing Intrusion Events Associated with a Connection
If you associate an intrusion policy with an access control rule or default action, the system can detect exploits in matching traffic. Using the event viewer, you can see the intrusion events, if any, associated with logged connections.
Instead of a list of events, the Defense Center displays the view intrusion events icon ( ) in the
Intrusion Events
column. Clicking on the icon does not drill down to the next workflow page or constrain connection events. Instead, it displays a pop-up window with a list of the intrusion events associated with the connection, as well as their priority and impact.
) in the
Intrusion Events
column. Clicking on the icon does not drill down to the next workflow page or constrain connection events. Instead, it displays a pop-up window with a list of the intrusion events associated with the connection, as well as their priority and impact.
In the pop-up window, you can click a listed event’s view icon ( ) to view details in the packet view. You can also click
View Intrusion Events
to view details on all of the connection’s associated intrusion events.
) to view details in the packet view. You can also click
View Intrusion Events
to view details on all of the connection’s associated intrusion events.

Tip To quickly view intrusion events associated with one or more connections, select the connections using the check boxes in the event viewer, then select Intrusion Events from the Jump to drop-down list. You can view the connections associated with intrusion events in a similar way. For more information, see Navigating Between Workflows.
When you view associated events, the Defense Center uses your default intrusion events workflow. For more information on intrusion events, see Working with Intrusion Events.
Viewing the Certificate Associated with an Encrypted Connection
If you configure SSL inspection, you can log encrypted connections. Using the event viewer, you can view details of the public key certificate used to encrypt a connection if the system acted on the traffic and the certificate is available.
Instead of the certificate itself, the Defense Center displays a lock icon ( ) in the
SSL Status
column. Clicking on the icon displays a pop-up window with the certificate details described in the following table.
) in the
SSL Status
column. Clicking on the icon displays a pop-up window with the certificate details described in the following table.
You can expand or collapse sections in the pop-up window by double-clicking the heading.
Note that if the system acted on the encrypted traffic but the certificate is unavailable, the lock icon is grayed out. For example, if the system blocked a connection because it contained an SSL handshake error and the system could not decrypt it, then the system would not have encryption certificate details, and the lock icon for that connection is grayed out.
Searching for Connection and Security Intelligence Data
Using the Defense Center’s Search page, you can search for specific connection events, Security Intelligence events, or connection summaries; display the results in the event viewer; and save your search criteria to reuse later. Custom Analysis dashboard widgets, report templates, and custom user roles can also use saved searches.
Searches delivered with the system, labeled with
(
Cisco
)
in the Saved Searches list, serve as examples.
Because connection graphs are based on connection summaries, the same criteria that constrain connection summaries also constrain connection graphs. Fields marked with an asterisk (
*
) constrain connection graphs and connection summaries, as well as individual connection or Security Intelligence events.
If you search connection summaries using invalid search constraints and view your results using a connection summary page in a custom workflow, the invalid constraints are labeled as not applicable (N/A) and are marked with a strikethrough, as shown in the following graphic.
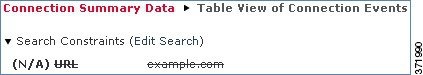
Also, keep in mind that your search results depend on the available data in the events you are searching. In other words, depending on the available data, your search constraints may not apply. See Information Available in Connection and Security Intelligence Events for information on when data is available for each connection data field.
The system displays examples of valid syntax next to each search field. When entering search criteria, keep the following points in mind:
-
All fields accept negation (
!). - All fields accept comma-separated lists of search values. Records that contain any of the listed values in the specified field match that search criteria.
- All fields accept comma-separated lists enclosed in quotation marks as search values.
– For fields that may contain only a single value, records with the specified field containing the exact string specified within the quotation marks match the search criteria. For instance, a search for
A, B, "C, D, E"
will match records where the specified field contains
"A"
or
"B"
or
"C, D, E"
. This permits matching on fields that include the comma in possible values.
– For fields that may contain multiple values at the same time, records with the specified fields containing all of the values in the quote-enclosed comma-separated list match that search criteria.
– For fields that may contain multiple values at the same time, search criteria may include single values as well as quote-enclosed comma-separated lists. For instance, a search for
A, B, "C, D, E"
on a field that may contain one of more of these letters matches records where the specified field contains
A
or
B
, or all of
C
,
D
, and
E
.
- Searches return only records that match the search criteria specified for all fields.
