- Title Page
- Introduction & Preface
- Logging into the FireSIGHT System
- Using Objects and Security Zones
- Managing Devices
- Setting Up an IPS Device
- Setting Up Virtual Switches
- Setting Up Virtual Routers
- Setting Up Aggregate Interfaces
- Setting Up Hybrid Interfaces
- Using Gateway VPNs
- Using NAT Policies
- Getting Started with Access Control Policies
- Blacklisting Using Security Intelligence IP Address Reputation
- Tuning Traffic Flow Using Access Control Rules
- Controlling Traffic with Network-Based Rules
- Controlling Traffic with Reputation-Based Rules
- Controlling Traffic Based on Users
- Controlling Traffic Using Intrusion and File Policies
- Understanding Traffic Decryption
- Getting Started with SSL Policies
- Getting Started with SSL Rules
- Tuning Traffic Decryption Using SSL Rules
- Understanding Intrusion and Network Analysis Policies
- Using Layers in Intrusion and Network Analysis Policies
- Customizing Traffic Preprocessing
- Getting Started with Network Analysis Policies
- Using Application Layer Preprocessors
- Configuring SCADA Preprocessing
- Configuring Transport & Network Layer Preprocessing
- Tuning Preprocessing in Passive Deployments
- Getting Started with Intrusion Policies
- Tuning Intrusion Rules
- Tailoring Intrusion Protection to Your Network Assets
- Detecting Specific Threats
- Limiting Intrusion Event Logging
- Understanding and Writing Intrusion Rules
- Blocking Malware and Prohibited Files
- Logging Connections in Network Traffic
- Working with Connection & Security Intelligence Data
- Analyzing Malware and File Activity
- Working with Intrusion Events
- Handling Incidents
- Configuring External Alerting
- Configuring External Alerting for Intrusion Rules
- Introduction to Network Discovery
- Enhancing Network Discovery
- Configuring Active Scanning
- Using the Network Map
- Using Host Profiles
- Working with Discovery Events
- Configuring Correlation Policies and Rules
- Using the FireSIGHT System as a Compliance Tool
- Creating Traffic Profiles
- Configuring Remediations
- Using Dashboards
- Using the Context Explorer
- Working with Reports
- Understanding and Using Workflows
- Using Custom Tables
- Searching for Events
- Managing Users
- Scheduling Tasks
- Managing System Policies
- Configuring Appliance Settings
- Licensing the FireSIGHT System
- Updating System Software
- Monitoring the System
- Using Health Monitoring
- Auditing the System
- Using Backup and Restore
- Specifying User Preferences
- Importing and Exporting Configurations
- Purging Discovery Data from the Database
- Viewing the Status of Long-Running Tasks
- Command Line Reference
- Security, Internet Access, and Communication Ports
- Third-Party Products
- glossary
Analyzing Malware and File Activity
The Defense Center logs records of the system’s file inspection and handling as captured files, file events, and malware events:
- Captured files represent files that the system captured.
- File events represent files that the system detected, and optionally blocked, in network traffic.
- Malware events represent malware files detected, and optionally blocked, in network traffic by the system.
- Retrospective malware events represent files whose malware file dispositions have changed.
When the system generates a malware event based on detection or blocking of malware in network traffic, it also generates a file event, because to detect malware in a file, the system must first detect the file itself. Note that endpoint-based malware events generated by FireAMP Connectors (see Integrating FireAMP with the FireSIGHT System) do not have corresponding file events. Similarly, when the system captures a file in network traffic, it also generates a file event because the system first detected the file.
You can use the Defense Center to view, manipulate, and analyze captured files, file events, and malware events, then communicate your analysis to others. The Context Explorer, dashboards, event viewer, context menu, network file trajectory map, and reporting features can give you a deeper understanding of the files and malware detected, captured, and blocked. You can also use events to trigger correlation policy violations, or alert you via email, SMTP, or syslog.
Because you cannot use a Malware license with a DC500 or enable a Malware license on a Series 2 device or Cisco NGIPS for Blue Coat X-Series, you cannot use those appliances to generate or analyze captured files, file events, and malware events associated with malware cloud lookups or with the contents of archive files.
- Working with File Storage
- Working with Dynamic Analysis
- Working with File Events
- Working with Malware Events
- Working with Captured Files
- Working with Network File Trajectory
For information on configuring your system to perform the malware protection and file control actions that produce the data discussed in this chapter, see Blocking Malware and Prohibited Files.
Working with File Storage
Supported Devices: Any except Series 2 or X-Series
Supported Defense Centers: Any except DC500
Based on your file policy configuration, you can use the file control feature to detect and block files. However, files originating from a suspicious host or network, or an excess of files sent to a monitored host on your network, may require further analysis. The file storage feature allows you to capture selected files detected in traffic, and automatically store them to a device’s hard drive or, if installed, the malware storage pack.
When a device detects a file in traffic, it can capture that file. This creates a copy the system can either store or submit for dynamic analysis. After your device captures the files, you have several options:
- Store captured files on the device’s hard drive for later analysis. See Understanding Captured File Storage for more information.
- Download the stored file to a local computer for further manual analysis or archival purposes. See Downloading Stored Files to Another Location for more information.
- Submit captured files to the Collective Security Intelligence Cloud for dynamic analysis. See Working with Dynamic Analysis for more information.
Note that once a device stores a file, it will not re-capture it if the file is detected in the future and the device still has that file stored.

Note A file detected for the first time ever is assigned a disposition after the Defense Center completes a cloud lookup. The system generates a file event, but cannot store a file unless the file is immediately assigned a disposition.
If a previously undetected file matches a file rule with a Block Malware action, the subsequent cloud lookup immediately returns a disposition, allowing the system to store the file and generate events.
If a previously undetected file matches a file rule with a Malware Cloud Lookup action, the system generates file events but requires additional time to perform a cloud lookup and return a disposition. Due to this delay, the system cannot store files matching a file rule with a Malware Cloud Lookup action until the second time they are seen on your network.
Whether the system captures or stores a file, you can:
- Review information about the captured file from the event viewer, including whether the file was stored or submitted for dynamic analysis, file disposition, and threat score, allowing you to quickly review possible malware threats detected on your network. See Working with Captured Files for more information.
- View the file’s trajectory to determine how it traversed your network and which hosts have a copy. See Analyzing Network File Trajectory for more information.
- Add the file to the clean list or custom detection list to always treat the file as if it had a clean or malware disposition on future detection. See Working with File Lists for more information.
You configure file rules in a file policy to capture and store files of a specific type, or with a particular file disposition, if available. After you associate the file policy with an access control policy and apply it to your devices, matching files in traffic are captured and stored. You can also limit the minimum and maximum file sizes to store. See Tuning File and Malware Inspection Performance and Storage and Working with File Rules for more information.
File storage requires sufficient disk space on the device. If the device’s primary hard drive does not have enough space, and you do not have a malware storage pack installed, you cannot store files on the device.

Note that because you cannot use a Malware license with a DC500 or enable a Malware license on a Series 2 device or Cisco NGIPS for Blue Coat X-Series, you cannot use those appliances to capture or store files.
Understanding Captured File Storage
Supported Devices: 8000 Series
Based on your file policy configuration, your device may store a substantial amount of file data to the hard drive. You can install a malware storage pack in the device; the system stores files to the malware storage pack, allowing more room on the primary hard drive to store events and configuration files. The system periodically deletes older files.

Without a malware storage pack installed, when you configure a device to store files, it allocates a set portion of the primary hard drive’s space solely to captured file storage. When you install a malware storage pack in a device and configure the device to store files, the device instead allocates the entire malware storage pack for storing captured files. The device cannot store any other information on the malware storage pack.
When the allocated space for captured file storage fills to capacity, the system deletes the oldest stored files until the allocated space reaches a system-defined threshold. Based on the number of files stored, you may see a substantial drop in disk usage after the system deletes files.
If a device has already stored files when you install a malware storage pack, the next time you restart the device, any captured files stored on the primary hard drive are moved to the malware storage pack. Any future files the device stores are stored to the malware storage pack. If the device’s primary hard drive does not have enough available space nor an installed malware storage pack, you cannot store files.
Note that you cannot include stored files in system backup files. For more information, see Creating Backup Files.
Downloading Stored Files to Another Location
Supported Devices: Any except Series 2 or X-Series
Supported Defense Centers: Any except DC500
Once a device stores a file, as long as the Defense Center can communicate with that device and it has not deleted the file, you can download the file. You can manually analyze the file, or download it to a local host for long-term storage and analysis. You can download a file from any associated file event, malware event, captured file view, or the file’s trajectory. For more information, see Using the Context Menu and Summary Information.
Because malware is harmful, by default, you must confirm every file download. However, you can disable the confirmation in the file download prompt. To re-enable the confirmation, see File Preferences.

