License Requirements for Realms
Threat Defense License
Any
Classic License
Control
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
The following topics describe realms and identity policies:
Any
Control
Any.
Any
Admin
Access Admin
Network Admin
You can use a Microsoft Azure Active Directory (AD) realm with ISE to authenticate users and get user sessions for user control. We get groups from Azure AD and logged-in user session data from ISE.
You have the following options:
Resource owned password credentials (ROPC): Enables users to log in with a client like AnyConnect using a user name and password. ISE sends user sessions to the Secure Firewall Management Center. For more information, see About Azure AD and Cisco ISE with Resource Owned Password Credentials.
Additional resource: Microsoft identity platform and OAuth 2.0 Resource Owner Password Credentials on learn.microsoft.com.
Extensible Authentication Protocol (EAP) Chaining with Tunnel-based Extensible Authentication Protocol (TEAP) and Transport Layer Security (TLS), abbreviated EAP/TEAP-TLS: TEAP is a tunnel-based EAP method that establishes a secure tunnel and executes other EAP methods under the protection of that secured tunnel. ISE is used to validate user credentials and to send user sessions to the Secure Firewall Management Center. For more information, see About Azure AD and Cisco ISE with TEAP/EAP-TLS.
 Note |
Before deploying policies related to a Microsoft Azure AD realm, see User Limits for Microsoft Azure Active Directory Realms. |
The following figure summarizes an Azure AD realm with Cisco ISE and resource owned password credentials (ROPC):

With ROPC,
The user logs in with a user name (or email address) and password using a VPN client like Cisco Secure Client.
The client ID, client secret, user name, password, and scopes are sent to Azure AD.
Tokens are sent from Azure AD to Cisco ISE, which sends user sessions to the Secure Firewall Management Center.
For details about configuring Cisco ISE, see Configure ISE 3.0 REST ID with Azure Active Directory.
Additional resource: Microsoft identity platform and OAuth 2.0 Resource Owner Password Credentials on learn.microsoft.com.
Tunnel Extensible Authentication Protocol (TEAP) , defined by RFC7170, can be used with ISE and the Secure Firewall Management Center as follows:
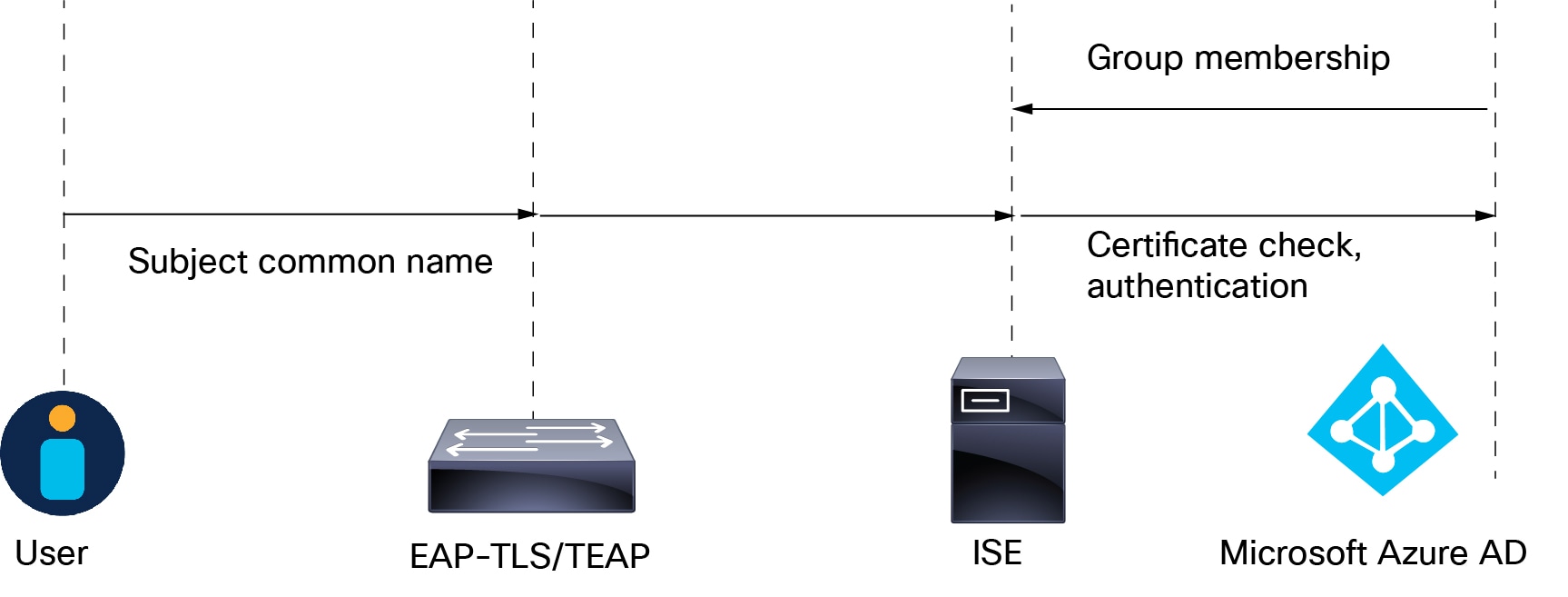
The following is based on Configure Cisco ISE 3.2 EAP-TLS with Microsoft Azure Active Directory:
The user's certificate is sent to ISE through EAP-TLS or TEAP with EAP-TLS as the inner method.
ISE evaluates the user’s certificate (validity period, trusted certificate authority, certificate revocation list, and so on).
ISE takes the certificate subject name (CN) and performs a look-up to the Azure Graph API to fetch the user’s groups and other attributes. This is referred to by Azure as User Principal name (UPN).
ISE authorization policies are evaluated against the user’s attributes returned from Azure.
This topic discusses the high-level tasks of creating a realm for passive authentication use with the Secure Firewall Management Center.
| Command or Action | Purpose | |
|---|---|---|
|
Step 1 |
Enable the Cisco Secure Dynamic Attributes Connector. |
|
|
Step 2 |
Configure Microsoft Azure AD. |
Several configuration tasks are required, including setting up an event hub, giving your application permission to the Microsoft Graph API, and enabling the audit log. |
|
Step 3 |
Configure Cisco ISE. |
|
|
Step 4 |
Create a Cisco ISE identity source. |
The identity source enables ISE to communicate with the Secure Firewall Management Center. |
|
Step 5 |
Get the information required to configure your Microsoft Azure AD realm. |
|
|
Step 6 |
Configure and verify your realm. |
Test the realm's configuration before you start to use it in access control policies. |
|
Step 7 |
Create access control policies and rules using your Microsoft Azure AD (SAML) realm. |
Unlike other types of realms, you do not need to create an identity policy or associate the identity policy with an access control policy. See Creating a Basic Access Control Policy and Create and Edit Access Control Rules. |
See About Azure AD and Cisco ISE with Resource Owned Password Credentials.
