About Users
You can add custom user accounts on managed devices, either as internal users or as external users on a LDAP or RADIUS server. Each managed device maintains separate user accounts. For example, when you add a user to the management center, that user only has access to the management center; you cannot then use that username to log directly into a managed device. You must separately add a user on the managed device.
Internal and External Users
Managed devices support two types of users:
-
Internal user—The device checks a local database for user authentication.
-
External user—If the user is not present in the local database, the system queries an external LDAP or RADIUS authentication server.
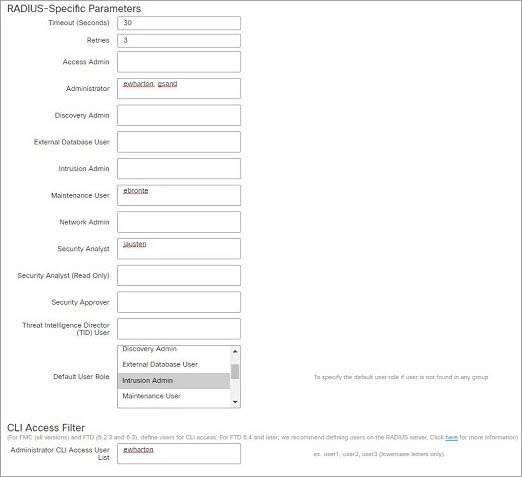
User Roles
Web Interface User Roles
There are a variety of user roles in Cisco Defense Orchestrator (CDO): Read-Only, Edit-Only, Deploy-only, Admin, and Super Admin. User roles are configured for each user on each tenant. If a CDO user has access to more than one tenant, they may have the same user ID but different roles on different tenants. A user may have a read-only role on one tenant and a Super Admin role on another. When the interface or the documentation refers to a Read-only user, Deploy Only, Edit Only, an Admin user, or a Super Admin user we are describing that user's permission level on a particular tenant. Note that you cannot create user roles in the cloud-delivered Firewall Management Center because it uses CDO user roles.
- Read Only
-
Read Only users can view all device configurations but not change them.
- Deploy Only
-
Deploy Only users can audit queued changes made to device configurations and deploy them but cannot change them.
- Edit Only
-
Edit Only users can make changes to all device configurations but cannot deploy them to devices.
- Super Admin and Admin
-
Super Admin and Admin users can access everything in the product. The difference between Super Admin and Admin users is that Super Admins can create accounts for other users on a tenant and modify existing user roles, while admins cannnot.
To know more about user roles in CDO, see User Roles.
 Tip |
We recommend that you read through the table only if you are familiar with the user roles in On-Prem Firewall Management Center. |
|
On-Prem Firewall Management Center User Role |
Equivalent Cloud-delivered Firewall Management Center User Role |
Capabilities |
|---|---|---|
|
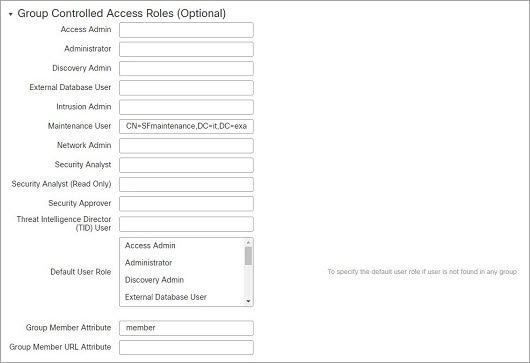
Access Admin, Discovery Admin, Intrusion Admin, Maintenance User |
Edit Only |
You can search, filter, or view the following:
You can back up or restore a device but cannot deploy policies to the devices. |
|
Administrator |
Super Admin |
You can access all features of the cloud-delivered Firewall Management Center and perform tasks, including create, read, modify, or delete policies or objects and deploy those changes to the devices. You can also edit user roles or create user records in CDO. |
|
Network Admin |
Admin |
You can access all features of the cloud-delivered Firewall Management Center and perform tasks, including create, read, modify, or delete policies or objects and deploy those changes to the devices. However, you cannot edit user roles or create user records in CDO. |
|
Security Analyst, Security Analyst (Read Only) |
Read Only |
You can view device information, policies, objects, and their related settings but cannot do the following:
|
|
Security Approver |
Deploy Only |
You can view most settings and deploy staged changes to devices but cannot create or modify objects or policies. |
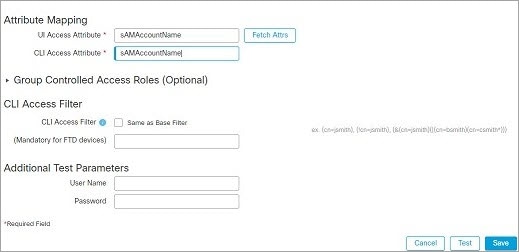
 to add a new user to your tenant.
to add a new user to your tenant.

 )
)


 )
) Feedback
Feedback