Overview of Firewall Services
The Firewall policy folder (in either Device or Policy view) includes firewall-related policies that you can deploy to the Adaptive Security Appliance (ASA), PIX Firewall (PIX), and Catalyst Firewall Services Module (FWSM).
 Note |
From version 4.21 onwards, Cisco Security Manager terminates whole support, including support for any bug fixes or enhancements, for all Aggregation Service Routers, Integrated Service Routers, Embedded Service Routers, and any device operating on Cisco IOS software |
These policies are focused on controlling access through the device, rather than access to the device (that is, logging into the device so that you can change its configuration or use show commands). Following is a general overview of the available firewall policies with pointers to topics that provide more detailed information:
-
AAA rules—These are AAA firewall or authentication proxy rules that can require a user to authenticate (with a username and password) and optionally be authorized before the device allows the user to make network connections through it. You can also create accounting rules to collect billing, security, or resource allocation information. For more information, see Understanding AAA Rules.
-
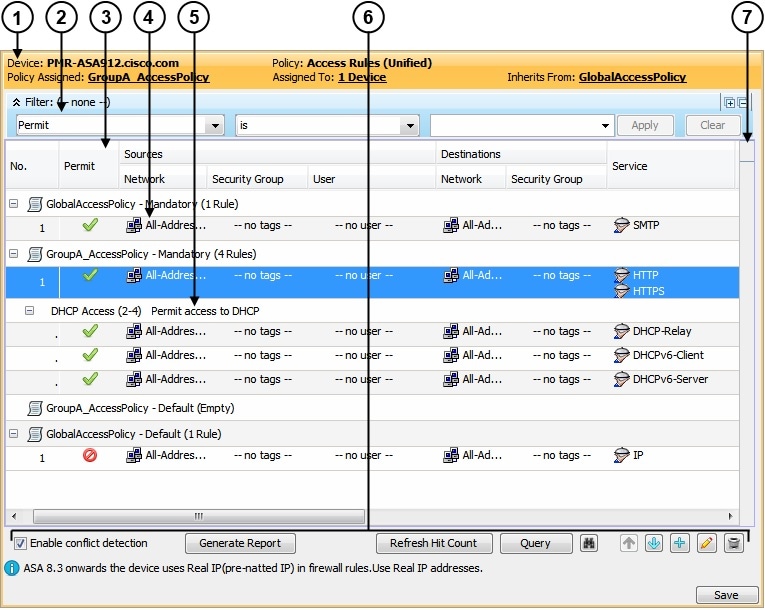
Access rules—These are traditional interface-based extended access control rules. They permit or deny a packet based on source address, destination address, source interface, and service, and you can apply them in both the in and out directions. For more information, see Understanding Access Rules.
-
Inspection rules—These are traditional Context-Based Access Control (CBAC) inspection rules that filter out bad TCP/UDP packets based on application-layer protocol session information and that enable return traffic for the selected services. For more information, see Understanding Inspection Rules.
-
Web filter rules—These are a type of inspection rule that filters web traffic based on the requested URL, allowing you to prevent connections to undesirable web sites. For more information, see Understanding Web Filter Rules.
-
Zone-based firewall rules—These rules replace access rules, inspection rules, and web filter rules on IOS devices if you want to configure your rules based on zones instead of interfaces. A zone is a defined group of interfaces that perform the same security role (such as Inside or Outside). By using zone rules, you can create more compact device configurations than you can by using the other types of rules. For more information, see Understanding the Zone-based Firewall Rules.
-
Botnet Traffic Filter Rules—These rules help you to spot botnet traffic when it is sent to known bad addresses. Botnets install malware on unsuspecting computers and use those computers as proxies to perform malicious actions. For more information, see Managing Firewall Botnet Traffic Filter Rules.
-
Transparent rules—These are Ethertype access control rules that apply to non-IP layer-2 traffic on transparent or bridged interfaces. For more information, see Configuring Transparent Firewall Rules.