This topic provides basic information about how to set up a Microsoft Azure Active Directory (AD) as a realm you can use with the Secure Firewall Management Center. We expect you to already be familiar with Azure AD; if not, consult documentation or a support resource before you get started.
Grant your Azure AD application the following permissions to Microsoft Graph as discussed in Authorization and the Microsoft Graph Security API on the Microsoft site:
Reader role
User.Read.All permission
Group.Read.All permission
This permission enables the Secure Firewall Management Center to download users and groups from Azure AD the first time.
Required information from this step for setting up the Azure AD realm in the Secure Firewall Management Center:
Name of the app you registered
Application (client) ID
Client secret
Directory (tenant) ID
Set up the event hub as discussed in Quickstart: Create an event hub using Azure portal on the Microsoft site. The Secure Firewall Management Center uses the event hub audit log to download periodic updates to users and groups.
More information: Features and terminology in Azure Event Hubs.
 Important |
You must choose the Standard pricing tier or better. If you choose Basic, the realm cannot be used. |
Required information from this step for setting up the Azure AD realm in the Secure Firewall Management Center:
Namespace Name
Connection string—primary key
Event Hub Name
Consumer group Name
Enable the audit log as discussed in Tutorial: Stream Azure Active Directory logs to an Azure event hub on the Microsoft site.
To send user session information to the Secure Firewall Management Center, configure Cisco ISE for Azure AD as discussed in Configure ISE 3.0 REST ID with Azure Active Directory.
In a Microsoft Azure AD realm, it's the responsibility of ISE to send user sessions (login, logout) to the Secure Firewall Management Center. This topic discusses how to set up ISE for use with an Azure AD realm.
To use ISE with Microsoft Azure ADMicrosoft Azure AD implemented through Representational State Transfer (REST) Identity (ID) service with the help of Resource Owner Password Credentials (ROPC), see Configure ISE 3.0 REST ID with Azure Active Directory.
To use ISE with authorization policies based on Azure AD group membership and other user attributes with EAP-TLS or TEAP as the authentication protocols, see Configure Cisco ISE 3.2 EAP-TLS with Microsoft Azure Active Directory.
What to do next
This task explains how to get the information required to set up a Microsoft Azure AD realm in the Secure Firewall Management Center. You might have already obtained this information when you set up Microsoft Azure AD as discussed in Configure Microsoft Azure Active Directory.
|
Step 1 |
Log in to https://portal.azure.com/ as a user with at least the Product Designer role. |
|
Step 2 |
At the top of the page, click Microsoft Entra ID. |
|
Step 3 |
In the left column, click App Registrations. |
|
Step 4 |
If necessary, filter the list of displayed apps to show the one you want to use. |
|
Step 5 |
Click the name of your app.
|
|
Step 6 |
Click Copy (
|
|
Step 7 |
Click Client Credentials. |
|
Step 8 |
Unless you already know the client secret value (as opposed to the client secret ID), you must create a new client secret as follows: |
|
Step 9 |
From https://portal.azure.com/, click . |
|
Step 10 |
In the right pane, click Copy (
|
|
Step 11 |
Write down or copy to a text file the name of the event hub (same as the Event Hubs Namespace at the top of the page). |
|
Step 12 |
In the left pane, under Settings, click Shared access policies. |
|
Step 13 |
Click the name of a policy. |
|
Step 14 |
Click Copy (
|
|
Step 15 |
Click . Write down the following value or copy it to the clipboard. This is your consumer group name.
|
|
Step 16 |
In the left pane, click Overview. |
|
Step 17 |
Click Copy (  This is your event hubs topic name. |
The following procedure enables you to create a realm (a connection between the management center and a Microsoft Azure AD realm).
Complete all of the following tasks:
Configure ISE as discussed in How to Configure ISE for Microsoft Azure AD
Create an ISE identity source as discussed in Configure ISE/ISE-PIC
Enable the Cisco Secure Dynamic Attributes Connector as discussed in Enable the Cisco Secure Dynamic Attributes Connector .
Get values required for the Azure AD realm as discussed in Get Required Information For Your Microsoft Azure AD Realm.
Configure Azure AD as discussed in Configure Microsoft Azure Active Directory
 Note |
To perform user and identity control with an Azure AD realm, you need only an access control policy with an associated Azure AD realm. You do not need to create an identity policy. |
|
Step 1 |
Log in to Secure Firewall Management Center . |
|||||||||||||||
|
Step 2 |
Click . |
|||||||||||||||
|
Step 3 |
To create a new realm, click . |
|||||||||||||||
|
Step 4 |
Enter the following information.
|
|||||||||||||||
|
Step 5 |
To perform other tasks (such as enable, disable, or delete a realm), see Manage a Realm. |
|||||||||||||||
|
Step 6 |
Enter the values you found as discussed in Get Required Information For Your Microsoft Azure AD Realm. |
|||||||||||||||
|
Step 7 |
Click Test. |
|||||||||||||||
|
Step 8 |
Fix any errors that are displayed in the test. |
|||||||||||||||
|
Step 9 |
Click Save. |
Create an access control policy and rule as discussed in Creating a Basic Access Control Policy.
 Note |
Before deploying policies related to a Microsoft Azure AD realm, see User Limits for Microsoft Azure Active Directory Realms. |
The Azure AD user session timeout for ISE/ISE-PIC is available on the User Session Timeout page when you edit an Azure AD realm.
The default value 1440 minutes (24 hours). After the timeout is exceeded, the user's session ends; if the user continues to access the network without logging in again, the user is seen by the management center as Unknown (except for Failed Captive Portal Users).
If you're setting up ISE/ISE-PIC without a realm, be aware there is a user session timeout that affects how users are seen by the Secure Firewall Management Center. For more information, see Realm Fields.
The following procedure enables you to create a realm (a connection between the management center and an Active Directory realm) and a directory (a connection between the management center and an LDAP server or an Active Directory domain controller).
(Recommended.) To connect securely from the management center to your Active Directory server, first perform the following tasks:
Microsoft has announced that Active Directory servers will start enforcing LDAP binding and LDAP signing in 2020. Microsoft is making these a requirement because when using default settings, an elevation of privilege vulnerability exists in Microsoft Windows that could allow a man-in-the-middle attacker to successfully forward an authentication request to a Windows LDAP server. For more information, see 2020 LDAP channel binding and LDAP signing requirement for Windows on the Microsoft support site.