Because files with a disposition of Unknown may contain malware, when you download a file, the system first archives the file in a
.zip
package. The
.zip
file name contains the file disposition and file type, if available, and SHA-256 value. You can password-protect the
.zip
file to prevent accidental unpacking. To edit or remove the default
.zip
file password, see File Preferences.
Working with Dynamic Analysis
Supported Devices: Any except Series 2 or X-Series
Supported Defense Centers: Any except DC500
To increase the accuracy of the cloud, and to provide additional malware analysis and threat identification, you can submit eligible captured files to the Cisco cloud for dynamic analysis. The cloud runs the file in a test environment and, based on the results, returns a threat score and dynamic analysis summary report to the Defense Center. You can also submit eligible files to the cloud for Spero analysis, which examines the file’s structure to supplement the malware identification.
Submitting a file to the cloud for dynamic analysis depends on the type of file captured, as well as the allowable minimum and maximum file sizes configured in the access control policy. You can submit:
- a file automatically for dynamic analysis if a file rule performs a malware cloud lookup on an executable file and the file disposition is Unknown
- up to twenty-five files at once manually for dynamic analysis if stored and a supported file type, such as PDFs, Microsoft Office documents, and others
Once submitted, the files are queued for analysis in the cloud. You can view captured files and a file’s trajectory to determine whether a file has been submitted for dynamic analysis. Note that each time a file is submitted for dynamic analysis, the cloud analyzes the file, even if the first analysis generated results.
For more information, see Working with File Rules and Submitting Files for Dynamic Analysis.

Note The system checks the cloud for updates to the list of file types eligible for dynamic analysis and the minimum and maximum file sizes you can submit (no more than once a day).
The cloud performs dynamic analysis by running the file in a sandbox environment. It returns:
- a threat score, which details the likelihood a file contains malware.
- a dynamic analysis summary report, which details why the cloud assigned the threat score.
Based on the file policy configuration, you can automatically block files whose threat score falls above a defined threshold. You can also review the dynamic analysis summary report to better identify malware and fine-tune your detection capabilities.
To supplement dynamic analysis, if a file rule performs a malware cloud lookup on an executable file, you can automatically submit the file for Spero analysis. The cloud examines the executable file’s structure, including metadata and header information, and can identify files as malware. See Understanding Malware Protection and File Control for more information.
Note that because you cannot use a Malware license with a DC500 or enable a Malware license on a Series 2 device or Cisco NGIPS for Blue Coat X-Series, you cannot use those appliances to submit files for dynamic analysis or Spero analysis.

Note You can configure your managed devices to submit files to the Cisco cloud via HTTP proxy. To configure physical appliances, see Configuring Management Interfaces for more information. To configure virtual appliances, see http-proxy. Cisco NGIPS for Blue Coat X-Series does not support proxy settings.
- Understanding Spero Analysis
- Submitting Files for Dynamic Analysis
- Reviewing the Threat Score and Dynamic Analysis Summary
Understanding Spero Analysis
Supported Devices: Any except Series 2 or X-Series
Supported Defense Centers: Any except DC500
Spero analysis supplements analysis of SHA-256 hashes, allowing for more complete identification of malware in executable files. Spero analysis involves the device examining file structural characteristics such as metadata and header information. After generating a Spero signature based on this information, the device submits it to the Spero heuristic engine in the Cisco cloud. Based on the Spero signature, the Spero engine returns whether the file is malware. If so, and the file currently has an unknown file disposition, the system assigns a Malware file disposition. For more information on file dispositions, see Understanding Malware Protection and File Control.
Note that you can only submit executable files for Spero analysis upon detection; you cannot manually submit them later. You can submit the file for Spero analysis without also submitting it for dynamic analysis. For more information, see Working with File Rules.
Submitting Files for Dynamic Analysis
Supported Devices: Any except Series 2 or X-Series
Supported Defense Centers: Any except DC500
From the event viewer context menu or network file trajectory, you can manually submit a file for dynamic analysis. In addition to executable files, you can also submit file types not eligible for automatic submission, such as PDFs, Microsoft Office documents, and others. See Using the Context Menu and Summary Information for more information.
To analyze multiple files after an incident, regardless of file disposition, you can manually submit up to 25 files (of specific types) at a time from the captured file view. This allows you to more quickly analyze a broad range of files and pinpoint the exact causes of the incident. For more information, see Working with Captured Files and Selecting Rows on a Workflow Page.
Reviewing the Threat Score and Dynamic Analysis Summary
Supported Devices: Any except Series 2 or X-Series
Supported Defense Centers: Any except DC500
After you submit a file for dynamic analysis, the Cisco cloud analyzes a file’s signatures and returns both a threat score and a dynamic analysis summary. These can help you more closely analyze potential malware threats and fine tune your detection strategy.
Files fall into one of four threat score ratings that correspond with the likelihood the file is malicious:
The Defense Center caches a file’s threat score locally for the same amount of time as the file’s disposition. If the system later detects these files, it displays the cached threat scores to the user instead of again querying the Cisco cloud. Based on your file policy configuration, you can automatically assign a malware file disposition to any file with a threat score that exceeds the defined malware threshold threat score. For more information, see Creating a File Policy.
If a dynamic analysis summary is available, you can click the threat score icon to view it. The dynamic analysis summary describes the various component ratings that comprise the overall threat score assigned by the Vulnerability Research Team (VRT) file analysis, as well as other processes started when the cloud attempted to run the file.
If multiple reports exist, this summary is based on the most recent report matching the exact threat score. If none match the exact threat score, then the report with the highest threat score is displayed. If more than one report exists, you can select a threat score to view each separate report.
The summary lists each component threat comprising the threat score. Each component threat is expandable to list the VRT’s findings, as well as any processes related to this component threat.
The process tree shows the processes that started when the cloud attempted to run the file. This can help identify whether a file that contains malware is attempting to access processes and system resources beyond what is expected (for example, running a Word document opens Microsoft Word, then starts Explorer, then starts Java).
Each listed process contains a process identifier and md5 checksum you can use to verify the actual process. The process tree displays processes started as a result of parent processes as child nodes.
From the dynamic analysis summary, you can click View Full Report to view the VRT’s Analysis report, detailing the VRT’s full analysis, including general file information, a more in-depth review of all detected processes, a breakdown of the file analysis, and other relevant information.
Working with File Events
The system logs the file events generated when a managed device detects or blocks a file in network traffic, according to the rules in currently applied file policies. Note that when the system generates a file event, the system also logs the end of the associated connection to the Defense Center database, regardless of the logging configuration of the invoking access control rule. For more information, see Understanding and Creating File Policies.

Note Files detected in network traffic and identified as malware by the FireSIGHT System generate both a file event and a malware event. This is because to detect malware in a file, the system must first detect the file itself. Endpoint-based malware events do not have corresponding file events. For more information, see Working with Malware Events and Working with Captured Files.
You can use the Defense Center’s event viewer to view, search, and delete file events. Additionally, the Files Dashboard provides an at-a-glance view of detailed information about the files (including malware files) detected on your network, using charts and graphs. Network file trajectory offers a more in-depth view of individual files, providing summary information about the file and how it has moved through the network over time. Using file identification data, you can trigger correlation rules and create reports, the latter using either the predefined Files Report template or a custom report template.
Viewing File Events
The FireSIGHT System’s event viewer allows you to view file events in a table, as well as manipulate the event view depending on the information relevant to your analysis. Note that the information available for any individual file event depends on several factors, including licenses. For more information, see Service Subscriptions.
The page you see when you access file events differs depending on the workflow, which is simply a series of pages you can use to evaluate events by moving from a broad to a more focused view. The system is delivered with the following predefined workflows for file events:
- File Summary , the default, provides a quick breakdown of the different file event categories and types, along with any associated malware file dispositions.
- Hosts Receiving Files and Hosts Sending Files provide a list of hosts that have received or sent files, grouped by the associated malware dispositions for those files.

