About Identity Policies
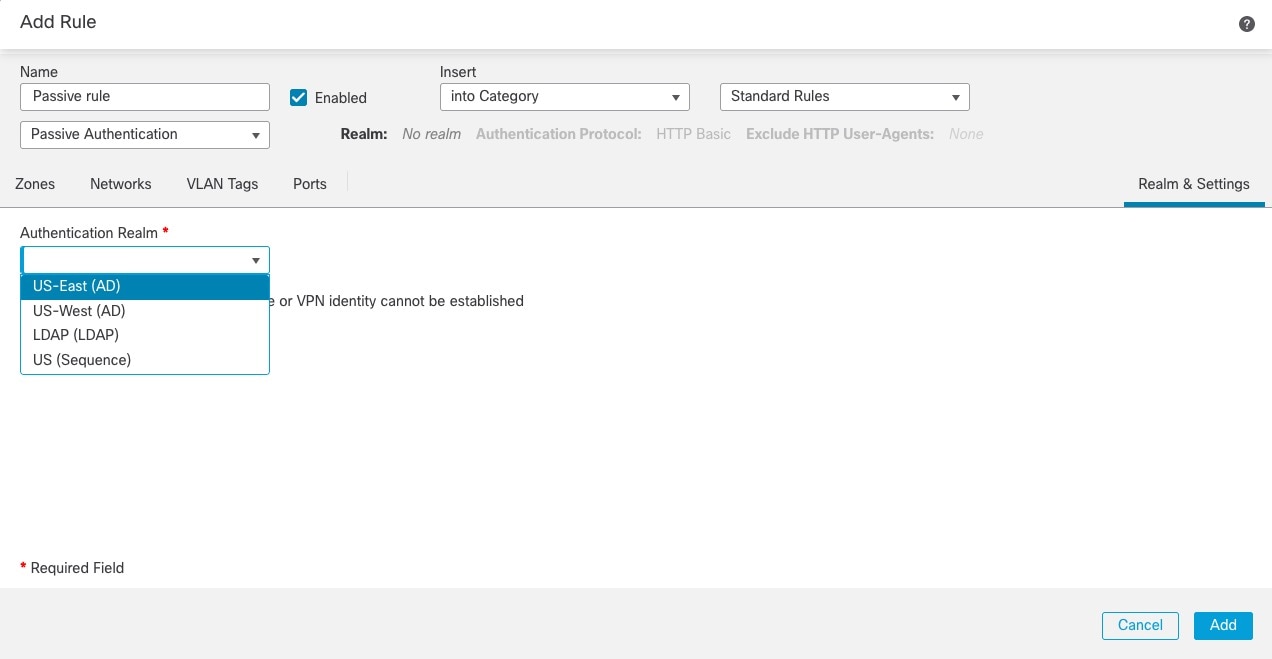
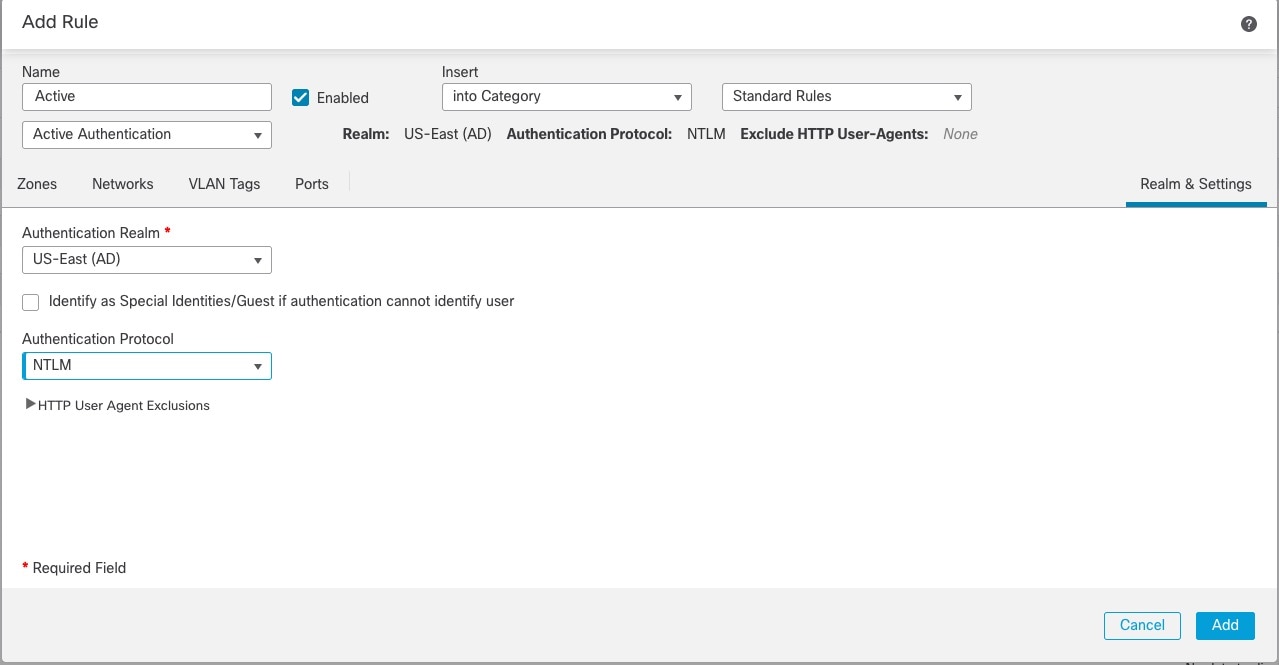
Identity policies contain identity rules. Identity rules associate sets of traffic with a realm and an authentication method: passive authentication, active authentication, or no authentication.
With the exception noted in the following paragraphs, you must configure realms and authentication methods you plan to use before you can invoke them in your identity rules:
-
You configure realms outside of your identity policy, at . For more information, see Create an LDAP Realm or an Active Directory Realm and Realm Directory.
-
You configure ISE/ISE-PIC, a passive authentication identity source, at .
-
You configure the TS Agent, a passive authentication identity source, outside the system. For more information, see the Cisco Terminal Services (TS) Agent Guide.
-
You configure captive portal, an active authentication identity source, within the identity policy. For more information, see How to Configure the Captive Portal for User Control.
-
You configure Remote Access VPN, an active authentication identity source, in Remote Access VPN policies. For more information, see Remote Access VPN Authentication.
After you add multiple identity rules to a single identity policy, order the rules. The system matches traffic to rules in top-down order by ascending rule number. The first rule that traffic matches is the rule that handles the traffic.
You can also filter traffic by network object, which limits the network each device monitors in the event your devices are at or near their memory limits.
After you configure one or more identity policies, you must associate one identity policy with your access control policy. When traffic on your network matches the conditions in your identity rule, the system associates the traffic with the specified realm and authenticates the users in the traffic using the specified identity source.
If you do not configure an identity policy, the system does not perform user authentication.
Exception to creating an identity policy
An identity policy is not required if all of the following are true:
-
You use the ISE/ISE-PIC identity source.
-
You do not use users or groups in access control policies.
-
You use Security Group Tags (SGT) in access control policies. For more information, see ISE SGT vs Custom SGT Rule Conditions.













 Feedback
Feedback