Decryption Rule Examples
This section provides an example of decryption rule that illustrate our best practices.
See one of the following sections for more information.
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
This chapter builds on concepts discussed in this guide to provide a specific example of an SSL policy with decryption rules that follow our best practices and recommendations. You should be able to apply this example to your situation, adapting it to the needs of your organization.
In short:
For trusted traffic (such as transferring a large compressed server backup), bypass inspection entirely, using prefiltering and flow offload.
Put first any decryption rules that can be evaluated quickly, such as those that apply to specific IP addresses.
Put last any decryption rules that require processing, Decrypt - Resign, and rules that block unsecure protocol versions and cipher suites.
This section provides an example of decryption rule that illustrate our best practices.
See one of the following sections for more information.
This task discusses how to run the decryption policy wizard for outbound traffic protection. This policy has four rules:
Do Not Decrypt rule for distinguished names that are known to be undecryptable, most likely because they use TLS/SSL pinning.
Do Not Decrypt rule for URL categories that we classify as sensitive based on their content (for example, medical and financial).
Do Not Decrypt rule for applications that are known to be undecryptable, most likely because they use TLS/SSL pinning.
Decrypt - Resign rule that uses a certificate authority object named IntCA to decrypt the remainder of the traffic.
You can then edit the rules if you want and also manually add:
Decrypt - Resign rules for traffic to monitor and determine whether the traffic should be blocked in the future.
Do Not Decrypt rules for other types of traffic
Block or Block with Reset rules for bad certificates and unsecure cipher suites.
If you enabled Change Management, you must create and assign a ticket before you can create a decryption policy. Before the decryption policy can be used, the ticket and all associated objects (like certificate authorities) must be approved. For more information, see Creating Change Management Tickets and Policies and Objects that Support Change Management.
|
Step 1 |
Log in to the Secure Firewall Management Center if you haven't already done so. |
|
Step 2 |
Click . |
|
Step 3 |
Click Create Decryption Policy. |
|
Step 4 |
Give the decryption policy a Name and optionally a Description. |
|
Step 5 |
Click the Outbound Protection tab. |
|
Step 6 |
From the Internal CA list, click the name of an internal certificate authority object or click Create New to upload or generate one. The following figure shows an example.
|
|
Step 7 |
(Optional.) To restrict traffic to source and destination networks, click Click to assign networks and ports. |
|
Step 8 |
Click Next. |
|
Step 9 |
Complete the wizard as discussed in Decryption Policy Exclusions. |
This task discusses how to exclude certain types of traffic from decryption. We create Do Not Decrypt rules in your decryption policy for these although the rules are initially enabled only for an outbound decryption policy (that is, one that uses the Decrypt - Resign policy action).
You must upload an internal CA certificate for your managed device before you can create a decryption policy that protects outbound connections. You can do this in any of the following ways:
Create an internal CA certificate object by going to and referring to PKI.
At the time you create this decryption policy.
|
Step 1 |
Complete the tasks discussed in: |
||||||||
|
Step 2 |
The exclusions page provides the following options. All options are enabled for an outbound protection policy (Decrypt - Resign rule action) and disabled for all other decryption policy actions.
The following figure shows the default options.
|
||||||||
|
Step 3 |
Click Create Policy. The following figure shows a sample outbound protection policy.
In the preceding example, the Do Not Decrypt rules corresponding to your choices for rule exclusions are automatically added before the Decrypt - Resign rule. The rule for sensitive URL categories is disabled because, by default, that exclusion is disabled. Had you selected the Bypass decryption for sensitive URL categories check box, the rule would have been enabled. |
||||||||
|
Step 4 |
Click Create Policy. |
Add rule conditions: Decryption Rule Conditions
Add a default policy action: Decryption Policy Default Actions
Configure logging options for the default action as described in Logging Connections with a Policy Default Action in the Cisco Secure Firewall Management Center Administration Guide .
Set advanced policy properties: Decryption Policy Advanced Options.
Associate the decryption policy with an access control policy as described in Associating Other Policies with Access Control.
Deploy configuration changes; see Deploy Configuration Changes.
The first decryption rule in the example does not decrypt traffic that goes to an internal network (defined as internal ). Do Not Decrypt rule actions are matched during ClientHello so they are processed very fast.
