- Title Page
- Introduction & Preface
- Logging into the FireSIGHT System
- Using Objects and Security Zones
- Managing Devices
- Setting Up an IPS Device
- Setting Up Virtual Switches
- Setting Up Virtual Routers
- Setting Up Aggregate Interfaces
- Setting Up Hybrid Interfaces
- Using Gateway VPNs
- Using NAT Policies
- Getting Started with Access Control Policies
- Blacklisting Using Security Intelligence IP Address Reputation
- Tuning Traffic Flow Using Access Control Rules
- Controlling Traffic with Network-Based Rules
- Controlling Traffic with Reputation-Based Rules
- Controlling Traffic Based on Users
- Controlling Traffic Using Intrusion and File Policies
- Understanding Traffic Decryption
- Getting Started with SSL Policies
- Getting Started with SSL Rules
- Tuning Traffic Decryption Using SSL Rules
- Understanding Intrusion and Network Analysis Policies
- Using Layers in Intrusion and Network Analysis Policies
- Customizing Traffic Preprocessing
- Getting Started with Network Analysis Policies
- Using Application Layer Preprocessors
- Configuring SCADA Preprocessing
- Configuring Transport & Network Layer Preprocessing
- Tuning Preprocessing in Passive Deployments
- Getting Started with Intrusion Policies
- Tuning Intrusion Rules
- Tailoring Intrusion Protection to Your Network Assets
- Detecting Specific Threats
- Limiting Intrusion Event Logging
- Understanding and Writing Intrusion Rules
- Blocking Malware and Prohibited Files
- Logging Connections in Network Traffic
- Working with Connection & Security Intelligence Data
- Analyzing Malware and File Activity
- Working with Intrusion Events
- Handling Incidents
- Configuring External Alerting
- Configuring External Alerting for Intrusion Rules
- Introduction to Network Discovery
- Enhancing Network Discovery
- Configuring Active Scanning
- Using the Network Map
- Using Host Profiles
- Working with Discovery Events
- Configuring Correlation Policies and Rules
- Using the FireSIGHT System as a Compliance Tool
- Creating Traffic Profiles
- Configuring Remediations
- Using Dashboards
- Using the Context Explorer
- Working with Reports
- Understanding and Using Workflows
- Using Custom Tables
- Searching for Events
- Managing Users
- Scheduling Tasks
- Managing System Policies
- Configuring Appliance Settings
- Licensing the FireSIGHT System
- Updating System Software
- Monitoring the System
- Using Health Monitoring
- Auditing the System
- Using Backup and Restore
- Specifying User Preferences
- Importing and Exporting Configurations
- Purging Discovery Data from the Database
- Viewing the Status of Long-Running Tasks
- Command Line Reference
- Security, Internet Access, and Communication Ports
- Third-Party Products
- glossary
- Components of a Workflow
- Comparing Predefined and Custom Workflows
- Comparing Workflows for Predefined and Custom Tables
- Predefined Intrusion Event Workflows
- Predefined Malware Workflows
- Predefined File Workflows
- Predefined Captured File Workflows
- Predefined Connection Data Workflows
- Predefined Security Intelligence Workflows
- Predefined Host Workflows
- Predefined Indications of Compromise Workflows
- Predefined Applications Workflows
- Predefined Application Details Workflows
- Predefined Servers Workflows
- Predefined Host Attributes Workflows
- Predefined Discovery Events Workflows
- Predefined User Workflows
- Predefined Vulnerabilities Workflows
- Predefined Third-Party Vulnerabilities Workflows
- Predefined Correlation and White List Workflows
- Predefined System Workflows
- Saved Custom Workflows
- Using Workflows
- Selecting Workflows
- Understanding the Workflow Toolbar
- Using Workflow Pages
- Setting Event Time Constraints
- Constraining Events
- Using Compound Constraints
- Sorting Table View Pages and Changing Their Layout
- Sorting Drill-Down Workflow Pages
- Selecting Rows on a Workflow Page
- Navigating to Other Pages in the Workflow
- Navigating Between Workflows
- Using Bookmarks
Understanding and Using Workflows
A workflow is a tailored series of data pages on the Defense Center web interface that analysts can use to evaluate events generated by the system. The Defense Center provides three types of workflows:
- Predefined workflows , which are preset workflows installed on the system that you cannot modify or delete.
- Saved custom workflows , which are predefined custom workflows that you can modify or delete.
- Custom workflows , which are workflows that you create and customize for your specific needs.
For example, when you analyze intrusion events, you can choose from several predefined workflows specifically created for the task.
Note that the data displayed in a workflow often depends on such factors as how you license and deploy your managed devices, whether you configure features that provide the data and, in the case of Series 2 appliances and Cisco NGIPS for Blue Coat X-Series, whether the appliance supports a feature that provides the data. For example, because neither the DC500 Defense Center nor Series 2 devices support URL filtering by category and reputation, the DC500 Defense Center does not display data for this feature and Series 2 devices do not detect this data.
See the following sections for more information about using predefined and custom workflows:

Tip You can also use custom workflows as the basis for event reports. See Working with Reports for more information.
Components of a Workflow
Workflows can include several types of pages, as described in the following sections.
Table views include a column for each of the fields in the database on which your workflow is based.
For example, the table view of discovery events includes the Time, Event, IP Address, User, MAC Address, MAC Vendor, Port, Description, and Device columns.
By contrast, the table view of servers includes the Last Used, IP Address, Port, Protocol, Application Protocol, Vendor, Version, Web Application, Application Risk, Business Relevance, Hits, Source Type, Device, and Current User columns.
Drill-down pages contain a subset of columns that are available in the database.
For example, a drill-down page for discovery events might include only the IP Address, MAC Address, and Time columns. A drill-down page for intrusion events, on the other hand, might include the Priority, Impact Flag, Inline Result, and Message columns.
Generally, drill-down pages are intermediate pages that you use to narrow your investigation to a few events before moving to a table view page.
Workflows based on connection data can include graph pages, also called connection graphs .
For example, a connection graph might display a line graph that shows the number of connections detected by the system over time. Generally, connection graphs are, like drill-down pages, intermediate pages that you use to narrow your investigation. For more information, see Working with Connection Graphs.
The final page of a workflow depends on the type of event on which the workflow is based:
– The host view is the final page for workflows based on applications, application details, discovery events, hosts, indications of compromise (IOC), servers, or any type of vulnerabilities. Viewing host profiles from this page allows you to easily view data on all IP addresses associated with hosts that have multiple addresses. For more information, see Using Host Profiles.
– The user detail view is the final page for workflows based on users and user activity. For more information, see Understanding User Details and Host History.
– The vulnerability detail view is the final page for workflows based on Cisco vulnerabilities. For more information, see Viewing Vulnerability Details.
– The packet view is the final page for workflows based on intrusion events. For more information, see Using the Packet View.
Workflows based on other kinds of events (for example, audit log events or malware events) do not have final pages.
See the following sections for more information on workflows:
- Comparing Predefined and Custom Workflows
- Comparing Workflows for Predefined and Custom Tables
- Predefined Intrusion Event Workflows
- Predefined Malware Workflows
- Predefined File Workflows
- Predefined Captured File Workflows
- Predefined Connection Data Workflows
- Predefined Security Intelligence Workflows
- Predefined Host Workflows
- Predefined Indications of Compromise Workflows
- Predefined Applications Workflows
- Predefined Application Details Workflows
- Predefined Servers Workflows
- Predefined Host Attributes Workflows
- Predefined Discovery Events Workflows
- Predefined User Workflows
- Predefined Vulnerabilities Workflows
- Predefined Third-Party Vulnerabilities Workflows
- Predefined Correlation and White List Workflows
- Predefined System Workflows
- Saved Custom Workflows
Comparing Predefined and Custom Workflows
The FireSIGHT System is delivered with a set of predefined workflows (described in the sections that follow) that you can use to analyze the events and other data it collects.
Custom workflows are workflows that you create to meet the unique needs of your organization. When you create a custom workflow, you choose the kind of event (or database table) on which the workflow is based. On the Defense Center, you can base a custom workflow on a custom table. You can also choose the pages a custom workflow contains; custom workflows can contain drill-down, table view, and host or packet view pages.
The Defense Center is delivered with several saved custom workflows , which are based on the saved custom tables that are also delivered with the Defense Center. The differences between workflows based on predefined and custom tables is described in the next section, Comparing Workflows for Predefined and Custom Tables.
Comparing Workflows for Predefined and Custom Tables
You can use the custom tables feature to create tables that use the data from two or more types of events. This is useful because you can, for example, create tables and workflows that correlate intrusion event data with discovery data to allow simple searches for events that affect critical systems. See Using Custom Tables for information about creating custom tables.
Each custom table has, by default, a workflow that you can use to view the events associated with the table. The features in the workflow differ depending on which type of table you use. For example, custom table workflows based on the intrusion event table always end with the packet view. However, custom table workflows based on discovery events end with the host view.
Unlike workflows based on the predefined event tables, workflows based on custom tables do not have links to other types of workflows.
Predefined Intrusi on Event Workflows
The following table describes the predefined intrusion event workflows included with the FireSIGHT System. For information on accessing these workflows, see Viewing Intrusion Events and Reviewing Intrusion Events.
Predefined Malware Workflows
Supported Devices: feature dependent
Supported Defense Centers: feature dependent
The following table describes the predefined malware workflows included on the Defense Center. All predefined malware workflows use the table view of malware events.
Note that because the DC500 Series 2 Defense Center, Series 2 devices, and Cisco NGIPS for Blue Coat X-Series do not support advanced malware protection, the DC500 Defense Center does not display data for this feature and Series 2 devices and Cisco NGIPS for Blue Coat X-Series do not detect this data.
For information on accessing malware events, see Working with Malware Events.
Predefined File Workflows
The following table describes the predefined file event workflows included on the Defense Center. All the predefined file event workflows use the table view of file events. For information on accessing file events, see Working with File Events.
Predefined Captured File Workflows
Supported Devices: feature dependent
Supported Defense Centers: feature dependent
The following table describes the predefined captured file workflows included on the Defense Center. All predefined captured file workflows use the table view of captured files.
Note that because the DC500 Series 2 Defense Center, Series 2 devices, and Cisco NGIPS for Blue Coat X-Series do not support advanced malware protection, the DC500 Defense Center does not display data for this feature and Series 2 devices and Cisco NGIPS for Blue Coat X-Series do not detect this data.
For information on accessing captured files, see Working with Captured Files.
Predefined Connection Data Workflows
The following table describes the predefined connection data workflows included on the Defense Center. All the predefined connection data workflows use the table view of connection data. For information on accessing connection data, see Viewing Connection and Security Intelligence Data.
Predefined Security Intelligence Workflows
Supported Devices: Any except Series 2
Supported Defense Centers: Any except DC500
The following table describes the predefined Security Intelligence workflows included on the Defense Center. All the predefined Security Intelligence workflows use the table view of Security Intelligence events. For more information on accessing Security Intelligence event data, see Viewing Connection and Security Intelligence Data.
Predefined Host Workflows
The following table describes the predefined workflows that you can use with host data.
This workflow contains a table view of hosts followed by the host view. Workflow views based on the Hosts table allow you to easily view data on all IP addresses associated with a host. See Viewing Hosts for more information. |
|
You can use this workflow to analyze the operating systems in use on your network. This workflow provides a series of pages that start with a list of the operating systems and operating system vendors on your network, continuing with the number of hosts running each version of that operating system. The next page lists hosts by criticality, IP address, and NetBIOS name, with their associated operating systems and operating system vendors. The workflow finishes with a table view of hosts, followed by the host view. See Viewing Hosts for more information. |
Predefined Indications of Compromise Workflows
The following table describes the predefined workflows that you can use with IOC (Indications of Compromise) data.
This workflow begins with a summary view of IOC data grouped by count and category, followed by a detail view that further subdivides the summary data by event type. Next is a full table view of IOC data. The workflow concludes with the host view. For more information on viewing and interpreting IOC data, see Working with Indications of Compromise. |
|
You can use this workflow to gauge which hosts on your network are most likely to be compromised (based on IOC data). This workflow contains a view of host IP addresses by IOC data count, followed by a table view of IOC data and concluding with the host view. For more information on viewing and interpreting IOC data, see Working with Indications of Compromise. |
Predefined Applications Workflows
The following table describes the predefined workflows that you can use with application data.
You can use this workflow to analyze running applications of each estimated business relevance level on your network, so you can monitor appropriate use of your network resources. This workflow begins with a count of hosts running applications of each relevance level, followed by a table of individual applications with their business relevance levels and host counts, a table view of applications, and the host view. See Viewing Applications for more information. |
|
You can use this workflow to analyze running applications of each category (such as email, search engine, or social networking) on your network, so you can monitor appropriate use of your network resources. This workflow begins with a count of hosts running applications of each category, followed by a count of hosts running individual applications, a table view of applications, and the host view. See Viewing Applications for more information. |
|
You can use this workflow to analyze running applications of each estimated security risk level on your network, so you can estimate the potential risk of users’ activity and take appropriate action. This workflow begins with a count of hosts running applications of each risk level, followed by a table of individual applications with their business relevance levels and host counts, a table view of applications, and the host view. See Viewing Applications for more information. |
|
You can use this workflow to obtain detailed information about the applications and associated hosts on your network, so you can closely examine host application activity. This workflow begins with a list of individual host IP addresses running applications, followed by a table view of applications and the host view. |
|
You can use this workflow to analyze running applications on your network, so you can gain an overview of how the network is being used. This workflow begins with a count of hosts running individual applications, followed by a table view of applications and the host view. See Viewing Applications for more information. |
Predefined Application Details Workflows
The following table describes the predefined workflows that you can use with application detail and client data.
You can use this workflow to analyze the client applications on your network in more detail. This workflow contains a series of pages that begin with a list of the client applications and application products on your network and a count of the number of hosts running each application. You can then view the number of hosts running each version of that application. The next page lets you identify which applications have been accessed most frequently on specific hosts. The workflow then provides a table view of client applications, followed by the host view. See Viewing Application Details for more information. |
|
This workflow contains a table view of client applications, followed by the host view. See Viewing Application Details for more information. |
Predefined Servers Workflows
The following table describes the predefined workflows that you can use with server data.
You can use this workflow to analyze the most frequently used applications on your network. This workflow contains a series of pages that show applications with a count of hosts where each application occurs, then add the vendor and version of each application. The workflow then concludes with a table view listing the applications per host, followed by the host view. See Viewing Servers for more information. |
|
You can use this workflow to analyze the most active applications on your network. This workflow contains a series of pages that show applications with a count of how often each application is accessed, then add the vendor and version information for each application. The workflow finishes with a page containing a table view listing the applications per host, followed by the host view. See Viewing Servers for more information. |
|
You can use this workflow to analyze the vendors and versions of detected server application protocols in detail. The workflow contains a list of servers associated with their vendors, then a list of servers correlated with both vendor and version, finishing with a table view of servers and the host view. |
|
This workflow contains a table view of applications followed by the host view. See Viewing Servers for more information. |
Predefined Host Attributes Workflows
The following table describes the predefined workflow that you can use with host attribute data.
You can use this workflow to monitor IP addresses of hosts on your network and the hosts’ status. This workflow begins with a table view of host attributes that lists individual IP addresses with current user, host criticality, notes, and white list compliance. It finishes with the host view. For more information, see Viewing Host Attributes. |
Predefined Discovery Events Workflows
The following table describes the predefined workflow that you can use with discovery event data.
This workflow provides a detailed list, in table view form, of discovery events, followed by the host view. For more information, see Understanding the Discovery Events Table. |
Predefined User Workflows
The following table describes the predefined user workflows included on the Defense Center.
This workflow provides a list of user information collected from user events or from the LDAP server connection. For details about the user identity workflow, see Viewing Users. |
Predefined Vulnerabilities Workflows
The following table describes the predefined vulnerabilities workflow included on the Defense Center.
You can use this workflow to review s a table view of vulnerabilities showing all the vulnerabilities in the database, followed by a table view of only those active vulnerabilities that apply to the detected hosts on your network.The workflow ends in a vulnerability detail view, which contains a detailed description for every vulnerability that meets your constraints. For more information, see Viewing Vulnerabilities. |
Predefined Third-Party Vulnerabilities Workflows
The following table describes the predefined third-party vulnerabilities workflows included on the Defense Center.
You can use this workflow to see quickly how many third-party vulnerabilities you have detected per host IP address on your monitored network. The workflow concludes with a table view of third-party vulnerabilities, followed by the host view. For more information, see Viewing Third-Party Vulnerabilities. |
|
You can use this workflow to see quickly how many third-party vulnerabilities you have detected per third-party vulnerability source, such as the QualysGuard Scanner. This workflow provides some details about those vulnerabilities on an intermediate drill-down page, then concludes with a table view of third-party vulnerabilities and the host view. For more information, see Viewing Third-Party Vulnerabilities. |
Predefined Correlation and White List Workflows
There is a predefined workflow for each type of correlation data, white list events, white list violations, and remediation status events.
This workflow contains a table view of correlation events. See Working with Correlation Events for more information. |
|
This workflow contains a table view of white list events. See Working with White List Events for more information. |
|