Note File dispositions appear only for files for which the system performed a malware cloud lookup; see File Rule Actions and Evaluation Order.
You can also create a custom workflow that displays only the information that matches your specific needs. For information on specifying a different default workflow, including a custom workflow, see Configuring Event View Settings.
The FireSIGHT System supports the display and input of file names that use Unicode (UTF-8) characters in all areas of the web interface, including the event viewer, event search, dashboard, Context Explorer, and so on. Note, however, that reports you generate in PDF format do not support Unicode; Unicode file names appear in the PDF report in transliterated form. For more information, see Generating and Viewing Reports. Note also that the SMB protocol converts Unicode file names to printable characters; files you detect over SMB that have Unicode file names appear with periods (
.
) in place of any unprintable characters.
Using the event viewer, you can:
- search for, sort, and constrain events, as well as change the time range for displayed events
- specify the columns that appear (table view only)
- view the host profile associated with an IP address, or the user details and host history associated with a user identity
- view the connections where specific files were detected
- view events using different workflow pages within the same workflow
- view events using a different workflow altogether
- drill down page-to-page within a workflow, constraining on specific values
- bookmark the current page and constraints so you can return to the same data (assuming the data still exists) at a later time
- view the sending and receiving countries and continents for routable IP addresses associated with a file
- view a file’s trajectory
- add a file to a file list, download a file, submit a file for dynamic analysis, or view the full text of a file’s SHA-256 value
- view a file’s Dynamic Analysis Summary report, if available
- view nested files inside an archive file
- create a report template using the current constraints
- delete events from the database
- use the IP address context menu to whitelist, blacklist, or obtain additional available information about a host or IP address associated with a file event
For detailed information on using the event viewer, including creating custom workflows, see Understanding and Using Workflows.
To quickly view the connections where specific files were detected, select the files using the check boxes in the event viewer, then select Connections Events from the Jump to drop-down list. For more information, see Navigating Between Workflows.
Access: Admin/Any Security Analyst
Step 1 Select Analysis > Files > File Events .
The first page of your default file events workflow appears. For information on the columns that appear, see Understanding the File Events Table.
Understanding the File Events Table
The Defense Center logs a file event when a managed device detects or blocks a file being transmitted in monitored network traffic, according to the settings in an applied file policy.
The table view of file events, which is the final page in predefined file event workflows, and which you can add to custom workflows, includes a column for each field in the files table. Some fields in the table view of file events are disabled by default. To enable a field for the duration of your session, click the expand arrow ( ) to expand the search constraints, then click the column name under
Disabled Columns
.
) to expand the search constraints, then click the column name under
Disabled Columns
.
Keep in mind that the information available for any individual file event depends on several factors, including licenses. For example, although you can perform file control with only a Protection license, a Malware license allows you to perform advanced malware protection for certain file types and track files transferred on your network.
The following table describes the file event fields.
The action associated with the file policy rule that detected the file, and any associated file action options. |
|
The country of the host sending the detected file. Note that the DC500 Defense Center does not support this feature. |
|
The country of the host receiving the detected file. Note that the DC500 Defense Center does not support this feature. |
|
The source port used by the traffic where the file was detected. |
|
The destination port used by the traffic where the file was detected. |
|
The action associated with the SSL rule, default action, or undecryptable traffic action that logged the encrypted connection:
If the system fails to decrypt an encrypted connection, it displays the undecryptable traffic action taken, as well as the failure reason. For example, if the system detects traffic encrypted with an unknown cipher suite and allowed it without further inspection, this field displays
Click the lock icon ( |
|
The user logged into the host ( Receiving IP ) where the file was destined. Note that because the user is associated with the destination host, users are not associated with file events where the user uploaded a file. |
|
One of the following file dispositions:
|
|
The SHA-256 hash value of the file, as well as a network file trajectory icon representing the most recently detected file event and file disposition, if this file was detected as the result of:
To view the network file trajectory, click the trajectory icon. For more information, see Analyzing Network File Trajectory. |
|
The threat score most recently associated with this file: To view the Dynamic Analysis Summary report, click the threat score icon. |
|
The general categories of file type, for example: |
|
The size of the file, in kilobytes. Note that if the system determines the file type of a file before the file is fully received, the file size may not be calculated and this field is blank. |
|
The originating URI of the file, for example, the URL where a user downloaded it. |
|
Name of the archive file (if any) with which the file is associated, for example, |
|
The SHA-256 hash value of the archive file (if any) with which the file is associated. |
|
The level (if any) at which the file was nested in an archive file, for example, |
|
The application protocol used by the traffic in which a managed device detected the file. |
|
Application Protocol, Client, or Web Application Category or Tag |
Criteria that characterize the application to help you understand the application's function; see Table 45-2. |
The client application used in the connection to transmit a file. |
|
For files transmitted using HTTP, the web application (content or requested URL) detected in the connection and used to transmit the file. |
|
The risk associated with the application traffic detected in the connection: |
|
The business relevance associated with the application traffic detected in the connection: |
|
For files where a malware disposition has changed, that is, for files associated with retrospective malware events, information about when and how the disposition changed. |
|
The metadata identifying the virtual firewall group through which the traffic passed. Note that the system only populates this field for ASA FirePOWER devices in multiple context mode. |
|
The number of events that match the information in each row. This field appears after you apply a constraint that creates two or more identical rows. |
Searching for File Events
Using the Defense Center’s Search page, you can search for specific file events, display the results in the event viewer, and save your search criteria to reuse later. Custom Analysis dashboard widgets, report templates, and custom user roles can also use saved searches.
Keep in mind that your search results depend on the available data in the events you are searching. In other words, depending on the available data, your search constraints may not apply. For example, the Disposition and SHA256 fields are populated only for files for which the Defense Center performed a malware cloud lookup.
The system displays examples of valid syntax next to each search field. When entering search criteria, keep the following points in mind:
-
All fields accept negation (
!). - All fields accept comma-separated lists of search values. Records that contain any of the listed values in the specified field match that search criteria.
- All fields accept comma-separated lists enclosed in quotation marks as search values.
– For fields that may contain only a single value, records with the specified field containing the exact string specified within the quotation marks match the search criteria. For instance, a search for
A, B, "C, D, E"
will match records where the specified field contains
"A"
or
"B"
or
"C, D, E"
. This permits matching on fields that include the comma in possible values.
– For fields that may contain multiple values at the same time, records with the specified fields containing all of the values in the quote-enclosed comma-separated list match that search criteria.
– For fields that may contain multiple values at the same time, search criteria may include single values as well as quote-enclosed comma-separated lists. For instance, a search for
A, B, "C, D, E"
on a field that may contain one of more of these letters matches records where the specified field contains
A
or
B
, or all of
C
,
D
, and
E
.
- Searches return only records that match the search criteria specified for all fields.
-
Many fields accept one or more asterisks (
*) as wild cards. -
Specify
n/ain any field to identify events where information is not available for that field; use!n/ato identify the events where that field is populated. - Use the device field to search for specific devices as well as devices in groups, stacks, or clusters. For more information on how the FireSIGHT System treats the device field in searches, see Specifying Devices in Searches.
- Click the add object icon (
 ) that appears next to a search field to use an object as a search criterion.
) that appears next to a search field to use an object as a search criterion.For detailed information on search syntax, including using objects in searches, see Searching for Events.
Special Search Syntax for File Events
To supplement the general search syntax listed above, the following list describes some special search syntax for file events.
The system returns all events where either the Sending Continent or the Receiving Continent matches the continent you specify.
The System returns all events where either the Sending Country or the Receiving Country matches the country you specify.
The system returns all events where either the Sending IP or the Receiving IP matches the IP address you specify.
The system performs a partial match, that is, you can search for all or part of the field contents without using asterisks.
Type one or more of the following:
–
Stored
returns all events where the associated file is currently stored.
–
Stored in connection
returns all events where the system captured and stored the associated file, regardless of whether the associated file is currently stored.
–
Failed
returns all events where the system failed to store the associated file.
Type any of the following keywords to view file events for encrypted traffic to which the system applied the action specified:
–
Do Not Decrypt
represents connections the system did not decrypt.
–
Block
and
Block with Reset
represent blocked encrypted connections.
–
Decrypt (Known Key)
represents incoming connections decrypted using a known private key.
–
Decrypt (Replace Key)
represents outgoing connections decrypted using a self-signed server certificate with a substituted public key.
–
Decrypt (Resign)
represents outgoing connections decrypted using a re-signed server certificate.
This column does not appear in the file events table view.
Type any of the following keywords to view file events for encrypted traffic that the system failed to decrypt for the reason specified:
–
Session Undecryptable in Passive Mode
–
Pending Server Name Category Lookup
–
Pending Common Name Category Lookup
–
Network Parameters Unavailable
–
Invalid Server Certificate Handle
–
Server Certificate Fingerprint Unavailable
–
External Certificate List Unavailable
–
External Certificate Fingerprint Unavailable
–
Internal Certificate List Invalid
–
Internal Certificate List Unavailable
–
Internal Certificate Unavailable
–
Internal Certificate Fingerprint Unavailable
–
Server Certificate Validation Unavailable
–
Server Certificate Validation Failure
This column does not appear in the file events table view.
Type a two-character ISO 3166-1 alpha-2 country code to view file events for encrypted traffic associated with the country of a certificate subject.
This column does not appear in the file events table view.
Type a two-character ISO 3166-1 alpha-2 country code to view file events for encrypted traffic associated with the country of a certificate issuer.
This column does not appear in the file events table view.
Type or paste the SHA hash value used to authenticate a certificate to view file events for traffic associated with that certificate.
This column does not appear in the file events table view.
Type or paste the SHA hash value used to authenticate the public key contained within a certificate to view file events for traffic associated with that certificate.
This column does not appear in the file events table view.
Access: Admin/Any Security Analyst
Step 1 Select Analysis > Search .
Step 2 Select File Events from the table drop-down list.
The page updates with the appropriate constraints.
Step 3 Enter your search criteria in the appropriate fields as described in the following sections:
- See the File Event Fields table for information on the fields in the file events table.
- See Special Search Syntax for File Events for special search syntax for file events.
- See Viewing the Certificate Associated with an Encrypted Connection for fields related to public key certificates.
Step 4 Optionally, if you plan to save the search, you can select the Private check box to save the search as private so only you can access it. Otherwise, leave the check box clear to save the search for all users.