After you run the decryption policy wizard, edit the policy to add the following rule. Drag it to the top of the list of rules so it's evaluated first.
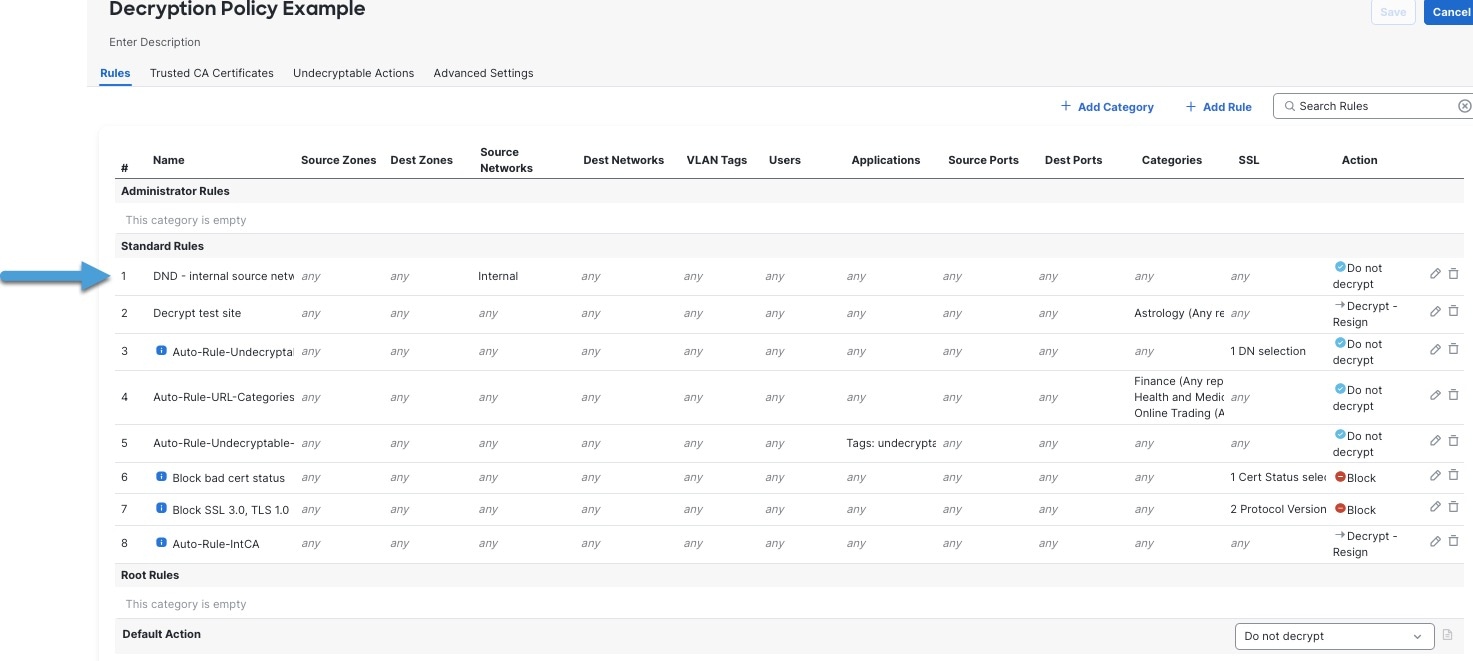
 Note |
If you have traffic going from internal DNS servers to internal DNS resolvers (such as Cisco Umbrella Virtual Appliances), you can add Do Not Decrypt rules for them as well. You can even add those to prefiltering policies if the internal DNS servers do their own logging. However, we strongly recommend you do not use Do Not Decrypt rules or prefiltering for DNS traffic that goes to the internet, such as internet root servers (for example, Microsoft internal DNS resolvers built into Active Directory). In those cases, you should fully inspect the traffic or even consider blocking it. |