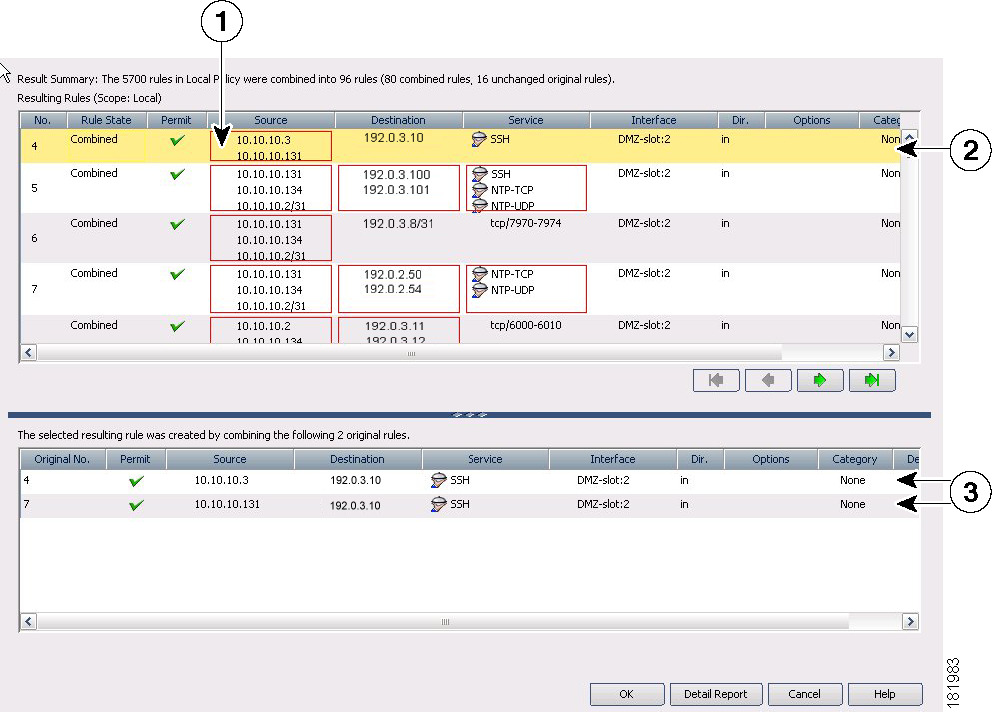
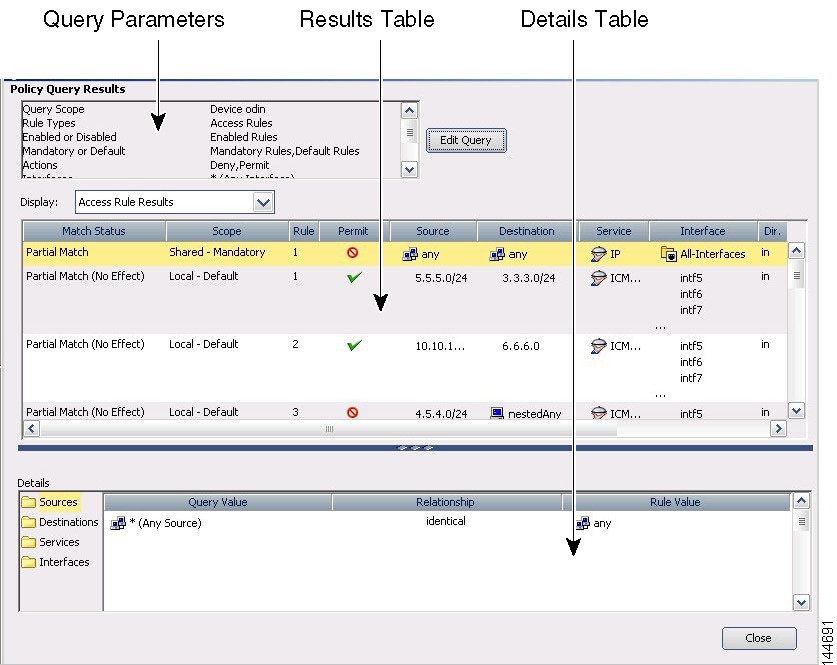
Most firewall rules policies are configured in rules tables. These tables allow in-line editing for most cells, rule organization using sections, and the ability to change the order of rules. If you create shared rules policies, you can apply them to a number of devices, even to devices running different operating systems, and Security Manager automatically creates the appropriate device commands to configure the policies based on the characteristics of each individual device, filtering out settings that do not apply to a device. For more information on using rule tables, see Managing Your Rules Tables.
