- Title Page
- Introduction & Preface
- Logging into the FireSIGHT System
- Using Objects and Security Zones
- Managing Devices
- Setting Up an IPS Device
- Setting Up Virtual Switches
- Setting Up Virtual Routers
- Setting Up Aggregate Interfaces
- Setting Up Hybrid Interfaces
- Using Gateway VPNs
- Using NAT Policies
- Getting Started with Access Control Policies
- Blacklisting Using Security Intelligence IP Address Reputation
- Tuning Traffic Flow Using Access Control Rules
- Controlling Traffic with Network-Based Rules
- Controlling Traffic with Reputation-Based Rules
- Controlling Traffic Based on Users
- Controlling Traffic Using Intrusion and File Policies
- Understanding Traffic Decryption
- Getting Started with SSL Policies
- Getting Started with SSL Rules
- Tuning Traffic Decryption Using SSL Rules
- Understanding Intrusion and Network Analysis Policies
- Using Layers in Intrusion and Network Analysis Policies
- Customizing Traffic Preprocessing
- Getting Started with Network Analysis Policies
- Using Application Layer Preprocessors
- Configuring SCADA Preprocessing
- Configuring Transport & Network Layer Preprocessing
- Tuning Preprocessing in Passive Deployments
- Getting Started with Intrusion Policies
- Tuning Intrusion Rules
- Tailoring Intrusion Protection to Your Network Assets
- Detecting Specific Threats
- Limiting Intrusion Event Logging
- Understanding and Writing Intrusion Rules
- Blocking Malware and Prohibited Files
- Logging Connections in Network Traffic
- Working with Connection & Security Intelligence Data
- Analyzing Malware and File Activity
- Working with Intrusion Events
- Handling Incidents
- Configuring External Alerting
- Configuring External Alerting for Intrusion Rules
- Introduction to Network Discovery
- Enhancing Network Discovery
- Configuring Active Scanning
- Using the Network Map
- Using Host Profiles
- Working with Discovery Events
- Configuring Correlation Policies and Rules
- Using the FireSIGHT System as a Compliance Tool
- Creating Traffic Profiles
- Configuring Remediations
- Using Dashboards
- Using the Context Explorer
- Working with Reports
- Understanding and Using Workflows
- Using Custom Tables
- Searching for Events
- Managing Users
- Scheduling Tasks
- Managing System Policies
- Configuring Appliance Settings
- Licensing the FireSIGHT System
- Updating System Software
- Monitoring the System
- Using Health Monitoring
- Auditing the System
- Using Backup and Restore
- Specifying User Preferences
- Importing and Exporting Configurations
- Purging Discovery Data from the Database
- Viewing the Status of Long-Running Tasks
- Command Line Reference
- Security, Internet Access, and Communication Ports
- Third-Party Products
- glossary
Creating Traffic Profiles
A traffic profile is just that—a profile of the traffic on your network, based on connection data collected over a time span that you specify. You can use connection data collected by your devices, the connection data exported by any or all of your NetFlow-enabled devices, or both.
After you create a traffic profile, you can detect abnormal network traffic by evaluating new traffic against your profile, which presumably represents normal network traffic.
Keep in mind that the FireSIGHT System uses connection data to create traffic profiles and trigger correlation rules based on traffic profile changes. You cannot include connections that you do not log to the Defense Center database in traffic profiles. The system uses only end-of-connection data to populate connection summaries (see Understanding Connection Summaries), which the system then uses to create connection graphs and traffic profiles. Therefore, if you want to create and use traffic profiles, make sure you log connection events at the end of connections.
The time span used to collect data to build your traffic profile is called the profiling time window (PTW). The PTW is a sliding window; that is, if your PTW is one week (the default), your traffic profile includes connection data collected over the last week. You can change the PTW to be as short as an hour or as long as several weeks.
When you first activate a traffic profile, it collects and evaluates connection data according to the criteria you have set, for a learning period equal in time to the PTW. The Defense Center does not evaluate rules you have written against the traffic profile until the learning period is complete.
You can create profiles using all the traffic on a monitored network segment, or you can create more targeted profiles using criteria based on the data in the connection events. For example, you could set the profile conditions so that the traffic profile only collects data where the detected session uses a specific port, protocol, or application. Or, you could add a host profile qualification to the traffic profile to collect data only for hosts that exhibit a host criticality of high .
Finally, when you create a traffic profile, you can specify inactive periods—periods in which connection data do not affect profile statistics and rules written against the profile do not trigger. You can also change how often the traffic profile aggregates and calculates statistics on collected connection data.
The following graphic shows a traffic profile with a PTW of one day and a sampling rate of five minutes.
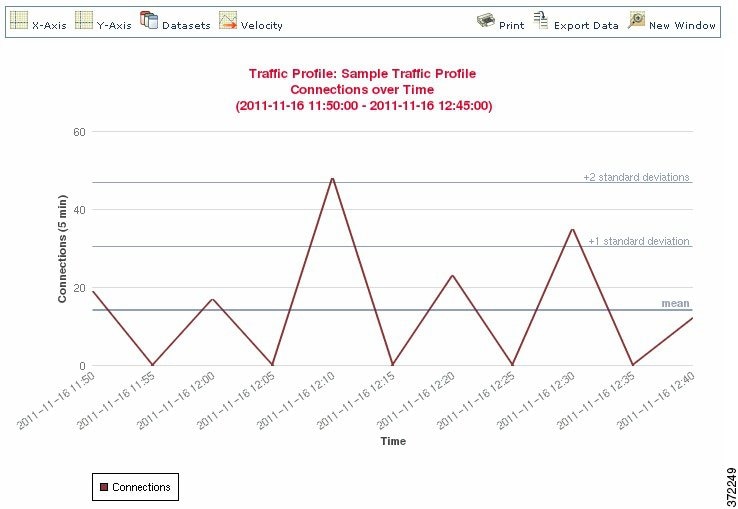
After you create and activate a traffic profile and its learning period is complete, you can create correlation rules that trigger when you detect anomalous traffic. For example, you could write a rule that triggers if the amount of data traversing your network (measured in packets, KBytes, or number of connections) suddenly spikes to three standard deviations above the mean amount of traffic, which could indicate an attack or other security policy violation. Then, you could include that rule in a correlation policy to alert you of the traffic spike or to perform a remediation in response. For information on using traffic profiles to detect abnormal network traffic, see Creating Rules for Correlation Policies.
You create traffic profiles on the Traffic Profiles page. The slider icon next to each profile indicates whether the profile is active. If you want to base a correlation rule on a traffic profile change, you must activate the profile. If the slider icon is blue with a check mark, the profile is active. If it is gray with an x, the profile is inactive. For more information, see Activating and Deactivating Traffic Profiles.
The progress bar shows the status of the traffic profile’s learning period. When the progress bar reaches 100%, correlation rules written against the profile will trigger.