This workflow provides a series of pages that list all the host IP addresses that violate at least one white list. The first page sorts the addresses based on the number of violations per address, with the IP addresses with the most number of violations at the top of the list. If a host IP address violates more than one white list, there is a separate row for each violated white list. The workflow also contains a table view of white list violations that lists all violations, with the most recently detected violation at the top of the list. Each row in the table contains a single detected violation. See Working with White List Violations for more information. |
|
This workflow includes a table view of white list violations that lists all violations with the most recently detected violation at the top of the list. Each row in the table contains a single detected violation. See Working with White List Violations for more information. |
|
This workflow contains a table view of remediation status, which includes the name of the policy that was violated and the name and status of the remediation that was applied. See Working with Remediation Status Events for more information. |
Predefined System Workflows
The FireSIGHT System is delivered with some additional workflows, including system events such as audit events and health events, as well as workflows that list results from rule update imports and active scans.
This workflow contains a table view of the audit log that lists audit events. See Viewing Audit Records for more information. |
|
This workflow displays events triggered by the health monitoring policy. See Working with the Health Events Table View for more information. |
|
This workflow contains a table view listing information about both successful and failed rule update imports. For more information, see Importing Rule Updates and Local Rule Files. |
|
This workflow contains a table view listing each completed scan. For more information, see Working with Active Scan Results. |
Saved Custom Workflows
License: Protection + FireSIGHT
In addition to predefined workflows, which cannot be modified, your Defense Center includes several saved custom workflows. Each of these workflows is based on a custom table and can be modified. For information on accessing these workflows, see Viewing a Workflow Based on a Custom Table.
You can use this workflow to quickly pick out and focus in on hosts that are important to your network, currently vulnerable, and possibly currently under attack. By default, this workflow starts with a summary of events sorted by impact level, then by host criticality, and then by the number of occurrences of the event. You can use the second page of the workflow to drill down and view the source and destination addresses where specific events occur. The workflow concludes with a table view of Intrusion Events with Destination Criticality, then the packet view. This workflow is based on the Intrusion Events with Destination Criticality custom table. For more information, see Understanding Custom Tables. |
|
This workflow lists events and their type in order of event priority, along with a count showing how many times each event has occurred. This workflow begins with a drill-down page that contains the priority level, classification and count of each listed event. The last pages in the workflow are the table view of events and the packet view. This workflow is based on the Intrusion Events custom table. For more information, see Understanding Custom Tables. |
|
You can use this workflow to find the most recent attacks on hosts that are important to your network and currently vulnerable. By default, this workflow starts with a list of the most recent events, sorted by impact level. The next page of the workflow provides a table view of Intrusion Events with Destination Criticality, followed by the packet view. This workflow is based on the Intrusion Events with Destination Criticality custom table. For more information, see Understanding Custom Tables. |
|
You can use this workflow to quickly view the basic information in the Hosts with Servers custom table. By default, this workflow begins with a table view of hosts with servers, followed by the host view. This workflow is based on the Hosts with Servers custom table. For more information, see Understanding Custom Tables. |
|
Intrusion Events with Destination Criticality Default Workflow |
You can use this workflow to quickly view the basic information in the Intrusion Events with Destination Criticality custom table. By default, this workflow starts with a table view of Intrusion Events with Destination Criticality, followed by the packet view. This workflow is based on the Intrusion Events with Destination Criticality custom table. For more information, see Understanding Custom Tables. |
You can use this workflow to quickly view the basic information in the Intrusion Events with Source Criticality custom table. By default, this workflow starts with a table view of Intrusion Events with Source Criticality, followed by the packet view. This workflow is based on the Intrusion Events with Source Criticality custom table. For more information, see Understanding Custom Tables. |
|
You can use this workflow to determine what servers are most frequently used on your network and which hosts are running those servers. By default, this workflow begins with a summary of servers with the frequency of access for each service. The next page lists servers by operating system vendor and version. The workflow concludes with a table view of hosts with servers, followed by the host view. This workflow is based on the Hosts with Servers custom table. For more information, see Understanding Custom Tables. |
Using Workflows
The drill-down and table view pages in workflows allow you to quickly narrow your view of the data so you can zero in on events that are significant to your analysis. Although the data in each type of workflow is different, all workflows share a common set of features. The following sections describe these features and explain how to use them:
- Selecting Workflows describes the workflow selection page and how to select a workflow to use.
- Understanding the Workflow Toolbar describes the toolbar options available in workflows.
- Using Workflow Pages describes the features that appear on all workflow pages and explains how to use them.
- Setting Event Time Constraints describes how to set the time range for event-based workflows. The workflow includes events generated in the specified time range.
- Constraining Events describes features that are used in workflows to constrain, or narrow, the view of data in workflows and to advance through workflow pages.
- Using Compound Constraints explains how compound constraints can be used and provides examples.
- Sorting Drill-Down Workflow Pages describes features for sorting the data displayed in workflows, and for removing and restoring table columns to view.
- Selecting Rows on a Workflow Page describes how to select data rows in the displayed table that you want to analyze or on which you want to perform some other action.
- Navigating to Other Pages in the Workflow describes how to open other workflows using the constraints, including any selected events, from the current workflow.
- Navigating Between Workflows describes the Jump to drop-down list and explains how you can use it to apply the current constraints to a different workflow.
- Searching for Events provides information about the feature used to search event data.
- Using Bookmarks describes how to create, manage, and use bookmarks.
Selecting Workflows
The FireSIGHT System provides predefined workflows for the types of data listed in the following table.
When you view any of the kinds of data described in the above table, events appear on the first page of the default workflow for that data.
Also note that workflow access depends on your user role (see Configuring User Roles), as follows:
- Administrator users can access any workflow, and are the only users who can access the audit log, scan results, and the rule update import log.
- Maintenance Users can access health events.
- Security Analyst and Security Analyst (Read Only) users can access intrusion, malware, file, connection, discovery, vulnerability, correlation, and health workflows.
To view the data using a workflow other than the default:
Access: Admin/Any Security Analyst
Step 1 Select the appropriate menu path and option as described in the Features Using Workflows table.
The first page of the default workflow for that data type appears. For information on specifying a different default workflow, see Configuring Event View Settings.
Step 2 Optionally, use a different workflow. Click (switch workflow) next to the workflow title, then select the workflow you want to use.
Step 3 The first page of your selected workflow appears.
Understanding the Workflow Toolbar
Each page in a workflow includes a toolbar that offers quick access to related features. The following table describes each of the links on the toolbar.
Bookmarks the current page so you can return to it later. Bookmarking captures the constraints in effect on the page you are viewing so you can return to the same data (assuming the data still exists) at a later time. See Using Bookmarks for information about creating bookmarks. |
|
Opens the report designer with the currently constrained workflow as the selection criteria. See Creating a Report Template from an Event View for information about creating reports. |
|
Opens a dashboard relevant to your current workflow. For example, Connection Events workflows link to the Connection Summary dashboard. See Using Dashboards for information about using dashboards. |
|
Displays a list of saved bookmarks from which you can select. See Using Bookmarks for information about creating and managing bookmarks. |
|
Displays a Search page where you can perform advanced searches on data in the workflow. You can also click the down arrow icon to select and use a saved search. See Searching for Events for information about searching workflows. |
Using Workflow Pages
The actions you can perform on a workflow page depend on the type of page. Table view pages and drill-down pages contain many features you can use to constrain the set of events you want to view or to navigate the workflow. For more information on the features available on each type of page, see the following sections:
Using Common Table View or Drill-Down Page Functionality
Table view and drill-down workflow pages provide a set of icons and other features in the table header and table rows that you can use to perform actions on the displayed data.
The features are described in the following table.
Click the blue down-arrow icon to display the corresponding row in the next page of the workflow. |
|
Click the network file trajectory icon, which appears in file name and SHA-256 hash value columns, to view the file’s trajectory map in a new window. For more information, see Analyzing Network File Trajectory. Note that because the DC500 Defense Center, Series 2 devices, and Cisco NGIPS for Blue Coat X-Series do not support advanced malware protection, you cannot view network file trajectory for network-based malware and file events on these appliances. |
|
Click the host profile icon, which appears in IP address columns, to display the host profile associated with that IP address in a pop-up window. For more information, see Using Host Profiles. Hosts that have been tagged as potentially compromised by triggered indications of compromise (IOC) rules appear with the compromised host icon instead of the usual icon. For more information on IOC, see Understanding Indications of Compromise.
If the host profile icon is grayed out, you cannot view the host profile because that host cannot be in the network map (for example, If you are performing traffic filtering based on Security Intelligence data, host icons next to blacklisted and monitored IP addresses in the connection event view look slightly different. This helps you identify which host in a connection was blacklisted. Note that neither the DC500 Defense Center nor Series 2 devices support Security Intelligence data. |
|
Click the threat score icon, which appears in threat score columns, to view the Dynamic Analysis Summary report for the highest threat score associated with a file. Note that because the DC500 Defense Center, Series 2 devices, and Cisco NGIPS for Blue Coat X-Series support advanced malware protection, you cannot view the Dynamic Analysis Summary report on these appliances. |
|
Click the user icon, which appears in user identity columns, to view user profile information. For more information, see Understanding User Details and Host History. If the user icon is grayed out, you cannot view the user profile because that user cannot be in the database (FireAMP Connector user). |
|
Click the vulnerability icon, which appears in third-party vulnerability ID columns, to view vulnerability details for third-party vulnerabilities. For more information, see Viewing Vulnerability Details. |
|
Select the check boxes by two or more rows on a page to indicate which rows you want to affect, then click one of the buttons at the bottom of the page (for example, the View button). You can also select the check box at the top of the row to select all the rows on the page. |
|
In some workflow pages, such as those for connection events, intrusion events, file events, and malware events, routable IP addresses include information about the associated country. When this geolocation information is available, the country’s flag and ISO code appear in the appropriate column (such as Source Country). Hover your pointer over the flag to view the country name. When viewing individual (rather than aggregated) data points, you can click the flag icon to view further geolocation details. See Using Geolocation for more information. Note that the DC500 Defense Center does not support geolocation data. |
|
Lists the values, if present, constraining the data view. Click the expand arrow ( To remove a single constraint, click it. To remove a compound constraint, click Compound Constraints . Click Edit Search or Save Search to open a search page pre-populated with the current single constraints. See Constraining Events for more information. Note Compound constraints are constraints created based on rows with multiple non-count values. You cannot perform a search or save a search on a compound constraint. |
|
The date range located in the upper right corner of the page sets a time range for events to include in the workflow. See Setting Event Time Constraints for more information. Note that events that were generated outside the appliance's configured time window (whether global or event-specific) may appear in an event view if you constrain the event view by time. This may occur even if you configured a sliding time window for the appliance. |
|
Workflow page links appear in the upper left corner of predefined workflow table view and drill-down pages, above events and below the workflow name. Click a workflow page link to display that page using any active constraints. |
|
The name of the workflow appears at the top of the page. Beside it, when applicable, is the (switch workflows) link, which you can use to select other workflows of the same type. |
Using Geolocation
Supported Devices: feature dependent
Supported Defense Centers: Any except DC500
While monitoring your network, the geolocation feature provides you with additional data about the geographical sources of routable IP addresses (country, continent, and so on). You can use this data to determine if, for example, connections are originating from or terminating in countries unconnected with your organization.
Geolocation information is available for intrusion events, connection events, file events, malware events, host profiles, and user profiles. Geolocation information is also available in the Context Explorer and the dashboard.
You can use geolocation data (source and destination country/continent) as conditions for access control rules, as well as create custom geolocation objects for this purpose. You can also use source/destination country data as conditions for correlation rules and traffic profiles. For more information, see Working with Geolocation Objects, Controlling Traffic by Network or Geographical Location, Creating Rules for Correlation Policies, and Specifying Traffic Profile Conditions.
By installing geolocation database (GeoDB) updates, you can view a Geolocation Details page with granular information available for an IP address, such as postal code, coordinates, time zone, Autonomous System Number (ASN), Internet service provider (ISP), use type (home or business), organization, domain name, connection type, and proxy information. You can also pinpoint the detected location with any of four third-party map tools. Without a GeoDB update, only the flag icon and country name appear; you cannot view the Geolocation Details page. For information on installing and updating the GeoDB, see Updating the Geolocation Database. You can view the current version of your GeoDB update by clicking Help > About .
Depending on availability, a number of fields may appear on the Geolocation Details page; fields with no information are not displayed. The following table contains information on these fields.
Step 1 In an event view, host profile, or other geolocation-supporting page, click the small country flag icon or ISO country code that appears by an individual data point. (You cannot view geolocation details for aggregate geolocation information, such as on the Connection Summary dashboard, despite the presence of flag icons.)