For more information about realm and directory configuration fields, see Realm Fields and Realm Directory and Synchronize fields.
A step-by-step example of setting up a realm with cross-domain trust is shown in Configure the Management Center for Cross-Domain-Trust: The Setup.
An Active Directory Global Catalog server is not supported as a realm directory. For more information about the Global Catalog Server, see Global Catalog on learn.microsoft.com.
 Note |
You must specify a unique AD Primary Domain for every Microsoft Active Directory (AD) realm. Although the system allows you to specify the same AD Primary Domain for different Microsoft AD realms, the system won't function properly. This happens because system assigns a unique ID to every user and group in each realm; therefore, the system cannot definitively identify any particular user or group. The system prevents you from specifying more than one realm with the same AD Primary Domain because users and groups won't be identified properly. This happens because system assigns a unique ID to every user and group in each realm; therefore, the system cannot definitively identify any particular user or group. |
If you're setting up ISE/ISE-PIC without a realm, be aware there is a user session timeout that affects how users are seen by the Secure Firewall Management Center. For more information, see Realm Fields.
If you're using Kerberos authentication for captive portal, see the following section before you begin: Prerequisites for Kerberos Authentication.
 Note |
Microsoft Azure Active Directory is not supported for captive portal. |
 Important |
To reduce latency between the Secure Firewall Management Center and your Active Directory domain controller, we strongly recommend you configure a realm directory (that is, domain controller) that is as close as possible geographically to the Secure Firewall Management Center. For example, if your Secure Firewall Management Center is in North America, configure a realm directory that is also in North America. Failure to do so can cause problems such as timeout downloading users and groups. |
|
Step 1 |
Log in to the Secure Firewall Management Center. |
||||||||||||
|
Step 2 |
Click . |
||||||||||||
|
Step 3 |
To create a new realm, choose from Add Realm drop-down list. |
||||||||||||
|
Step 4 |
To perform other tasks (such as enable, disable, or delete a realm), see Manage a Realm. |
||||||||||||
|
Step 5 |
Enter realm information as discussed in Realm Fields. |
||||||||||||
|
Step 6 |
In the Directory Server Configuration section, enter directory information as discussed in Realm Directory and Synchronize fields. |
||||||||||||
|
Step 7 |
(Optional.) To configure another domain for this realm, click Add another directory. |
||||||||||||
|
Step 8 |
Click Configure Groups and Users.
|
||||||||||||
|
Step 9 |
Click the Realm Configuration tab. |
||||||||||||
|
Step 10 |
Enter Group Attribute, and (if you use Kerberos authentication for captive portal) enter AD Join Username and AD Join Password. For more information, see Realm Directory and Synchronize fields. |
||||||||||||
|
Step 11 |
If you use Kerberos authentication, click Test. If the test fails, wait a short time and try again. |
||||||||||||
|
Step 12 |
Enter user session timeout values, in minutes, for ISE/ISE-PIC Users, Terminal Server Agent Users, Captive Portal Users, Failed Captive Portal Users, and Guest Captive Portal Users. |
||||||||||||
|
Step 13 |
When you're finished configuring the realm, click Save. |
Configure the Management Center for Cross-Domain-Trust: The Setup
Edit, delete, enable, or disable a realm; see Manage a Realm.
Optionally, monitor the task status; see Viewing Task Messages in the Cisco Secure Firewall Management Center Administration Guide.
Realms are connections between the Secure Firewall Management Center and the user accounts on the servers you monitor. They specify the connection settings and authentication filter settings for the server. Realms can:
Specify the users and user groups whose activity you want to monitor.
Query the user repository for user metadata on authoritative users, as well as some non-authoritative users: POP3 and IMAP users detected by traffic-based detection and users detected by traffic-based detection, a TS Agent, or ISE/ISE-PIC.
(Microsoft AD realm only.) A realm sequence is an ordered list of two or more Active Directory realms to use in identity policy. When you associate a realm sequence with an identity rule, the system searches the Active Directory domains in order from first to last as specified in the realm sequence.
You can add multiple domain controllers as directories in a realm, but they must share the same basic realm information. The directories in a realm must be exclusively LDAP or exclusively Active Directory (AD) servers. After you enable a realm, your saved changes take effect next time the Secure Firewall Management Center queries the server.
To perform user awareness, you must configure a realm for any of the supported server types. The system uses these connections to query the servers for data associated with POP3 and IMAP users, and to collect data about LDAP users discovered through traffic-based detection.
The system uses the email addresses in POP3 and IMAP logins to correlate with LDAP users on an Active Directory, Microsoft Azure Active Directory, or OpenLDAP. For example, if a managed device detects a POP3 login for a user with the same email address as an LDAP user, the system associates the LDAP user’s metadata with that user.
To perform user control, you can configure any of the following:
A realm or realm sequence for an Active Directory, Microsoft Azure Active Directory, server, or for ISE/ISE-PIC
 Note |
Configuring a Microsoft AD realm or realm sequence is optional if you plan to configure SGT ISE attribute conditions but not user, group, realm, Endpoint Location, or Endpoint Profile conditions; or if you use your identity policy only to filter network traffic. Realm sequence is not available for Microsoft Azure AD realms. |
A realm or realm sequence for a Microsoft AD server for the TS Agent.
For captive portal, an LDAP realm.
A realm sequence is not supported for LDAP.
You can nest Microsoft AD groups and the Secure Firewall Management Center downloads those groups and the users they contain. You can optionally restrict which groups and users get downloaded as discussed in Create an LDAP Realm or an Active Directory Realm and Realm Directory.
You can configure a realm or realm sequence to establish a connection between the management center and an LDAP or Microsoft AD server to retrieve user and user group metadata for certain detected users:
LDAP and Microsoft AD users authenticated by captive portal or reported by ISE/ISE-PIC. This metadata can be used for user awareness and user control.
POP3 and IMAP user logins detected by traffic-based detection, if those users have the same email address as an LDAP or AD user. This metadata can be used for user awareness.
The management center obtains the following information and metadata about each user:
LDAP user name
First and last names
Email address
Department
Telephone number
 Important |
To reduce latency between the Secure Firewall Management Center and your Active Directory domain controller, we strongly recommend you configure a realm directory (that is, domain controller) that is as close as possible geographically to the Secure Firewall Management Center. For example, if your Secure Firewall Management Center is in North America, configure a realm directory that is also in North America. Failure to do so can cause problems such as timeout downloading users and groups. |
User activity data is stored in the user activity database and user identity data is stored in the users database. The maximum number of users you can store and use in access control depends on your management center model. When choosing which users and groups to include, make sure the total number of users is less than your model limit. If your access control parameters are too broad, the management center obtains information on as many users as it can and reports the number of users it failed to retrieve in the Tasks tab page of the Message Center.
