About ECMP
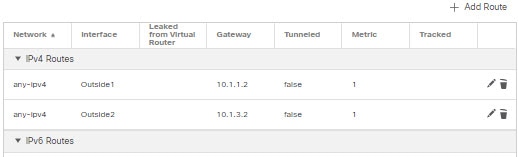
The threat defense device supports Equal-Cost Multi-Path (ECMP) routing. You can configure traffic zones per virtual router to contain a group of interfaces. You can have up to 8 equal cost static or dynamic routes across up to 8 interfaces within each zone. For example, you can configure multiple default routes across three interfaces in the zone:
route for 0.0.0.0 0.0.0.0 through outside1 to 10.1.1.2
route for 0.0.0.0 0.0.0.0 through outside2 to 10.2.1.2
route for 0.0.0.0 0.0.0.0 through outside3 to 10.3.1.2






 Feedback
Feedback