-
Many fields accept one or more asterisks (
*) as wild cards. -
Specify
n/ain any field to identify events where information is not available for that field; use!n/ato identify the events where that field is populated. - Use the device field to search for specific devices as well as devices in groups, stacks, or clusters. For more information on how the FireSIGHT System treats the device field in searches, see Specifying Devices in Searches.
- Click the add object icon (
 ) that appears next to a search field to use an object as a search criterion.
) that appears next to a search field to use an object as a search criterion.For detailed information on search syntax, including using objects in searches, see Searching for Events.
Special Search Syntax for Connection and Security Intelligence Data
To supplement the general search syntax listed above, the following list describes some special search syntax for connection and Security Intelligence data.
A Monitor rule matched by the connection
Use the Access Control Rule criterion to search for connections that matched individual Monitor rules.
Because traffic matching a Monitor rule is always later handled by another rule or by the default action, you cannot search for a connection with an action of
Monitor
. Searching for the name of a Monitor rule returns all connections that matched that Monitor rule, regardless of the rule or default action that later handled the connection.
A Criterion with a numerical value (Bytes, Packets, Connections)
You can precede the number with greater than (
>
), greater than or equal to (
>=
), less than (
<
), less than or equal to (
<=
), or equal to (
=
).

Tip To view meaningful results for searches using the Connections criterion, you must use a custom workflow that has a connection summary page.
Files or Intrusion Events associated with the connection
You cannot use the connection/Security Intelligence events Search page to search for file, malware, and intrusion events associated with a connection. For information on viewing these associated events, see Viewing Files Detected in a Connection and Viewing Intrusion Events Associated with a Connection.
The Initiator User or URL for a connection
The system performs a partial match, that is, you can search for all or part of the field contents without using asterisks.
The total Traffic (in bytes) or transport Protocol used in the connection
To determine if there is a protocol or traffic constraint on a connection table view, expand the search constraints.
To search for a specific protocol, use the name or number protocol as listed in http://www.iana.org/assignments/protocol-numbers .
These columns do not appear in table views.
TCP Flags in a NetFlow connection
Type a list of comma-separated TCP flags to view all connections that have at least one of those flags (instead of all). You can also select the Only check box to search for connections that have any of the flags you specify as their only TCP flag.
SSL Encryption applied to the connection
Type
yes
or
no
to view SSL-encrypted or non-encrypted connections.
This column does not appear in Security Intelligence or connection events table views.
Type one or more of the keywords listed for SSL Actual Action and SSL Failure Reason to view encrypted traffic to which the system applied an action or encountered a condition. This field may simultaneously contain one SSL Actual Action value and SSL Failure Reason value.
When decryption is successful, the Security Intelligence and connection event table views display the value for SSL Actual Action in the SSL Status column. When the system fails to decrypt traffic, the Security Intelligence and connection event table views display the values for both SSL Actual Action and SSL Failure Reason in the SSL Status column.
Type any of the following keywords to view encrypted traffic to which the system applied the action specified:
–
Do Not Decrypt
represents connections the system did not decrypt.
–
Block
and
Block with Reset
represent blocked encrypted connections.
–
Decrypt (Known Key)
represents incoming connections decrypted using a known private key.
–
Decrypt (Replace Key)
represents outgoing connections decrypted using a self-signed server certificate with a substituted public key.
–
Decrypt (Resign)
represents outgoing connections decrypted using a re-signed server certificate.
When decryption is successful, the Security Intelligence and connection event table views display this value in the SSL Status column. When the system fails to decrypt traffic, the Security Intelligence and connection event table views display this value with the SSL Failure Reason in the SSL Status column.
Type any of the following keywords to view encrypted traffic that the system was expected to process in the manner specified given the SSL rules in effect:
–
Do Not Decrypt
represents connections the system did not decrypt.
–
Block
and
Block with Reset
represent blocked encrypted connections.
–
Decrypt (Known Key)
represents incoming connections decrypted using a known private key.
–
Decrypt (Replace Key)
represents outgoing connections decrypted using a self-signed server certificate with a substituted public key.
–
Decrypt (Resign)
represents outgoing connections decrypted using a re-signed server certificate.
This column does not appear in Security Intelligence or connection events table views.
Type any of the following keywords to view encrypted traffic that the system failed to decrypt for the reason specified:
–
Session Undecryptable in Passive Mode
–
Pending Server Name Category Lookup
–
Pending Common Name Category Lookup
–
Network Parameters Unavailable
–
Invalid Server Certificate Handle
–
Server Certificate Fingerprint Unavailable
–
External Certificate List Unavailable
–
External Certificate Fingerprint Unavailable
–
Internal Certificate List Invalid
–
Internal Certificate List Unavailable
–
Internal Certificate Unavailable
–
Internal Certificate Fingerprint Unavailable
–
Server Certificate Validation Unavailable
–
Server Certificate Validation Failure
When the system fails to decrypt traffic, the Security Intelligence and connection event table views display this value with the SSL Actual Action in the SSL Status column.