Tip In event views, hover your pointer over the flag icon to view a tooltip with the country’s name.
The Geolocation Details page appears in a new window.
Using Table View Pages
Table view s include a column for each of the fields in the database if the column is enabled by default. Note that when you disable a column on a table view, the FireSIGHT System adds the Count column to the event view if disabling the column would create two or more identical rows. When you click on a value in a table view page, you constrain by that value. When you create a custom workflow, you add a table view to it by clicking Add Table View .
Table view pages provide some additional features not available on drill-down, host view, packet view, or vulnerability detail pages. The following table provides more information on those features.
Click this icon in the column heading that you want to hide. In the pop-up window that appears, click Apply . |
|
When you remove columns from a page, or columns are disabled by default, the column names appear in the Disabled Columns list, which is located above the table and hidden by default.
To add a disabled column back to the event view, click the Search Constraints expand arrow ( See Sorting Drill-Down Workflow Pages for more information. |
Using Drill-Down Pages
Drill-down pages contain a subset of columns that are available in the database. Note that drill-down pages for predefined workflows always have a Count column. Drill-down pages allow you to narrow the scope of events you are viewing and to move forward in the workflow. If you click on a value in a drill-down page, for example, you constrain by that value and move to the next page in the workflow, focusing more closely on events that match your selected values. Clicking a value in a drill-down page does not disable the column where the value is, even if the page you advance to is a table view. When you create a custom workflow, you add a drill-down page to it by clicking Add Page .
For more information on using features on drill-down pages to constrain the set of events as you go through a workflow, see Using Common Table View or Drill-Down Page Functionality.
Using the Host View, Packet View, or Vulnerability Detail Pages
The final page in a discovery event, host, host attributes, indications of compromise, servers, client applications, or connection data workflow is the host view. The final page in a vulnerability workflow is the vulnerability detail page. An intrusion event workflow always ends with the packet view. On the final page of a workflow, you can expand detail sections to view specific information about each object in the set you focused on over the course of the workflow. Although the web interface does not list the constraints on the final page of a workflow, previously set constraints are retained and applied to the set of data.
Setting Event Time Constraints
Each event has a time stamp that indicates when the event occurred. You can constrain the information that appears in some workflows by setting the time window, sometimes called the time range.
Workflows based on events that can be constrained by time include a time range line at the top of the page, as shown in the following graphic.