Rule detail:
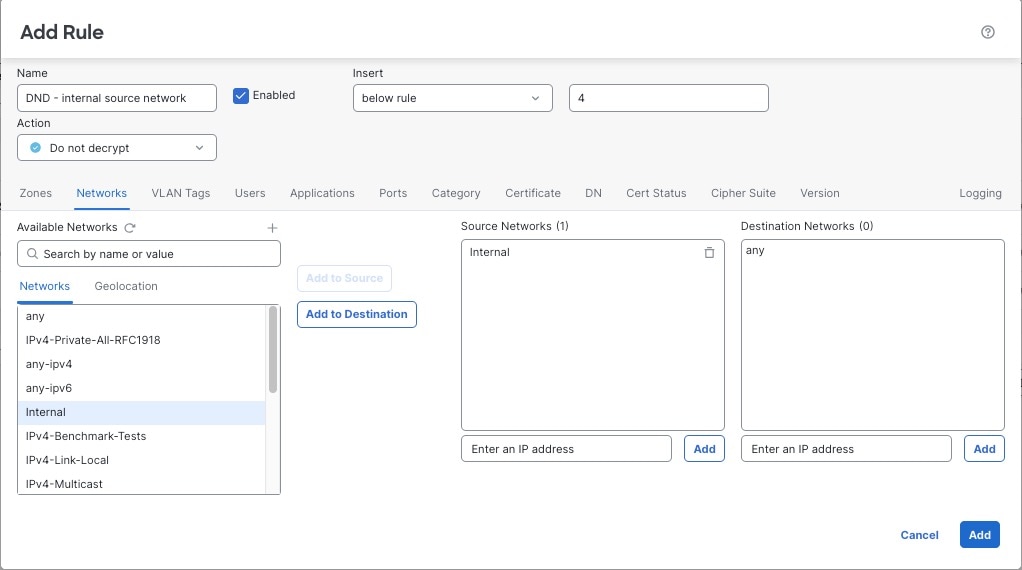
The next rule is optional in the example; use it to decrypt and monitor limited types of traffic before determining whether or not to allow it on your network.
After you run the decryption policy wizard, edit the policy to add the following rule. Drag it to the second position in the list of rules.
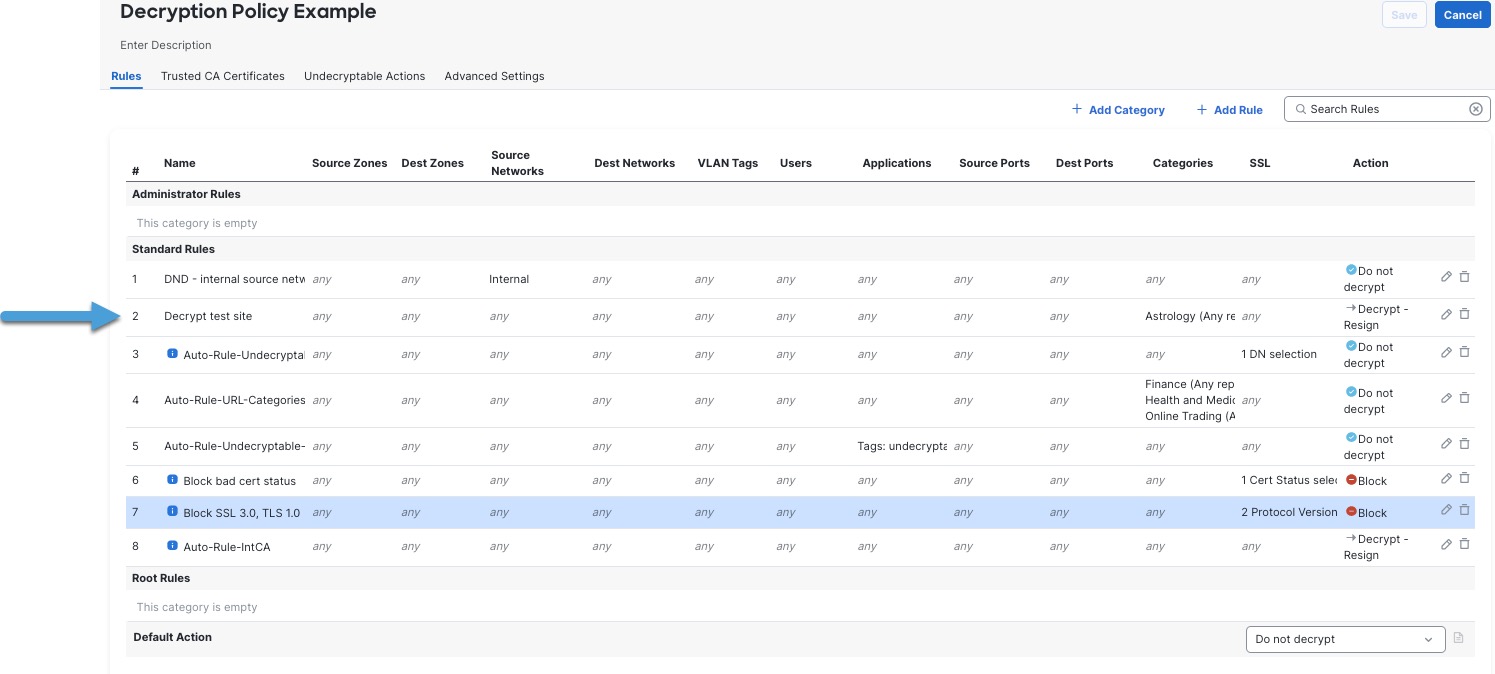
Rule detail:
The last decryption rules, because they are the most specific and require the most processing, are rules that either monitor or block bad certificates and unsecure protocol versions.