To optionally limit the subnets on which a managed device watches for user awareness data, you can use the configure identity-subnet-filter command as discussed in the Cisco Secure Firewall Threat Defense Command Reference.
 Note |
If you remove a user that has been detected by the system from your user repository, the management center does not remove that user from its users database; you must manually delete it. However, your LDAP changes are reflected in access control rules when the management center next updates its list of authoritative users. |
When you configure a Microsoft Active Directory (AD) realm in the management center, it is associated with a Microsoft Active Directory or LDAP domain.
A grouping of Microsoft Active Directory (AD) domains that trust each other is commonly referred to as a forest. This trust relationship can enable domains to access each other's resources in different ways. For example, a user account defined in domain A can be marked as a member of a group defined in domain B.
 Note |
Trusted domains apply to Microsoft Active Directory domains only. They do not apply to either Microsoft Azure Active Directory or LDAP domains. |
The system supports AD forests that are configured in a trust relationship. There are several types of trust relationships; this guide discusses two-way, transitive forest trust relationships. The following simple example shows two forests: forest.example.com and eastforest.example.com . Users and groups in each forest can be authenticated by AD in the other forest, provided you configure the forests that way.
If you set up the system with one realm for each domain and one directory for each domain controller, the system can discover up to 100,000 foreign security principals (users and groups). If these foreign security principals match a user downloaded in another realm, then they can be used in access control policy.
You need not configure a realm for any domain that has no users you wish to use in access control policies.

To continue the example, suppose you have three AD forests (one of which could be a subdomain or an independent forest), all set up as two-way transitive forest relationships, all users and groups are available in all three forests as well as in the system. (As in the preceding example, all three AD domains must be set up as realms and all domain controllers must be configured as directories in those realms.)

Finally, you can set up the management center to be able to enforce identity policies on users and groups in a two-forest system with two-way transitive forest trust. Suppose each forest has at least one domain controller, each of which authenticates different users and groups. For the management center to be able to enforce identity policies on those users and groups, you must set up each domain containing relevant users as management center realm and each domain controller as management center directory in the respective realm.
Failure to properly configure the management center prevents some of the users and groups from being able to be used in policies. You will see warnings when you try to synchronize users and groups in that case.

Using the preceding example, set up the management center as follows:
Realm for any domain in forest.example.com that contains users you want to control with access control policies
Directory in the realm for AMERICAS.forest.example.com
Directory in the realm for ASIA.forest.example.com
Realm for any domain in eastforest.example.com that contains users you want to control with access control policies
Directory in the realm for EUROPE.eastforest.example.com
 Note |
The management center uses the AD field msDS-PrincipalName to resolve references to find user and group names in each domain controller. msDS-PrincipalName returns a NetBIOS name. |
You can configure realms to connect to the following types of servers, providing they have TCP/IP access from the management center:
|
Server Type |
Supported for ISE/ISE-PIC data retrieval? |
Supported for TS Agent data retrieval? |
Supported for captive portal data retrieval? |
|---|---|---|---|
|
Microsoft Active Directory on Windows Server 2012, 2016, and 2019 |
Yes |
Yes |
Yes |
|
Microsoft Azure AD |
Yes |
No |
No |
|
OpenLDAP on Linux |
No |
No |
Yes |
An Active Directory Global Catalog server is not supported as a realm directory. For more information about the Global Catalog Server, see Global Catalog on learn.microsoft.com.
 Note |
If the TS Agent is installed on a Microsoft Active Directory Windows Server shared with another passive authentication identity source (ISE/ISE-PIC), the management center prioritizes the TS Agent data. If the TS Agent and a passive identity source report activity by the same IP address, only the TS Agent data is logged to the management center. |
Note the following about your server group configurations:
To perform user control on user groups or on users in groups, you must configure user groups on the LDAP or Active Directory server.
Group names cannot start with S- because it is used internally by LDAP.
Neither group names nor organizational unit names can contain special characters like
asterisk (*), equals (=), or backslash
(\); otherwise, users in those groups or organizational
units are not downloaded and are not available for identity policies.
If necessary, you can modify your Active Directory server configuration to increase this default limit and accommodate more users.
To uniquely identify the users reported by a server in your Remote Desktop Services environment, you must configure the Cisco Terminal Services (TS) Agent. When installed and configured, the TS Agent assigns unique ports to individual users so the system can uniquely identify those users. (Microsoft changed the name Terminal Services to Remote Desktop Services.)
For more information about the TS Agent, see the Cisco Terminal Services (TS) Agent Guide.
The servers in your realms must use the attribute names listed in the following table for the Secure Firewall Management Center to retrieve user metadata from the servers. If the attribute names are incorrect on your server, the Secure Firewall Management Center cannot populate its database with the information in that attribute.
|
Metadata |
Management Center Attribute |
LDAP ObjectClass |
Active Directory Attribute |
OpenLDAP Attribute |
|---|---|---|---|---|
|
LDAP user name |
Username |
|
samaccountname |
cn uid |
|
first name |
First Name |
givenname |
givenname |
|
|
last name |
Last Name |
sn |
sn |
|
|
email address |
|
userprincipalname (if mail has no value) |
|
|
|
department |
Department |
department distinguishedname (if department has no value) |
ou |
|
|
telephone number |
Phone |
telephonenumber |
telephonenumber |
 Note |
The LDAP ObjectClass for groups is group, groupOfNames, (group-of-names for Active Directory) or groupOfUniqueNames. |
For more information about ObjectClasses and attributes, see the following references:
If you're using Kerberos to authentication captive portal users, keep the following in mind.
If you're using Kerberos authentication, the managed device's host name must be less than 15 characters (it's a NetBIOS limitation set by Windows); otherwise, captive portal authentication fails. You set the managed device host name when you set up the device. For more information, see an article like this one on the Microsoft documentation site: Naming conventions in Active Directory for computers, domains, sites, and OUs.
DNS must return a response of 64KB or less to the hostname; otherwise, the AD connection test fails. This limit applies in both directions and is discussed in RFC 6891 section-6.2.5.
The following fields are used to configure a realm.
These settings apply to all Active Directory servers or domain controllers (also referred to as directories) in a realm.
A unique name for the realm.
To use the realm in identity policies, the system supports alphanumeric and special characters.
