About Decryption Policies
A decryption policy determines how the system handles encrypted traffic on your network. You can configure one or more decryption policies, associate a decryption policy with an access control policy, then deploy the access control policy to a managed device. When the device detects a TCP handshake, the access control policy first handles and inspects the traffic. If it subsequently identifies a TLS/SSL-encrypted session over the TCP connection, the decryption policy takes over, handling and decrypting the encrypted traffic.
Create a decryption policy using the wizard
You can use a wizard to create the following types of decryption policies:
-
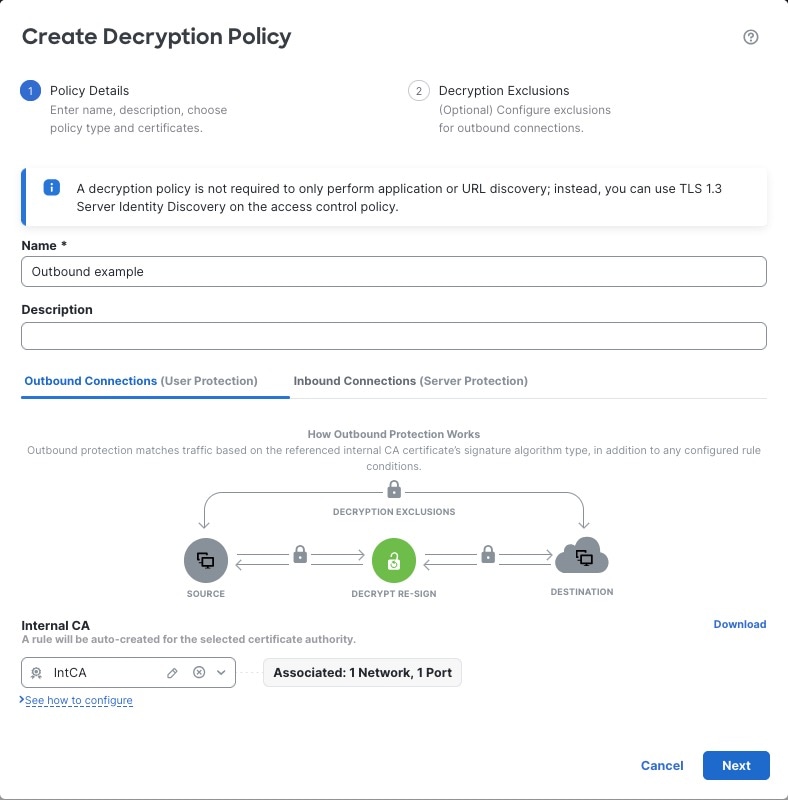
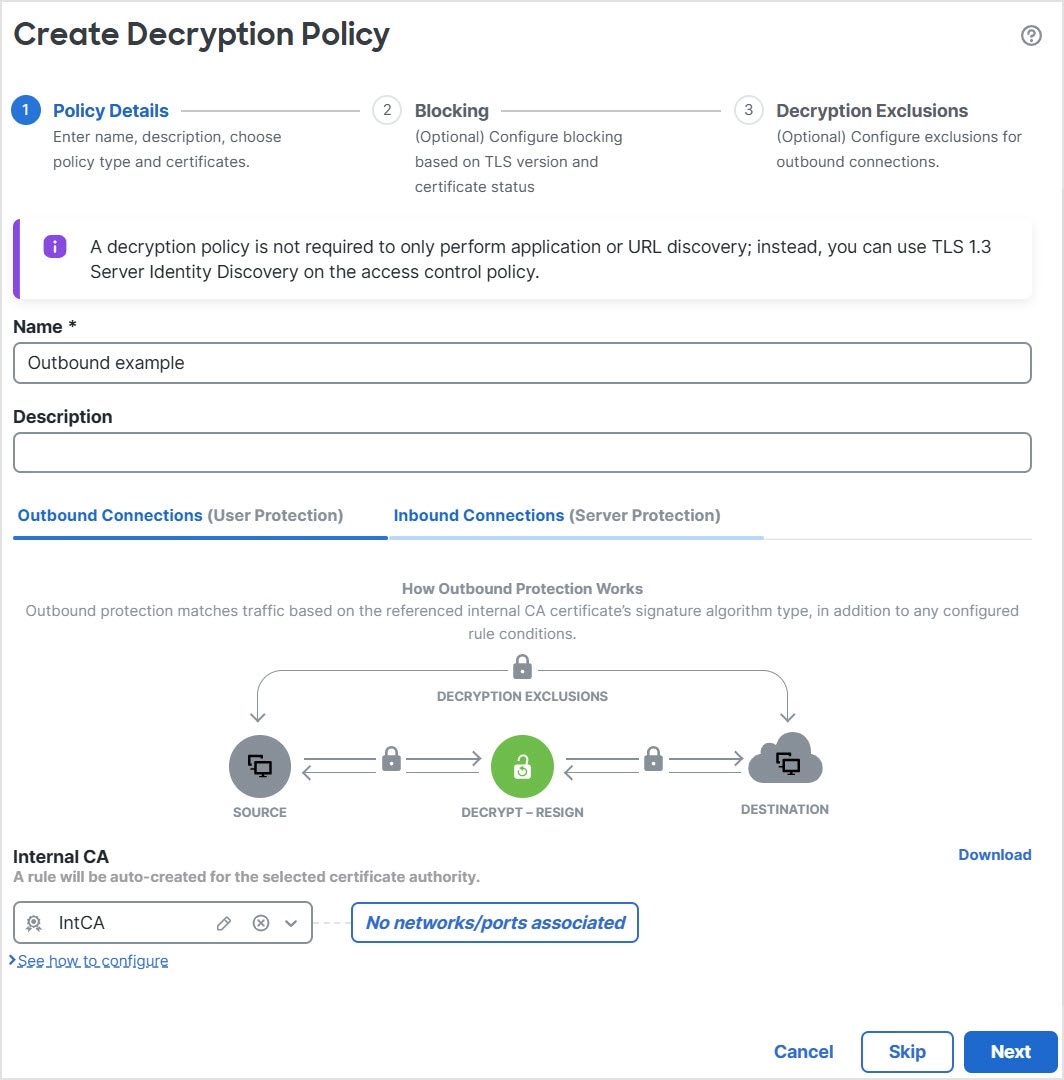
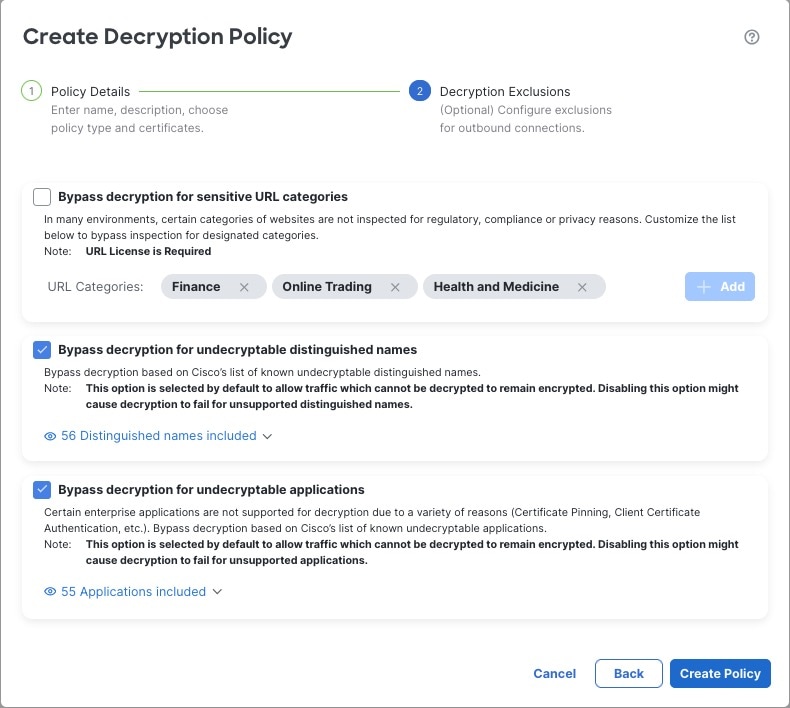
Outbound protection (Decrypt - Resign rule action). If traffic matches this rule, the system re-signs the server certificate with the CA certificate, then acts as a man-in-the-middle.
