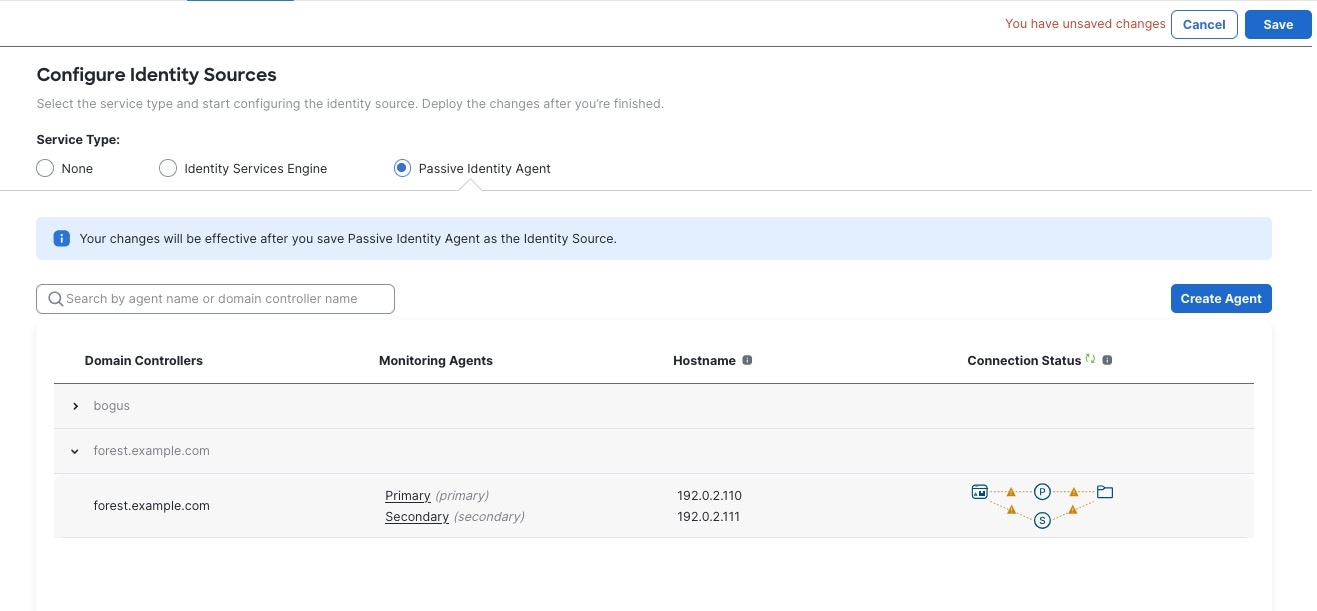
The Passive Identity Agent Identity Source
The passive identity agent identity source sends session data from Microsoft Active Directory (AD) to the Cloud-Delivered Firewall Management Center. All you need is a supported Microsoft AD setup as discussed in About Realms and Realm Sequences.
The passive identity agent version 1.0 sends IPv4 user sessions only but Version 1.1 sends IPv4 and IPv6 user sessions.