To use the realm in RA VPN configurations, the system supports alphanumeric, hyphen (-), underscore (_), and plus (+) characters.
The type of realm, AD for Microsoft Active Directory, LDAP for other supported LDAP repositories, or Local. For a list of supported LDAP repositories, see Supported Servers for Realms. You can authenticate captive portal users with an LDAP repository; all others require Active Directory.
 Note |
Only captive portal supports an LDAP realm. |
For Microsoft Active Directory realms only. Domain for the Active Directory server where users should be authenticated.
 Note |
You must specify a unique AD Primary Domain for every Microsoft Active Directory (AD) realm. Although the system allows you to specify the same AD Primary Domain for different Microsoft AD realms, the system won't function properly. This happens because system assigns a unique ID to every user and group in each realm; therefore, the system cannot definitively identify any particular user or group. The system prevents you from specifying more than one realm with the same AD Primary Domain because users and groups won't be identified properly. This happens because system assigns a unique ID to every user and group in each realm; therefore, the system cannot definitively identify any particular user or group. |
The distinguished username and password for a user with appropriate access to the user information you want to retrieve.
Note the following:
For some versions of Microsoft Active Directory, specific permissions might be required to read users and groups. Consult the documentation provided with Microsoft Active Directory for details.
For OpenLDAP, the user's access privileges are determined by the <level> parameter discussed in section 8 of the OpenLDAP specification. The user's <level> should be auth or better.
The user name must be fully qualified (for example, administrator@mydomain.com, not administrator).
 Note |
The SHA-1 hash algorithm is not secure for storing passwords on your Active Directory server and should not be used. For more information, consult a reference such as Migrating your Certification Authority Hashing Algorithm from SHA1 to SHA2 on Microsoft TechNet or Password Storage Cheat Sheet on the Open Web Application Security Project website. We recommend SHA-256 for communicating with Active Directory. |
(Optional.) The directory tree on the server where the Secure Firewall Management Center should begin searching for user data. If you don't specify a Base DN, the system retrieves the top-level DN provided you can connect to the server.
Typically, the base distinguished name (DN) has a basic structure indicating the company domain name and operational unit. For example, the Security organization of the Example company might have a base DN of ou=security,dc=example,dc=com.
(Optional.) The directory tree on the server where the Secure Firewall Management Center should search for users with the group attribute. A list of supported group attributes is shown in Supported Server Object Class and Attribute Names. If you don't specify a Group DN, the system retrieves the top-level DN provided you can connect to the server.
 Note |
Following is the list of characters the system supports in users, groups, DNs in your directory server. Using any characters other than the following could result in the system failing to download users and groups.
A space is not supported anywhere in a user name, including at the end. |
The following fields are available when you edit an existing realm.
These settings apply to individual servers (such as Active Directory domain controllers) in a realm.
If you're using Kerberos for authenticating captive portal, also make sure you understand the following:
If you're using Kerberos authentication, the managed device's host name must be less than 15 characters (it's a NetBIOS limitation set by Windows); otherwise, captive portal authentication fails. You set the managed device host name when you set up the device. For more information, see an article like this one on the Microsoft documentation site: Naming conventions in Active Directory for computers, domains, sites, and OUs.
DNS must return a response of 64KB or less to the hostname; otherwise, the AD connection test fails. This limit applies in both directions and is discussed in RFC 6891 section-6.2.5.
The server's port.
(Strongly recommended.) The encryption method to use:
STARTTLS—encrypted LDAP connection
LDAPS—encrypted LDAP connection
None—unencrypted LDAP connection (unsecured traffic)
To communicate securely with an Active Directory server, see Connect Securely to Active Directory.
The TLS/SSL certificate to use for authentication to the server. You must configure STARTTLS or LDAPS as the Encryption type to use a TLS/SSL certificate.
If you are using a certificate to authenticate, the name of the server in the certificate must match the server Hostname / IP Address. For example, if you use 10.10.10.250 as the IP address but computer1.example.com in the certificate, the connection fails.
You can choose only a routed interface group. For more information, see Interface.
Click one of the following:Resolve via route lookup: Use routing to connect to the Active Directory server.
Choose an interface: Choose a specific managed device interface group to connect to the Active Directory server.
For Microsoft Active Directory realms only. Domain for the Active Directory server where users should be authenticated.
 Note |
You must specify a unique AD Primary Domain for every Microsoft Active Directory (AD) realm. Although the system allows you to specify the same AD Primary Domain for different Microsoft AD realms, the system won't function properly. This happens because system assigns a unique ID to every user and group in each realm; therefore, the system cannot definitively identify any particular user or group. The system prevents you from specifying more than one realm with the same AD Primary Domain because users and groups won't be identified properly. This happens because system assigns a unique ID to every user and group in each realm; therefore, the system cannot definitively identify any particular user or group. |
Base DN:
(Optional.) The directory tree on the server where the management center should begin searching for user data.
Typically, the base distinguished name (DN) has a basic structure indicating the company domain name and operational unit. For example, the Security organization of the Example company might have a base DN of ou=security,dc=example,dc=com.
Enables you to download users and groups for user awareness and user control.
Limits the groups that can be used in policy.
Groups that are displayed in the Available Groups field are available for policy unless you move groups to the Included Groups and Users or Excluded Groups and Users field.
If you move groups to the Included Groups and Users field, only those groups and users they contain are downloaded and user data is available for user awareness and user control.
If you move groups to the Excluded Groups and Users field, all groups and users they contain except these are downloaded and available for user awareness and user control.
To include users from groups that are not included, enter the user name in the field below User Inclusion and click Add.
To exclude users from groups that are not excluded, enter the user name in the field below User Exclusion and click Add.
 Note |
The users that are downloaded to the management center is calculated using the formula R = I - (E+e) + i , where
|
To create a secure connection between an Active Directory server and the management center (which we strongly recommend), you must perform all of the following tasks:
Export the Active Directory server's root certificate.
Import the root certificate into the management center as a trusted CA certificate ).
Find the Active Directory server's fully qualified name.
Create the realm directory.
See one of the following tasks for more information.
To configure a realm directory in the management center, you must know the fully qualified server name, which you can find as discussed in the procedure that follows.
You must log in to the Active Directory server as a user with sufficient privileges to view the computer's name.
|
Step 1 |
Log in to the Active Directory server. |
|
Step 2 |
Click Start. |
|
Step 3 |
Right-click This PC. |
|
Step 4 |
Click Properties. |
|
Step 5 |
Click Advanced System Settings. |
|
Step 6 |
Click the Computer Name tab. |
|
Step 7 |
Note the value of Full computer name. |
The task that follows discusses how to export the Active Directory server's root certificate, which is required to connect securely to the management center to obtain user identity information.