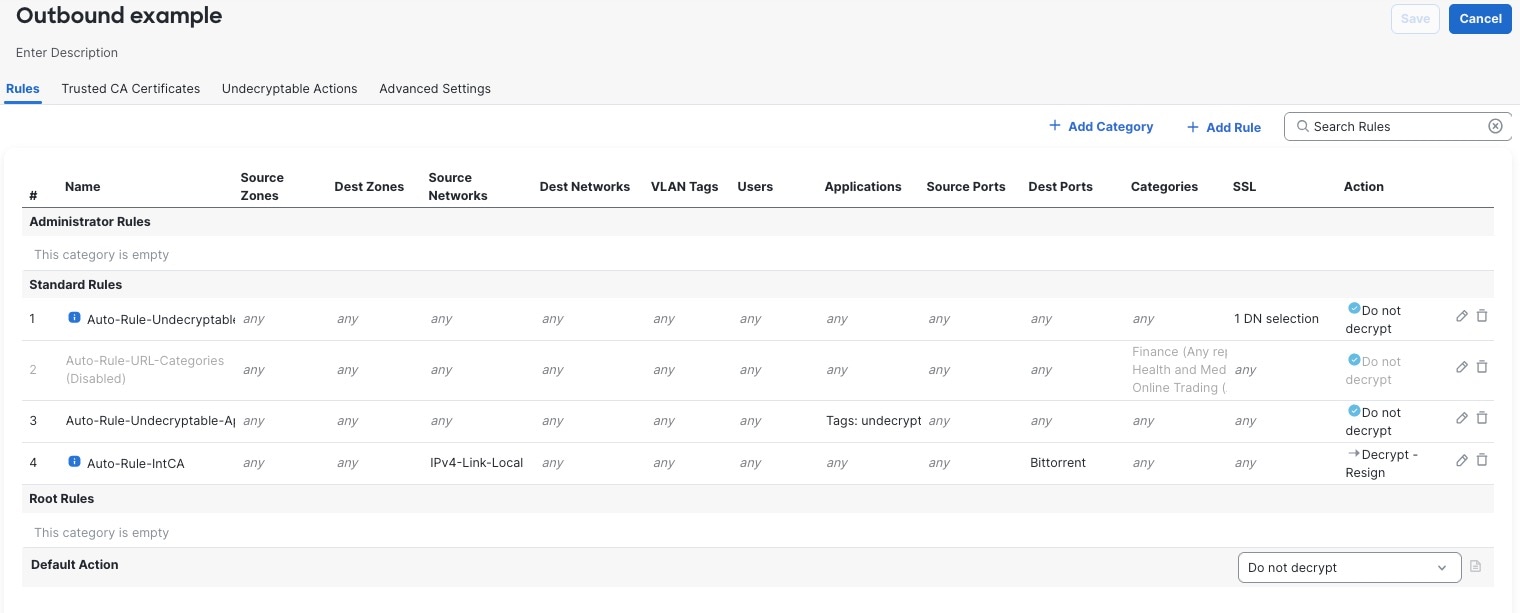
Three rules with a Do Not Decrypt action are added to the policy at the same time, saving you the trouble of doing it later. These rules correspond to any decryption exclusions you configure when you create the policy (for example, you can choose to bypass decryption for applications that are known to use certificate pinning.
For more information, see Create a Decryption Policy with Outbound Connection Protection.
