Basic Interface Configuration (ASA 5505)
This chapter includes tasks for starting your interface configuration for the ASA 5505, including creating VLAN interfaces and assigning them to switch ports.
Information About ASA 5505 Interfaces
This section describes the ports and interfaces of the ASA 5505 and includes the following topics:
- Understanding ASA 5505 Ports and Interfaces
- Maximum Active VLAN Interfaces for Your License
- VLAN MAC Addresses
- Power over Ethernet
- Monitoring Traffic Using SPAN
- Auto-MDI/MDIX Feature
Understanding ASA 5505 Ports and Interfaces
The ASA 5505 supports a built-in switch. There are two kinds of ports and interfaces that you need to configure:
- Physical switch ports—The ASA has 8 Fast Ethernet switch ports that forward traffic at Layer 2, using the switching function in hardware. Two of these ports are PoE ports. See Power over Ethernet for more information. You can connect these interfaces directly to user equipment such as PCs, IP phones, or a DSL modem. Or you can connect to another switch.
- Logical VLAN interfaces—In routed mode, these interfaces forward traffic between VLAN networks at Layer 3, using the configured security policy to apply firewall and VPN services. In transparent mode, these interfaces forward traffic between the VLANs on the same network at Layer 2, using the configured security policy to apply firewall services. See Maximum Active VLAN Interfaces for Your License for more information about the maximum VLAN interfaces. VLAN interfaces let you divide your equipment into separate VLANs, for example, home, business, and Internet VLANs.
To segregate the switch ports into separate VLANs, you assign each switch port to a VLAN interface. Switch ports on the same VLAN can communicate with each other using hardware switching. But when a switch port on VLAN 1 wants to communicate with a switch port on VLAN 2, then the ASA applies the security policy to the traffic and routes or bridges between the two VLANs.
Maximum Active VLAN Interfaces for Your License
In routed mode, you can configure the following VLANs depending on your license:
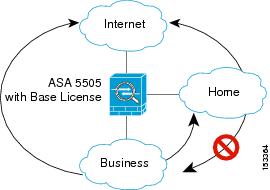
- Base license—3 active VLANs. The third VLAN can only be configured to initiate traffic to one other VLAN. See Figure 13-1 for more information.
- Security Plus license—20 active VLANs.
In transparent firewall mode, you can configure the following VLANs depending on your license:
- Base license—2 active VLANs in 1 bridge group.
- Security Plus license—3 active VLANs: 2 active VLANs in 1 bridge group, and 1 active VLAN for the failover link.

Note![]() An active VLAN is a VLAN with a nameif command configured.
An active VLAN is a VLAN with a nameif command configured.
With the Base license in routed mode, the third VLAN can only be configured to initiate traffic to one other VLAN. See Figure 13-1 for an example network where the Home VLAN can communicate with the Internet, but cannot initiate contact with Business.
Figure 13-1 ASA 5505 with Base License
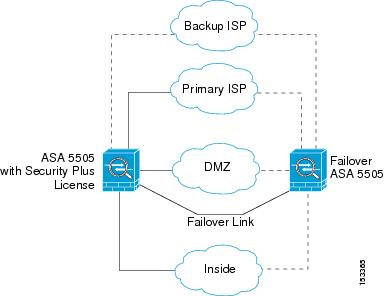
With the Security Plus license, you can configure 20 VLAN interfaces in routed mode, including a VLAN interface for failover and a VLAN interface as a backup link to your ISP. You can configure the backup interface to not pass through traffic unless the route through the primary interface fails. You can configure trunk ports to accommodate multiple VLANs per port.

Note![]() The ASA 5505 supports Active/Standby failover, but not Stateful Failover.
The ASA 5505 supports Active/Standby failover, but not Stateful Failover.
See Figure 13-2 for an example network.
Figure 13-2 ASA 5505 with Security Plus License
VLAN MAC Addresses
- Routed firewall mode—All VLAN interfaces share a MAC address. Ensure that any connected switches can support this scenario. If the connected switches require unique MAC addresses, you can manually assign MAC addresses. See Configuring the MAC Address, MTU, and TCP MSS.