After you run the decryption policy wizard, edit the policy to add the following rules. Drag them to a position before the Decrypt - Resign rule.
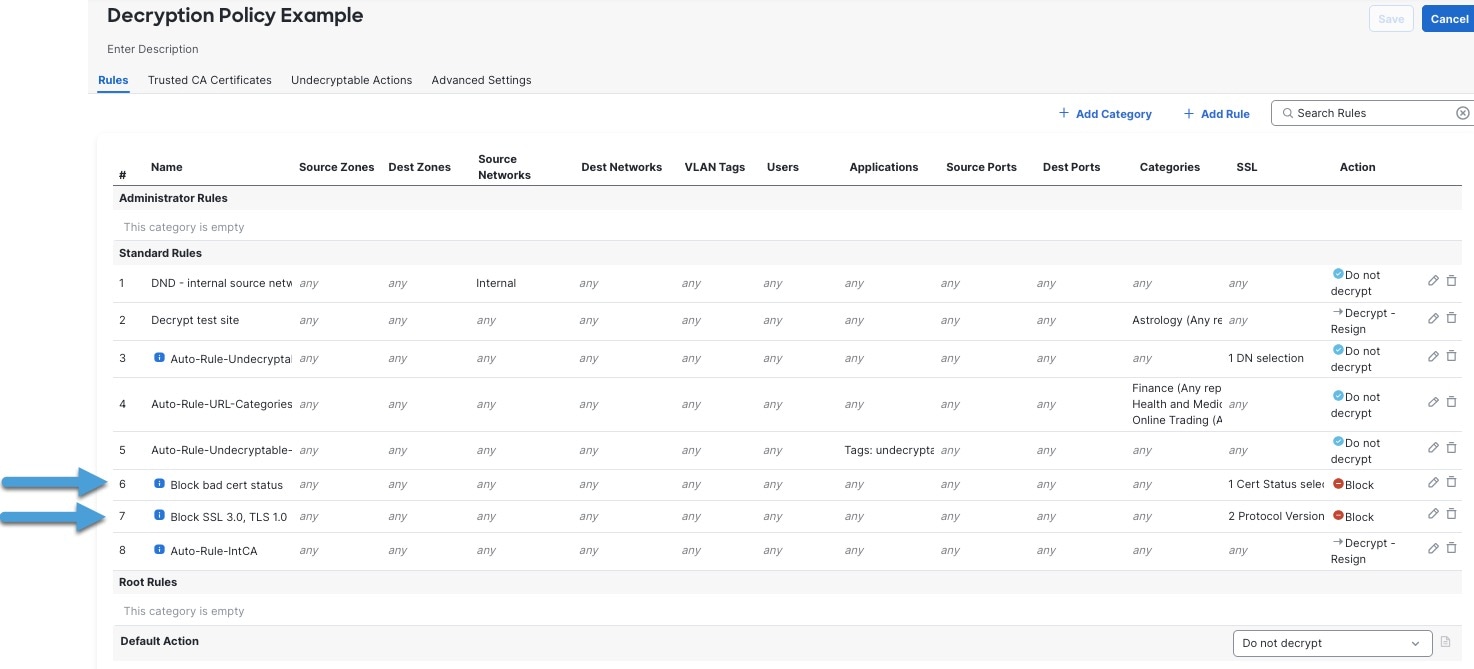
Rule details:
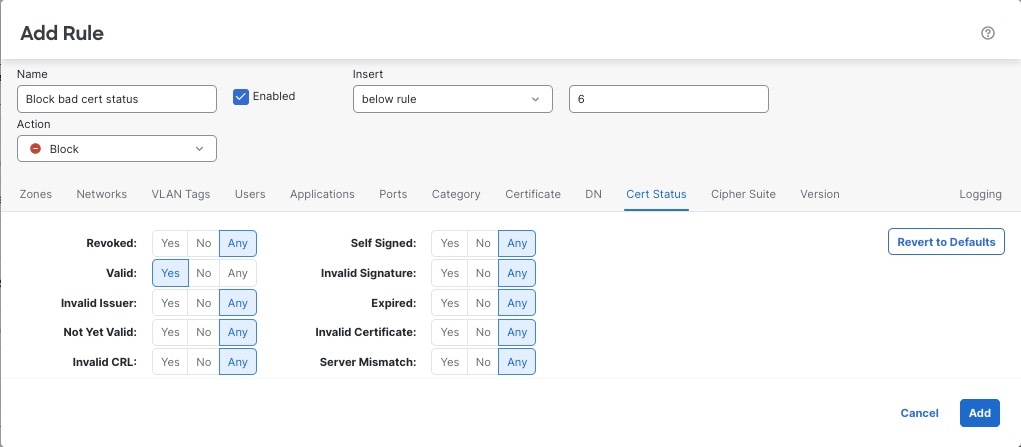
The last decryption rules, because they are the most specific and require the most processing, are rules that either monitor or block bad certificates and unsecure protocol versions. The example in this section shows how to monitor or block traffic by certificate status.
 Important |
Use the Cipher Suite and Version rule conditions only in rules with either the Block or Block with reset rule actions. Do not use Cipher Suite and Version with either Decrypt - Resign or Decrypt - Known Key rule actions. These conditions in rules with other rule actions can interfere with the system's ClientHello processing, resulting in unpredictable performance. |
|
Step 1 |
Log in to the Secure Firewall Management Center if you haven't already done so. |
|
Step 2 |
Click . |
|
Step 3 |
Click Edit ( |
|
Step 4 |
Click Edit ( |
|
Step 5 |
Click Add Rule. |
|
Step 6 |
n the Add Rule dialog box, in the Name field, enter a name for the rule. |
|
Step 7 |
Click Cert Status. |
|
Step 8 |
For each certificate status, you have the following options:
|
|
Step 9 |
From the Action list, click either Monitor to only monitor and log traffic that matches the rule or click Block or Block with Reset to block the traffic and optionally reset the connection. |
|
Step 10 |
