The ISE/ISE-PIC Identity Source
You can integrate your Cisco Identity Services Engine (ISE) or ISE Passive Identity Connector (ISE-PIC) deployment with the system to use ISE/ISE-PIC for passive authentication.
ISE/ISE-PIC is an authoritative identity source, and provides user awareness data for users who authenticate using Active Directory (AD), LDAP, RADIUS, or RSA. Additionally, you can perform user control on Active Directory users. ISE/ISE-PIC does not report failed login attempts or the activity of ISE Guest Services users.
In addition to user awareness and control, if you use ISE ISE to define and use security group tags (SGT) for classifying traffic in a Cisco TrustSec network, you can write access control rules that use SGT as both source and destination matching criteria. This enables you to block or allow access based on security group membership rather than IP addresses or network objects. For more information, see Configure Dynamic Attributes Conditions. Also see ISE/ISE-PIC Guidelines and Limitations.
 Note |
The system does not parse IEEE 802.1x machine authentication but it does parse 802.1x user authentication. If you are using 802.1x with ISE, you must include user authentication. 802.1x machine authentication will not provide a user identity to the FMC that can be used in policy. |
For more information on Cisco ISE/ISE-PIC, see the Cisco Identity Services Engine Passive Identity Connector Administrator Guide or the Cisco Identity Services Engine Administrator Guide.
 Note |
We strongly recommend you use the latest version of ISE/ISE-PIC to get the latest feature set and the most number of issue fixes. |
Source and Destination Security Group Tag (SGT) Matching
If you use ISE to define and use security group tags (SGT) for classifying traffic in a Cisco TrustSec network, you can write access control rules that use SGT as both source and destination matching criteria. This enables you to block or allow access based on security group membership rather than IP addresses or network objects. For more information, see Configure Dynamic Attributes Conditions.
Matching on SGT tags provides the following benefits:
-
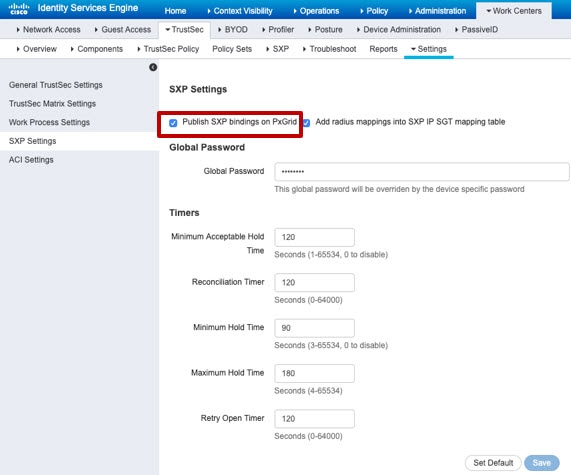
The FMC can subscribe to Security Group Tag eXchange Protocol (SXP) mappings from ISE.
ISE uses SXP to propagate the IP-to-SGT mapping database to managed devices. When you configure FMC to use an ISE server, you enable the option to listen to the SXP topic from ISE. This causes the FMC to learn about the security group tags and mappings directly from ISE. The FMC then publishes SGTs and mappings to managed devices.
The SXP Topic receives security group tags based on static and dynamic mappings learned through the SXP protocol between ISE and other SXP compliant devices (like switches).
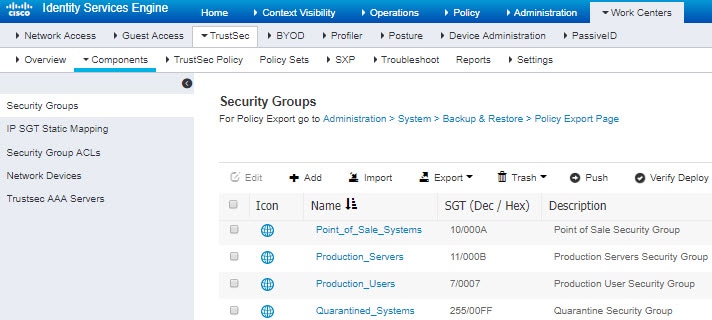
You can create security group tags in ISE and assign host or network IP addresses to each tag. You can also assign SGTs to user accounts, and the SGT is assigned to the user's traffic. If the switches and routers in the network are configured to do so, these tags then get assigned to packets as they enter the network controlled by ISE, the Cisco TrustSec cloud.
SXP is not supported by ISE-PIC.
-
The FMC and managed devices can learn about SGT mappings without deploying additional policy. (In other words, you can view connection events for SGT mappings without deploying an access control policy.)
-
Supports Cisco TrustSec, which enables you to segment your network to protect critical business assets.
-
When a managed device evaluates SGT as a traffic matching criteria for an access control rule, it uses the following priority:
-
The source SGT tag defined in the packet, if any.
For the SGT tag to be in the packet, the switches and routers in the network must be configured to add them. See the ISE documentation for information on how to implement this method.
For the SGT tag to be in the packet, the switches and routers in the network must be configured to add them. See the ISE documentation for information on how to implement this method.
-
The SGT assigned to the user session, as downloaded from the ISE session directory. The SGT can be matched to source or destination.
-
The SGT-to-IP address mapping downloaded using SXP. If the IP address is in the range for an SGT, then the traffic matches the access control rule that uses the SGT. The SGT can be matched to source or destination.
-
Examples:
-
In ISE, create an SGT tag named Guest Users and associate it with the 192.0.2.0/24 network.
For example, you could use Guest Users as a source SGT condition in your access control rule and restrict access to certain URLs, web site categories, or networks from anyone who accesses your network.
-
In ISE, create an SGT tag named Restricted Networks and associate it with the 198.51.100.0/8 network.
For example, you could use Restricted Networks as a destination SGT rule condition and block access from Guest Users and other networks that have users who are not authorized to access the network.


 )
) )
) Feedback
Feedback