- Transparent firewall mode—Each VLAN has a unique MAC address. You can override the generated MAC addresses if desired by manually assigning MAC addresses. See Configuring the MAC Address, MTU, and TCP MSS.
Power over Ethernet
Ethernet 0/6 and Ethernet 0/7 support PoE for devices such as IP phones or wireless access points. If you install a non-PoE device or do not connect to these switch ports, the ASA does not supply power to the switch ports.
If you shut down the switch port, you disable power to the device. Power is restored when you enable the portd. See Configuring and Enabling Switch Ports as Access Ports for more information about shutting down a switch port.
Monitoring Traffic Using SPAN
If you want to monitor traffic that enters or exits one or more switch ports, you can enable SPAN, also known as switch port monitoring. The port for which you enable SPAN (called the destination port) receives a copy of every packet transmitted or received on a specified source port. The SPAN feature lets you attach a sniffer to the destination port so you can monitor all traffic; without SPAN, you would have to attach a sniffer to every port you want to monitor. You can only enable SPAN for one destination port.
You can only enable SPAN monitoring using the Command Line Interface tool by entering the switchport monitor command. See the switchport monitor command in the command reference for more information.
Auto-MDI/MDIX Feature
All ASA 5505 interfaces include the Auto-MDI/MDIX feature. Auto-MDI/MDIX eliminates the need for crossover cabling by performing an internal crossover when a straight cable is detected during the auto-negotiation phase. You cannot disable Auto-MDI/MDIX.
Licensing Requirements for ASA 5505 Interfaces
Guidelines and Limitations
The ASA 5505 does not support multiple context mode.
- In transparent mode, you can configure up to eight bridge groups. Note that you must use at least one bridge group; data interfaces must belong to a bridge group.
- Each bridge group can include up to four VLAN interfaces, up to the license limit.
Active/Standby failover is only supported with the Security Plus license. Active/Active failover is not supported.
Default Settings
This section lists default settings for interfaces if you do not have a factory default configuration. For information about the factory default configurations, see Factory Default Configurations.
Starting ASA 5505 Interface Configuration
This section includes the following topics:
- Task Flow for Starting Interface Configuration
- Configuring VLAN Interfaces
- Configuring and Enabling Switch Ports as Access Ports
- Configuring and Enabling Switch Ports as Trunk Ports
Task Flow for Starting Interface Configuration
To configure interfaces in single mode, perform the following steps:
Step 1![]() Configure VLAN interfaces. See Configuring VLAN Interfaces.
Configure VLAN interfaces. See Configuring VLAN Interfaces.
Step 2![]() Configure and enable switch ports as access ports. See Configuring and Enabling Switch Ports as Access Ports.
Configure and enable switch ports as access ports. See Configuring and Enabling Switch Ports as Access Ports.
Step 3![]() (Optional for Security Plus licenses) Configure and enable switch ports as trunk ports. See Configuring and Enabling Switch Ports as Trunk Ports.
(Optional for Security Plus licenses) Configure and enable switch ports as trunk ports. See Configuring and Enabling Switch Ports as Trunk Ports.
Step 4![]() Complete the interface configuration according to “Routed Mode Interfaces,” or Chapter16, “Transparent Mode Interfaces”
Complete the interface configuration according to “Routed Mode Interfaces,” or Chapter16, “Transparent Mode Interfaces”
Configuring VLAN Interfaces
This section describes how to configure VLAN interfaces. For more information about ASA 5505 interfaces, see Information About ASA 5505 Interfaces.
Guidelines
We suggest that you finalize your interface configuration before you enable Easy VPN. If you enabled Easy VPN, you cannot add or delete VLAN interfaces, nor can you edit the security level or interface name.
Detailed Steps
Step 1![]() Choose the Configuration > Device Setup > Interfaces pane.
Choose the Configuration > Device Setup > Interfaces pane.
Step 2![]() On the Interfaces tab, click Add.
