Why Use NAT?
Each computer and device within an IP network is assigned a unique IP address that identifies the host. Because of a shortage of public IPv4 addresses, most of these IP addresses are private, not routable anywhere outside of the private company network. RFC 1918 defines the private IP addresses you can use internally that should not be advertised:
-
10.0.0.0 through 10.255.255.255
-
172.16.0.0 through 172.31.255.255
-
192.168.0.0 through 192.168.255.255
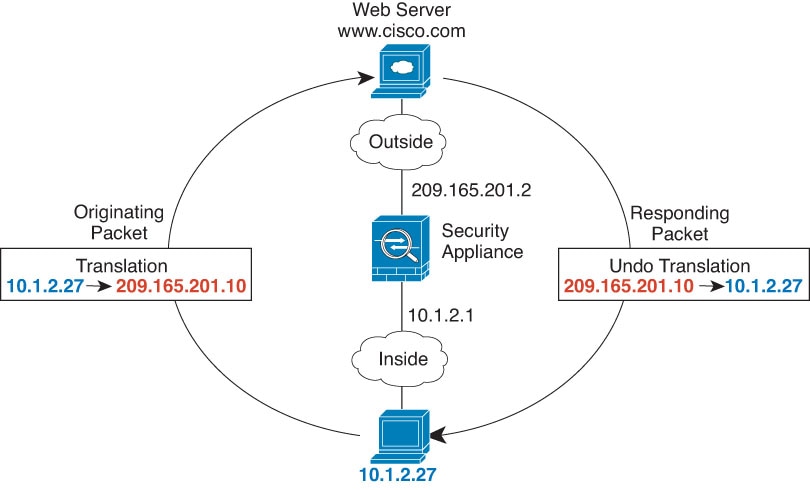