By default, workflows on Cisco appliances use an expanding time window set to the past hour. For example, if you log in at 11:30 AM, you will see events that occurred between 10:30 AM and 11:30 AM. As time moves forward, the time window expands. At 12:30 PM, you will see events that occurred between 10:30 AM and 12:30 PM.
You can change this behavior by setting your own default time window, which governs three properties:
- time window type (static, expanding, or sliding)
- time window length
- the number of time windows (either multiple time windows or a single global time window)
For general information on the default time window, see Default Time Windows.
Regardless of the default time window setting, you can manually change the time window during your event analysis by clicking the time range at the top of the page, which displays the Date/Time pop-up window. Depending on the number of time windows you configured and the type of appliance you are using, you can also use the Date/Time window to change the default time window for the type of event you are viewing.
Finally, you can pause the time window, which allows you to examine the data provided by the workflow without the time window changing and removing or adding events that you are not interested in. Note that to avoid displaying the same events on different workflow pages, the time window automatically pauses when you click a link at the bottom of the page to display another page of events; you can unpause the time window when you are ready.
Changing the Time Window
Regardless of the default time window, you can manually change the time window during your event analysis.

Note Manual time window settings are valid for only the current session. When you log out and then log back in, time windows are reset to the default.
Depending on the number of time windows you configured, changing the time window for one workflow may affect other workflows on the appliance. For example, if you have a single, global time window, changing the time window for one workflow changes it for all other workflows on the appliance. On the other hand, if you are using multiple time windows, changing the audit log or health event workflow time windows has no effect on any other time window, while changing the time window for other kinds of events affects all events that can be constrained by time (with the exception of audit events and health events).
Note that because not all workflows can be constrained by time, time window settings have no effect on workflows based on hosts, host attributes, applications, application details, vulnerabilities, users, or white list violations.
Use the Time Window tab on the Date/Time window to manually configure a time window. Depending on the number of time windows you configured in your default time window settings, the tab’s title is one of the following:
- Events Time Window , if you configured multiple time windows and are setting the time window for a workflow other than the audit log or health events workflow
- Health Monitoring Time Window , if you configured multiple time windows and are setting the time window for the health events workflow
- Audit Log Time Window , if you configured multiple time windows and are setting the time window for the audit log
- Global Time Window , if you configured a single time window
The first decision you must make when configuring a time window is the type of time window you want to use:
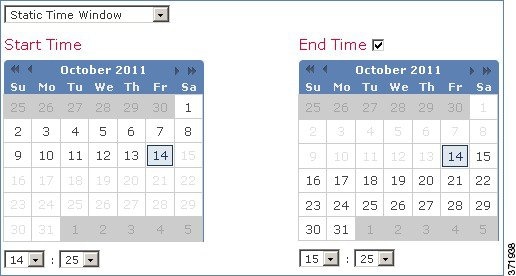
- A static time window displays all the events generated from a specific start time to a specific end time.
- An expanding time window displays all the events generated from a specific start time to the present; as time moves forward, the time window expands and new events are added to the event view.
- A sliding time window displays all the events generated from a specific start time (for example, one week ago) to the present; as time moves forward, the time window “slides” so that you see only the events for the range you configured (in this example, for the last week).
Depending on what type you select, the Date/Time window changes to give you different configuration options. The following graphic shows the Date/Time window, specifying that you want to use an expanding time window. With expanding time windows, the End Time calendar is grayed out and specifies that the end time is “Now.”
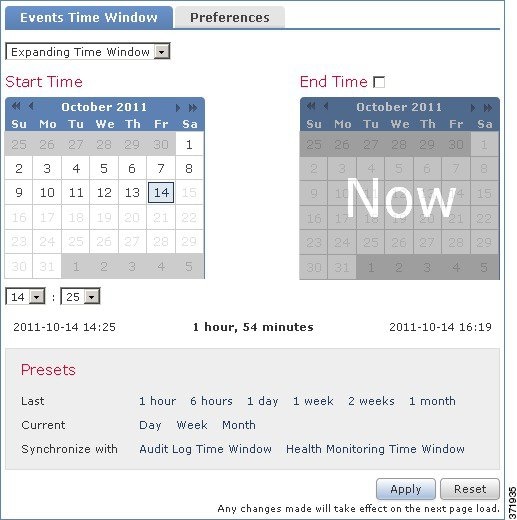
If you use a static time window, you can set an end time.
If you choose to use a sliding time window, your options change further.


Note The FireSIGHT System uses a 24-hour clock based on the time you specified in your time zone preferences. See Setting Your Default Time Zone for information about configuring a time zone.
The following table explains the various settings you can configure on the Time Window tab.
To change the time window during event analysis:
Access: Admin/Maint/Any Security Analyst
Step 1 On a workflow constrained by time, click the time range icon ( ).
).
Step 2 On the Time Window tab, set the time window as described in the Time Window Settings table.