Type a macro value representing a cipher suite used to encrypt the connection. See www.iana.org/assignments/tls-parameters/tls-parameters.xhtml for cipher suite value designations.
Type a two-character ISO 3166-1 alpha-2 country code to view encrypted traffic associated with the encryption certificate subject country.
This column does not appear in Security Intelligence or connection events table views.
Type a two-character ISO 3166-1 alpha-2 country code to view encrypted traffic associated with the encryption certificate subject country.
This column does not appear in Security Intelligence or connection events table views.
Type or paste the SHA hash value used to authenticate a certificate to view traffic associated with that certificate.
This column does not appear in Security Intelligence or connection events table views.
Type or paste the SHA hash value used to authenticate the public key contained within a certificate to view traffic associated with that certificate.
This column does not appear in Security Intelligence or connection events table views.
This applies only if you configured a Certificate Status rule condition. Type one or more of the keywords listed below to view encrypted traffic associated with server certificate statuses. Encrypted traffic may match multiple server certificate status values simultaneously.
Type any of the following keywords to view encrypted traffic associated with the following messages exchanged between client and server during the SSL handshake:
Type any of the following keywords to view encrypted traffic associated with the specified SSL or TLS protocol version:
Type or paste the serial number assigned to the public key certificate by the issuing CA.
This column does not appear in Security Intelligence or connection events table views.
To search for connection or Security Intelligence data:
Access: Admin/Any Security Analyst
Step 1 Select Analysis > Search .
Step 2 You have the following options:
The page updates with the appropriate constraints.
Step 3 Enter your search criteria in the appropriate fields:
- See Understanding Connection and Security Intelligence Data Fields for information on the fields in the connection and Security Intelligence events tables.
- See Viewing the Certificate Associated with an Encrypted Connection for information on fields related to public key certificates.
- See Special Search Syntax for Connection and Security Intelligence Data for special search syntax for connection and Security Intelligence events.
Step 4 Optionally, if you plan to save the search, you can select the Private check box to save the search as private so only you can access it. Otherwise, leave the check box clear to save the search for all users.

Tip If you want to use the search as a data restriction for a custom user role, you must save it as a private search.
Step 5 Optionally, you can save the search to be used again in the future. You have the following options:
For a new search, a dialog box appears prompting for the name of the search; enter a unique search name and click Save . If you save new criteria for a previously-existing search, no prompt appears. The search is saved (and visible only to your account if you selected Private ) so that you can run it at a later time.
A dialog box appears prompting for the name of the search; enter a unique search name and click Save . The search is saved (and visible only to your account if you selected Private ) so that you can run it at a later time.
Step 6 Click Search to start the search.
Your search results appear in your default connection or Security Intelligence workflow, constrained by the current time range.
Viewing the Connection Summary Page
The Connection Summary page provides graphs of the activity on your monitored network organized by different criteria. For example, the Connections over Time graph displays the total number of connections on your monitored network over the interval that you select.

Note The Connection Summary page is visible only to users who have custom roles that are restricted by searches on connection events and who have been granted explicit access to the Connection Summary page. For more information, see Understanding Restricted User Access Properties and Managing Custom User Roles.
The following table describes the different actions you can perform on the Connection Summary page.
modify the time and date range for the Connection Summary page |
find more information in Setting Event Time Constraints. |
find more information in Working with Connection Graphs. |
|
click View on the graph you want to detach. For more information on detached graphs, see Detaching Connection Graphs. |
You can perform almost all the same actions on connection summary graphs that you can perform on connection graphs. However, because the graphs on the Connection Summary page are based on aggregated data, you cannot examine the individual connection events on which the graphs are based. In other words, you cannot drill down to a connection data table view from a connection summary graph.
To view the Connection Summary page:
Step 1 Select Overview > Summary > Connection Summary .
The Connection Summary page appears for the current time range on your Defense Center.
Step 2 From the Select Device list, select the device whose summary you want to view, or select All to view a summary of all devices.
 ) to view details in a table view of file events
) to view details in a table view of file events ) to view details in a table view of malware events
) to view details in a table view of malware events ) to track the file’s transmission through your network
) to track the file’s transmission through your network Feedback
Feedback