On the Interfaces tab, click Add.
The Add Interface dialog box appears with the General tab selected.

Step 3![]() In the Available Switch Ports pane, choose a switch port, and click Add.
In the Available Switch Ports pane, choose a switch port, and click Add.
You see the following message:
“switchport is associated with name interface. Adding it to this interface, will remove it from name interface. Do you want to continue?”
Click OK to add the switch port.
You will always see this message when adding a switch port to an interface; switch ports are assigned to the VLAN 1 interface by default even when you do not have any configuration.
Repeat for any other switch ports that you want to carry this VLAN.

Note![]() Removing a switch port from an interface essentially just reassigns that switch port to VLAN 1, because the default VLAN interface for switch ports is VLAN 1.
Removing a switch port from an interface essentially just reassigns that switch port to VLAN 1, because the default VLAN interface for switch ports is VLAN 1.
Step 4![]() Click the Advanced tab.
Click the Advanced tab.

Note![]() You receive an error message about setting the IP address. You can either set the IP address and other parameters now, or you can finish configuring the VLAN and switch ports by clicking Yes, and later set the IP address and other parameters according to “Routed Mode Interfaces,” or Chapter16, “Transparent Mode Interfaces”
You receive an error message about setting the IP address. You can either set the IP address and other parameters now, or you can finish configuring the VLAN and switch ports by clicking Yes, and later set the IP address and other parameters according to “Routed Mode Interfaces,” or Chapter16, “Transparent Mode Interfaces”
Step 5![]() In the VLAN ID field, enter the VLAN ID for this interface, between 1 and 4090.
In the VLAN ID field, enter the VLAN ID for this interface, between 1 and 4090.
If you do not want to assign the VLAN ID, ASDM assigns one for you randomly.
Step 6![]() (Optional for the Base license) To allow this interface to be the third VLAN by limiting it from initiating contact to one other VLAN, in the Block Traffic From this Interface to drop-down list, choose the VLAN to which this VLAN interface cannot initiate traffic.
(Optional for the Base license) To allow this interface to be the third VLAN by limiting it from initiating contact to one other VLAN, in the Block Traffic From this Interface to drop-down list, choose the VLAN to which this VLAN interface cannot initiate traffic.
With the Base license, you can only configure a third VLAN if you use this command to limit it.
For example, you have one VLAN assigned to the outside for Internet access, one VLAN assigned to an inside business network, and a third VLAN assigned to your home network. The home network does not need to access the business network, so you can use this option on the home VLAN; the business network can access the home network, but the home network cannot access the business network.
If you already have two VLAN interfaces configured with a name, be sure to configure this setting before setting the name on the third interface; the ASA does not allow three fully functioning VLAN interfaces with the Base license on the ASA 5505.

Note![]() If you upgrade to the Security Plus license, you can remove this option and achieve full functionality for this interface. If you leave this option enabled, this interface continues to be limited even after upgrading.
If you upgrade to the Security Plus license, you can remove this option and achieve full functionality for this interface. If you leave this option enabled, this interface continues to be limited even after upgrading.
To configure the MAC address and MTU, see Configuring the MAC Address, MTU, and TCP MSS.
What to Do Next
Configure the switch ports. See Configuring and Enabling Switch Ports as Access Ports and the Configuring and Enabling Switch Ports as Trunk Ports.
Configuring and Enabling Switch Ports as Access Ports
By default (with no configuration), all switch ports are shut down, and assigned to VLAN 1. To assign a switch port to a single VLAN, configure it as an access port. To create a trunk port to carry multiple VLANs, see Configuring and Enabling Switch Ports as Trunk Ports. If you have a factory default configuration, see ASA 5505 Default Configuration to check if you want to change the default interface settings according to this procedure.
For more information about ASA 5505 interfaces, see Information About ASA 5505 Interfaces.

Detailed Steps
Step 1![]() Choose the Configuration > Device Setup > Interfaces pane.
Choose the Configuration > Device Setup > Interfaces pane.