Tip You can sort traffic profiles by state (active versus inactive) or alphabetically by name using the Sort by drop-down list.
Providing Basic Profile Information
When you create a traffic profile, you must give it a name and, optionally, a short description.
To begin creating a traffic profile:
Step 1 Select Policies > Correlation , then click Traffic Profiles .
The Traffic Profiles page appears.
The Create Profile page appears.
Step 3 In the Profile Name field, type a name of up to 255 characters for the new traffic profile.
Step 4 In the Profile Description field, type a short description of up to 255 characters of the new traffic profile.
Step 5 Continue with Specifying Traffic Profile Conditions.
Specifying Traffic Profile Conditions
Profile conditions constrain the kinds of connection data you want the traffic profile to track. A simple traffic profile that profiles all the traffic on a monitored network segment has no conditions. In contrast, traffic profiles can be complex, with multiple nested conditions.
For example, the traffic profile conditions in the following graphic collects HTTP connections on the 10.4.x.x subnet.
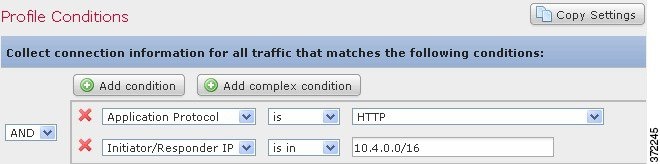
You build traffic profile conditions in the Profile Conditions section of the Create Profile page. See Understanding Condition-Building Mechanics for information on building conditions. Also, the syntax you can use to build conditions is fully described in Syntax for Traffic Profile Conditions.