Tip If you want to use the search as a data restriction for a custom user role, you must save it as a private search.
Step 5 Optionally, you can save the search to be used again in the future. You have the following options:
For a new search, a dialog box appears prompting for the name of the search; enter a unique search name and click Save . If you save new criteria for a previously-existing search, no prompt appears. The search is saved (and visible only to your account if you selected Private ) so that you can run it at a later time.
A dialog box appears prompting for the name of the search; enter a unique search name and click Save . The search is saved (and visible only to your account if you selected Private ) so that you can run it at a later time.
Step 6 Click Search to start the search.
Your search results appear in your default file events workflow, constrained by the current time range.
Working with Malware Events
Supported Devices: feature dependent
Supported Defense Centers: feature dependent
The system logs malware events to the Defense Center database when:
- a managed device detects a file in network traffic that is then identified as malware by a malware cloud lookup
- a managed device detects a file on the custom detection list in network traffic
- the system learns that a file’s malware disposition has changed; these are called retrospective malware events
- a FireAMP Connector installed on an endpoint in your organization detects a threat and communicates that threat to the Cisco cloud
Because FireAMP malware detection is performed at the endpoint at download or execution time, while managed devices detect files in network traffic, the information in these malware events is different. Retrospective malware events also contain slightly different data than other network-based malware events, or endpoint-based malware events.
The following sections briefly describe the different kinds of malware events. For information on the overall malware detection process, see Understanding Malware Protection and File Control.
Endpoint-Based (FireAMP) Malware Events
If your organization has a FireAMP subscription, individual users install FireAMP Connectors on their computers and mobile devices. These lightweight agents communicate with the Cisco cloud, which in turn communicates with your Defense Center; see Working with Cloud Connections for FireAMP. The cloud can send notification of threats, as well other kinds of information including data on scans, quarantines, blocked executions, and cloud recalls. The Defense Center logs this information to its database as malware events.

Note The IP addresses reported in endpoint-based malware events may not be in your network map—and may not even be in your monitored network at all. Depending on your deployment, level of compliance, and other factors, endpoints in your organization where FireAMP Connectors are installed may not be the same hosts as those monitored by your managed devices.
Malware Events Based on Network Traffic
Supported Devices: Any except Series 2 or X-Series
Supported Defense Centers: Any except DC500
With a Malware license, your managed devices can detect malware in network traffic as part of your overall access control configuration; see Understanding and Creating File Policies.
The following scenarios can lead to generating malware events:
-
If a managed device detects one of a set of specific file types, the Defense Center performs a malware cloud lookup, which returns a file disposition to the Defense Center of
Malware,Clean, orUnknown. -
If the Defense Center cannot establish a connection with the cloud, or the cloud is otherwise unavailable, the file disposition is
Unavailable. You may see a small percentage of events with this disposition; this is expected behavior. -
If the threat score associated with a file exceeds the malware threshold threat score defined in the file policy that detected the file, the Defense Center assigns a file disposition of
Malwareto the file. -
If the managed device detects a file whose SHA-256 value is stored on the custom detection list, the Defense Center assigns a file disposition of
Custom Detectionto the file. -
If the managed device detects a file on the clean list, the Defense Center assigns a file disposition of
Cleanto the file.
The Defense Center logs records of files’ detection and dispositions, along with other contextual data, as malware events.