Step 2![]() Click the Switch Ports tab.
Click the Switch Ports tab.
Step 3![]() Click the switch port you want to edit.
Click the switch port you want to edit.
The Edit Switch Port dialog box appears.

Step 4![]() To enable the switch port, check the Enable SwitchPort check box.
To enable the switch port, check the Enable SwitchPort check box.
Step 5![]() In the Mode and VLAN IDs area, click the Access radio button.
In the Mode and VLAN IDs area, click the Access radio button.
Step 6![]() In the VLAN ID field, enter the VLAN ID associated with this switch port. The VLAN ID can be between 1 and 4090.
In the VLAN ID field, enter the VLAN ID associated with this switch port. The VLAN ID can be between 1 and 4090.
By default, the VLAN ID is derived from the VLAN interface configuration you completed in Configuring VLAN Interfaces (on the Configuration > Device Setup > Interfaces > Interfaces > Add/Edit Interface dialog box). You can change the VLAN assignment in this dialog box. Be sure to apply the change to update the VLAN configuration with the new information. If you want to specify a VLAN that has not yet been added, we suggest you add the VLAN according to the Configuring VLAN Interfaces rather than specifying it in this dialog box; in either case, you need to add the VLAN according to the Configuring VLAN Interfaces and assign the switch port to it.
Step 7![]() (Optional) To prevent the switch port from communicating with other protected switch ports on the same VLAN, check the Isolated check box.
(Optional) To prevent the switch port from communicating with other protected switch ports on the same VLAN, check the Isolated check box.
This option prevents the switch port from communicating with other protected switch ports on the same VLAN. You might want to prevent switch ports from communicating with each other if the devices on those switch ports are primarily accessed from other VLANs, you do not need to allow intra-VLAN access, and you want to isolate the devices from each other in case of infection or other security breach. For example, if you have a DMZ that hosts three web servers, you can isolate the web servers from each other if you apply the Protected option to each switch port. The inside and outside networks can both communicate with all three web servers, and vice versa, but the web servers cannot communicate with each other.
Step 8![]() (Optional) From the Duplex drop-down list, choose Full, Half, or Auto.
(Optional) From the Duplex drop-down list, choose Full, Half, or Auto.
The Auto setting is the default. If you set the duplex to anything other than Auto on PoE ports Ethernet 0/6 or 0/7, then Cisco IP phones and Cisco wireless access points that do not support IEEE 802.3af will not be detected and supplied with power.
Step 9![]() (Optional) From the Speed drop-down list, choose 10, 100, or Auto.
(Optional) From the Speed drop-down list, choose 10, 100, or Auto.
The Auto setting is the default. If you set the speed to anything other than Auto on PoE ports Ethernet 0/6 or 0/7, then Cisco IP phones and Cisco wireless access points that do not support IEEE 802.3af will not be detected and supplied with power.
What to Do Next
- If you want to configure a switch port as a trunk port, see Configuring and Enabling Switch Ports as Trunk Ports.
- To complete the interface configuration, see “Routed Mode Interfaces,” or Chapter16, “Transparent Mode Interfaces”
Configuring and Enabling Switch Ports as Trunk Ports
This procedure describes how to create a trunk port that can carry multiple VLANs using 802.1Q tagging. Trunk mode is available only with the Security Plus license.
To create an access port, where an interface is assigned to only one VLAN, see Configuring and Enabling Switch Ports as Access Ports.
Guidelines
This switch port cannot pass traffic until you assign at least one VLAN to it, native or non-native.
Detailed Steps
Step 1![]() Choose the Configuration > Device Setup > Interfaces pane.
Choose the Configuration > Device Setup > Interfaces pane.
Step 2![]() Click the Switch Ports tab.
Click the Switch Ports tab.
Step 3![]() Click the switch port you want to edit.
Click the switch port you want to edit.
The Edit Switch Port dialog box appears.

Step 4![]() To enable the switch port, check the Enable SwitchPort check box.
To enable the switch port, check the Enable SwitchPort check box.