Tip If you want to use the settings from an existing traffic profile, click Copy Settings and, in the pop-up window, select the traffic profile you want to use and click Load.
Syntax for Traffic Profile Conditions
The following table describes how to build a traffic profile condition.
Keep in mind that NetFlow records do not contain information about which host in the connection is the initiator and which is the responder. When the system processes NetFlow records, it uses an algorithm to determine this information based on the ports each host is using, and whether those ports are well-known. For more information, see Differences Between NetFlow and FireSIGHT Data.
The information available for a traffic profile depends on several factors, including the detection method, the logging method, and event type. For more information, see Information Available in Connection and Security Intelligence Events.
Select an application protocol name from the drop-down list of available protocols. |
|
Select an application protocol category name from the drop-down list of available categories. |
|
Select a client name from the drop-down list of available clients. |
|
Select a client category name from the drop-down list of available categories. |
|
Specify in the traffic profile whether you want to use connection data collected by your Cisco devices or by NetFlow-enabled devices. If you do not specify a connection type, the traffic profile includes both. |
|
Select a country from the drop-down list of available countries. This represents the country associated with a source or destination IP address identified in network traffic. |
|
Use a specific IP address or CIDR notation to specify a range of IP addresses.
See Specifying IP Addresses in Searches for a description of the syntax allowed for IP addresses. Note, however, that you
cannot
use the |
|
Select the NetFlow-enabled device whose data you want to use to create the traffic profile. If you did not add any NetFlow-enabled devices to your deployment (using the local configuration), the NetFlow Device drop-down list is blank. |
|
Select a Security Intelligence category name from the drop-down list of available categories. To use a Security Intelligence category for a traffic profile condition, that category must be set to Monitor instead of Block in the Security Intelligence section of your access control policy. For more information, see Building the Security Intelligence Whitelist and Blacklist. |
|
Select a web application name from the drop-down list of available web applications. |
|
Select a web application category name from the drop-down list of available categories. |
Adding a Host Profile Qualification
You can constrain any traffic profile with information from the host profile of the tracked hosts. This constraint is called a host profile qualification . For example, as shown in the following graphic, you could collect connection data only for hosts that are assigned a host criticality of high .

To use a host profile qualification, the host must exist in the database and the host profile property you want to use as a qualification must already be included in the host profile. For example, if you configure a correlation policy rule to trigger when an intrusion event is generated on a host running Windows, the rule only triggers if the host is already identified as Windows when the intrusion event is generated.
To add a host profile qualification:
Step 1 On the Create Profile page, click Add Host Profile Qualification .
The Host Profile Qualification section appears.
Step 2 Build the host profile qualification’s conditions.
You can create a single, simple condition, or you can create more elaborate constructs by combining and nesting conditions. See Understanding Condition-Building Mechanics for information building conditions.
The syntax you can use to build conditions is described in Syntax for Host Profile Qualifications.

