802.1x on Cisco IOS Routers
 Note |
From version 4.17, though Cisco Security Manager continues to support IOS features/functionality, it does not support any bug fixes or enhancements. |
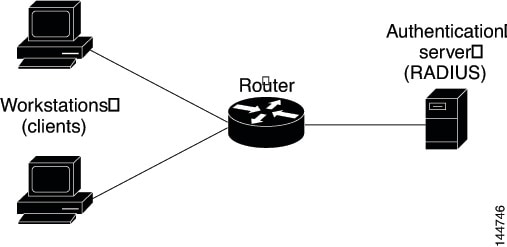
The IEEE 802.1x standard defines 802.1x port-based authentication as a client-server based access control and authentication protocol that restricts unauthorized clients from connecting to a LAN through public ports. The authentication server validates each client connected to an interface before making available any services offered by the router or the LAN.
Until the client is authenticated, 802.1x access control allows only Extensible Authentication Protocol over LAN (EAPOL) traffic through the interface to which the client is connected. If authentication is successful, normal traffic can pass through the interface.
802.1x authentication provides VPN access control, enabling unauthenticated traffic to access the Internet while preventing it from accessing the VPN tunnel. This solution is especially useful for enterprises whose workers access the corporate VPN through a home access router that other family members use to access the Internet. When you use 802.1x, you create a virtual interface to carry unauthenticated traffic while authenticated traffic continues to pass through the physical interface.
802.1x requires that you use DHCP to provide IP addresses to the clients that request authentication. We recommend that you use two IP address pools, one for authenticated traffic and the other for unauthenticated traffic. If you use two pools, the DNS server in the corporate DHCP pool should point to the corporate DNS server. The DNS server for the noncorporate DHCP pool should use the DNS server provided by the ISP on the public interface. You configure DHCP by selecting a DHCP policy. See DHCP on Cisco IOS Routers for more information.
 Note |
802.1x is supported on the following platforms—Cisco 800, 1700, 1800, 1900, 2600, 2800, 2900, 3600, 3700, 3800, 3900 Series Routers. |
For more information about 802.1x, see:
Understanding 802.1x Device Roles
802.1x port-based authentication uses the following device roles:
-
Client—The workstation requesting access to the VPN. It must be running 802.1x-compliant client software, such as that offered with the Microsoft Windows XP operating system.
-
Authentication server—Authenticates clients. The authentication server validates the client’s identity and notifies the router whether the client is authorized to access the network. The Remote Authentication Dial-In User Service (RADIUS) security system with EAP extensions is the only supported authentication server. In Security Manager, a AAA (authentication, authorization, and accounting) server, as defined in a AAA server object, is the authentication server for 802.1x policies.
-
Router (edge router or wireless access point)—Controls physical access to the network based on the authentication status of the client. The router is an intermediary (proxy) between the client and the authentication server, requesting identity information from the client, verifying that information with the authentication server, and relaying a response to the client. In Security Manager, the router on which you configure an 802.1x policy acts as the switch.
Related Topics
802.1x Interface Authorization States
When you use 802.1x, the interface state determines whether to grant the client network access. By default, the interface starts in the unauthorized state. While in this state, the interface disallows all traffic in both directions, except for EAPOL packets. After a client is authenticated, the interface transitions to the authorized state, enabling all client traffic to flow normally.
If a client that does not support 802.1x is connected to an unauthorized 802.1x interface, the router requests the client’s identity. In this situation, the client does not respond to the request, the interface remains in the unauthorized state, and the client is not granted access to the network. In contrast, when an 802.1x-enabled client connects to an interface that is not running the 802.1x protocol, the client initiates the authentication process by sending the EAPOL-Start frame. If no response is received, the client sends the request a fixed number of times. Because no response is received, the client begins sending frames as if the interface were in the authorized state.
You can control the interface authorization state by selecting one of the following options:
-
Auto—Enables 802.1x authentication, which causes the interface to start in the unauthorized state. Only EAPOL frames are sent and received through the interface. Authentication begins when the link state of the interface transitions from down to up or when an EAPOL-Start frame is received. The router requests the client’s identity and begins relaying authentication messages between the client and the authentication server. The router uses the MAC address of each client trying to access the network as unique client identifiers.
-
Force authorized—Disables 802.1x authentication, which causes the interface to move to the authorized state without authenticating the client.
After a client is successfully authenticated, the interface state changes to authorized, which enables all frames from the client to enter the network. If authentication fails, the interface remains in the unauthorized state, but authentication can be retried. If the authentication server cannot be reached, the router can retransmit the request. If the authentication server does not respond after the defined number of attempts, authentication fails and network access is denied to the client.
When a client logs off, it sends an EAPOL-Logoff message, which causes the interface to return to the unauthorized state.
Related Topics
Topologies Supported by 802.1x
802.1x port-based authentication supports two topologies:
-
Point-to-point
-
Wireless LAN
In a point-to-point configuration, only one client can be connected to the 802.1x-enabled interface. The router detects the client when the interface state changes from down to up. If a client leaves the network or is replaced by another client, the interface state changes from up to down, which returns the interface to the unauthorized state.
In a wireless LAN configuration, the 802.1x interface is configured in multihost mode, which is authorized as soon as one client is authenticated. After the interface is authorized, all other clients indirectly attached to the interface are granted access to the network. If the port becomes unauthorized (either because reauthentication fails or an EAPOL-Logoff message is received), the router denies access to the network to all attached clients. In this topology, the wireless access point is a client to the router and is responsible for authenticating the clients attached to it.
Related Topics
Defining 802.1x Policies
You configure an 802.1x policy by defining:
-
The AAA server group containing the AAA server that authenticates hosts that are trying to connect to the network.
-
The virtual interface that carries unauthenticated traffic and the physical interface that carries authenticated traffic.
-
(Optional) Properties of the physical interface, including the control type, automatic reauthentication, and several timeout values.
If the router on which you are defining the 802.1x policy is not part of a VPN (for example, if it is directly connected to the corporate network to which you want to restrict access), you must manually define an access list. You can do this by defining an access rules policy (see Understanding Access Rules).
Before You Begin
-
Configure the selected router with a DHCP policy that contains two IP address pools, one for authenticated clients and one for unauthenticated clients. See Defining DHCP Policies.
-
Make sure the router can route packets to the configured AAA (RADIUS) server. You can verify this by pinging the server from the router.
Related Topics
Procedure
|
Step 1 |
Do one of the following:
The 802.1x page is displayed. See Table 1 for a description of the fields on this page. |
||||
|
Step 2 |
Enter the name of the AAA server group containing the AAA server to use for authenticating clients using 802.1x, or click Select to select a server group from a list or to create a new one. The selected AAA server must use RADIUS with EAP extensions.
|
||||
|
Step 3 |
In the Virtual Template field, enter the name of the interface or interface role that serves as the untrusted, virtual interface for carrying unauthenticated traffic, or click Select to select an interface role from a list or to create a new role. For more information, see Specifying Interfaces During Policy Definition.
|
||||
|
Step 4 |
Enter the name of the interface or interface role that serves as the trusted, physical interface for carrying authenticated traffic, or click Select to select a role from a list. The interface role you select should represent the internal protected interface that was configured as part of the VPN topology and no other physical interface on the selected router. For more information, see Defining the Endpoints and Protected Networks. |
||||
|
Step 5 |
(Optional) Modify the defaults of the physical interface used for 802.1x authentication. See Table 1 for details. |
 Feedback
Feedback