You must know the name of your Active Directory server's root certificate. The root certificate might have the same name as the domain or the certificate might have a different name. The procedure that follows shows one way you can find the name; there could be other ways, however.
|
Step 1 |
Following is one way to find the name of the Active Directory Server's root certificate; consult Microsoft documentation for more information: |
|
Step 2 |
Export the certificate using the certutil command. This is only one way to export the certificate. It's a convenient way to export the certificate, especially if you can run a web browser and connect to the management center from the Active Directory server. |
Synchronizing users and groups means the management center queries the realms and directories you configured for groups and users in those groups. All users the management center finds can be used in identity policies.
If issues are found, you most likely need to add a realm that contains users and groups the management center cannot load. For details, see Realms and Trusted Domains.
Create a Secure Firewall Management Center realm for each Active Directory domain and a management center directory for each Active Director domain controller in each forest. See Create an LDAP Realm or an Active Directory Realm and Realm Directory.
 Note |
Synchronizing users and groups is not necessary for Microsoft Azure AD realms. |
You must create a realm only for domains that have users you want to use in user control.
You can nest Microsoft AD groups and the Secure Firewall Management Center downloads those groups and the users they contain. You can optionally restrict which groups and users get downloaded as discussed in Create an LDAP Realm or an Active Directory Realm and Realm Directory.
You must create the realm with the original domain name of the domain and not any alternative user principal name (UPN) suffixes
of the domain. Otherwise, users and groups fail to download and identity policies will not be enforced. For example, if the
original domain is domain.example.com and the alternative UPN name isdomain2.mydomain.com, you must configure the realm to use domain.example.com. For more information about configuring an alternative UPN suffix, see a resource like Configuring Alternate Login ID on learn.microsoft.com.
|
Step 1 |
Log in to the Secure Firewall Management Center if you have not already done so. |
||||||
|
Step 2 |
Click . |
||||||
|
Step 3 |
Next to each realm, click Download ( |
||||||
|
Step 4 |
To see the results, click the Sync Results tab.
|
The following procedure enables you to create a realm sequence, which is an ordered list of realms the system searches when it applies identity policy. You add a realm sequence to an identity rule exactly the same way as you add a realm; the difference is that the system searches all the realms in the order specified in the realm sequence when applying an identity policy.
You must create and enable at least two realms, each corresponding to a connection with an Active Directory server. You cannot create realm sequences for LDAP realms.
Create a realm as discussed in Create an LDAP Realm or an Active Directory Realm and Realm Directory.
|
Step 1 |
Log in to the Secure Firewall Management Center if you have not already done so. |
|
Step 2 |
Click . |
|
Step 3 |
Click the Realm Sequences tab. |
|
Step 4 |
Click Add Sequence. |
|
Step 5 |
In the Name field, enter a name to identify the realm sequence. |
|
Step 6 |
(Optional.) In the Description field, enter a description for the realm sequence. |
|
Step 7 |
Under Realms, click Add ( |
|
Step 8 |
Click the name of each realm to add to the sequence. To narrow your search, enter all or part of a realm name in Filter field. |
|
Step 9 |
Click OK. |
|
Step 10 |
In the Add Realm Sequence dialog box, drag and drop the realms in the order in which you want the system to search for them.
|
|
Step 11 |
Click Save. |
This is an introduction to several topics that walk you through configuring the management center with two realms with cross-domain trust.
This step-by-step example involves two forests: forest.example.com and eastforest.example.com . The forests are configured so that certain users and groups in each forest can be authenticated by Microsoft AD in the other forest.
 Note |
This topic applies to Microsoft AD realms only. It does not apply to Microsoft Azure AD realms. |
Following is the example setup used in this example.

Using the preceding example, you would set up the management center as follows:
Realm and directory for any domain in forest.example.com that contains users you want to control with access control policy
Realm and directory for any domain in eastforest.example.com that contains users you want to control with access control policy
Each realm in the example has one domain controller, which is configured in the management center as a directory. The directories in this example are configured as follows:
forest.example.com
Base distinguished name (DN) for users: ou=UsersWest,dc=forest,dc=example,dc=com
Base DN for groups: ou=EngineringWest,dc=forest,dc=example,dc=com
eastforest.example.com
Base DN for users: ou=EastUsers,dc=eastforest,dc=example,dc=com
Base DN for groups: ou=EastEngineering,dc=eastforest,dc=example,dc=com
This is the first task in a step-by-step procedure that explains how to configure the management center to recognize Active Directory servers configured in a cross-domain trust relationship, which is an increasingly common configuration for enterprise organizations. For an overview of this sample configuration, see Configure the Management Center for Cross-Domain-Trust: The Setup.
If you set up the system with one realm for each domain and one directory for each domain controller, the system can discover up to 100,000 foreign security principals (users and groups). If these foreign security principals match a user downloaded in another realm, then they can be used in access control policy.
You must configure Microsoft Active Directory servers in a cross-domain trust relationship; see Realms and Trusted Domains for more information.
If you authenticate users with LDAP or Microsoft Azure AD, you cannot use this procedure.
|
Step 1 |
Log in to the Secure Firewall Management Center if you have not already done so. |
||
|
Step 2 |
Click . |
||
|
Step 3 |
Click . |
||
|
Step 4 |
Enter the following information to configure forest.example.com .
|
||
|
Step 5 |
Click Test and make sure the test succeeds before you continue. |
||
|
Step 6 |
Click Configure Groups and Users. |
||
|
Step 7 |
If your configuration was successful, the next page is displayed similar to the following.
|
||
|
Step 8 |
If you made changes on this page or tab pages, click Save. |
||
|
Step 9 |
Click . |
||
|
Step 10 |
Click Add Realm. |
||
|
Step 11 |
Enter the following information to configure eastforest.example.com .
|
||
|
Step 12 |
Click Test and make sure the test succeeds before you continue. |
||
|
Step 13 |
Click Configure Groups and Users. |
||
|
Step 14 |
If your configuration was successful, the next page is displayed similar to the following.
|
After you configure two or more Active Directory servers that have a cross-domain trust relationship, you must download users and groups. That process exposes possible issues with the Active Directory configuration (for example, groups or users downloaded for one Active Directory domain but not the other).