 Note |
You do not need to configure the Cisco Identity Services Engine (ISE) to use this identity source. |
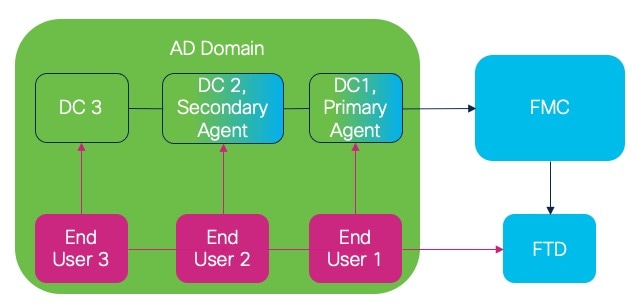
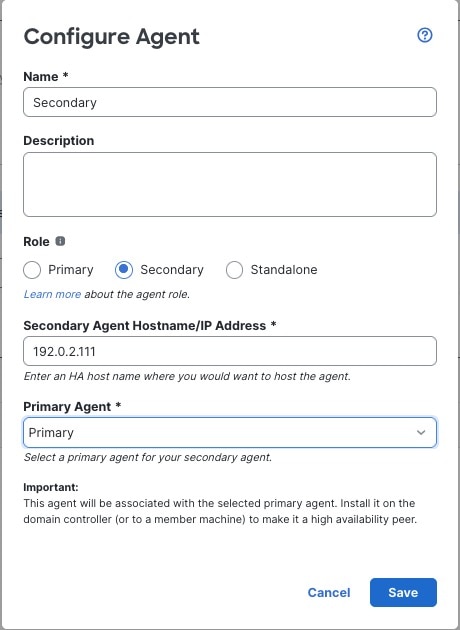
Passive identity agent roles