To save changes to the rule, at the bottom of the page, click Add. |
|
Step 11 |
To save changes to the policy, at the top of the page, click Save. |
The organization trusts the Verified Authority certificate authority. The organization does not trust the Spammer Authority certificate authority. The system administrator uploads the Verified Authority certificate and an intermediate CA certificate issued by Verified Authority to the system. Because Verified Authority revoked a certificate it previously issued, the system administrator uploads the CRL that Verified Authority provided.
The following figure shows a certificate status rule condition checking for valid certificates, those issued by a Verified Authority, are not on the CRL, and still within the Valid From and Valid To date. Because of the configuration, traffic encrypted with these certificates is not decrypted and inspected with access control.
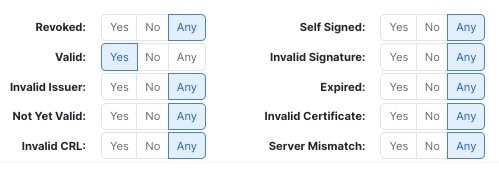
The following figure shows a certificate status rule condition checking for the absence of a status. In this case, because of the configuration, it matches against traffic encrypted with a certificate that has not expired.

In the following example, traffic would match this rule condition if the incoming traffic is using a certificate that has an invalid issuer, is self-signed, expired, and it is an invalid certificate.
The following graphic illustrates a certificate status rule condition that matches if the SNI of the request matches the server name or if the CRL is not valid.