Tip To remove a host profile qualification, click Remove Host Profile Qualification.
Syntax for Host Profile Qualifications
When you build a host profile qualification condition, you must first select the host you want to use to constrain your traffic profile. You can select either Responder Host or Initiator Host . After you select the host role, continue building your host profile qualification condition, as described in the Syntax for Host Profile Qualifications table.
Although you can configure the network discovery policy to add hosts to the network map based on data exported by NetFlow-enabled devices, the available information about these hosts is limited. For example, there is no operating system data available for these hosts, unless you provide it using the host input feature. In addition, if your traffic profile uses connection data exported by NetFlow-enabled devices, keep in mind that NetFlow records do not contain information about which host in the connection is the initiator and which is the responder. When the system processes NetFlow records, it uses an algorithm to determine this information based on the ports each host is using, and whether those ports are well-known. For more information, see Differences Between NetFlow and FireSIGHT Data.
To match against implied or generic clients, create a host profile qualification based on the application protocol used by the server responding to the client. When the client list on a host that acts as the initiator or source of a connection includes an application protocol name followed by client , that client may actually be an implied client. In other words, the system reports that client based on server response traffic that uses the application protocol for that client, not on detected client traffic.
For example, if the system reports HTTPS client as a client on a host, create a host profile qualification for Responder Host where Application Protocol is set to HTTPS , because HTTPS client is reported as a generic client based on the HTTPS server response traffic sent by the responder or destination host.
Select one or more host types from the drop-down list. You can choose between a normal host or one of several types of network device. |
|
Select one or more operating system vendor names from the drop-down list. |
|
Select one or more operating system names from the drop-down list. |
|
Select one or more operating system versions from the drop-down list. |
|
Type the network protocol number as listed in http://www.iana.org/assignments/ethernet-numbers . |
|
Type the name or number of the transport protocol as listed in http://www.iana.org/assignments/protocol-numbers . |
|
Select the host criticality from the list that appears. You can select None , Low , Medium , or High . For more information on host criticality, see Working with the Predefined Host Attributes. |
|
Select whether the MAC type is ARP/DHCP Detected . That is, select whether the system positively identified the MAC address as belonging to the host ( is ARP/DHCP Detected ), whether the system is seeing many hosts with that MAC address because, for example, there is a router between the device and the host ( is not ARP/DHCP Detected ), or whether the MAC type is irrelevant ( is any ). |
|
Type all or part of the MAC vendor of hardware used by the host. |
|
any available host attribute, including the default compliance white list host attribute |
Specify the appropriate value, which depends on the type of host attribute you select:
For more information on host attributes, see Working with User-Defined Host Attributes. |
Setting Profile Options
The profiling time window (PTW) is the sliding time window, equal in length to the learning period, that the FireSIGHT System uses to calculate statistics for the traffic profile. The default PTW is one week, but you can change it to be as short as an hour or as long as several weeks.
Also, traffic profiles are based on aggregated connection data. By default, traffic profiles generate statistics on connection events generated by the system over five-minute intervals. However, you can set this sampling rate anywhere between the default five minutes and one hour.
Keep in mind that you should set your PTW and sampling rate so that your traffic profiles contain enough data to be statistically meaningful. For example, a PTW of one day with a sampling rate of one hour would only contain 24 data points, which may not be enough for accurate analysis of network traffic patterns.

Tip Your PTW should include at least 100 data points.
You can also set up inactive periods in traffic profile. For example, consider a network infrastructure where all the workstations are backed up at midnight every night. The backup takes about 30 minutes and spikes the network traffic. In that case, you might want to set up a recurring inactive period for your traffic profile to coincide with the scheduled backups. During inactive periods, the traffic profile collects data (so you can see the traffic on the traffic profile graphs), but that data is not used when calculating profile statistics. You can set up inactive periods to recur daily, weekly, or monthly. Inactive periods can be as short as five minutes or as long as one hour. Traffic profile graphs plotted over time show inactive periods as a shaded region.
Saving a Traffic Profile
Use the following procedure to save a traffic profile.
- To save the profile without activating it, click Save .
- To save the profile and start collecting data immediately, click Save & Activate .
Activating and Deactivating Traffic Profiles
When you want it to begin profiling the traffic on a monitored network segment, you must activate a traffic profile.
Deactivate a profile when you want it to stop collecting and evaluating connection data. Rules written against deactivated traffic profiles do not trigger. In addition, deactivating a traffic profile deletes all data collected and aggregated by the profile. If you later reactivate a deactivated traffic profile, you must wait the length of its PTW before rules written against it will trigger.
To activate or deactivate a traffic profile:
Step 1 Select Policies > Correlation , then click Traffic Profiles .
The Traffic Profiles page appears.
Editing a Traffic Profile
You cannot substantially edit an active traffic profile; if the traffic profile is active you can only change its name and description. To edit a traffic profile’s conditions options, you must first deactivate it. Note that deactivating a traffic profile deletes all the data it has collected.
For more information on activating and deactivating traffic profiles, see Activating and Deactivating Traffic Profiles.
Step 1 Select Policies > Correlation , then click Traffic Profiles .
The Traffic Profiles page appears.
Step 2 Next to the traffic profile you want to edit, click Edit .
The Create Profile page appears.
Step 3 Make changes to the profile and click Save .
Understanding Condition-Building Mechanics
You build traffic profiles by specifying the conditions they use to collect data. You can create either simple conditions or more elaborate constructs with nested conditions.
For example, if you want to create a traffic profile that collects data for your entire monitored network segment, you can create a very simple profile with no conditions, as shown in the following graphic.