Note Files detected in network traffic and identified as malware by the FireSIGHT System generate both a file event and a malware event. This occurs because to detect malware in a file, the system must first detect the file itself. For more information, see Working with File Events and Working with Captured Files.
Supported Devices: Series 3, virtual
Supported Defense Centers: Any except DC500
For malware files detected in network traffic, file dispositions can change. For example, the Cisco cloud can determine that a file that was previously thought to be clean is now identified as malware, or the reverse — that a malware-identified file is actually clean.
The cloud notifies the Defense Center if the file disposition changes for a file for which you performed a malware lookup in the last week. Then, two things happen:
This new retrospective malware event represents a disposition change for all files detected in the last week that have the same SHA-256 hash value. For that reason, these events contain limited information: the date and time the Defense Center was notified of the disposition change, the new disposition, the SHA-256 hash value of the file, and the threat name. They do not contain IP addresses or other contextual information.
- The Defense Center changes the file disposition for previously detected files with the retrospective event’s associated SHA-256 hash value.
If a file’s disposition changes to Malware, the Defense Center logs a new malware event to its database. Except for the new disposition, the information in this new malware event is identical to that in the file event generated when the file was initially detected.
If a file’s disposition changes to Clean, the Defense Center does not remove the malware event from the malware table. Instead, the event simply reflects the change in disposition. This means that files with clean dispositions can appear in the malware table, but only if they were originally thought to be malware. Files that were never identified as malware appear only in the files table.
In either case, the malware event’s Message indicates how and when the disposition changed, for example:
You can use the Defense Center’s event viewer to view, search, and delete malware events. Additionally, the Files Dashboard and Context Explorer provide an at-a-glance view of detailed information about the files (including malware files) detected on your network, using charts and graphs. Network file trajectory offers a more in-depth view of individual malware files, providing summary information about the file and how it has moved through the network over time. Using malware detection data, you can trigger correlation rules and create reports, the latter using either the predefined Malware Report template or a custom report template.
Viewing Malware Events
The FireSIGHT System’s event viewer allows you to view malware events in a table, as well as manipulate the event view depending on the information relevant to your analysis. Note that the information available for any individual malware event depends on several factors, including licenses. For more information, see Service Subscriptions.
The page you see when you access malware events differs depending on the workflow, which is simply a series of pages you can use to evaluate events by moving from a broad to a more focused view. The system is delivered with the following predefined workflows for malware events:
- Malware Summary , the default, provides a list of detected malware, grouped by individual threat.
- Malware Event Summary provides a quick breakdown of the different malware event types and subtypes.
- Hosts Receiving Malware and Hosts Sending Malware provide a list of hosts that have received or sent malware, grouped by the associated malware dispositions for those files. Note that dispositions appear only for files detected as the result of Malware Cloud Lookup or Block Malware file rules.
- Applications Introducing Malware provides a list of the client applications that accessed or executed the malware detected on endpoints in your organization. From this list, you can drill down into the individual malware files accessed by each parent client.
You can also create a custom workflow that displays only the information that matches your specific needs. For information on specifying a different default workflow, including a custom workflow, see Configuring Event View Settings.
The FireSIGHT System supports the display and input of Unicode (UTF-8) file names in all areas of the web interface, including the event viewer, event search, dashboard, Context Explorer, and so on. Note, however, that reports you generate in PDF format do not support Unicode; Unicode file names appear in the PDF report in transliterated form. For more information, see Generating and Viewing Reports.
Using the event viewer, you can:
- search for, sort, and constrain events, as well as change the time range for displayed events
- specify the columns that appear (table view only)
- view the host profile associated with an IP address, or the user details and host history associated with a user identity
- view the connections where specific malware was detected (for network-based malware events only)
- view events using different workflow pages within the same workflow
- view events using a different workflow altogether
- drill down page-to-page within a workflow, constraining on specific values
- bookmark the current page and constraints so you can return to the same data (assuming the data still exists) at a later time
- view geolocation information for routable IP addresses associated with a file
- view a file’s trajectory
- view nested files inside an archive file
- create a report template using the current constraints
- delete events from the database
- add a file to a file list, download a file, submit a file for dynamic analysis, or view the full text of a file’s SHA-256 value
- view a file’s Dynamic Analysis Summary report, if available
- use the IP address context menu to whitelist, blacklist, or obtain additional available information about a host or IP address associated with a malware event
Note that Series 2 devices, Cisco NGIPS for Blue Coat X-Series, and the DC500 Defense Center do not support network-based malware protection or archive file inspection, which can affect the data displayed. For example, a Series 3 Defense Center managing only Series 2 devices can display only endpoint-based malware events.
For detailed information on using the event viewer, including creating custom workflows, see Understanding and Using Workflows.
Access: Admin/Any Security Analyst
Step 1 Select Analysis > Files > Malware Events .
The first page of your default malware events workflow appears. For information on the columns that appear, see Understanding the Malware Events Table.
Understanding the Malware Events Table
Supported Devices: feature dependent
Supported Defense Centers: feature dependent
The system logs malware events to the Defense Center database when a FireAMP Connector installed on an endpoint in your organization detects a threat, or a managed device detects a file in network traffic that is then identified as malware by a malware cloud lookup. The system also logs retrospective malware events when it learns that a file’s malware disposition has changed. Note that Series 2 devices, Cisco NGIPS for Blue Coat X-Series, and the DC500 Defense Center do not support network-based malware protection, which can affect the data displayed. For example, a Series 3 Defense Center managing only Series 2 devices can display only endpoint-based malware events. For more information, see Understanding Malware Protection and File Control and Working with Malware Events.
The table view of malware events, which is the final page in predefined malware event workflows, and which you can add to custom workflows, includes a column for each field in the files table. Some fields in the table view of malware events are disabled by default. To enable a field for the duration of your session, click the expand arrow ( ) to expand the search constraints, then click the column name under
Disabled Columns
.
) to expand the search constraints, then click the column name under
Disabled Columns
.
Keep in mind that not every field is populated for every event; the different types of malware event can contain different information. For example, because FireAMP malware detection is performed at the endpoint at download or execution time, endpoint-based malware events contain information on file path, invoking client application, and so on. In contrast, because managed devices detect malware files in network traffic, their associated malware events contain port, application protocol, and originating IP address information about the connection used to transmit the file.
The following table lists each malware event field, and indicates whether the system displays information in that field, depending on the malware event type. Note that the DC500 Defense Center does not support sending or receiving continent or country geolocation information.
The file rule action associated with the rule action for the rule the file matched, and any associated file rule action options. |
||||
For network-based malware events, the IP address of the host receiving detected malware. For endpoint-based malware events, the IP address of the endpoint where the FireAMP Connector is installed and where the malware event occurred. |
||||
The source port used by the traffic in which a managed device detected malware. |
||||
The destination port used by the traffic in which a managed device detected malware. |
||||
The action associated with the SSL rule, default action, or undecryptable traffic action that logged the encrypted connection:
If the system fails to decrypt an encrypted connection, it displays the undecryptable traffic action taken, as well as the failure reason. For example, if the system detects traffic encrypted with an unknown cipher suite and allowed it without further inspection, this field displays
Click the lock icon ( |
||||
The user of the host ( Receiving IP ) where the malware event occurred. For network-based malware events, this user is determined by network discovery. Because the user is associated with the destination host, users are not associated with malware events where the user uploaded a malware file. For endpoint-based malware events, FireAMP Connectors determine user names. FireAMP users cannot be tied to user discovery or control. They do not appear in the Users table, nor can you view details for these users. |
||||
The type of malware event. For a full list of event types, see Malware Event Types. |
||||
The FireAMP action that led to malware detection, for example, |
||||
One of the following file dispositions:
Note that clean files appear in the malware table only if they were changed to clean; see Retrospective Malware Events. |
||||
The SHA-256 hash value of the file, as well as a network file trajectory icon representing the most recently detected file event and file disposition. To view the network file trajectory, click the trajectory icon. For more information, see Analyzing Network File Trajectory. |
||||
The threat score most recently associated with this file: To view the Dynamic Analysis Summary report, click the threat score icon. |