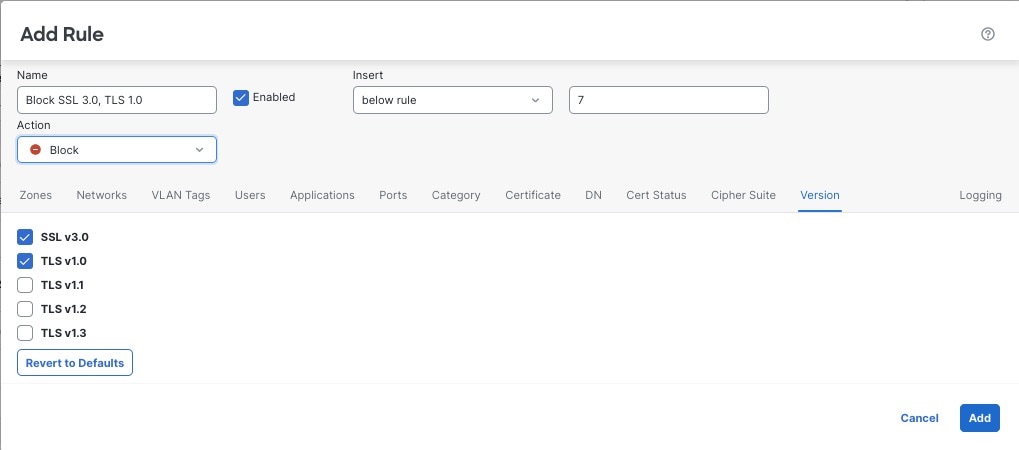
This example shows how to block TLS and SSL protocols on your network that are no longer considered secure, such as TLS 1.0, TLS 1.1, and SSLv3. It's included to give you a little more detail about how protocol version rules work.
You should exclude nonsecure protocols from your network because they are all exploitable. In this example:
You can block some protocols using Version page on the decryption rule.
Because the system considers SSLv2 as undecryptable, you can block it using the Undecryptable Actions on the decryption policy.
Similarly, because compressed TLS/SSL is not supported, you should block it as well.
 Important |
Use the Cipher Suite and Version rule conditions only in rules with either the Block or Block with reset rule actions. Do not use Cipher Suite and Version with either Decrypt - Resign or Decrypt - Known Key rule actions. These conditions in rules with other rule actions can interfere with the system's ClientHello processing, resulting in unpredictable performance. |
|
Step 1 |
Log in to the Secure Firewall Management Center if you haven't already done so. |
|
Step 2 |
Click . |
|
Step 3 |
Click Edit ( |
|
Step 4 |
Click Edit ( |
|
Step 5 |
Click Add Rule. |
|
Step 6 |
In the Add Rule dialog box, in the Name field, enter a name for the rule. |
|
Step 7 |
From the Action list, click Block or Block with reset. |
|
Step 8 |
Click Version page. |
|
Step 9 |
Check the check boxes for protocols that are no longer secure, such as SSL v3.0, TLS 1.0, and TLS 1.1. Clear the check boxes for any protocols that are still considered secure. The following figure shows an example.
|
|
Step 10 |
Choose other rule conditions as needed. |
|
Step 11 |
Click Add. |
This rule is included to give you an idea about how to monitor or block traffic based on the server certificate's distinguishedname. It's included to give you a little more detail.
The distinguished name can consist of country code, common name, organization, and organizational unit, but typically consists
of a common name only. For example, the common name in the certificate for https://www.cisco.com is cisco.com. (However, it's not always this simple; Distinguished Name (DN) Rule Conditions shows how to find common names.)
The host name portion of the URL in the client request is the Server Name Indication (SNI). The client specifies which hostname they want to connect to (for example, auth.amp.cisco.com) using the SNI extension in the TLS handshake. The server then selects the corresponding private key and certificate chain
that are required to establish the connection while hosting all certificates on a single IP address.
|
Step 1 |
Log in to the Secure Firewall Management Center if you haven't already done so. |
||
|
Step 2 |
Click . |
||
|
Step 3 |
Click Edit ( |
||
|
Step 4 |
Click Edit ( |
||
|
Step 5 |
Click Add Rule. |
||
|
Step 6 |
In the Add Rule dialog box, in the Name field, enter a name for the rule. |
||
|
Step 7 |
From the Action list, click Block or Block with reset. |
||
|
Step 8 |
Click DN. |
||
|
Step 9 |
Find the distinguished names you want to add from the Available DNs, as follows:
|
||
|
Step 10 |
To select an object, click it. To select all objects, right-click and then Select All. |
||
|
Step 11 |
Click Add to Subject or Add to Issuer.