Step 5![]() In the Mode and VLAN IDs area, click the Trunk radio button.
In the Mode and VLAN IDs area, click the Trunk radio button.
Step 6![]() In the VLAN IDs field, enter the VLAN IDs associated with this switch port, separated by commas. The VLAN ID can be between 1 and 4090.
In the VLAN IDs field, enter the VLAN IDs associated with this switch port, separated by commas. The VLAN ID can be between 1 and 4090.
You can include the native VLAN in this field, but it is not required; the native VLAN is passed whether it is included in this field or not.
This switch port cannot pass traffic until you assign at least one VLAN to it, native or non-native.
If the VLANs are already in your configuration, after you apply the change, the Configuration > Device Setup > Interfaces > Interfaces tab shows this switch port added to each VLAN. If you want to specify a VLAN that has not yet been added, we suggest you add the VLAN according to the Configuring VLAN Interfaces rather than specifying it in this dialog box; in either case, you need to add the VLAN according to the Configuring VLAN Interfaces and assign the switch port to it.
Step 7![]() To configure the native VLAN, check the Configure Native VLAN check box, and enter the VLAN ID in the Native VLAN ID field. The VLAN ID can be between 1 and 4090.
To configure the native VLAN, check the Configure Native VLAN check box, and enter the VLAN ID in the Native VLAN ID field. The VLAN ID can be between 1 and 4090.
Packets on the native VLAN are not modified when sent over the trunk. For example, if a port has VLANs 2, 3 and 4 assigned to it, and VLAN 2 is the native VLAN, then packets on VLAN 2 that egress the port are not modified with an 802.1Q header. Frames which ingress (enter) this port and have no 802.1Q header are put into VLAN 2.
Each port can only have one native VLAN, but every port can have either the same or a different native VLAN.
Step 8![]() (Optional) To prevent the switch port from communicating with other protected switch ports on the same VLAN, check the Isolated check box.
(Optional) To prevent the switch port from communicating with other protected switch ports on the same VLAN, check the Isolated check box.
This option prevents the switch port from communicating with other protected switch ports on the same VLAN. You might want to prevent switch ports from communicating with each other if the devices on those switch ports are primarily accessed from other VLANs, you do not need to allow intra-VLAN access, and you want to isolate the devices from each other in case of infection or other security breach. For example, if you have a DMZ that hosts three web servers, you can isolate the web servers from each other if you apply the Protected option to each switch port. The inside and outside networks can both communicate with all three web servers, and vice versa, but the web servers cannot communicate with each other.
Step 9![]() (Optional) From the Duplex drop-down list, choose Full, Half, or Auto.
(Optional) From the Duplex drop-down list, choose Full, Half, or Auto.
The Auto setting is the default. If you set the duplex to anything other than Auto on PoE ports Ethernet 0/6 or 0/7, then Cisco IP phones and Cisco wireless access points that do not support IEEE 802.3af will not be detected and supplied with power.
Step 10![]() (Optional) From the Speed drop-down list, choose 10, 100, or Auto.
(Optional) From the Speed drop-down list, choose 10, 100, or Auto.
The Auto setting is the default. If you set the speed to anything other than Auto on PoE ports Ethernet 0/6 or 0/7, then Cisco IP phones and Cisco wireless access points that do not support IEEE 802.3af will not be detected and supplied with power.
Monitoring Interfaces
This section includes the following topics:
ARP Table
The Monitoring > Interfaces > ARP Table pane displays the ARP table, including static and dynamic entries. The ARP table includes entries that map a MAC address to an IP address for a given interface.
- Interface —Lists the interface name associated with the mapping.
- IP Address —Shows the IP address.
- MAC Address —Shows the MAC address.
- Proxy ARP—Displays Yes if proxy ARP is enabled on the interface. Displays No if proxy ARP is not enabled on the interface.
- Clear —Clears the dynamic ARP table entries. Static entries are not cleared.
- Refresh —Refreshes the table with current information from the ASA and updates Last Updated date and time.
