The default network analysis policy is tuned for typical network requirements and optimal performance. Usually, the default
network analysis policy suffices most network requirements and you might not need to customize the policy. However, when you
have a specific network requirement or when you are facing performance issues, the default network analysis policy can be
customized. Note that customising the network analysis policy is an advanced configuration that should be done only by advanced
users or Cisco support.
Network analysis policy configuration for Snort 3 is a data-driven model, which is based on JSON and JSON Schema. Schema is
based on the OpenAPI specification, and it helps you get a view of the supported inspectors, settings, settings type, and
valid values. The Snort 3 inspectors are plugins that process packets (similar to the Snort 2 preprocessor). Network analysis
policy configuration is available to download in the JSON format.
In Snort 3, the list of inspectors and settings are not in a one-to-one mapping with the Snort 2 list of preprocessors and
settings. Also, the number of inspectors and settings available in management center is a subset of the inspectors and settings that Snort 3 supports. See https://snort.org/snort3 for more information on Snort 3. See https://www.cisco.com/go/snort3-inspectors for more information on the inspectors available in management center.

Note
|
-
While upgrading the management center to the 7.0 release, the changes that were done in the Snort 2 version of the network analysis policy are not migrated to
Snort 3 after the upgrade.
-
Unlike the intrusion policy, there is no option to synchronize Snort 2 network analysis policy settings to Snort 3.
|
Default Inspector Updates
Lightweight Security Package (LSP) updates may contain new inspectors or modifications to integer ranges for existing inspector
configurations. Following the installation of an LSP, new inspectors and/or updated ranges will be available under Inspectors in the Snort 3 Version of your network analysis policy.
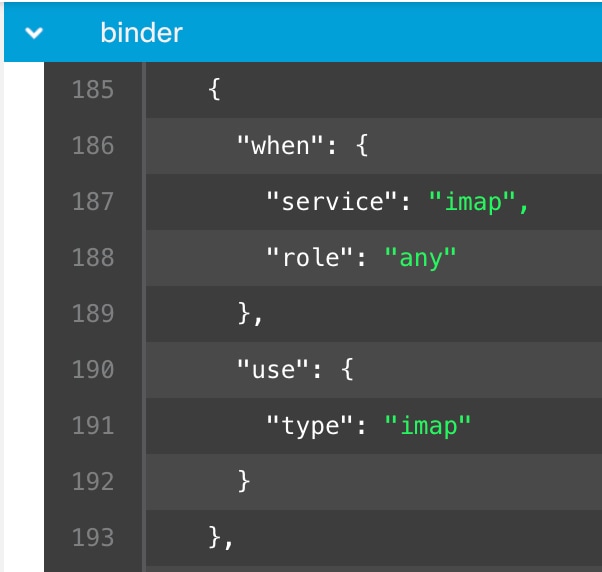
Binder Inspector
Binder inspector defines the flow when a particular inspector has to be accessed and taken into consideration. When the traffic
matches the conditions defined in the binder inspector, only then the values/configurations for that inspector come into effect.
For example:
For the imap inspector, the binder defines the following condition when it has to be accessed. That is when:
If these conditions are met, then use the type imap.
Singleton Inspectors
Singleton inspectors contain a single instance. These inspectors do not support adding more instances like multiton inspectors.
Settings of singleton inspector are applied to the entire traffic and not to a specific traffic segment.
For example:
{
"normalizer":{
"enabled":true,
"type":"singleton",
"data":{
"ip4":{
"df":true
}
}
}
}
Multiton Inspectors
Multiton inspectors contain multiple instances which you can configure as needed. These inspectors support configuring settings
based on specific conditions, such as network, port, and VLAN. One set of supported settings is called an instance. There
is a default instance, and you can also add additional instances based on specific conditions. If the traffic matches that
condition, the settings from that instance are applied. Otherwise, the settings from the default instance are applied. Also,
the name of the default instance is the same as the inspector's name.
For a multiton inspector, when you upload the overridden inspector configuration, you also need to include/define a matching
binder condition (conditions under when the inspector has to be accessed or used) for each instance in the JSON file, otherwise,
the upload will result in an error. You can also create new instances, but make sure that you include a binder condition for
every new instance that you create to avoid errors.
For example:
-
Multiton inspector where the default instance is modified.
{
"http_inspect":{
"enabled":true,
"type":"multiton",
"instances":[
{
"name":"http_inspect",
"data":{
"response_depth":5000
}
}
]
}
}
-
Multiton inspector where the default instance and default binder is modified.
{
"http_inspect":{
"enabled":true,
"type":"multiton",
"instances":[
{
"name":"http_inspect",
"data":{
"response_depth":5000
}
}
]
},
"binder":{
"type":"binder",
"enabled":true,
"rules":[
{
"use":{
"type":"http_inspect"
},
"when":{
"role":"any",
"ports":"8080",
"proto":"tcp",
"service":"http"
}
}
]
}
}
-
Multiton inspector where a custom instance and a custom binder is added.
{
"http_inspect":{
"enabled":true,
"type":"multiton",
"instances":[
{
"name":"http_inspect1",
"data":{
"response_depth":5000
}
}
]
},
"binder":{
"type":"binder",
"enabled":true,
"rules":[
{
"use":{
"type":"http_inspect",
"name":"http_inspect1"
},
"when":{
"role":"any",
"ports":"8080",
"proto":"tcp",
"service":"http"
}
}
]
}
}

 )
) )
) )
) )
)


 Feedback
Feedback