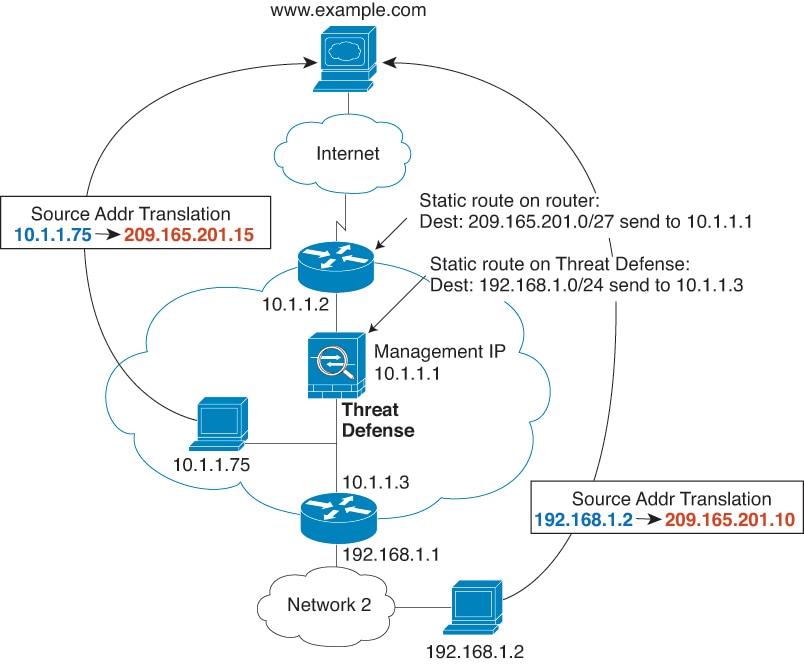
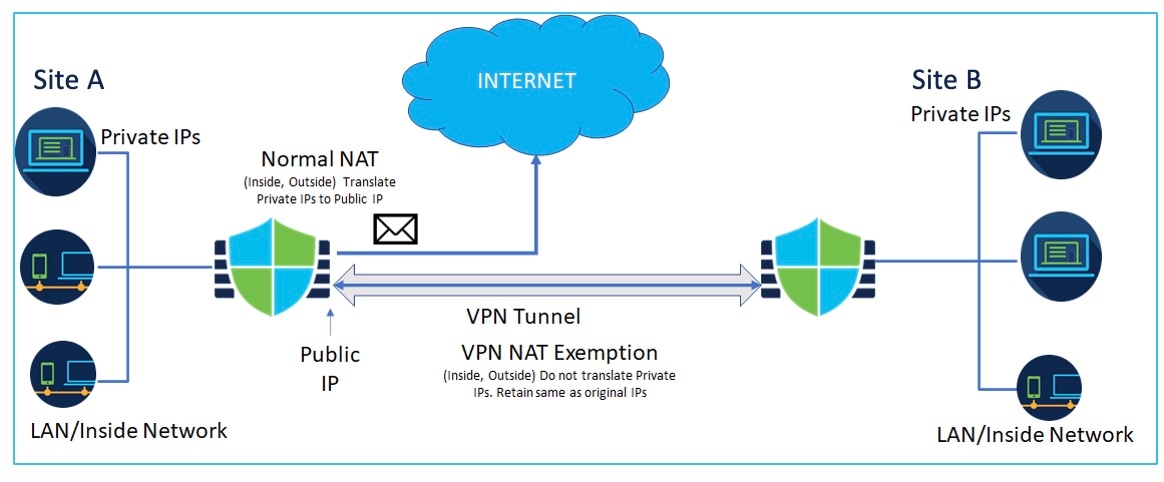
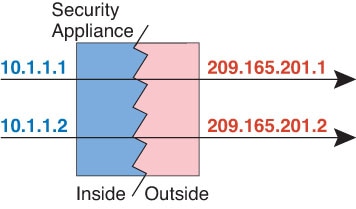
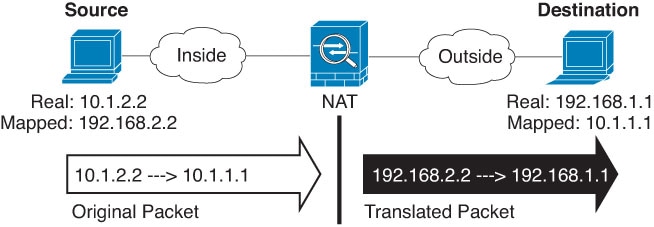
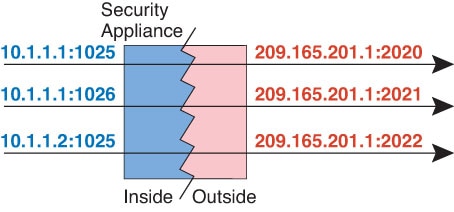
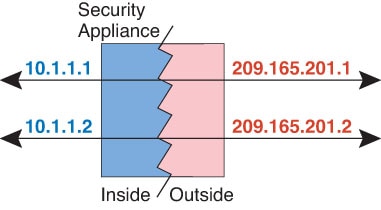
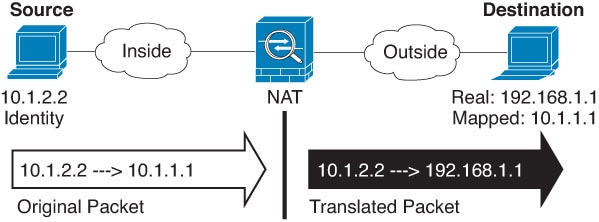
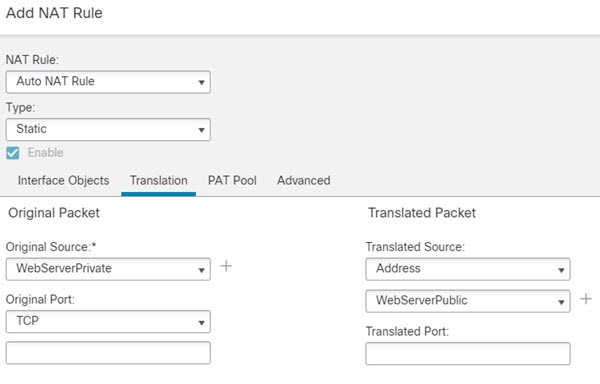
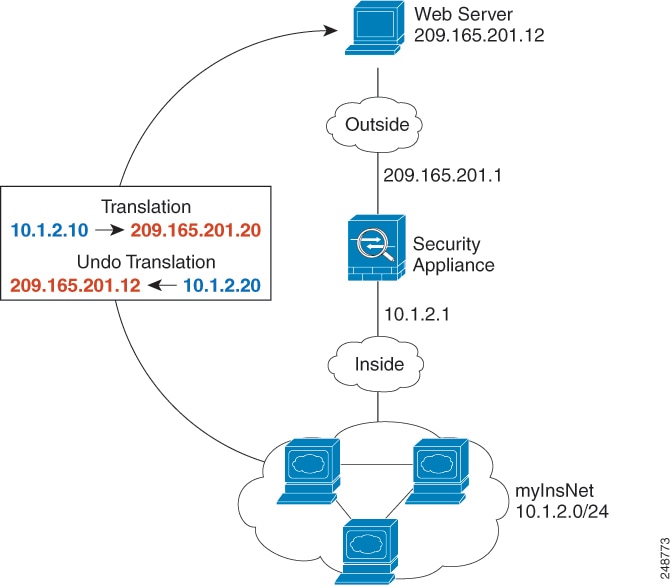
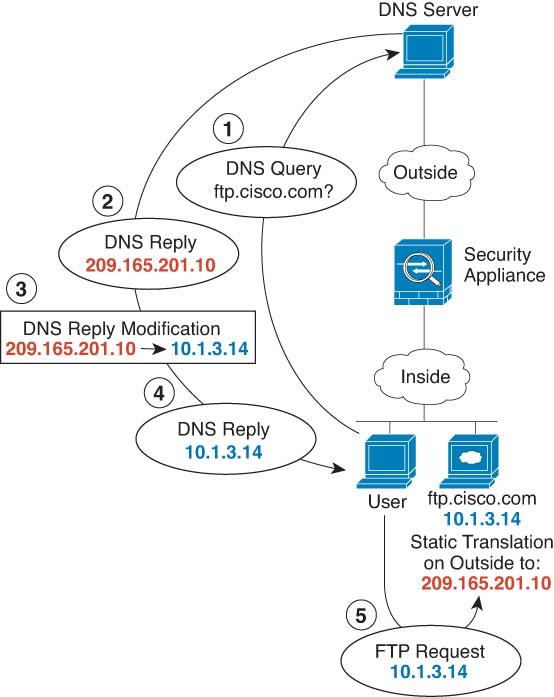
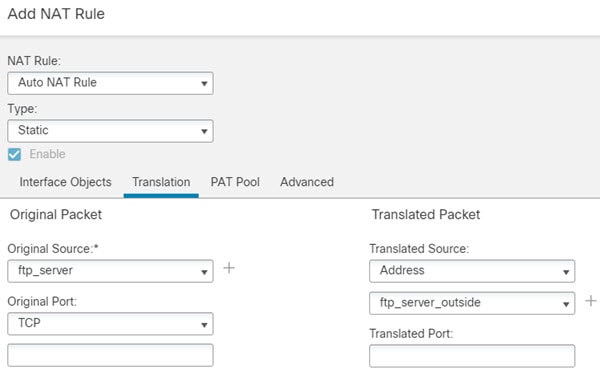
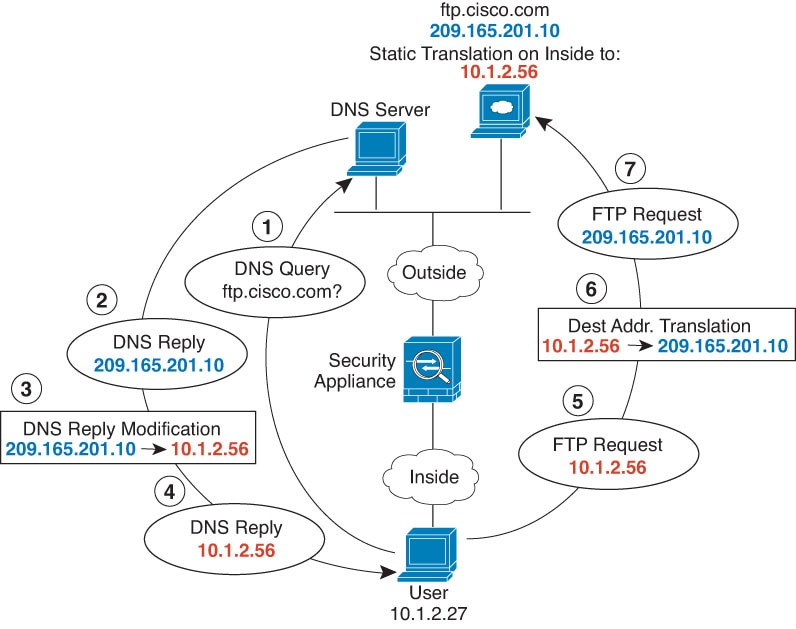
One of the main functions of NAT is to enable private IP networks to connect to the Internet. NAT replaces a private IP address with a public IP address, translating the private addresses in the internal private network into legal, routable addresses that can be used on the public Internet. In this way, NAT conserves public addresses because it can be configured to advertise at a minimum only one public address for the entire network to the outside world.
Other functions of NAT include:
-
Security—Keeping internal IP addresses hidden discourages direct attacks.