- Last Updated — Display only . Shows the date and time the display was updated.
MAC Address Table
The Monitoring > Interfaces > MAC Address Table pane shows the static and dynamic MAC address entries. See MAC Address Table for more information about the MAC address table and adding static entries.
- Interface—Shows the interface name associated with the entry.
- MAC Address—Shows the MAC address.
- Type—Shows if the entry is static or dynamic.
- Age—Shows the age of the entry, in minutes. To set the timeout, see MAC Address Table.
- Refresh—Refreshes the table with current information from the ASA.
Interface Graphs
The Monitoring > Interfaces > Interface Graphs pane lets you view interface statistics in graph or table form. If an interface is shared among contexts, the ASA shows only statistics for the current context. The number of statistics shown for a subinterface is a subset of the number of statistics shown for a physical interface.
- Available Graphs for—Lists the types of statistics available for monitoring. You can choose up to four types of statistics to show in one graph window. You can open multiple graph windows at the same time.
–![]() Byte Counts—Shows the number of bytes input and output on the interface.
Byte Counts—Shows the number of bytes input and output on the interface.
–![]() Packet Counts—Shows the number of packets input and output on the interface.
Packet Counts—Shows the number of packets input and output on the interface.
–![]() Packet Rates—Shows the rate of packets input and output on the interface.
Packet Rates—Shows the rate of packets input and output on the interface.
–![]() Bit Rates—Shows the bit rate for the input and output of the interface.
Bit Rates—Shows the bit rate for the input and output of the interface.
–![]() Drop Packet Count—Shows the number of packets dropped on the interface.
Drop Packet Count—Shows the number of packets dropped on the interface.
These additional statistics display for physical interfaces:
–![]() Buffer Resources—Shows the following statistics:
Buffer Resources—Shows the following statistics:
Overruns—The number of times that the ASA was incapable of handing received data to a hardware buffer because the input rate exceeded the ASA capability to handle the data.
Underruns—The number of times that the transmitter ran faster than the ASA could handle.
No Buffer—The number of received packets discarded because there was no buffer space in the main system. Compare this with the ignored count. Broadcast storms on Ethernet networks are often responsible for no input buffer events.
–![]() Packet Errors—Shows the following statistics:
Packet Errors—Shows the following statistics:
CRC—The number of Cyclical Redundancy Check errors. When a station sends a frame, it appends a CRC to the end of the frame. This CRC is generated from an algorithm based on the data in the frame. If the frame is altered between the source and destination, the ASA notes that the CRC does not match. A high number of CRCs is usually the result of collisions or a station transmitting bad data.
Frame—The number of frame errors. Bad frames include packets with an incorrect length or bad frame checksums. This error is usually the result of collisions or a malfunctioning Ethernet device.
Input Errors—The number of total input errors, including the other types listed here. Other input-related errors can also cause the input error count to increase, and some datagrams might have more than one error; therefore, this sum might exceed the number of errors listed for the other types.
Runts—The number of packets that are discarded because they are smaller than the minimum packet size, which is 64 bytes. Runts are usually caused by collisions. They might also be caused by poor wiring and electrical interference.
Giants—The number of packets that are discarded because they exceed the maximum packet size. For example, any Ethernet packet that is greater than 1518 bytes is considered a giant.
Deferred—For FastEthernet interfaces only. The number of frames that were deferred before transmission due to activity on the link.
–![]() Miscellaneous—Shows statistics for received broadcasts.
Miscellaneous—Shows statistics for received broadcasts.
–![]() Collision Counts—For FastEthernet interfaces only. Shows the following statistics:
Collision Counts—For FastEthernet interfaces only. Shows the following statistics:
Output Errors—The number of frames not transmitted because the configured maximum number of collisions was exceeded. This counter should only increment during heavy network traffic.
Collisions—The number of messages retransmitted due to an Ethernet collision (single and multiple collisions). This usually occurs on an overextended LAN (Ethernet or transceiver cable too long, more than two repeaters between stations, or too many cascaded multiport transceivers). A packet that collides is counted only once by the output packets.