Make sure you have performed the tasks discussed in Configure the Secure Firewall Management Center for Cross-Domain-Trust Step 1: Configure Realms and Directories.
|
Step 1 |
Log in to the Secure Firewall Management Center if you have not already done so. |
|
Step 2 |
Click . |
|
Step 3 |
At the end of the row of any realm in the cross-domain trust, click Download Now( |
|
Step 4 |
Click Check Mark ( If groups and users fail to download, try again. If subsequent attempts fail, review your realm and directory setup as discussed in Realm Fields and Realm Directory and Synchronize fields. |
|
Step 5 |
Click . |
The final step in setting up cross-domain trust in the management center is to make sure users and groups are downloaded without errors. A typical reason why users and groups do not download properly is that the realms to which they belong have not been downloaded to the management center.
This topic discusses how to diagnose that a group referred in one forest to cannot be downloaded because the realm is not configured to find the group in the domain controller hierarchy.
|
Step 1 |
Log in to the Secure Firewall Management Center if you have not already done so. |
|
Step 2 |
Click . In the Realms column, if Yellow Triangle ( |
|
Step 3 |
Download users and groups again from the realms that display issues.
|
|
Step 4 |
Click the Sync Results tab page.  ) is displayed in the Realms column, click Yellow Triangle ( ) is displayed in the Realms column, click Yellow Triangle ( ) next to the realm that has issues. ) next to the realm that has issues.
|
|
Step 5 |
In the middle column, click either Groups or Users to find more information. |
|
Step 6 |
In the Groups or Users tab page, click Yellow Triangle ( The right column should display enough information you can isolate the source of the issue.
In the preceding example, forest.example.com includes a cross-domain group CrossForestInvalidGroup that contains another group EastMarketingUsers that was not downloaded by the management center. If, after synchronizing the eastforest.example.com realm again, the error does not resolve, it likely means that the Active Directory domain controller does not include EastMarketingUsers . To resolve this issue, you can:
|
This section discusses how to perform various maintenance tasks for a realm using controls on the Realms page:
If the controls are dimmed, the configuration belongs to an ancestor domain, or you do not have permission to modify the
configuration.. If View ( ) appears instead, the configuration belongs to an ancestor domain, or you do not have permission to modify the configuration.
) appears instead, the configuration belongs to an ancestor domain, or you do not have permission to modify the configuration.
|
Step 1 |
Log in to the Secure Firewall Management Center if you have not already done so. |
|
Step 2 |
Click . |
|
Step 3 |
To delete a realm, click Delete ( |
|
Step 4 |
To edit a realm, click Edit ( |
|
Step 5 |
To enable a realm, slide State to the right; to disable a realm, slide it to the left. |
|
Step 6 |
To download users and user groups, click Download ( |
|
Step 7 |
To copy a realm, click Copy ( |
|
Step 8 |
To compare realms, see Compare Realms. |
You must be an Admin, Access Admin, Network Admin, or Security Approver to perform this task.
|
Step 1 |
Log in to the Secure Firewall Management Center if you have not already done so. |
|
Step 2 |
Click . |
|
Step 3 |
Click Compare Realms. |
|
Step 4 |
Choose Compare Realm from the Compare Against list. |
|
Step 5 |
Choose the realms you want to compare from the Realm A and Realm B lists. |
|
Step 6 |
Click OK. |
|
Step 7 |
To navigate individually through changes, click Previous or Next above the title bar. |
|
Step 8 |
(Optional.) Click Comparison Report to generate the realm comparison report. |
|
Step 9 |
(Optional.) Click New Comparison to generate a new realm comparison view. |
If you notice unexpected server connection behavior, consider tuning your realm configuration, device settings, or server settings. For other related troubleshooting information, see:
The Secure Firewall Management Center's health monitor informs you of user or realm mismatches, which are defined as:
User mismatch: A user is reported to the Secure Firewall Management Center without being downloaded.
A typical reason for a user mismatch is that the user belongs to a group you have excluded from being downloaded to the Secure Firewall Management Center. Review the information discussed in Cisco Secure Firewall Management Center Device Configuration Guide.
Realm mismatch: A user logs into a domain that corresponds to a realm not known to the management center.
For example, if you defined a realm that corresponds to a domain named domain.example.com in the management center but a login is reported from a domain named another-domain.example.com , this is a realm mismatch. Users in this domain are identified by the management center as Unknown.
You set the mismatch threshold as a percentage, above which a health warning is triggered. Examples:
If you use the default mismatch threshold of 50%, and there are two mismatched realms in eight incoming sessions, the mismatch percentage is 25% and no warning is triggered.
If you set the mismatch threshold to 30% and there are three mismatched realms in five incoming sessions, the mismatch percentage is 60% and a warning is triggered.
Unknown users that do not match identity rules have no policies applied to them. (Although you can set up identity rules for Unknown users, we recommend keeping the number of rules to a minimum by identifying users and realms correctly.)
For more information, see Detect Realm or User Mismatches.
Possible causes follow:
If you have the realm Type configured incorrectly, users and groups cannot be downloaded because of a mismatch between the attribute the system expects
and what the repository provides. For example, if you configure Type as LDAP for a Microsoft Active Directory realm, the system expects the uid attribute, which is set to none on Active Directory. (Active Directory repositories use sAMAccountName for the user ID.)
Solution: Set the realm Type field appropriately: AD for Microsoft Active Directory or LDAP for another supported LDAP repository.
Users in Active Directory groups that have special characters in the group or organizational unit name might not be available
for identity policy rules. For example, if a group or organizational unit name contains the characters asterisk (*), equals (=), or backslash (\), users in those groups are not downloaded and can't be used for identity policies.
Solution: Remove special characters from the group or organizational unit name.
 Important |
To reduce latency between the Secure Firewall Management Center and your Active Directory domain controller, we strongly recommend you configure a realm directory (that is, domain controller) that is as close as possible geographically to the Secure Firewall Management Center. For example, if your Secure Firewall Management Center is in North America, configure a realm directory that is also in North America. Failure to do so can cause problems such as timeout downloading users and groups. |
Possible causes follow:
If you attempt to download more than the maximum number of users in any one realm, the download stops at the maximum number of users and a health alert is displayed. User download limits are set per Secure Firewall Management Center model. For more information, see User Limits for Microsoft Active Directory.
Every user must be a member of a group. Users that are members of no groups do not get downloaded.
This solution applies to an AD domain that is in a trust relationship with other AD domains. In the following discussion, external domain means a domain other than the one to which the user logs in.
If a user belongs to a group defined in a trusted external domain, the Secure Firewall Management Center doesn't track membership in the external domain. For example, consider the following scenario:
Domain controllers 1 and 2 trust each other
Group A is defined on domain controller 2
User mparvinder in controller 1 is a member of Group A
Even though user mparvinder is in Group A, the Secure Firewall Management Center access control policy rules specifying membership Group A don't match.