-
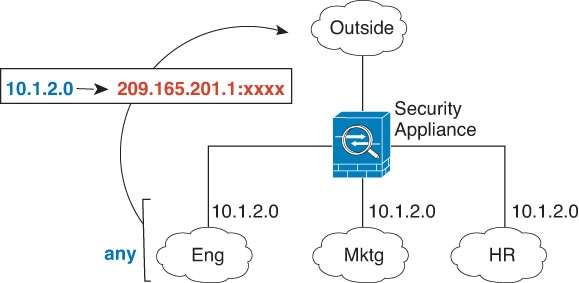
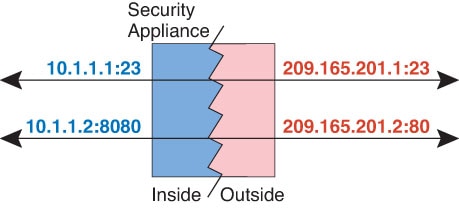
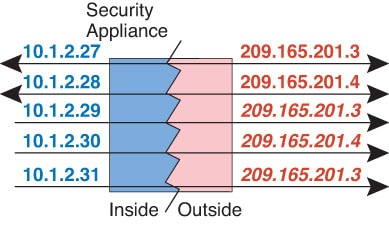
IP routing solutions—Overlapping IP addresses are not a problem when you use NAT.
-
Flexibility—You can change internal IP addressing schemes without affecting the public addresses available externally; for example, for a server accessible to the Internet, you can maintain a fixed IP address for Internet use, but internally, you can change the server address.
-
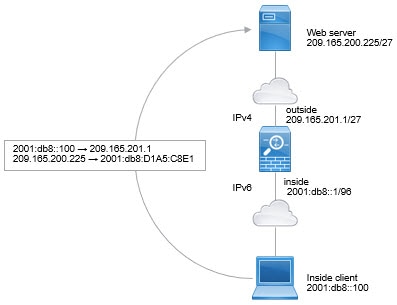