Another powerful feature used by most firewall rules policies is the idea of inheritance. When you create shared policies, one of your options is to have a device inherit the policy rather than be assigned the policy. This allows you to have a set of shared rules that apply to all devices, while having unique rules that apply to only those devices that require them. For more information about inheritance, see the following topics:
The following topics provide additional overview information about firewall services policies:
Understanding the Processing Order of Firewall Rules
When you configure firewall rules policies, you should keep in mind the logical order in which the rules are processed. For example, if you plan to drop all traffic of a certain type in an access rule, there is no reason to create rules in other firewall policies that apply to that type of traffic, because they will never be triggered. Conversely, if you want to apply certain types of inspection or web filtering on traffic, you must ensure that your access rules first allow that traffic to enter the device.
Following is the general logical processing order of firewall rules:
-
AAA rules—If you require authentication, with or without authorization, the user must successfully pass the test or the traffic is dropped.
-
Access rules (In direction)—The traffic must then get through your access rules. If you used AAA rules, you might have allowed temporary per-user access rules to be configured for the user’s session. These per-user rules are configured in your AAA server, not in Security Manager.
On ASA 8.3+ devices, global access rules are then processed after any interface-specific access rules. For more information, see Understanding Global Access Rules.
-
Inspection rules (In direction), web filter rules (In direction), botnet rules, service policy rules (IPS, QoS, Connection)—All of these are applied to the traffic. For devices that do not allow you to configure the direction, all rules are considered to be in the In direction.
-
Zone-based firewall rules—If you configured zone-based rules for an IOS device, these rules replace inspection and web filter rules (botnet rules do not apply to IOS devices).
-
Routing protocols are then applied to the traffic. The traffic is dropped if it cannot be routed. (Routing policies are in the Platform folders for the various device types and are not considered firewall policies.)
-
ScanSafe Web Security policies, Inspection rules (Out direction), web filter rules (Out direction)—For IOS devices only, if you created ScanSafe policies, or inspection or web filter rules in the Out direction, they are now applied.
-
Access rules (Out direction)—Finally, the traffic must pass through any Out direction access rules.
Transparent rules do not fit into this picture. Because transparent rules apply to non-IP layer-2 traffic only, if a transparent rule applies to a packet, no other firewall rule applies to it; and conversely, if other rules apply, the transparent rule never applies.
Related Topics
Understanding How NAT Affects Firewall Rules
Devices that support firewall rules also allow you to configure network address translation (NAT). NAT substitutes the real address in a packet with a mapped address that is routable on the destination network.
If you configure NAT to occur on an interface, the firewall rules that are also configured on that interface should assess traffic based on the translated address rather than on the original (pre-NAT) address, with the exception of ASA 8.3+ devices.
Devices running ASA software release 8.3 and later use the original, or real, IP address when evaluating traffic with the exception of IPSec VPN traffic policies. Thus, when you configure firewall rules, ACL policy objects, or the IOS, QoS, and connection rules platform service policy, ensure that you use the original addresses.
For more information about NAT, see the following topics:
-
ASA, PIX, FWSM devices—Understanding Network Address Translation.
-
IOS devices—NAT Policies on Cisco IOS Routers.
ACL Names Preserved by Security Manager
Security Manager tries to preserve user-defined access control list (ACL) names as they appear in device configurations. Security Manager can preserve the ACL names configured on a device in the following circumstances:
-
If the ACL name is specified in Security Manager.
For access rules policies, you can specify ACL names in or . You can specify a given name for a single interface and direction, but the name is used for any other interfaces and directions that use the same ACL. Keep in mind that you cannot use the same name as an ACL policy object that you assign to other policies on the device, and you cannot use the same name for IPv4 and IPv6 ACLs.
 Note |
Prior to the release of Security Manager 4.4 and versions 9.0 and later of the ASA, separate pages, policies and policy objects were provided for configuring IPv4 and IPv6 firewall rules and policies. With Security Manager 4.4 and ASA 9.0+, these policies and policy objects were combined or unified. However, for the earlier ASA versions, a separate page for IPv6 access rules is still provided in Device view, while in Policy view, IPv4 and unified versions of the AAA-, access- and inspection-rule policy types are provided. |
-
If a policy uses an ACL policy object, the name of the policy object is used for the ACL name. ACL policy objects created during discovery use the name of the ACL defined on the device whenever possible. Behavior depends on an administrative setting:
-
If you select Allow Device Override for Policy Objects in , if a policy object with the same name exists in Security Manager, but it has different content, the name is reused and a device-level override is created.