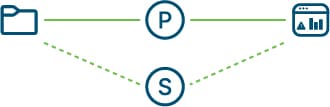
The passive identity agent supports the following roles:
-
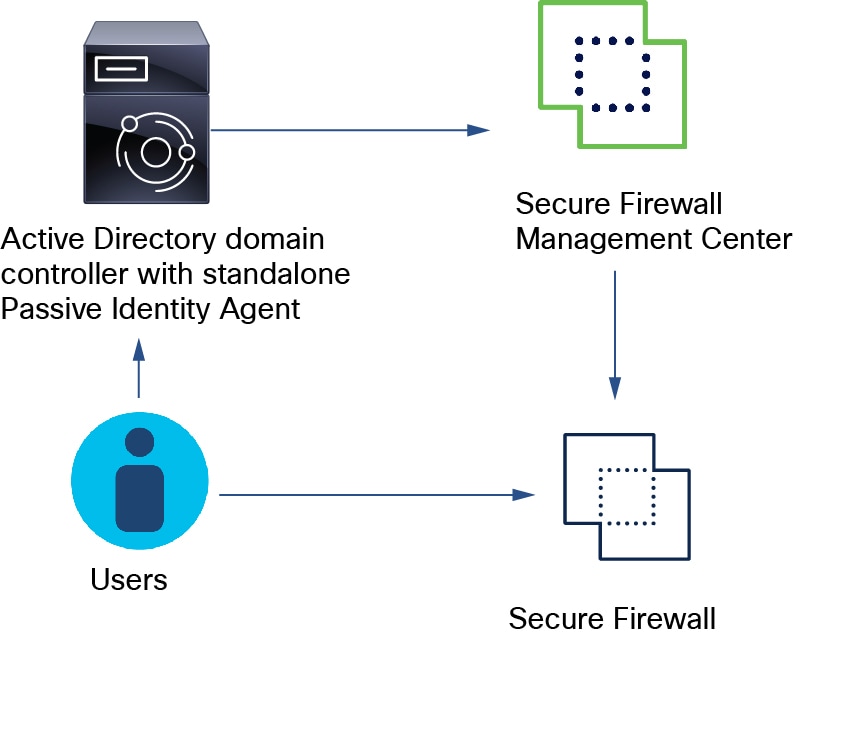
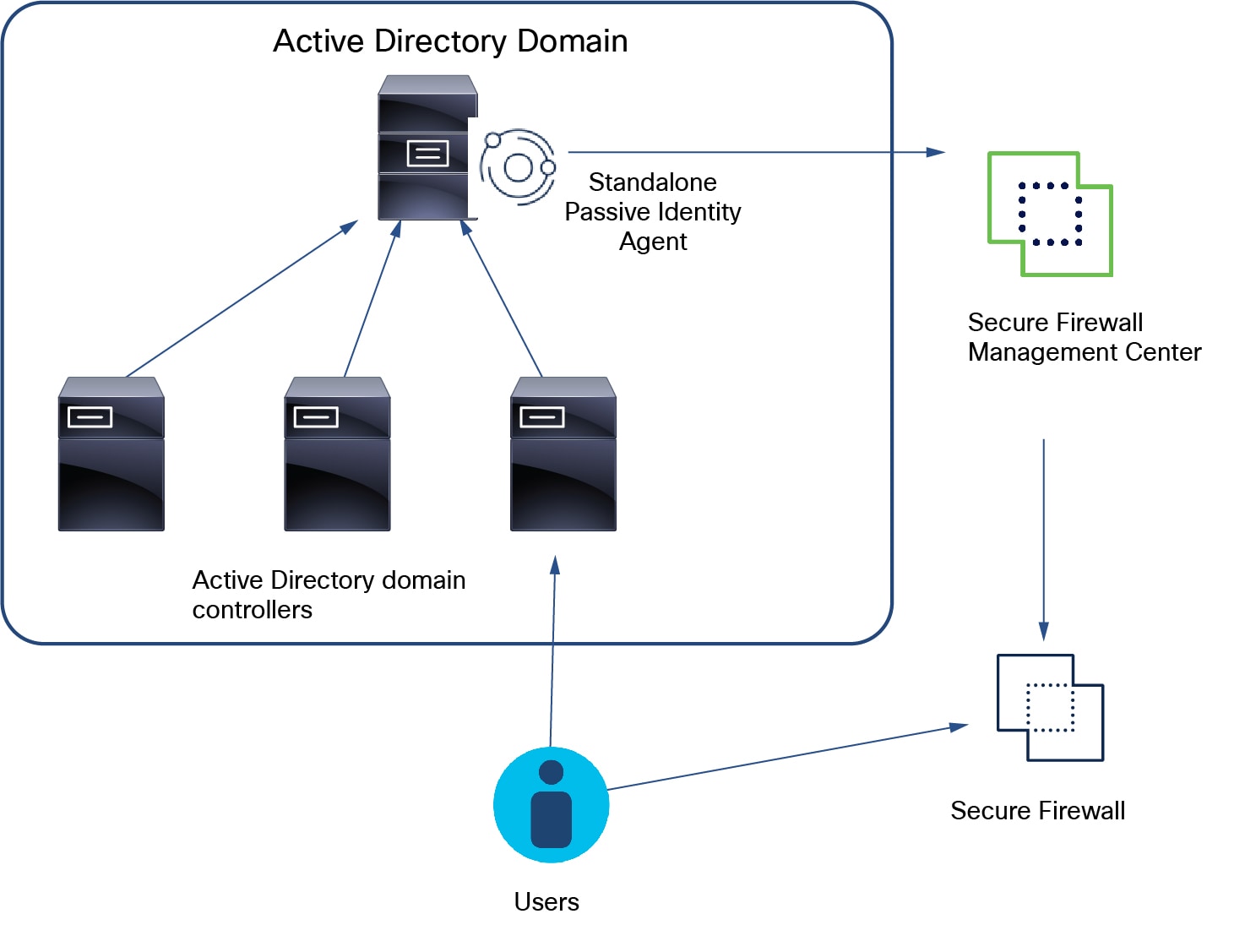
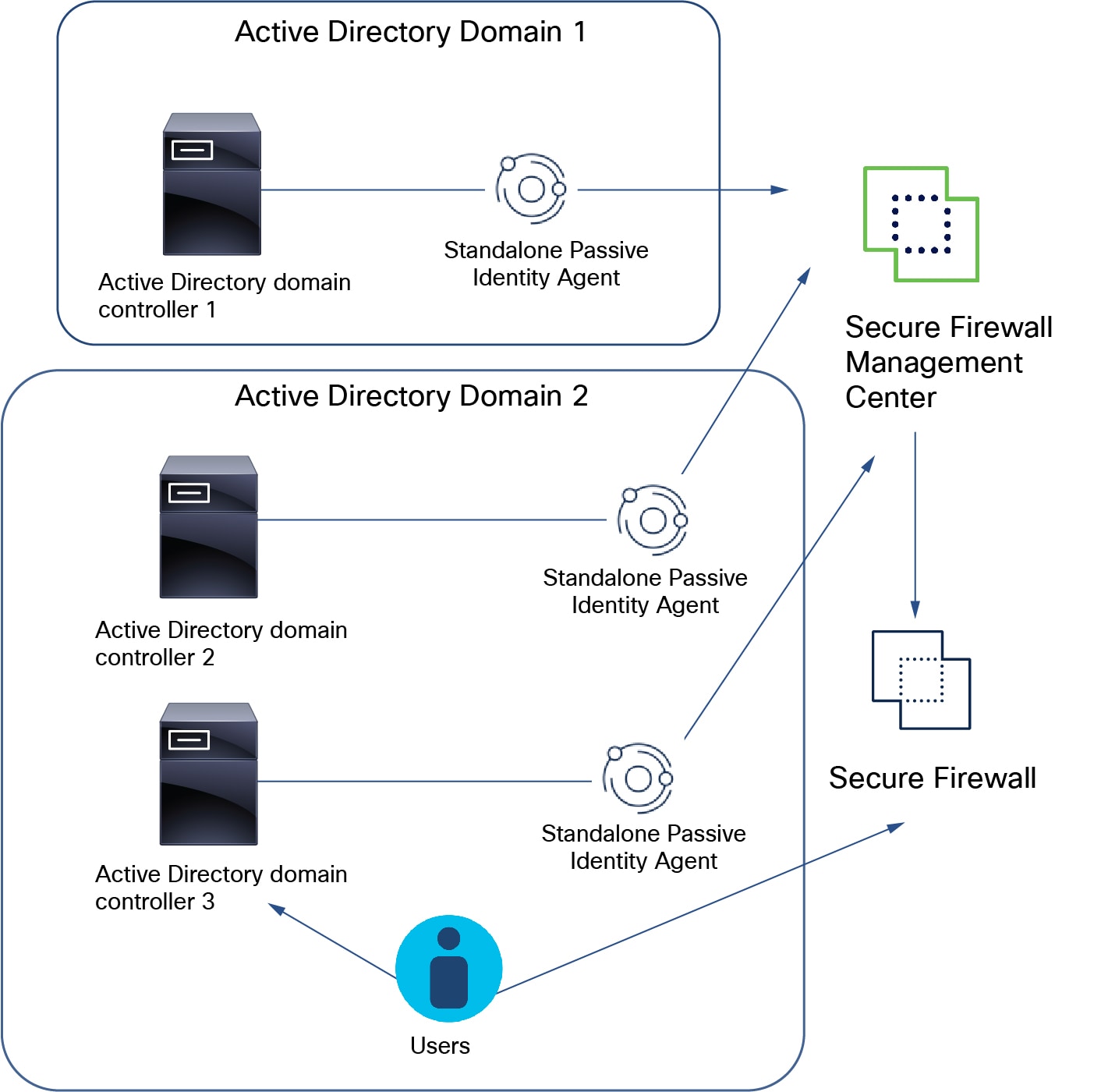
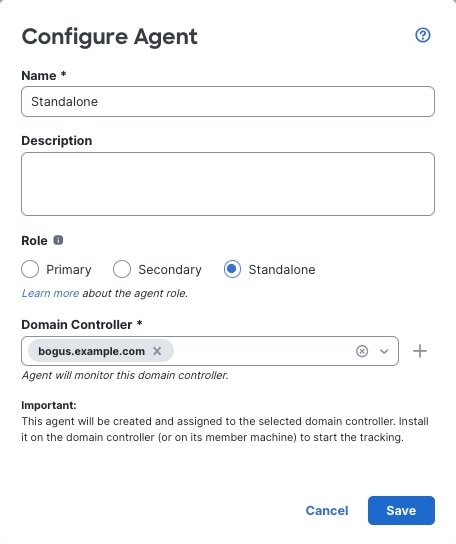
Standalone: A passive identity agent that is not part of a redundant pair. A standalone agent can read users and groups from multiple Active Directory servers and domain controllers, provided the software is installed on all of them.