||||
The file path of the malware file, not including the file name. |
||||
The file type of the malware file, for example, |
||||
The general categories of file type, for example: |
||||
The originating URI of the malware file, for example, the URL where a user downloaded it. |
||||
Name of the archive file (if any) with which the malware file is associated, for example, |
||||
The SHA-256 hash value of the archive file (if any) with which the malware file is associated. To view the contents of an archive file, right-click on that archive file’s event viewer row to open the context menu, then click View Archive Contents . For more information, see Viewing the Contents of Archived Files. |
||||
The level (if any) at which the file was nested in an archive file, for example, |
||||
The client application accessing the malware file when detection occurred. These applications are not tied to network discovery or application control. |
||||
The SHA-256 hash value of the parent file accessing the FireAMP-detected or quarantined file when detection occurred. |
||||
The application protocol used by the traffic in which a managed device detected a malware file. |
||||
Application Protocol, Client, or Web Application Category or Tag |
Criteria that characterize the application to help you understand the application's function; see Table 45-2.. |
|||
The client application that runs on one host and relies on a server to send a file. |
||||
The application that represents the content or requested URL for HTTP traffic detected in the connection. |
||||
Whether the malware event triggered an indication of compromise (IOC) against a host involved in the connection. When endpoint-based malware detection triggers an IOC rule, a full malware event is generated, with the type
FireAMP
|
||||
The risk associated with the application traffic detected in the connection: |
||||
The business relevance associated with the application traffic detected in the connection: |
||||
The FireAMP detector that identified the malware, such as ClamAV, Spero, or SHA. |
||||
Any additional information associated with the malware event. For network-based malware events, this field is populated only for files whose disposition has changed; see Retrospective Malware Events. |
||||
For network-based malware events, the name of the device that detected the malware file. For endpoint-based malware events and retrospective malware events generated by the cloud, the name of the Defense Center. |
||||
The metadata identifying the virtual firewall group through which the traffic passed. Note that the system only populates this field for ASA FirePOWER devices in multiple context mode. |
||||
The number of events that match the information in each row. This field appears after you apply a constraint that creates two or more identical rows. |
Malware Event Types
Supported Devices: feature dependent
Supported Defense Centers: feature dependent
For network-based malware events, the event type can be one of:
An endpoint-based malware event can have any of the following types:
- Blocked Execution
- Cloud Recall Quarantine
- Cloud Recall Quarantine Attempt Failed
- Cloud Recall Quarantine Started
- Cloud Recall Restore from Quarantine
- Cloud Recall Restore from Quarantine Failed
- Cloud Recall Restore from Quarantine Started
- FireAMP IOC
- Quarantine Failure
- Quarantined Item Restored
- Quarantine Restore Failed
- Quarantine Restore Started
- Scan Completed, No Detections
- Scan Completed With Detections
- Scan Failed
- Scan Started
- Threat Detected
- Threat Detected in Exclusion
- Threat Quarantined
If a file’s trajectory map contains malware events, the events are one of the following types: Threat Detected in Network File Transfer, Threat Detected in Network File Transfer (retrospective), Threat Detected, Threat Detected in Exclusion, and Threat Quarantined. See Working with Network File Trajectory for more information.
Note that Series 2 devices, Cisco NGIPS for Blue Coat X-Series, and the DC500 Defense Center do not support network-based malware protection, which can affect the data displayed. For example, a Series 3 Defense Center managing only Series 2 devices can display only endpoint-based malware events.
Searching for Malware Events
Using the Defense Center’s Search page, you can search for specific malware events, display the results in the event viewer, and save your search criteria to reuse later. Custom Analysis dashboard widgets, report templates, and custom user roles can also use saved searches.
Searches delivered with the system, labeled with
(
Cisco
)
in the Saved Searches list, serve as examples.
Keep in mind that your search results depend on the available data in the events you are searching. In other words, depending on the available data, your search constraints may not apply. For example, because endpoint-based malware events are not generated as a result of managed devices inspecting network traffic, they do not contain connection information (port, application protocol, and so on).
The system displays examples of valid syntax next to each search field. When entering search criteria, keep the following points in mind:
-
All fields accept negation (
!). - All fields accept comma-separated lists of search values. Records that contain any of the listed values in the specified field match that search criteria.
- All fields accept comma-separated lists enclosed in quotation marks as search values.
– For fields that may contain only a single value, records with the specified field containing the exact string specified within the quotation marks match the search criteria. For instance, a search for
A, B, "C, D, E"
will match records where the specified field contains
"A"
or
"B"
or
"C, D, E"
. This permits matching on fields that include the comma in possible values.
– For fields that may contain multiple values at the same time, records with the specified fields containing all of the values in the quote-enclosed comma-separated list match that search criteria.
– For fields that may contain multiple values at the same time, search criteria may include single values as well as quote-enclosed comma-separated lists. For instance, a search for
A, B, "C, D, E"
on a field that may contain one of more of these letters matches records where the specified field contains
A
or
B
, or all of
C
,
D
, and
E
.
- Searches return only records that match the search criteria specified for all fields.
-
Many fields accept one or more asterisks (
*) as wild cards. -
Specify
n/ain any field to identify events where information is not available for that field; use!n/ato identify the events where that field is populated. - Use the device field to search for specific devices as well as devices in groups, stacks, or clusters. For more information on how the FireSIGHT System treats the device field in searches, see Specifying Devices in Searches.
- Click the add object icon (
 ) that appears next to a search field to use an object as a search criterion.
) that appears next to a search field to use an object as a search criterion.For detailed information on search syntax, including using objects in searches, see Searching for Events.
Special Search Syntax for Malware Events
To supplement the general search syntax listed above, the following list describes some special search syntax for malware events.
The system returns all events where either the Sending IP or the Receiving IP matches the IP address you specify.
When searching for events with a specific malware event type (see Malware Event Types), enclose the event type in quotation marks, for example,
"Scan Completed With Detection"
. Otherwise, the system performs a partial match. That is, if you search using the same string but do not use quotation marks, the system returns events with the following types:
–
Scan Completed, No Detections
–
Scan Completed With Detection
The system returns all events where either the Initiator Continent or the Responder Continent matches the continent you specify.
The system returns all events where either the Initiator Country or the Responder Country matches the country you specify.
The system performs a partial match, that is, you can search for all or part of the field contents without using asterisks.
Type any of the following keywords to view malware events for encrypted traffic to which the system applied the action specified:
–
Do Not Decrypt
represents connections the system did not decrypt.
–
Block
and
Block with Reset
represent blocked encrypted connections.
–
Decrypt (Known Key)
represents incoming connections decrypted using a known private key.
–
Decrypt (Replace Key)
represents outgoing connections decrypted using a self-signed server certificate with a substituted public key.
–
Decrypt (Resign)
represents outgoing connections decrypted using a re-signed server certificate.
This column does not appear in the malware events table view.
Type any of the following keywords to view malware events for encrypted traffic that the system failed to decrypt for the reason specified:
–
Session Undecryptable in Passive Mode
–
Pending Server Name Category Lookup
–
Pending Common Name Category Lookup
–
Network Parameters Unavailable
–
Invalid Server Certificate Handle
–
Server Certificate Fingerprint Unavailable
–
External Certificate List Unavailable
–
External Certificate Fingerprint Unavailable
–
Internal Certificate List Invalid
–
Internal Certificate List Unavailable
–
Internal Certificate Unavailable
–
Internal Certificate Fingerprint Unavailable
–
Server Certificate Validation Unavailable
–
Server Certificate Validation Failure
This column does not appear in the malware events table view.
Type a two-character ISO 3166-1 alpha-2 country code to view malware events for encrypted traffic associated with the country of a certificate subject.
This column does not appear in the malware events table view.
Type a two-character ISO 3166-1 alpha-2 country code to view encrypted traffic associated with the country of a certificate issuer.
This column does not appear in the malware events table view.
Type or paste the SHA hash value used to authenticate a certificate to view traffic associated with that certificate.
This column does not appear in the malware events table view.
Type or paste the SHA hash value used to authenticate the public key contained within a certificate to view traffic associated with that certificate.
This column does not appear in the malware events table view.
Access: Admin/Any Security Analyst
Step 1 Select Analysis > Search .
Step 2 Select Malware Events from the table drop-down list.
The page updates with the appropriate constraints.
Step 3 Enter your search criteria in the appropriate fields as described in the following sections:
- See the Malware Event Fields table for information on the fields in the malware events table.
- See Special Search Syntax for Malware Events for special search syntax for malware events.
- See Viewing the Certificate Associated with an Encrypted Connection for fields related to public key certificates.
Step 4 Optionally, if you plan to save the search, you can select the Private check box to save the search as private so only you can access it. Otherwise, leave the checkbox clear to save the search for all users.