Tip Click Reset to change the time window back to the default settings.
The window closes and the event view page displays events from the new time range.
Changing the Default Time Window for Your Event Type
During your event analysis, you can use the Preferences tab on the Date/Time window to change the default time window for the type of event you are viewing without having to use the event view settings (see Default Time Windows).
Keep in mind that changing the default time window in this way changes the default time window for only the type of event you are viewing. For example, if you configured multiple time windows, changing the default time window on the Preferences tab changes the settings for either the events, health monitoring, or audit log window, in other words, whichever time window is indicated by the first tab. If you configured a single time window, changing the default time window on the Preferences tab changes the default time window for all types of events.
The following graphic shows the Defense Center version of the Preferences tab, on an appliance that has multiple time windows configured.
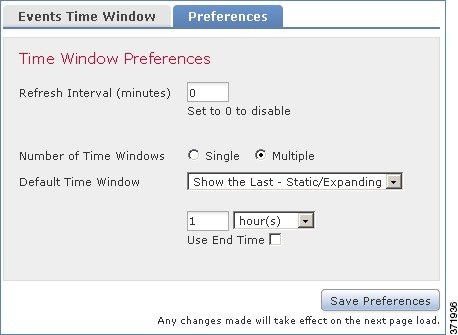
The following table explains the various settings you can configure on the Preferences tab.
To change time window preferences during event analysis:
Access: Admin/Maint/Any Security Analyst
Step 1 On a workflow constrained by time, click the time range icon ( ).
).
Step 2 Select the Preferences tab and change your preferences, as described in the Time Window Preferences table.
Step 3 Click Save Preferences .
Pausing the Time Window
You can pause the time window, which allows you to examine a snapshot of the data provided by the workflow. This is useful because when an unpaused workflow updates, it may remove events that you want to examine or add events that you are not interested in.
Note that you cannot pause a static time window. In addition, pausing an event time window has no effect on dashboards, nor does pausing a dashboard have any effect on pausing an event time window.
When you are finished with your analysis, you can unpause the time window. Unpausing the time window updates it according to your preferences, and also updates the event view to reflect the unpaused time window.
If the database contains more events than can be displayed on a single workflow page, you can click the links at the bottom of the page to display more events (see Navigating to Other Pages in the Workflow). When you do this, the time window automatically pauses so that you do not see the same events twice. You can unpause the time window when you are ready.
Access: Admin/Maint/Any Security Analyst
Step 1 On the time range control, click the pause icon ( ).
).
The time window is paused until you unpause it.
Access: Admin/Maint/Any Security Analyst
Step 1 On the time range control, click the play icon ( ).
).
The time window is unpaused and updates according to your preferences. The event view updates to reflect the current time window.
Constraining Events
The information that you see on a workflow page is determined by the constraints that you impose. For example, when you initially open an event workflow, the information is constrained to events that were generated in the previous hour.
To advance to the next page in the workflow and constrain the data you are viewing by specific values, select the rows with those values on the page and click View . To advance to the next page in the workflow retaining the current constraints and carrying forward all events, select View All.

Note If you select a row with multiple non-count values and click View, you create a compound constraint. For more information on compound constraints, see Using Compound Constraints.
There is a third method for constraining data in a workflow. To constrain the page to the rows with values that you selected and also add the selected value to the list of constraints at the top of the page, click a value within a row on the page.
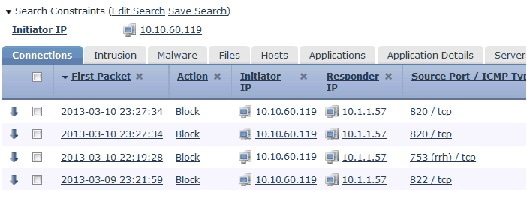
For example, if you click 10.10.60.119 in the Initiator IP column on a page with the following events:

...then the constrained page includes only the events with that IP address:

Tip The procedure for constraining connection events based on Monitor rule criteria is slightly different and you may need to take some extra steps. Additionally, you cannot constrain connection events by associated file or intrusion information. For more information, see Working with Connection and Security Intelligence Data Tables.
You can also use searches to constrain the information in a workflow. The search criteria you enter on the search page are listed as the constraints at the top of the page, with the resulting events constrained accordingly. On the Defense Center, the current constraints are also applied when navigating to other workflows, unless they are compound constraints (see Navigating Between Workflows).
When searching, you must pay careful attention to whether your search constraints apply to the table you are searching. For example, client data is not available in connection summaries. If you search for connection events based on the detected client in the connection and then view the results in a connection summary event view, the Defense Center displays connection data as if you had not constrained it at all. Invalid constraints are labeled as not applicable (N/A) and are marked with a strikethrough.
The following table describes each of the actions you can perform when applying a constraint.
|
For example, if you are viewing a list of logged connections and want to constrain the list to only those you allowed using access control, click Allow in the Action column. As another example, if you are viewing intrusion events and want to constrain the list to only events where the destination port is 80, click 80 (http)/tcp in the DST Port/ICMP Code column. |
|
the check box for events with those values and click View . Note that a compound constraint is added if the row contains multiple non-count values. For more information on compound constraints, see Using Compound Constraints. |
|
Edit Search in the Search Constraints box. Use this feature when you want to constrain against multiple values in a single column. For example, if you want to view the events related to two IP addresses, click Edit Search , then modify the appropriate IP address field on the Search page to include both addresses, and then click Search . |
|
Save Search in the Search Constraints box and give the query a name. Note that you cannot save queries containing compound constraints. For more information on compound constraints, see Using Compound Constraints. |
|
Jump to and select the event view. See Navigating Between Workflows for more information. Note that you do not retain compound constraints when you switch to another workflow. For more information on compound constraints, see Using Compound Constraints. |
|
the expand arrow ( |
Using Compound Constraints
Compound constraints are based on all non-count values for a specific event. When you select a row with multiple non-count values, you set a compound constraint that only retrieves events matching all the non-count values in that row on that page. For example, if you select a row that has a source IP address of
10.10.31.17
and a destination IP address of
10.10.31.15
and a row that has a source IP address of
172.10.10.17
and a destination IP address of
172.10.10.15
, you retrieve all of the following:
When you combine compound constraints with simple constraints, the simple constraints are distributed across each set of compound constraints. If, for example, you added a simple constraint for a protocol value of
tcp
to the compound constraints listed above, you retrieve all of the following:
- Events that have a source IP address of 10.10.31.17 AND a destination IP address of 10.10.31.15 AND a protocol of tcp
- Events that have a source IP address of 172.10.31.17 AND a destination IP address of 172.10.31.15 AND a protocol of tcp
You cannot perform a search or save a search on a compound constraint. You also cannot retain compound constraints when you use the event view links or click (switch workflow) to switch to another workflow. If you bookmark an event view with compound constraints applied, the constraints are not saved with the bookmark.
To clear all compound constraints, click Compound Constraints .
Sorting Table View Pages and Changing Their Layout
When viewing data in a workflow, you can sort the data based on any available column and remove and restore columns to view. You can sort data in ascending or descending order by column.

Tip If you create a custom workflow, you can fully customize the arrangement of columns on the pages and predefine the page sort order. See Creating Custom Workflows for more information.
Sorting Drill-Down Workflow Pages
When viewing data in a workflow or event view, you can sort the data based on any available column and remove and restore columns to view. You can sort data in ascending or descending order by column. The direction icon ( ) indicates which column the data is sorted by, and whether the sort is ascending (upward-pointing icon) or descending (downward-pointing icon).
) indicates which column the data is sorted by, and whether the sort is ascending (upward-pointing icon) or descending (downward-pointing icon).