Late Collisions—The number of frames that were not transmitted because a collision occurred outside the normal collision window. A late collision is a collision that is detected late in the transmission of the packet. Normally, these should never happen. When two Ethernet hosts try to talk at once, they should collide early in the packet and both back off, or the second host should see that the first one is talking and wait. If you get a late collision, a device is jumping in and trying to send the packet on the Ethernet while the ASA is partly finished sending the packet. The ASA does not resend the packet, because it may have freed the buffers that held the first part of the packet. This is not a real problem because networking protocols are designed to cope with collisions by resending packets. However, late collisions indicate a problem exists in your network. Common problems are large repeated networks and Ethernet networks running beyond the specification.
–![]() Input Queue—Shows the number of packets in the input queue, the current and the maximum, including the following statistics:
Input Queue—Shows the number of packets in the input queue, the current and the maximum, including the following statistics:
Hardware Input Queue—The number of packets in the hardware queue.
Software Input Queue—The number of packets in the software queue.
–![]() Output Queue—Shows the number of packets in the output queue, the current and the maximum, including the following statistics:
Output Queue—Shows the number of packets in the output queue, the current and the maximum, including the following statistics:
Hardware Output Queue—The number of packets in the hardware queue.
Software Output Queue—The number of packets in the software queue.
- Add—Adds the selected statistic type to the selected graph window.
- Remove—Removes the selected statistic type from the selected graph window. This button name changes to Delete if the item you are removing was added from another panel, and is not being returned to the Available Graphs pane.
- Show Graphs—Shows the graph window name to which you want to add a statistic type. If you have a graph window already open, a new graph window is listed by default. If you want to add a statistic type to an already open graph, choose the open graph window name. The statistics already included on the graph are shown in the Selected Graphs pane, to which you can add additional types. Graph windows are named for ASDM followed by the interface IP address and the name “Graph”. Subsequent graphs are named “Graph (2)” and so on.
- Selected Graphs—Shows the statistic types you want to show in the selected graph window. You an include up to four types.
–![]() Show Graphs—Shows the graph window or updates the graph with additional statistic types if added.
Show Graphs—Shows the graph window or updates the graph with additional statistic types if added.
Graph/Table
The Mon itoring > Interfaces > Interface Graphs > Graph/Table window shows a graph for the selected statistics. The Graph window can show up to four graphs and tables at a time. By default, the graph or table displays the real-time statistics. If you enable History Metrics (see Enabling History Metrics), you can view statistics for past time periods.
- View—Sets the time period for the graph or table. To view any time period other than real-time, enable History Metrics (see Enabling History Metrics). The data is updated according to the specification of the following options:
–![]() Real-time, data every 10 sec
Real-time, data every 10 sec
–![]() Last 10 minutes, data every 10 sec
Last 10 minutes, data every 10 sec
–![]() Last 60 minutes, data every 1 min
Last 60 minutes, data every 1 min
–![]() Last 12 hours, data every 12 min
Last 12 hours, data every 12 min
–![]() Last 5 days, data every 2 hours
Last 5 days, data every 2 hours
- Export—Exports the graph in comma-separated value format. If there is more than one graph or table on the Graph window, the Export Graph Data dialog box appears. Choose one or more of the graphs and tables listed by checking the check box next to the name.
- Print—Prints the graph or table. If there is more than one graph or table on the Graph window, the Print Graph dialog box appears. Choose the graph or table you want to print from the Graph/Table Name list.
- Bookmark—Opens a browser window with a single link for all graphs and tables on the Graphs window, as well as individual links for each graph or table. You can then copy these URLs as bookmarks in your browser. ASDM does not have to be running when you open the URL for a graph; the browser launches ASDM and then displays the graph.
Where to Go Next
Complete the interface configuration according to “Routed Mode Interfaces,” or Chapter16, “Transparent Mode Interfaces”
Feature History for ASA 5505 Interfaces
Table 13-1 lists the release history for this feature.
 Feedback
Feedback