-
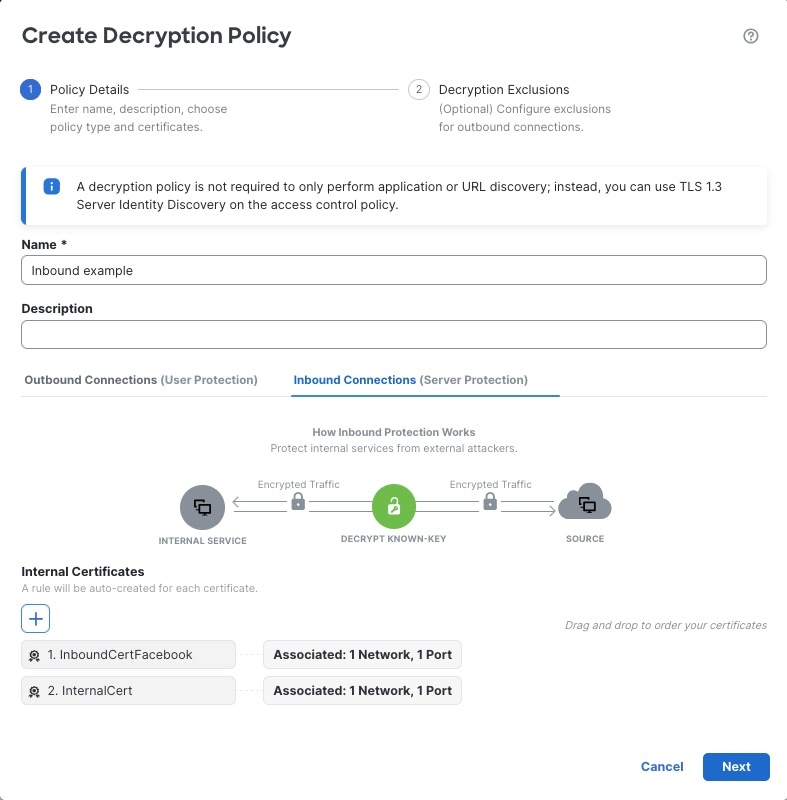
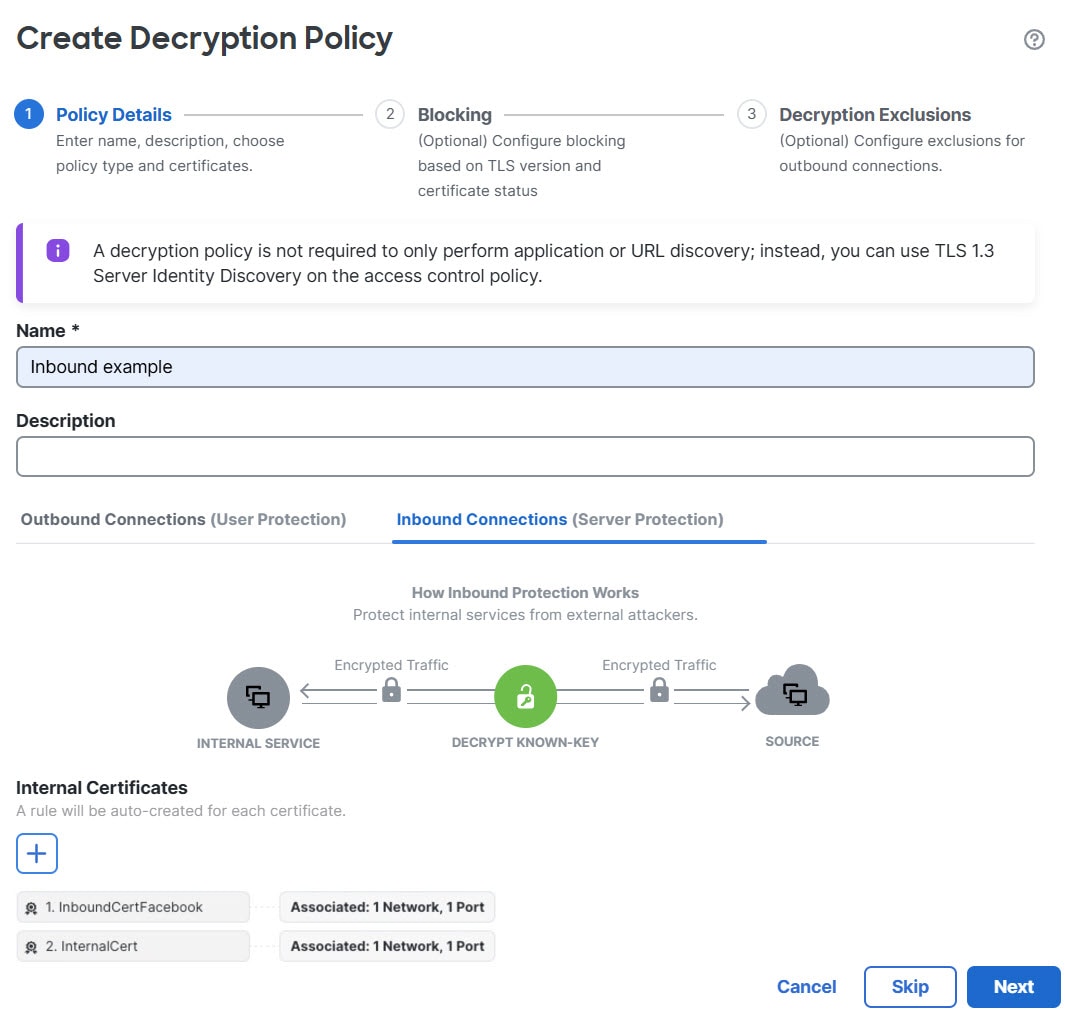
Inbound protection (Decrypt - Known Key rule action). You can associate one or more server certificates and paired private keys with the action. If traffic matches the rule, and the certificate used to encrypt the traffic matches the certificate associated with the action, the system uses the appropriate private key to obtain the session encryption and decryption keys.
Three rules with a Do Not Decrypt action are added to the policy at the same time but these rules are disabled by default. These rules correspond to any decryption exclusions you configure when you create the policy (for example, you can choose to bypass decryption for applications that are known to use certificate pinning.
For more information, see Create a Decryption Policy with Inbound Connection Protection.
-
Any other decryption rule action (such as blocking or monitoring).
For more information, see Create a Decryption Policy with Other Rule Actions.
The wizard automatically creates a separate rule for each certificate you specify. For example, an inbound protection rule might specify one certificate for traffic coming to the Finance department internal network and a different certificate for traffic coming to the Engineering network.
The wizard creates additional rules for outbound and inbound protection policies as follows:
-
Outbound protection (Decrypt - Resign rule action): The wizard creates Do Not Decrypt rules for traffic that matches exceptions you specify in the wizard. For example, you can choose to not decrypt traffic from undecryptable applications, typically those using certificate pinning.
The Do Not Decrypt rules are placed first in the decryption policy so that traffic is passed through the firewall with minimal processing.
-
Inbound protection (Decrypt - Known Key rule action): The wizard does not allow you to choose any exceptions but it adds the Do Not Decrypt rules to the policy and disables them; that way, you can enable those exceptions later if you need to.
Do Not Decrypt policy example
Following is an example decryption policy with a Do Not Decrypt rule action:

The simplest decryption policy, as shown in the following diagram, directs the device where it is deployed to handle encrypted traffic with a single default action. You can set the default action to block decryptable traffic without further inspection, or to inspect undecrypted decryptable traffic with access control. The system can then either allow or block the encrypted traffic. If the device detects undecryptable traffic, it either blocks the traffic without further inspection or does not decrypt it, inspecting it with access control.
To get started, see Create a Decryption Policy





 Feedback
Feedback