Tip If you create a custom workflow, you can fully customize the arrangement of columns on the pages and predefine the page sort order. See Creating Custom Workflows for more information.
Access: Admin/Maint/Any Security Analyst
Step 1 Click the column title.
Access: Admin/Maint/Any Security Analyst
Step 1 Click the column title again.
Selecting Rows on a Workflow Page
There are several different ways to select and then act on the rows on workflow pages:
You can then click any of the buttons at the bottom of the page ( View , Delete , and so on) to perform that action on all of the events on that page.
You can then click any of the buttons at the bottom of the page to perform that action on only the events associated with that row.
- To select a single row and view its associated events on the next page of the workflow, click the arrow icon (
 ).
).
Note You cannot select rows from multiple pages at once.
Navigating to Other Pages in the Workflow
If the database contains more events than can be displayed on a single workflow page, you can click the links at the bottom of the page to display more events.
When you click one of these links, the time window automatically pauses so that you do not see the same events twice; you can unpause the time window when you are ready. For more information, see Setting Event Time Constraints.
The following table describes how to use the navigation links.
Navigating Between Workflows
You can navigate to other workflows using the links in the Jump to... drop-down list on a workflow page. Select the drop-down list to view and select additional workflows.
When you select a new workflow, properties shared by the rows you select and the constraints you set are used in the new workflow, if they are applicable. If configured constraints or event properties do not map to fields in the new workflow, they are dropped. In addition, compound constraints are not retained when you switch from one workflow to another. In addition, constraints from the captured files workflow only transfer to file and malware event workflows.

Note When you view event counts over a time range, the total number of events may not reflect the number of events for which more detailed data is available. This occurs because the system sometimes prunes older event details to manage disk space usage. To minimize the occurrence of event detail pruning, you can fine-tune event logging to log only those events most important to your deployment. For more information, see Logging Connections in Network Traffic.
Note that unless you have either paused the time window or have configured a static time window, the time window changes when you change workflows. For more information, see Setting Event Time Constraints.
The Jump to drop-down list provides quick access to workflows for the following tables:
- connection events
- security intelligence events
- intrusion events
- malware events
- file events
- hosts
- indications of compromise
- applications
- application details
- servers
- host attributes
- discovery events
- users
- vulnerabilities
- third-party vulnerabilities
- correlation events
- white list events
This feature enhances your ability to investigate suspicious activity. For example, if you are viewing connection data and notice that an internal host is transmitting an abnormally large amount of data to an external site, you can select the responder IP address and the port as constraints and then jump to the Applications workflow. The applications workflow will use the responder IP address and port as IP Address and Port constraints and display additional information about the application, such as what kind of application it is. You can also click Hosts at the top of the page to view the host profile for the remote host.
After finding more information about the application, you can select Correlation Events to return to the connection data workflow, remove the Responder IP from the constraints, add the Initiator IP to constraints, and select Application Details to see what client the user on the initiating host used when transferring data to the remote host. Note that the Port constraint is not transferred to the Application Details page. While keeping the local host as a constraint, you can also use other navigation buttons to find additional information:
- To discover if any policies have been violated by the local host, keep the IP address as a constraint and select Correlation Events from the Jump to drop-down list.
- To find out if an intrusion rule triggered against the host, indicating a compromise, select Intrusion Events from the Jump to drop-down list.
- To view the host profile for the local host and determine if the host is susceptible to any vulnerabilities that may have been exploited, select Hosts from the Jump to drop-down list.
Using Bookmarks
Create a bookmark if you want to return quickly to a specific location and time in an event analysis. Bookmarks retain information about:
- the workflow you are using
- the part of the workflow you are viewing
- the page number within the workflow
- any search constraints
- any disabled columns
- the time range you are using
The bookmarks you create are available to all user accounts with bookmark access. This means that if you uncover a set of events that require more in-depth analysis, you can easily create a bookmark and turn over the investigation to another user with the appropriate privileges.

Note If the events that appear in a bookmark are deleted (either directly by a user or by automatic database cleanup), the bookmark no longer displays the original set of events.
See these sections for more information about using bookmarks:
- Creating Bookmarks describes how to create a new bookmark.
- Viewing Bookmarks describes how to view and use existing bookmarks.
- Deleting Bookmarks describes how to delete bookmarks.
Creating Bookmarks
Use the following procedure to create a new bookmark.
Access: Admin/Maint/Any Security Analyst
Step 1 During an event analysis, with the events of interest displayed, click Bookmark This Page .
The Create a Bookmark page appears.
Step 2 In the Bookmark Name field, type a name (up to 80 alphanumeric characters and spaces) for the bookmark, then click Save Bookmark .
The bookmark is saved and the event page you bookmarked appears again.
Viewing Bookmarks
Use the following procedure to view and use existing bookmarks.
Access: Admin/Maint/Any Security Analyst
Step 1 From any event view, click View Bookmarks .
Step 2 Next to the bookmark you want to use, click View .
The page you bookmarked appears.

Note If the events that originally appeared in a bookmark are deleted (either directly by a user or by automatic database cleanup), the bookmark no longer displays the original set of events.
Deleting Bookmarks
Use the following procedure to delete bookmarks. Note that deleting a bookmark does not affect the events retrieved by that bookmark.
Access: Admin/Maint/Any Security Analyst
Step 1 From any event view, click View Bookmarks .
Step 2 Click Delete next to the bookmark you want to remove.
Using Custom Workflows
If the predefined and Cisco-provided custom workflows do not meet your needs, you can create custom workflows.
- Creating Custom Workflows for a procedure to create custom workflows
- Creating Custom Connection Data Workflows for a procedure to create a custom workflow based on connection data
- Viewing Custom Workflows for procedures for viewing custom workflows based on event and custom tables
- Editing Custom Workflows for a procedure for editing custom workflows
- Deleting Custom Workflows for a procedure for deleting custom workflows
Creating Custom Workflows
If the predefined and Cisco-provided custom workflows do not meet your needs, you can create custom workflows.

Tip Instead of creating a new custom workflow, you can export a custom workflow from another appliance and then import it onto your appliance. You can then edit the imported workflow to suit your needs. For more information, see Importing and Exporting Configurations.
When you create a custom workflow, you:
- select a table to be the source of the workflow
- provide a workflow name
- add drill-down pages and table view pages to the workflow
For each drill-down page in the workflow, you can:
- provide a name that appears at the top of the page in the web interface
- include up to five columns per page
- specify a default sort order, ascending or descending
You can add table view pages in any position in the sequence of workflow pages. They do not have any editable properties, such as a page name, sort order, or user-definable column positions.
The final page of a custom workflow depends on the table on which you base the workflow, as described in the following table. These final pages are added by default when you create the workflow.
The appliance does not add a final page to custom workflows based on other kinds of events (for example, audit log or malware events).

