To configure advanced settings for an access control policy, select Advanced Settings from the More drop-down arrow at the end of the packet flow line.
Advanced access control policy settings typically require little or no
modification. The default settings are appropriate for most deployments. Note that
many of the advanced preprocessing and performance options in access control
policies may be modified by rule updates as described in Update Intrusion Rules in the Cisco Secure Firewall Management
Center Administration Guide
.
If View ( ) appears instead, settings are inherited from an ancestor policy, or you do not have permission to modify the settings.
) appears instead, settings are inherited from an ancestor policy, or you do not have permission to modify the settings.
Inheriting Settings from a Parent Policy
If the access control policy has a base policy, you can elect to inherit settings from the base policy. Select Inherit from base policy for each setting group where you want to use the parent policy's settings. If inheritance has been configured so that these
settings are locked, you cannot configure unique settings for the policy, these settings are read-only.
If you are allowed to configure unique settings for the policy, you must deselect Inherit from base policy to make your edits.
General Settings
|
Option
|
Description
|
|
Maximum URL characters to store in connection events
|
To customize the number of characters you store for each URL
requested by your users. See
Limiting Logging of Long
URLs in the Cisco Secure Firewall Management
Center Administration Guide for more
information.
To customize the length of time before you re-block a website after a user bypasses an initial block, see Setting the User Bypass Timeout for a Blocked Website.
|
|
Allow an Interactive Block to bypass blocking for (seconds)
|
See Setting the User Bypass Timeout for a Blocked Website.
|
|
Retry URL cache miss lookup
|
The first time the system encounters a URL that does not have a locally stored category and reputation, it looks up that URL
in the cloud and adds the result to the local data store, for faster processing of that URL in the future.
This setting determines what the system does when it needs to look up a URL's category and reputation in the cloud.
By default, this setting is enabled: The system momentarily delays the traffic while it checks the cloud for the URL's reputation
and category, and uses the cloud verdict to handle the traffic.
If you disable this setting: When the system encounters a URL that is not in its local cache, the traffic is immediately passed
and handled according to the rules configured for Uncategorized and reputationless traffic.
In passive deployments, the system does not retry the lookup, as it cannot hold packets.
|
| Enable Threat Intelligence Director |
Disable this option to stop publishing TID data to your configured devices.
|
|
Enable reputation enforcement on DNS traffic
|
This option is enabled by default, for improved URL filtering performance and efficacy. For details and additional instructions,
see DNS Filtering: Identify URL Reputation and Category During DNS Lookup and subtopics.
|
|
Inspect traffic during policy apply
|
To inspect traffic when you deploy configuration changes unless specific configurations require restarting the Snort process,
ensure that Inspect traffic during policy apply is set to its default value (enabled).
When this option is enabled, resource demands could result in a small number of packets dropping without inspection. Additionally,
deploying some configurations restarts the Snort process, which interrupts traffic inspection. Whether traffic drops during
this interruption or passes without further inspection depends on how the target device handles traffic. See Snort Restart Scenarios for more information.
|
TLS Server Identity Discovery
The latest version of the Transport Layer Security (TLS) protocol 1.3, defined by RFC 8446, is the preferred protocol for many web servers to provide secure communications. Because the TLS 1.3 protocol encrypts the
server's certificate for additional security, and the certificate is needed to match application and URL filtering criteria
in access control rules, the Firepower System provides a way to extract the server certificate without decrypting the entire packet.
You can enable this feature, referred to as TLS server identity discovery, when you configure advanced settings for an access control policy.
If you enable this option, we recommend you also enable the decryption policy's advanced TLS adaptive server identity probe
option as well. Together, these options enable more efficient decryption of TLS 1.3 traffic. For more information, see TLS 1.3 Decryption Best Practices.
When a new connection starts that will be affected by TLS server identity discovery, the threat
defense holds the original ClientHello packet to determine the identity of the server to which it connects before continuing. The
threat
defense device sends a specialized connection from the threat
defense to the server. The server's response includes the server certificate, the specialized connection is terminated, and the original
connection is evaluated as required by the access control policy.