Tip If you want to use the search as a data restriction for a custom user role, you must save it as a private search.
Step 5 Optionally, you can save the search to be used again in the future. You have the following options:
For a new search, a dialog box appears prompting for the name of the search; enter a unique search name and click Save . If you save new criteria for a previously-existing search, no prompt appears. The search is saved (and visible only to your account if you selected Private ) so that you can run it at a later time.
A dialog box appears prompting for the name of the search; enter a unique search name and click Save . The search is saved (and visible only to your account if you selected Private ) so that you can run it at a later time.
Step 6 Click Search to start the search.
Your search results appear in your default malware events workflow, constrained by the current time range.
Working with Captured Files
Supported Devices: Any except Series 2 or X-Series
Supported Defense Centers: Any except DC500
The system logs when a managed device captures a file detected in network traffic according to the rules in currently applied file policies. From the event viewer, you can view information associated with the captured file, such as the most recent file name associated with the SHA-256 value, the file disposition and threat score, the file storage status, the archive inspection status, and whether the file was manually submitted for dynamic analysis.

Note Files captured by a device containing malware generate both a file event and a malware event, as malware must be detected before it is captured. For more information, see Working with File Events and Working with Malware Events.
You can use the Defense Center’s event viewer to view and search captured files, as well as submit captured files for dynamic analysis. Additionally, the Files Dashboard provides an at-a-glance view of detailed information about the files (including malware files) detected on your network, using charts and graphs.
Viewing Captured Files
The FireSIGHT System’s event viewer allows you to view captured files in a table, as well as manipulate the event view depending on the information relevant to your analysis.
The page you see when you access captured files differs depending on the workflow, which is simply a series of pages you can use to evaluate events by moving from a broad to a more focused view. The system is delivered with the following predefined workflows for captured files:
- Captured File Summary , the default, provides a breakdown of captured files based on type, category, and threat score.
- Dynamic Analysis Status provides a count of captured files based on whether they have been submitted for dynamic analysis.
You can also create a custom workflow that displays only the information that matches your specific needs. For information on specifying a different default workflow, including a custom workflow, see Configuring Event View Settings.
The FireSIGHT System supports the display and input of Unicode (UTF-8) file names in all areas of the web interface, including the event viewer, event search, dashboard, Context Explorer, and so on. Note, however, that reports you generate in PDF format do not support Unicode; Unicode file names appear in the PDF report in transliterated form. For more information, see Generating and Viewing Reports.
Using the event viewer, you can:
- search for, sort, and constrain events, as well as change the time range for displayed events
- specify the columns that appear (table view only)
- view events using different workflow pages within the same workflow
- view events using a different workflow altogether
- drill down page-to-page within a workflow, constraining on specific values
- bookmark the current page and constraints so you can return to the same data (assuming the data still exists) at a later time
- view a file’s trajectory
- view the contents and inspection status of an archive file
- add a file to a file list, download a file, submit a file for dynamic analysis, or view the full text of a file’s SHA-256 value
- view a file’s Dynamic Analysis Summary report, if available
- submit up to 25 files at a time for dynamic analysis
- create a report template using the current constraints
Note that Series 2 devices, Cisco NGIPS for Blue Coat X-Series, and the DC500 Defense Center do not support network-based malware protection or archive file inspection, which can affect the data displayed. For example, a Series 3 Defense Center managing only Series 2 devices cannot display captured files.
For detailed information on using the event viewer, including creating custom workflows, see Understanding and Using Workflows.
Access: Admin/Any Security Analyst
Step 1 Select Analysis > Files > Captured Files .
The first page of your default file events workflow appears. For information on the columns that appear, see Understanding the Captured Files Table.
Understanding the Captured Files Table
The Defense Center logs when a managed device captures a file being transmitted in monitored network traffic, according to the settings in an applied file policy.
The table view of captured files, which is the final page in predefined captured file workflows, and which you can add to custom workflows, includes a column for each field in the captured files table. Some fields in the table view of captured files are disabled by default. To enable a field for the duration of your session, click the expand arrow ( ) to expand the search constraints, then click the column name under
Disabled Columns
. The following table describes the captured file fields.
) to expand the search constraints, then click the column name under
Disabled Columns
. The following table describes the captured file fields.
The last time the information associated with this file was updated. |
|
The most recently detected file name associated with the file’s SHA-256 hash value. |
|
One of the following file dispositions:
|
|
The SHA-256 hash value of the file, as well as a network file trajectory icon representing the most recently detected file event and file disposition. To view the network file trajectory, click the trajectory icon. For more information, see Analyzing Network File Trajectory. |
|
The threat score most recently associated with this file: To view the Dynamic Analysis Summary report, click the threat score icon. |
|
The general categories of file type, for example: |
|
For archive files, the status of archive inspection:
To view the contents of an archive file, right-click on its event viewer row to bring up the context menu, then select View Archive Contents . For more information, see Configuring Archive File Inspection Options. |
|
The time the file was most recently submitted to the cloud for dynamic analysis. |
Searching for Captured Files
Using the Defense Center’s Search page, you can search for specific captured files, display the results in the event viewer, and save your search criteria to reuse later. Custom Analysis dashboard widgets, report templates, and custom user roles can also use saved searches.
Keep in mind that your search results depend on the available data in the events you are searching. In other words, depending on the available data, your search constraints may not apply. For example, if a file has never been submitted for dynamic analysis, it may not have an associated threat score.
The system displays examples of valid syntax next to each search field. When entering search criteria, keep the following points in mind:
-
All fields accept negation (
!). - All fields accept comma-separated lists of search values. Records that contain any of the listed values in the specified field match that search criteria.
- All fields accept comma-separated lists enclosed in quotation marks as search values.
– For fields that may contain only a single value, records with the specified field containing the exact string specified within the quotation marks match the search criteria. For instance, a search for
A, B, "C, D, E"
will match records where the specified field contains
"A"
or
"B"
or
"C, D, E"
. This permits matching on fields that include the comma in possible values.
– For fields that may contain multiple values at the same time, records with the specified fields containing all of the values in the quote-enclosed comma-separated list match that search criteria.
– For fields that may contain multiple values at the same time, search criteria may include single values as well as quote-enclosed comma-separated lists. For instance, a search for
A, B, "C, D, E"
on a field that may contain one of more of these letters matches records where the specified field contains
A
or
B
, or all of
C
,
D
, and
E
.
- Searches return only records that match the search criteria specified for all fields.
-
Many fields accept one or more asterisks (
*) as wild cards. -
Specify
n/ain any field to identify events where information is not available for that field; use!n/ato identify the events where that field is populated. - Click the add object icon (
 ) that appears next to a search field to use an object as a search criterion.
) that appears next to a search field to use an object as a search criterion.For detailed information on search syntax, including using objects in searches, see Searching for Events.
Special Search Syntax for Captured Files
To supplement the general search syntax listed above, the following table describes some special search syntax for captured files.
Access: Admin/Any Security Analyst
Step 1 Select Analysis > Search .
Step 2 Select Captured Files from the table drop-down list.
The page updates with the appropriate constraints.
Step 3 Enter your search criteria in the appropriate fields.
See the Captured File Fields table for information on the fields in the captured files table.
Step 4 Optionally, if you plan to save the search, you can select the Private check box to save the search as private so only you can access it. Otherwise, leave the check box clear to save the search for all users.

Tip If you want to use the search as a data restriction for a custom user role, you must save it as a private search.
Step 5 Optionally, you can save the search to be used again in the future. You have the following options:
For a new search, a dialog box appears prompting for the name of the search; enter a unique search name and click Save . If you save new criteria for a previously-existing search, no prompt appears. The search is saved (and visible only to your account if you selected Private ) so that you can run it at a later time.
A dialog box appears prompting for the name of the search; enter a unique search name and click Save . The search is saved (and visible only to your account if you selected Private ) so that you can run it at a later time.
Step 6 Click Search to start the search.
Your search results appear in your default captured file workflow, constrained by the current time range.
Working with Network File Trajectory
Supported Devices: feature dependent
Supported Defense Centers: feature dependent
The network file trajectory feature maps how hosts transferred files, including malware files, across your network. You can use the map to determine which hosts may have transferred malware, which hosts are at risk, and observe file transfer trends.
The trajectory map charts file transfer data, the disposition of the file, and if a file transfer was blocked or the file was quarantined. The data used to build the map can come from network-based malware events (any file event for which the system performed a malware cloud lookup and returned a malware disposition) and certain endpoint-based malware events related to detecting and blocking malware (any Threat Detected or Threat Quarantined event type). Vertical lines between data points represent file transfers between hosts. Horizontal lines connecting the data points show a host’s file activity over time.
You can track the transmission of any file type for which the system can perform a malware cloud lookup. To directly access a file’s trajectory, you can use the Network File Trajectory List page ( Analysis > Files > Network File Trajectory ) and locate specific files. Additionally, if you are analyzing an intrusion and want to review the trajectory for a related file, you can access the file’s trajectory from the Context Explorer, dashboard, or event views of connection, file, or malware events.
The data a single trajectory map displays depends on the licenses applied to your appliance. The following table lists the licenses necessary to track different types of file trajectory.
See Understanding Malware Protection and File Control for more information.
Note that because you cannot use a Malware license with a DC500 nor enable a Malware license on a Series 2 device or Cisco NGIPS for Blue Coat X-Series, you cannot use those appliances to capture, store or block individual files, submit files for dynamic analysis, view the contents of archive files, or view file trajectories for files for which you conduct a malware cloud lookup. You can, however, still view file trajectories for endpoint-based threat and quarantine tracking.
For more information, see the following sections:
Reviewing Network File Trajectory
Supported Devices: feature dependent
Supported Defense Centers: feature dependent
As you review captured files, file events, and malware events, you can view a file’s trajectory map from the Context Explorer, properly configured dashboard widgets, and various event views. You can also review the most recently viewed network file trajectories and the most recently detected malware from the Network File Trajectory List page.
For more information, see the following sections:
- Viewing the Top File Names Graph
- Drilling Down on Context Explorer Data
- Understanding the Custom Analysis Widget
- Configuring Archive File Inspection Options
- Understanding the File Events Table
- Understanding the Malware Events Table
- Understanding the Captured Files Table
- Information Available in Connection and Security Intelligence Events
- Accessing Network File Trajectory
Accessing Network File Trajectory
Supported Devices: feature dependent
Supported Defense Centers: feature dependent
The Network File Trajectory List page allows you to locate files that have a SHA-256 hash value, whether to analyze the most recently detected malware, or to track a specific threat.
The page displays the malware most recently detected on your network, as well as the files whose trajectory maps you have most recently viewed. From these lists, you can view when the file was most recently seen on the network, the file’s SHA-256 hash value, name, type, current file disposition, contents (for archive files), and the number of events associated with the file. For more information on the fields, see Understanding the File Events Table.
The page also contains a search box that lets you locate files, either based on SHA-256 hash value or file name, or by the IP address of the host that transferred or received a file. After you locate a file, you can click the File SHA256 value to view the detailed trajectory map. See Analyzing Network File Trajectory for more information.
The FireSIGHT System supports the display and input of Unicode (UTF-8) file names in all areas of the web interface, including the event viewer, event search, dashboard, Context Explorer, and so on. Note, however, that reports you generate in PDF format do not support Unicode; Unicode file names appear in the PDF report in transliterated form. For more information, see Generating and Viewing Reports.
Note that because you cannot use a Malware license with a DC500, nor can you enable a Malware license on a Series 2 device or Cisco NGIPS for Blue Coat X-Series, you cannot use those appliances to view file trajectories for files for which you conduct a malware cloud lookup.
To locate a file from the Network File Trajectory List page:
Step 1 Select Analysis > Files > Network File Trajectory .
The Network File Trajectory List page appears, displaying the lists of recently viewed files and recent malware.
Step 2 Optionally, you can type a complete SHA-256 hash value, host IP address, or file name of a file you want to track into the search field and press Enter.
The Query Results page appears listing all files that match the search. If only one result matches, the Network File Trajectory page for that file appears.
Analyzing Network File Trajectory
Supported Devices: feature dependent
Supported Defense Centers: feature dependent
You can trace a file through the network by viewing the detailed network file trajectory. The file’s trajectory presents summary information about a file, displays the map charting data points over time, and also lists the event data tied to the data points in a table. Using the table and the map, you can pinpoint specific file events, hosts on the network that transferred or received this file, related events in the map, and other related events in a table constrained on selected values.
Note that because you cannot use a Malware license with a DC500, nor can you enable a Malware license on a Series 2 device or Cisco NGIPS for Blue Coat X-Series, you cannot use those appliances to view file trajectories for files for which you conduct a malware cloud lookup.
Summary Information
Supported Devices: feature dependent
Supported Defense Centers: feature dependent
A file’s trajectory page displays basic information about the file, including file identification information, when the file was first seen and most recently seen on the network, the number of related events and hosts associated with the file, and the file’s current disposition. From this section, if the managed device stored the file, you can download it locally, submit the file for dynamic analysis, or add the file to a file list.