|
||
|
Step 12 |
Add any literal common names or distinguished names that you want to specify manually. Click the Enter DN or CN prompt below the Subject DNs or Issuer DNs list; then type a common name or distinguished name and click Add. Although you can add a CN or DN to either list, it's more common to add them to the Subject DNs list. |
||
|
Step 13 |
Add or continue editing the rule. |
||
|
Step 14 |
When you're done, to save changes to the rule, click Add at the bottom of the page. |
||
|
Step 15 |
To save changes to the policy, click Save at the top of the page. |
The following figure shows a distinguished name rule condition searching for certificates issued to goodbakery.example.com or issued by goodca.example.com. Traffic encrypted with these certificates is allowed, subject to access control.
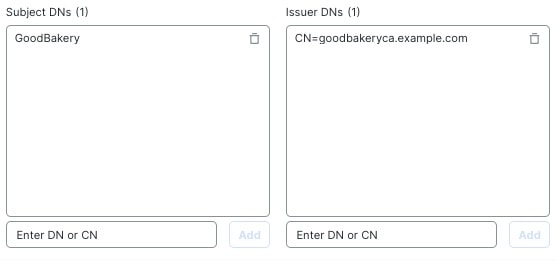
This task discusses how to associate the decryption policy with an access control policy and setting recommended advanced settings for the access control policy.
For your decryption policy to be used by the system, you must associate it with an access control policy.
Create the sample decryption policy as discussed in this guide.
For more information about decryption policy advanced options, see Decryption Policy Advanced Options.
|
Step 1 |
Log in to the Secure Firewall Management Center if you haven't already done so. |
|
Step 2 |
Click . |
|
Step 3 |
Either create a new access control policy or click Edit ( |
|
Step 4 |
Click the word Decryption as the following figure shows.
|
|
Step 5 |
From the list, click the name of your decryption policy and also check Early application detection and URL categorization as the following figure shows.
|
|
Step 6 |
Click Apply. |
|
Step 7 |
Click as the following figure shows.
|
|
Step 8 |
Click Edit ( |
|
Step 9 |
Select the check box as the following figure shows.
|
|
Step 10 |
Click OK. |
|
Step 11 |
At the top of the page, click Save. |
|
Step 12 |
At the top of the page, click Return to Access Control Policy Management, as the following figure shows
|
|
Step 13 |
Click Edit ( |
|
Step 14 |
At the bottom of the page, next to the default action, click |
|
Step 15 |
Check Log at beginning of connection and any other options you choose. For more information, see Logging Settings for Access Control PoliciesLogging Settings for Access Control Policies in the Cisco Secure Firewall Management Center Device Configuration Guide. |
|
Step 16 |
Click Apply. |
|
Step 17 |
At the top of the page, click Save. |
Add rule conditions: Decryption Rule Conditions.
Add a default policy action: Decryption Policy Default Actions.
Configure logging options for the default action as described in Logging Connections with a Policy Default Action in the Cisco Secure Firewall Management Center Administration Guide .
Set advanced policy properties: Decryption Policy Advanced Options.
Associate the decryption policy with an access control policy as described in Associating Other Policies with Access Control.
Deploy configuration changes; see Deploy Configuration Changes.
Prefiltering is the first phase of access control, before the system performs more resource-intensive evaluation. Prefiltering is simple, fast, and early compared to subsequent evaluation, which uses inner headers and has more robust inspection capabilities.
Based on your security needs and traffic profile, you should consider prefiltering and therefore excluding from any policy and inspection the following:
Common intraoffice applications such as Microsoft Outlook 365
Elephant flows, such as server backups
How to configure recommended best practice settings for your decryption rules.
Decryption rules: Enable logging for every rule except those with a Do Not Decrypt rule action. (It's up to you; if you want to see information about traffic that isn't decrypted, enable logging for those rules also.)
|
Step 1 |
Log in to the Secure Firewall Management Center if you haven't already done so. |
|
Step 2 |
Click . |
|
Step 3 |
Click Edit ( |
|
Step 4 |
Click Edit ( |
|
Step 5 |
Click the Logging tab. |
|
Step 6 |
Click Log at End of Connection. |
|
Step 7 |
Click Save. |
|
Step 8 |
Click Save at the top of the page. |