Note The procedure for creating a custom workflow based on connection data is slightly different. For more information, see the next section, Creating Custom Connection Data Workflows.
Access: Admin/Any Security Analyst
Step 1 Select Analysis > Custom > Custom Workflows .
The Custom Workflows page appears.
Step 2 Click Create Custom Workflow .
The Edit Custom Workflow page appears.
Step 3 Type a name for the workflow in the Name field.
You can use up to 60 alphanumeric characters and spaces in the name.
Step 4 Optionally, type a description for the workflow in the Description field.
You can use up to 80 alphanumeric characters and spaces.
Step 5 Select the table you want to include from the Table drop-down list.
Step 6 Optionally, click Add Page to add one or more drill-down pages to the workflow.
A drill-down page section appears.
Begin by typing a name for the page in the Page Name field, using up to 80 alphanumeric characters, but no spaces.
Under Column 1, select a sort priority and a table column. This column will appear in the leftmost column of the page. For example, to create a page showing the destination ports that are targeted, and to sort the page by count, select 2 from the Sort Priority drop-down list and DST Port/ICMP Code from the Field drop-down list.
Continue selecting fields to include and setting their sort priority until all the fields to appear on the page have been specified. You can specify up to five fields per page.

Note If you selected Vulnerabilities as the Table Type in step 5, then add IP Address as a table column, the IP Address column does not appear when you are viewing vulnerabilities using your custom workflow, unless you use the search feature to constrain the workflow to view a specific IP address or block of addresses. For more information on searching for vulnerabilities, see Searching for Vulnerabilities.
Step 7 Optionally, click Add Table View to add a table view page to the workflow.

Note You must add at least one drill-down page or a table view of events to a custom workflow.
The new workflow is saved and added to the list of custom workflows.
Creating Custom Connection Data Workflows
Custom workflows based on connection data are like other custom workflows, except you can include connection data graph pages as well as drill-down pages and table view pages. You can include as many of each type of page in the workflow as you want, in any order. Each connection data graph page contains a single graph, which can be a line graph, bar graph, or pie chart. On line and bar graphs, you may include more than one dataset. For more information on connection data, including connection summaries, connection graphs, and datasets, see Understanding Connection and Security Intelligence Data.

Tip Instead of creating a new custom workflow, you can export a custom workflow from another appliance and then import it onto your appliance. You can then edit the imported workflow to suit your needs. For more information, see Importing and Exporting Configurations.
To create a custom workflow based on connection data:
Step 1 Select Analysis > Custom > Custom Workflow .
Step 2 Click Create Custom Workflow .
The Edit Custom Workflow page appears.
Step 3 Type a name for the workflow in the Name field.
You can use up to 60 alphanumeric characters and spaces.
Step 4 Optionally, type a description for the workflow in the Description field.
You can use up to 80 alphanumeric characters and spaces.
Step 5 From the Table drop-down list, select Connection Events .
Step 6 Optionally, add one or more drill-down pages to the workflow:
In either case, a drill-down page section appears.
Begin by typing a name for the page in the Page Name field using up to 80 alphanumeric characters, but no spaces.
Under Column 1 , select a sort priority and a table column. This column will appear in the leftmost column of the page.
Continue selecting fields to include and setting their sort priority until all the fields to appear on the page have been specified. You can specify up to five fields per page.
For example, to create a page showing the amount of traffic transmitted over your monitored network and to sort the page by the responders that transmitted the most traffic, select 1 from the Sort Priority drop-down list and Responder Bytes from the Field drop-down list.
Step 7 Optionally, click Add Graph to add one or more graph pages to the workflow.
Begin by typing a name for the page in the Graph Name field using up to 80 alphanumeric characters, but no spaces.
Then, select the type of graph you want to include on the page: line graph, bar graph, or pie chart.
Then, specify what kind of data you want to graph by selecting the x- and y-axes of the graph. On a pie chart, the x-axis represents the independent variable and the y-axis represents the dependent variable.
Finally, select the datasets you want to include on the graph. Note that pie charts can only include one data set.
Step 8 Optionally, add a table view of connection data by clicking Add Table View .
The new workflow is saved and added to the list of custom workflows.
Viewing Custom Workflows
The method you use to view a workflow depends on whether the workflow is based on one of the predefined event tables or on a custom table.
If your custom workflow is based on a predefined event table, access it in the same way that you would access a workflow that ships with the appliance. For example, to access a custom workflow based on the Hosts table, select Analysis Hosts . If, on the other hand, your custom workflow is based on a custom table, you must access it from the Custom Tables page.

Tip You can set a custom workflow as the default workflow for any event type; see Configuring Event View Settings.
Viewing Custom Workflows for Predefined Tables
Use the following procedure to view a custom workflow that is not based on a custom table. Keep in mind that workflow access depends on your platform and user role, as described in Selecting Workflows.
To view a custom workflow based on a predefined table:
Access: Admin/Any Security Analyst
Step 1 Select the appropriate menu path and option for the table on which you based your custom workflow, as described in the Features Using Workflows table.
The first page of the default workflow for that table appears. To use a different workflow, including a custom workflow, click (switch workflow) beside the current workflow title. For information on specifying a different default workflow, see Configuring Event View Settings. If no events appear and the workflow can be constrained by time, you may need to adjust the time range; see Setting Event Time Constraints.
Viewing Custom Workflows for Custom Tables
Use the following procedure to view a custom workflow that is based on a custom table.
To view a custom workflow based on a custom table:
Access: Admin/Any Security Analyst
Step 1 Select Analysis > Custom > Custom Tables .
The Custom Tables page appears, listing the available custom tables.
Step 2 Click the view icon next to the custom table you want to view, or click the name of the custom table.
The first page of the default workflow for that table appears. To use a different workflow, including a custom workflow, click (switch workflow) beside the current workflow title. For information on specifying a different default workflow, see Configuring Event View Settings. If no events appear and the workflow can be constrained by time, you may need to adjust the time range; see Setting Event Time Constraints.
Editing Custom Workflows
If your event evaluation process changes, you can edit custom workflows to meet your new needs. Note that you cannot edit any of the predefined workflows.
Access: Admin/Any Security Analyst
Step 1 Select Analysis > Custom > Custom Workflows .
The Custom Workflows page appears, listing the existing custom workflows.
Step 2 Click the edit icon ( ) next to the name of the workflow that you want to edit.
) next to the name of the workflow that you want to edit.
The Edit Workflow page appears.
Step 3 Make any changes that you want to the workflow and click Save .
The changes you made to the workflow are saved.
Deleting Custom Workflows
The following procedure explains how to delete a custom workflow that you no longer need.
Access: Admin/Any Security Analyst
Step 1 Select Analysis > Custom > Custom Workflows .
The Custom Workflows page appears, listing the available custom workflows.
Step 2 Click the delete icon ( ) next to the name of the workflow that you want to delete.
) next to the name of the workflow that you want to delete.

 (clean)
(clean) (malware)
(malware) (custom detection)
(custom detection) (unknown)
(unknown) (unavailable)
(unavailable)
 (potentially compromised)
(potentially compromised) (blacklisted)
(blacklisted) (blacklisted, set to monitor)
(blacklisted, set to monitor) (Low threat score)
(Low threat score) (Medium threat score)
(Medium threat score) (High threat score)
(High threat score) (Very High threat score)
(Very High threat score)

 ) to display the active constraints and disabled columns list or the collapse arrow (
) to display the active constraints and disabled columns list or the collapse arrow (
 ) indicates which column the data is sorted by, and whether the sort is ascending (upward-pointing icon) or descending (downward-pointing icon).
) indicates which column the data is sorted by, and whether the sort is ascending (upward-pointing icon) or descending (downward-pointing icon). ) to expand the search constraints, then click the column name under Disabled Columns.
) to expand the search constraints, then click the column name under Disabled Columns.  Feedback
Feedback