Tip To view related file events, click a field value link. The first page in the File Events default workflow opens in a new window, displaying all file events that also contain the selected value.
The following table describes the summary information fields.
The SHA-256 hash value of the file. The hash is displayed by default in a condensed format. To view the full hash value, hover your pointer over it. If multiple SHA-256 hash values are associated with a file name, hover your pointer over the link to view all of the hash values.
Click the download file icon ( 
|
|
The names of the file associated with the event, as seen on the network.
If multiple file names are associated with a SHA-256 hash value, the most recent detected file name is listed. You can expand this to view the remaining file names by clicking |
|
The general categories of file type, for example, |
|
The client application accessing the malware file when detection occurred. These applications are not tied to network discovery or application control. |
|
The first time a managed device or FireAMP Connector detected the file, and the IP address of the host that first uploaded the file. |
|
The most recent time a managed device or FireAMP Connector detected the file, and the IP address of the host that last downloaded the file. |
|
The number of events seen on the network associated with the file, and the number of events displayed in the map if there are more than 250 detected events. |
|
The number of hosts that either sent or received the file. Because one host can upload and download a file at different times, the total number of hosts may not match the total number of senders plus the total number of receivers in the |
|
The number of hosts that sent the file, followed by the number of hosts that received the file. |
|
One of the following file dispositions:
Click the edit icon ( |
|
For inspected archive files, the number of files the archive contains. Click the view icon ( For more information about archive file inspection, see Configuring Archive File Inspection Options. |
|
|
Click the threat score icon to view the Dynamic Analysis Summary report, click the threat score icon. Click the threat score link to view all captured files with that threat score.
Click the cloud icon ( |
Trajectory Map
Supported Devices: feature dependent
Supported Defense Centers: feature dependent
A file’s trajectory map visually tracks a file from the first detection on your network to the most recent. The map shows when hosts transferred or received the file, how often they transferred the file, and when the file was blocked or quarantined. The map also shows how often file events occurred for the file and when the system assigned the file a disposition or retrospective disposition. You can select a data point in the map and highlight a path that traces back to the first instance the host transferred that file; this path also intersects with every occurrence involving the host as either sender or receiver of the file. The following graphic shows an example trajectory map:

The map’s y-axis contains a list of all host IP addresses that have interacted with the file. The IP addresses are listed in descending order based on when the system first detected the file on that host. Each row contains all events associated with that IP address, whether a single file event, file transfer, or retrospective event. The x-axis contains the date and time the system detected each event. The timestamps are listed in chronological order. If multiple events occurred within a minute, all are listed within the same column. You can scroll the map horizontally and vertically to view additional events and IP addresses.
The map displays up to 250 events associated with the file SHA-256 hash. If there are more than 250 events, the map displays the first 10, then truncates extra events with an arrow icon ( ). The map then displays the remaining 240 events. The following graphic shows events truncated with the arrow icon:
). The map then displays the remaining 240 events. The following graphic shows events truncated with the arrow icon:
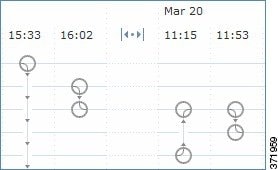
You can view all events not displayed in the File Summary event view by clicking the arrow icon ( ). The first page of the File Events default workflow appears in a new window with all the extra events constrained based on the file type. If endpoint-based malware events are not displayed, you must switch to the Malware Events table to view these.
). The first page of the File Events default workflow appears in a new window with all the extra events constrained based on the file type. If endpoint-based malware events are not displayed, you must switch to the Malware Events table to view these.
Each data point represents an event plus the file disposition, as described in the legend below the map. For example, a Malware Block event icon combines the Malicious Disposition icon and the Block Event icon.
Endpoint-based malware events include one icon. A retrospective event displays an icon in the column for each host on which the file is detected. File transfer events always include two icons, one file send icon and one file receive icon, connected by a vertical line. Arrows indicate the file transfer direction from sender to receiver.
You can view summary information from the event icon by hovering your pointer over the event icon ( ). The displayed summary information matches the information displayed in the Events table. The following graphic shows an event icon’s summary information:
). The displayed summary information matches the information displayed in the Events table. The following graphic shows an event icon’s summary information:

If you click any event summary information link, the first page of the File Events default workflow appears in a new window with all the extra events constrained based on the file type the File Summary event view opens in a new window, displaying all file events that match on the criteria value you clicked.
To locate the first time a file event occurred involving an IP address, click the address. This highlights a path to that data point, as well as any intervening file events and IP addresses related to the first file event. The corresponding event in the Events table is also highlighted. The map scrolls to that data point if not currently visible. The following graphic shows the path highlighted after clicking an IP address:

To track a file’s progress through the network, you can click any data point to highlight a path that includes all data points related to the selected data point. This includes data points associated with the following types of events:
- any file transfers in which the associated IP address was either sender or receiver
- any endpoint-based malware events involving the associated IP address
- if another IP address was involved, all file transfers in which that associated IP address was either sender or receiver
- if another IP address was involved, any endpoint-based malware events involving the other IP address
The following graphic shows the path highlighted after clicking an event icon:

All IP addresses and timestamps associated with any highlighted data point are also highlighted. The corresponding event in the Events table is also highlighted. If a path includes truncated events, the path itself is highlighted with a dotted line. Truncated events might intersect the path, but are not displayed in the map.
Events Table
Supported Devices: feature dependent
Supported Defense Centers: feature dependent
The Events table lists event information for each data point in the map. You can sort events in ascending or descending order by clicking the column headers. You can highlight a data point in the map by selecting the table row. The map scrolls to display the selected file event if not currently visible. For more information on the fields, see Understanding the File Events Table.




 ) to view certificate details. For more information, see
) to view certificate details. For more information, see  )
) )
) )
) )
) )
) )
) )
) )
) )
) )
) )
) )
) ) to download the file to your local computer. If prompted, confirm you want to download the file. Follow your browser’s prompts to save the file. If the file is unavailable for download, this icon is grayed out.
) to download the file to your local computer. If prompted, confirm you want to download the file. Follow your browser’s prompts to save the file. If the file is unavailable for download, this icon is grayed out. ) to add the file to or remove the file from the clean list or custom detection list.
) to add the file to or remove the file from the clean list or custom detection list. ) to view information about content files in the Archive Contents window.
) to view information about content files in the Archive Contents window. )
)  )
)  )
) ).
). ) to submit the file to the cloud for dynamic analysis. If the file is unavailable for submission or you cannot connect to the cloud, this icon is grayed out.
) to submit the file to the cloud for dynamic analysis. If the file is unavailable for submission or you cannot connect to the cloud, this icon is grayed out. Feedback
Feedback