TLS server identity discovery prioritizes the certificate's Common Name (CN) over the Server Name Indication (SNI).
To enable TLS server identity discovery, click the Advanced tab, click
Edit ( ) for the setting, and select Early application detection and URL
categorization.
) for the setting, and select Early application detection and URL
categorization.
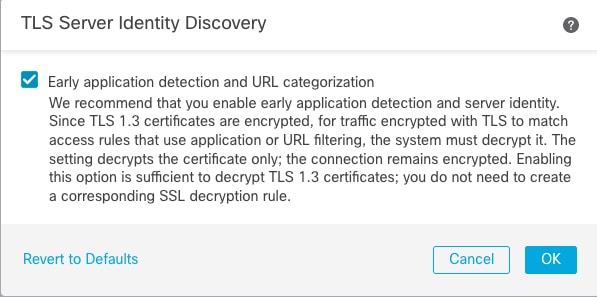
We strongly recommend enabling it for any traffic you want to match on application or URL criteria, especially if you want
to perform deep inspection of that traffic. A
decryption policy is not required because traffic is not decrypted in the process of extracting the server certificate.

Note
|
-
Because the certificate is decrypted, TLS server identity discovery can reduce performance depending on the hardware platform.
-
TLS server identity discovery is not supported in inline tap mode or passive mode deployments.
-
Enabling TLS server identity discovery is not supported on any Secure Firewall
Threat Defense Virtual deployed to AWS. If you have any such managed devices managed by the Secure Firewall Management Center, the connection event PROBE_FLOW_DROP_BYPASS_PROXY increments every time the device attempts to extract the server certificate.
-
TLS Server Identity Discovery also operates on TLS 1.2 sessions.
|
Network Analysis and Intrusion Policies
Advanced network analysis and intrusion policy settings allow you to:
-
Specify the intrusion policy and associated variable set that are used to inspect packets that must pass before the system
can determine exactly how to inspect that traffic.
-
Change the access control policy’s default network analysis policy, which governs many preprocessing options.
-
Use custom network analysis rules and network analysis policies to tailor preprocessing options to specific security zones,
networks, and VLANs.
For more information, see Advanced Access Control Settings for Network Analysis and Intrusion Policies.
Threat Defense Service Policy
You can use the Threat Defense Service Policy to apply services to specific traffic classes. For example, you can use a service
policy to create a timeout configuration that is specific to a particular TCP application, as opposed to one that applies
to all TCP applications. This policy applies to threat defense devices only, and will be ignored for any other device type. The service policy rules are applied after the access control
rules. For more information, see Service Policies.
Portscan Threat Detection
Portscan detector is a threat detection mechanism designed to help you detect and prevent portscan activity in all types of
traffic to protect networks from eventual attacks. Portscan traffic can be detected efficiently in both allowed and denied
traffic. For more information, see Threat Detection.
Elephant Flow Settings
Elephant flows are large, long duration, and fast flows that can cause duress for
Snort cores. There are two actions that can be applied on elephant flows to reduce
system stress, CPU hogging, packet drops, and so on. These actions are:
For more information, see the Elephant Flow Detection chapter in the Cisco Secure Firewall
Management Center Snort 3 Configuration
Guide.
Intelligent Application Bypass Settings
Intelligent Application Bypass (IAB) is an expert-level configuration that specifies applications to bypass or test for bypass
if traffic exceeds a combination of inspection performance and flow thresholds. For more information, see Intelligent Application Bypass.
Transport/Network Layer Preprocessor Settings
Advanced transport and network preprocessor settings apply globally to all networks, zones, and VLANs where you deploy your
access control policy. You configure these advanced settings in an access control policy rather than in a network analysis
policy. For more information, see Advanced Transport/Network Preprocessor Settings.
Detection Enhancement Settings
Advanced detection enhancement settings allow you to configure adaptive profiles so you can:
-
Use file policies and applications in access control rules.
-
Use service metadata in intrusion rules.
-
In passive deployments, improve reassembly of packet fragments and TCP streams based on your network’s host operating systems.
For more information, see Adaptive Profiles.









 Feedback
Feedback