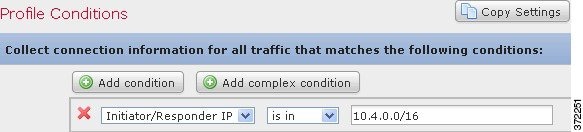
If you wanted to constrain the profile and collect data only for the 10.4.x.x network, you can add a single condition, as shown in the following graphic.
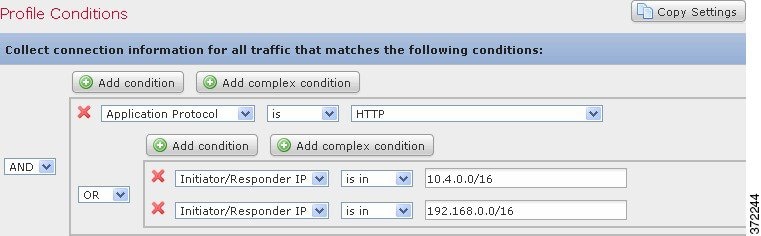
But the following traffic profile, which collects HTTP activity on the 10.4.x.x network and the 192.168.x.x network, has three conditions, with the last constituting a complex condition.
The syntax you can use within conditions varies depending on the element you are creating, but the mechanics are the same. For more information, see:
Building a Single Condition
Most conditions have three parts: a category, an operator, and a value. Some conditions are more complex and contain several categories, each of which may have their own operators and values.
For example, the following traffic profile collects information on the 10.4.x.x network. The category of the condition is
Initiator/Responder IP
, the operator is
is in
, and the value is
10.4.0.0/16
.

The following steps explain how to build this traffic profile condition.
Step 1 Select Policies > Correlation , then click Traffic Profiles .
The Traffic Profiles page appears.
The Create Profile page appears.
Step 3 Under Profile Conditions , begin building the profile’s single condition by selecting Initiator/Responder IP from the first (category) drop-down list.
Step 4 Select is in from the second (operator) drop-down list.

Tip When the category represents an IP address, choosing is in or is not in as the operator allows you to specify whether the IP address is in or is not in a range of IP addresses, as expressed in CIDR notation. For information on using CIDR notation in the FireSIGHT System, see IP Address Conventions.
Step 5 Type
10.4.0.0/16
in the text field.
In contrast, the following host profile qualification is more complex; it constrains a traffic profile such that it collects connection data only if the responding host in the detected connection is running a version of Microsoft Windows.
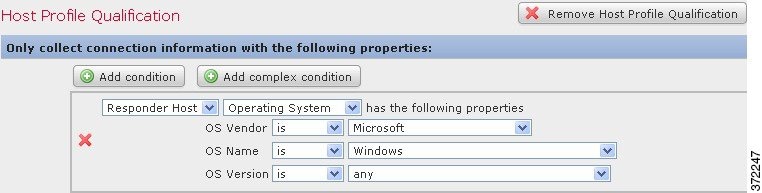
The following steps explain how to build this host profile qualification.
To build this host profile qualification:
Step 1 Select Policies > Correlation , then click Traffic Profiles .
The Traffic Profiles page appears.
The Create Profile page appears.
Step 3 Click Add Host Profile Qualification .
Step 4 Under Host Profile Qualification , in the first condition, specify the host whose information you want to collect.
In this example, select Responder Host because we only want information on responding hosts in a connection.
Step 5 Begin specifying the details of the operating system of the host by choosing the Operating System category.
Three subcategories appear: OS Vendor , OS Name , and OS Version .
Step 6 To specify that the host can be running any version of Microsoft Windows, use the same operator for all three subcategories: is .
Step 7 Finally, specify the values for the subcategories.
Select Microsoft as the value for OS Vendor , Windows as the value for OS Name , and leave any as the value for OS Version .
Note that the categories you can choose from depend on whether you are building traffic profile conditions or a host profile qualification. In addition, a condition’s available operators depend on the category you choose. Finally, the syntax you can use to specify a condition’s value depends on the category and operator. Sometimes you must type the value in a text field. Other times, you can pick a value from a drop-down list.