Solution: Create a similar group in domain controller 1 that contains has all domain 1 accounts that belong to group A. Change the access control policy rule to match any member of Group A or Group B.
If a user belongs to a domain that is child of parent domain, Firepower doesn't track the parent/child relationships between domains. For example, consider the following scenario:
Domain child.parent.com is child of domain parent.com
User mparvinder is defined in child.parent.com
Even though user mparvinder is in a child domain, the Firepower access control policy matching the parent.com don't match mparvinder in the child.parent.com domain.
Solution: Change the access control policy rule to match membership in either parent.com or child.parent.com.
The Test button on the directory page sends an LDAP query to the hostname or IP address you entered. If it fails, check the following:
The Hostname you entered resolves to the IP address of an LDAP server or Active Directory domain controller.
The IP Address you entered is valid.
The Test AD Join button on the realm configuration page verifies the following:
DNS resolves the AD Primary Domain to an LDAP server or Active Directory domain controller’s IP address.
The AD Join Username and AD Join Password are correct.
AD Join Username must be fully qualified (for example, administrator@mydomain.com, not administrator).
The user has sufficient privileges to create a computer in the domain and join the Secure Firewall Management Center to the domain as a Domain Computer.
If you notice the system performing user timeouts at unexpected intervals, confirm that the time on your ISE/ISE-PIC server is synchronized with the time on the Secure Firewall Management Center. If the appliances are not synchronized, the system may perform user timeouts at unexpected intervals.
If you notice the system performing user timeouts at unexpected intervals, confirm that the time on your ISE/ISE-PIC, or TS Agent server is synchronized with the time on the Secure Firewall Management Center. If the appliances are not synchronized, the system may perform user timeouts at unexpected intervals.
After the system detects activity from an ISE/ISE-PIC or TS Agent user whose data is not yet in the database, the system retrieves information about them from the server. In some cases, the system requires additional time to successfully retrieve this information from Microsoft Windows servers. Until the data retrieval succeeds, activity seen by the ISE/ISE-PIC, or TS Agent user is not displayed in the web interface.
Note that this can also prevent the system from handling the user's traffic using access control rules.
If you notice user or user activity events contain unexpected IP addresses, check your realms. The system does not support configuring multiple realms with the same AD Primary Domain value.
If your deployment includes a terminal server and you have a realm configured for one or more servers connected to the terminal server, you must deploy the Cisco Terminal Services (TS) Agent to accurately report user logins in terminal server environments. When installed and configured, the TS Agent assigns unique ports to individual users so the system can uniquely identify those users in the web interface.
For more information about the TS Agent, see the Cisco Terminal Services (TS) Agent Guide.
This section discusses how to detect realm or user mismatches, which are defined as:
User mismatch: A user is reported to the Secure Firewall Management Center without being downloaded.
A typical reason for a user mismatch is that the user belongs to a group you have excluded from being downloaded to the Secure Firewall Management Center. Review the information discussed in Cisco Secure Firewall Management Center Device Configuration Guide.
Realm mismatch: A user logs into a domain that corresponds to a realm not known to the management center.
For additional details, see Troubleshoot Realms and User Downloads.
Unknown users that do not match identity rules have no policies applied to them. (Although you can set up identity rules for Unknown users, we recommend keeping the number of rules to a minimum by identifying users and realms correctly.)
|
Step 1 |
Enable detection of realm or user mismatches: |
|
Step 2 |
View user and realm mismatches in any of the following ways:
|
|
Step 3 |
On the Health Monitor page, in the Display column, expand Realm: Domain or Realm: User to view details about the mismatch. |
Typical issues with troubleshooting the management center configuration for cross-domain trust include the following:
Not adding realms or directories for all forests that have shared groups.
Configure a realm to exclude users from being downloaded and those users are referenced in a group in a different realm.
Certain temporary issues.
If there are issues with the management center being able to synchronize users and groups with your Active Directory forests, the Sync Results tab page is displayed similar to the following.

The following table explains how to interpret the information.
|
Column |
Meaning |
|---|---|
|
Realms |
Displays all realms configured in the system. Click Refresh ( Yellow Triangle ( Nothing is displayed next to a realm if all users and groups synchronized successfully. |
|
Groups |
Click Groups to display all groups in the realm. As with realms, Yellow Triangle ( Click Yellow Triangle ( |
|
Users |
Click Users to display all users, sorted by group. |
|
Users contained in the selected group |
Displays all users in the group you selected in the Groups column. Clicking Yellow Triangle ( |
|
Groups that contain selected user |
Displays all groups the selected user belongs to. Clicking Yellow Triangle ( |
|
Error detail information (displayed to the right of the table). |
The system displays the NetBIOS forest name and group name it could not synchronize. Typical reasons the system cannot synchronize these users and groups follow:
|
If there is a possibility the issues are temporary, download users and groups for all realms.
If you haven't done so already, log in to the management center.
Click .
Click Download ( ).
).
Click the Sync Results tab page.
If no indicator is displayed for entries in the Realms column, the issues have been resolved.
Make sure you configured:
management center realm for each forest that has users you want to use in identity policies.
management center directory for each domain controller in that forest with users you want to use in identity polices.
The following figure shows an example.

|
Feature |
Minimum Management Center |
Minimum Threat Defense |
Details |
|---|---|---|---|
|
Microsoft Azure Active Directory (AD) realms. |
7.4.0 |
7.4.0 |
You can use a Microsoft Azure Active Directory (AD) realm with ISE to authenticate users and get user sessions for user control. New/modified screens: System( |
|
Proxy sequences. |
7.2.0 |
7.2.0 |
Similar to a realm sequence, a proxy sequence is one or more managed devices that can communicate with Cisco Defense Orchestrator in the event Cisco Defense Orchestrator cannot communicate with the LDAP or Active Directory server. New/modified screens: |
|
Cross-domain trust for Active Directory domains. |
7.2.0 |
7.0.0 |
A grouping of Microsoft Active Directory (AD) domains that trust each other is commonly referred to as a forest. This trust relationship can enable domains to access each other's resources in different ways. For example, a user account defined in domain A can be marked as a member of a group defined in domain B. The management center can get users from Active Directory forests for identity rules. |
|
Realm sequences. |
7.2.0 |
6.7.0 |
A realm sequence is an ordered list of two or more realms to which to apply identity rules. When you associate a realm sequence with an identity policy, the Firepower System searches the Active Directory domains in order from first to last as specified in the realm sequence. New/modified screens: |
|
Realms for user control. |
7.2.0 |
Any |
A realm is a connection between the management center either an Active Directory or LDAP user repository. |