-
If you do not select that option, a new policy object is created with the same name but with a number appended to it, for example, ACLobject_1. This is the default behavior.
-
-
If you select Reuse Existing Names for the Firewall Access List Names setting in , names defined on the device are reused for firewall rules that generate ACLs.
-
If the ACL is unshared, even if you change the content of the ACL in Security Manager.
-
If the ACL is shared, but the policies that share the ACL are defined identically in Security Manager. If you change the content of the ACL, one ACL retains the name and the others are assigned generated names.
 Note |
On ASA devices and on PIX devices not running version 6.3(x), Security Manager does not reuse the ACL name if it is used by a NAT policy static rule and contains an object-group. The ACL is deployed with the contents of the object-group defined as the source. This is because the device requires that all ACEs in the ACL have the same source. |
Tips
-
If you use an ACL policy object that uses a name also used by an ACL already defined on the device, and the existing ACL is for a command that Security Manager does not support, you will get a deployment error asking you to choose a different name. If this happens, rename the policy object.
-
ACLs named <number>_<number> are not valid on IOS devices. Security Manager strips off the suffix prior to deployment. This also means that you cannot assign an IOS device more than one ACL object with the same numbered prefix. However, named ACLs that have a numbered suffix are allowed, for example, ACLname_1.
-
Numbered ACLs must use the correct number ranges for IOS devices. Standard ACLs must be in the range 1-99 or 1300-1999. Extended ACLs must be in the range 100-199 or 2000-2699.
-
ACL names for IOS devices cannot begin with an underscore (_).
-
Policies that do not preserve user-defined names include SSL VPN policies, transparent firewall rules, and AAA rules (for IOS devices).
The following topics provide additional information about ACL naming:
ACL Naming Conventions
When the name for the ACL is generated by Security Manager, the name is derived from the type of rule or platform being defined and certain configuration settings that make it unique. All newly created ACLs are given a name based on the naming conventions shown in the following table.
 Tip |
During deployment, sometimes a suffix .n (where n is an integer) might get added to an ACL name if the existing ACL cannot be edited in place. For example, if an ACL named acl_mdc_outside_10 already exists on the device, a new ACL with the name acl_mdc_outside_10.1 is created if you do not remove the old ACL before you deploy the new ACL. |
|
Policy Type |
Naming Convention |
||
|---|---|---|---|
|
Access ACLs |
|
||
|
IPv6 Access ACLs |
|
||
|
Inspection Rules |
|
||
|
NAT0 ACLs |
|
||
|
NAT ACLs |
|
||
|
NAT Policy Static Translation Rules ACLs |
|
||
|
AAA ACLs |
For PIX/ASA/FWSM: CSM_AAA_{AUTHO | ATHEN | ACCT}_InterfaceName _ServerGroupName Authentication Proxy for IOS devices:
|
||
|
Web Filter Rules ACLs |
For ASA 7.0+/PIX 7.0+: devices correspond to a filter command. For IOS devices, a numbered ACL. |
Resolving User Defined ACL Policy Naming Conflicts
Cisco Security Manager generates ACL names that begin with “CSM_”. You should not use the same naming pattern while defining a ACL in the device. If you declare ACL names with the “CSM_” prefix on device, during discovering the device configuration in Cisco Security Manager, those ACL names are replaced with Security Manager generated names and respective configuration delta would be applied to a device on the next deployment.
For example, Cisco Security Manager has CSM_FW_ACL_InterfaceName as the ACL naming pattern for inbound firewall interface. Here, if you use the CSM pattern for ACL name declaration in device like, CSM_xyz, Security Manager renames it as “CSM_FW_ACL_InterfaceName”.
 Note |
This rule is valid for firewall access list and delta would be generated and applied to a device even when the Reuse existing names setting is configured in Tools > Security Manager Administration > Deployment. |
Resolving ACL Name Conflicts Between Policies
If an ACL is shared, but the policies that share the ACL are not defined identically in Security Manager, one policy uses the original name of the ACL and the other policies use a new name generated by Security Manager. The order of preference for determining which policy uses the original name is as follows:
-
Access list ACLs
-
AAA ACLs
-
Static ACLs
-
NAT0 ACLs
-
NAT ACLs
For example, if an access ACL and a NAT0 ACL try to reuse the same ACL, the access ACL uses the original name as configured on the device and the NAT0 ACL is renamed by Security Manager.

 Feedback
Feedback