Note Where the condition syntax allows you to pick a value from a drop-down list, you can often use multiple values from the list. For more information, see Using Multiple Values in a Condition.
For information on the syntax for building traffic profile conditions and host profile qualifications, see:
Adding and Linking Conditions
You can create simple traffic profile conditions and host profile qualifications, or you can create more elaborate constructs by combining and nesting conditions.
When your construct includes more than one condition, you must link them with an AND or an OR operator. Conditions on the same level are evaluated together:
- The AND operator requires that all conditions on the level it controls must be met.
- The OR operator requires that at least one of the conditions on the level it controls must be met.
For example, the following traffic profile contains two conditions linked by AND . This means that the traffic profile collects connection data only if both conditions are true. In this example, it collects HTTP connections for all hosts with IP addresses in the 10.4.x.x subnet.

In contrast, the following traffic profile, which collects connection data for HTTP activity in either the 10.4.x.x network or the 192.168.x.x network, has three conditions, with the last constituting a complex condition.

Logically, the above traffic profile is evaluated as follows:
Step 1 To add a single condition, click Add condition above the current condition.
A new condition is added to the same logical level as the current set of conditions. By default, it is linked to the conditions on its level with the OR operator, though you can change the operator to AND .
For example, if you add a simple condition to the following host profile qualification:

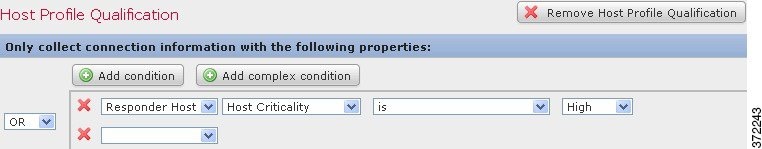
Step 1 Click Add complex condition above the current condition.
A complex condition is added below the current set of conditions. The complex condition comprises two subconditions, which are linked to each other with the opposite operator from the one used to link the conditions on the level above it.
For example, if you add a complex condition to the following host profile qualification:


Step 1 Use the drop-down list to the left of a set of conditions:
- To require that all conditions on the level that the operator controls are met, select AND .
- To require that only one of the conditions on the level that the operator controls is met, select OR .
Using Multiple Values in a Condition
When you are building a condition, and the condition syntax allows you to pick a value from a drop-down list, you can often use multiple values from the list. For example, if you want to add a host profile qualification to a traffic profile that requires that a host be running some flavor of UNIX, instead of constructing multiple conditions linked with the OR operator, use the following procedure.
To include multiple values in one condition:
Step 1 Build a condition, choosing is in or is not in as the operator.
The drop-down list changes to a text field.
Step 2 Click anywhere in the text field or on the Edit link.
Step 3 Under Available , use Ctrl or Shift while clicking to select multiple values. You can also click and drag to select multiple adjacent values.
Step 4 Click the right arrow ( > ) to move the selected entries to Selected .
Your selections appear in the value field of your condition on the Create Profile page.
Viewing Traffic Profiles
Because traffic profiles are based on connection data, you can view graphs of traffic profiles. The following graphic shows a traffic profile with a PTW of one week, a sampling rate of five minutes, and a daily half-hour inactive period from midnight to 12:30 AM.

You can perform almost all the same actions on traffic profile graphs that you can perform on connection data graphs. However, because traffic profiles are based on aggregated data (connection summaries), you cannot examine the individual connection events on which the graphs are based. In other words, you cannot drill down to a connection data table view from a traffic profile graph. See Viewing Connection and Security Intelligence Data for more information. In addition, traffic profiles appear as detached graphs. For more information, see Detaching Connection Graphs.
In addition, traffic profile graphs plotted over time show the mean (average) y-axis value as a bold horizontal line. Graphs over time also plot the values of the first four standard deviations above and below the mean, assuming that network traffic is distributed normally. By default, these statistics are calculated over the PTW, but if you alter the time settings for a graph, the Defense Center recalculates the statistics. Rules written against traffic profile statistics, however, are always evaluated against the statistics for the PTW.
To view a traffic profile graph for a traffic profile:
Step 1 Select Policies > Correlation , then click Traffic Profiles .
The Traffic Profiles page appears.
Step 2 Next to the traffic profile for which you want to view the graph, click the graph icon ( ).
).
The graph for the traffic profile appears in a separate browser window.
 Feedback
Feedback