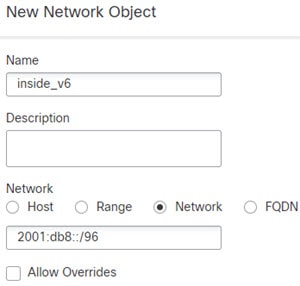
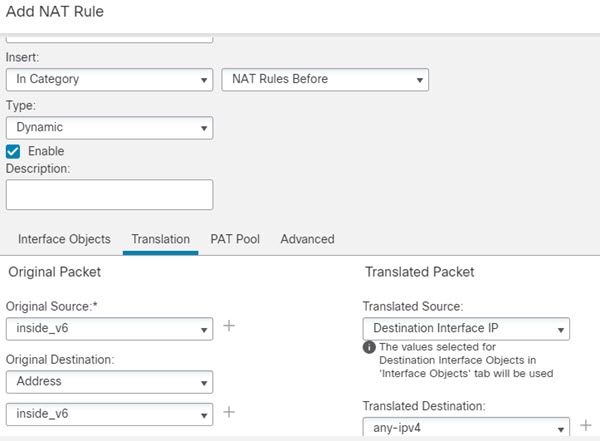
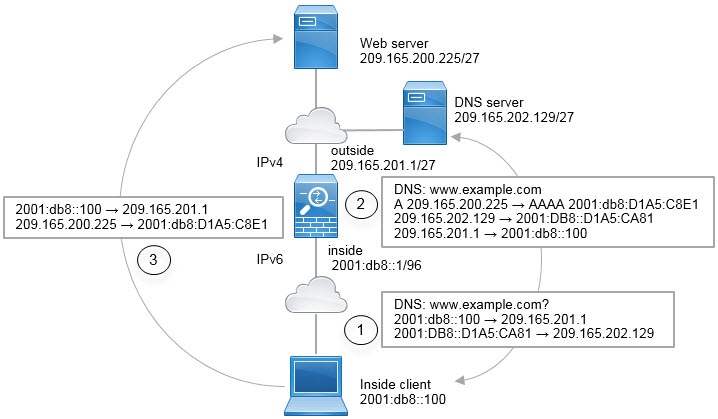
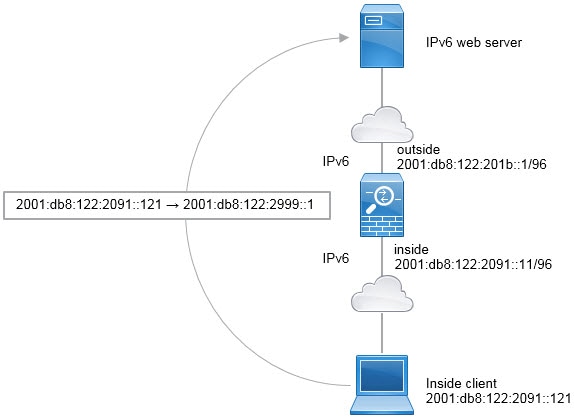
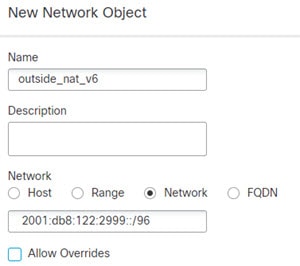
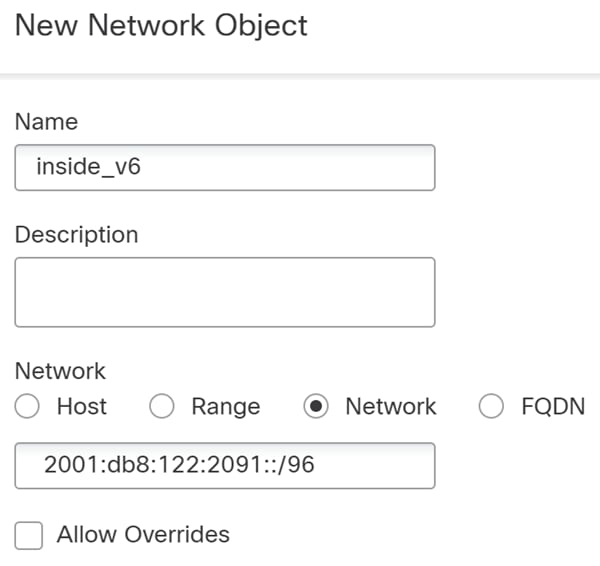
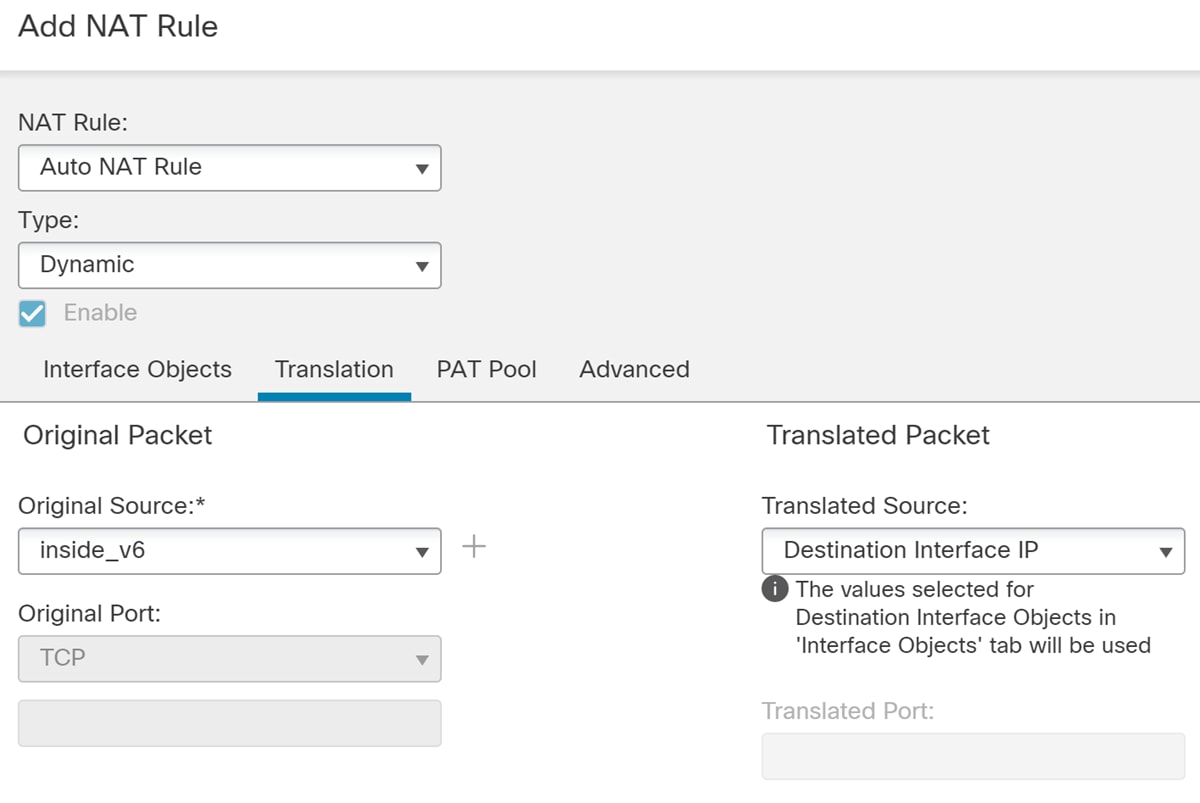
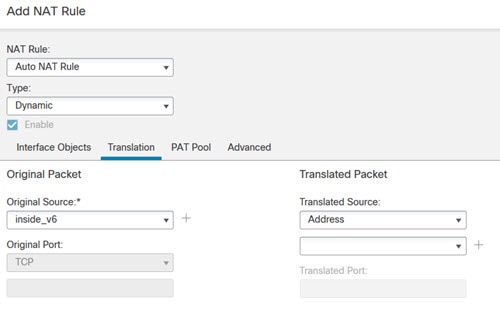
Translating between IPv4 and IPv6 (Routed mode only) —If you want to connect an IPv6 network to an IPv4 network, NAT lets you translate between the two types of addresses.