-
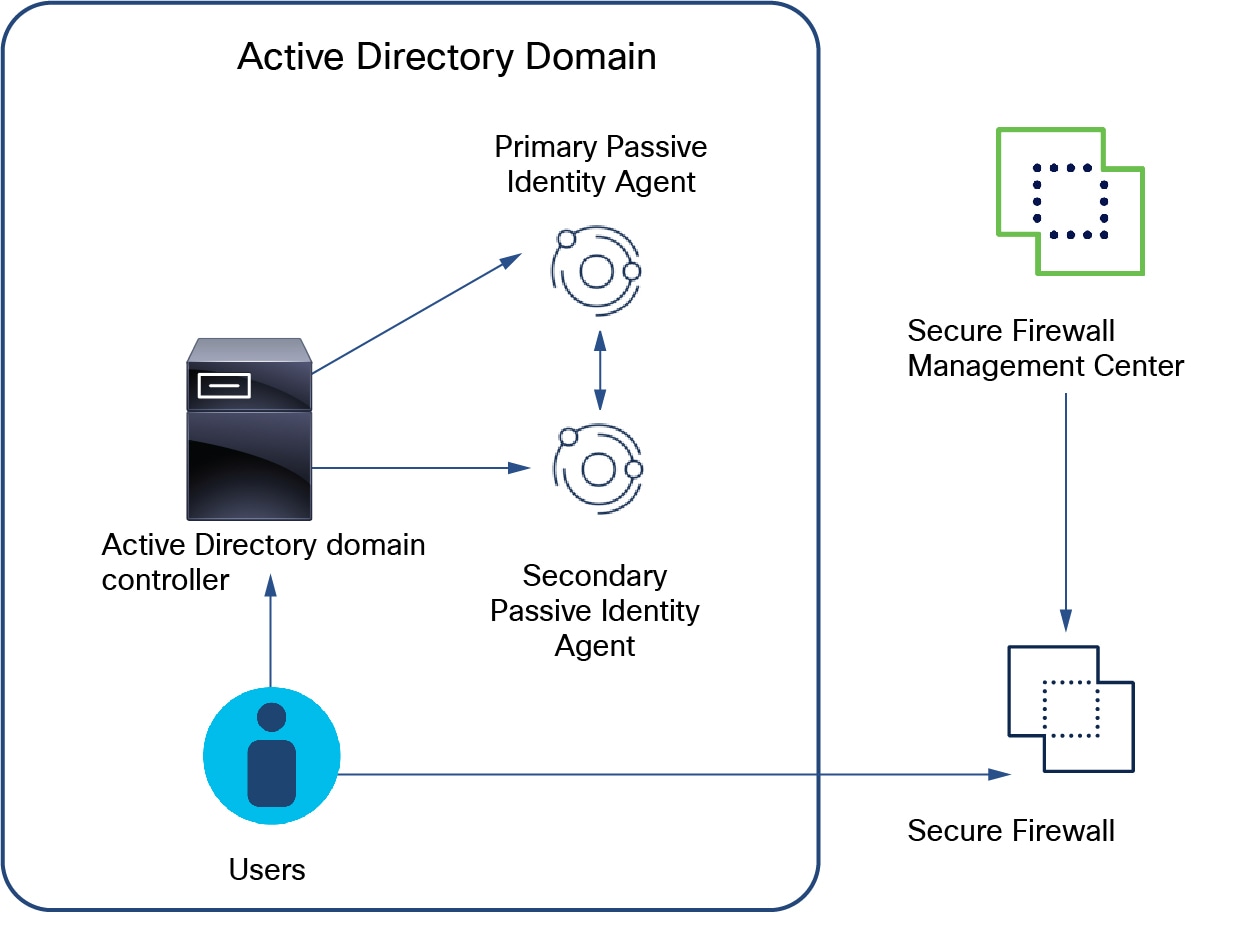
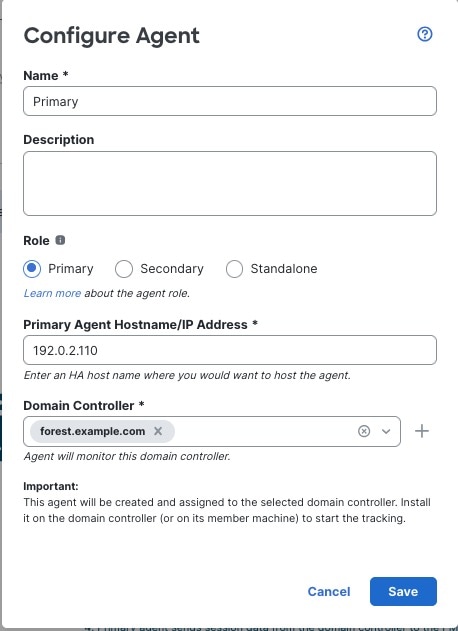
Primary: (Primary agent in a redundant pair.) Can be installed on a Microsoft AD domain controller, directory server, or any network client.
Handles all communication with the Cloud-Delivered Firewall Management Center unless it stops communicating, in which case communication is handled by secondary agents.
-
Secondary: (Secondary, or backup, agent in a redundant pair.) Can be installed on a Microsoft AD domain controller, directory server, or any network client.
Monitors the health of the primary agent and takes over if the primary agent stops communicating with the Cloud-Delivered Firewall Management Center.
Passive identity agent system requirements
The passive identity agent requires the following:
-
If you install the passive identity agent on a Windows Active Directory server, the server must run Windows Server 2008 or later.
-
If you install it on a Windows client attached to the domain, the client must run Windows 8 or later.
-
The system clock on all systems must be synchronized. We strongly recommend using the same NTP servers on all of them. This means:
-
The Security Cloud Control.
For more information, see Configure NTP Server.
-
All Windows Active Directory servers and domain controllers.
-
The machine on which the passive identity agent is installed.
-
-
Security Cloud Control must run November 8, 2024 or later.
-
You must enable Snort 3 on the Secure Firewall Threat Defense devices.
Passive identity agent limitations
The passive identity agent the following limitations:
-
Up to 10 agents simultaneously
-
One passive identity agent identity source can monitor up to 50 AD directories
-
Up to 300,000 concurrent user sessions
-
IPv6 addresses are not supported (passive identity agent 1.0)
-
IPv6 addresses are supported (passive identity agent 1.1)
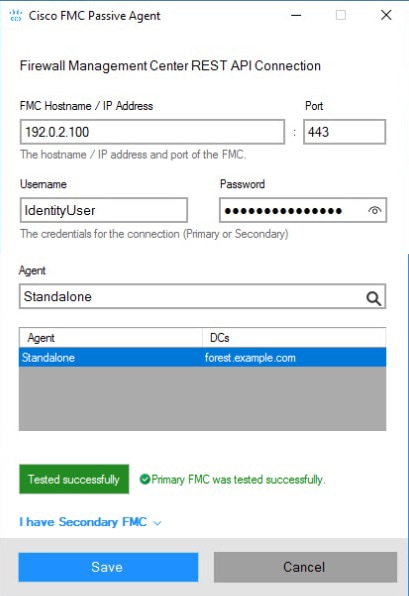
Deploy the passive identity agent
For information about deployment options, see Deploy the Passive Identity Agent.
 Note |
We recommend you use the latest version of the passive identity agent. To see the available versions, go to software.cisco.com. To upgrade the passive identity agent, see Upgrade the Passive Identity Agent Software |















 Feedback
Feedback