 Note |
NAT is not required. If you do not configure NAT for a given set of traffic, that traffic will not be translated, but will have all of the security policies applied as normal. |








































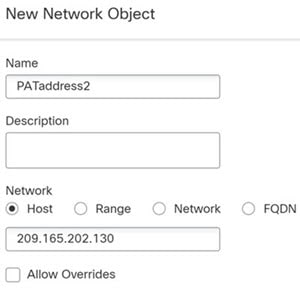



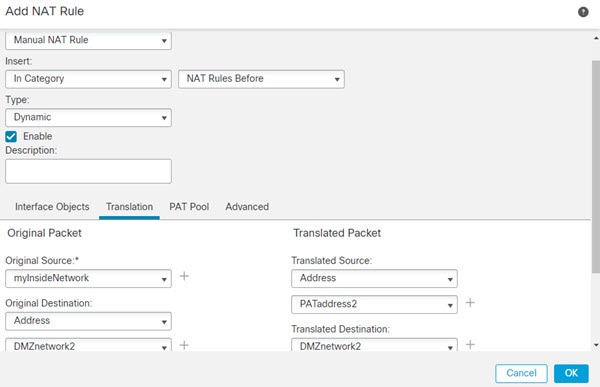
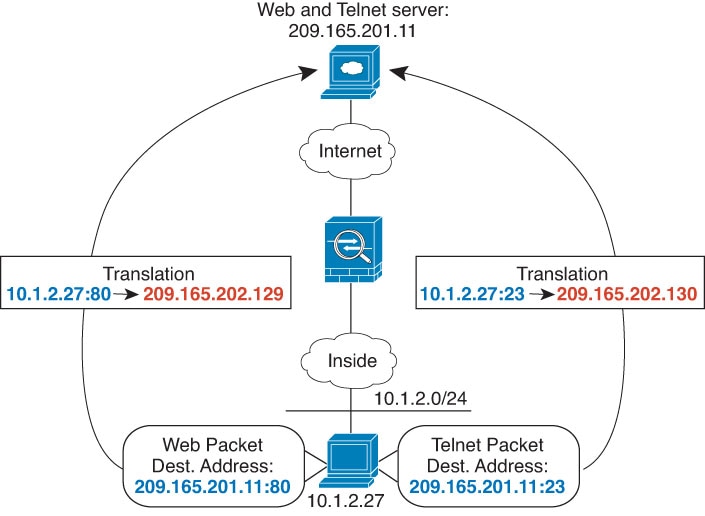

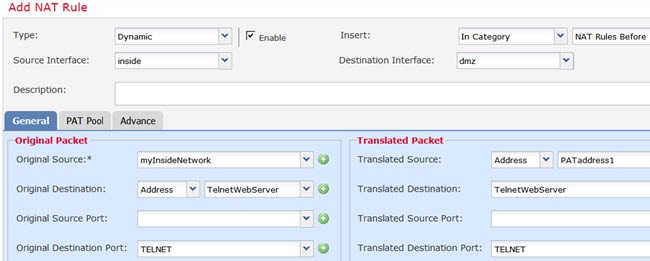














 Feedback
Feedback