About Zero Trust Access
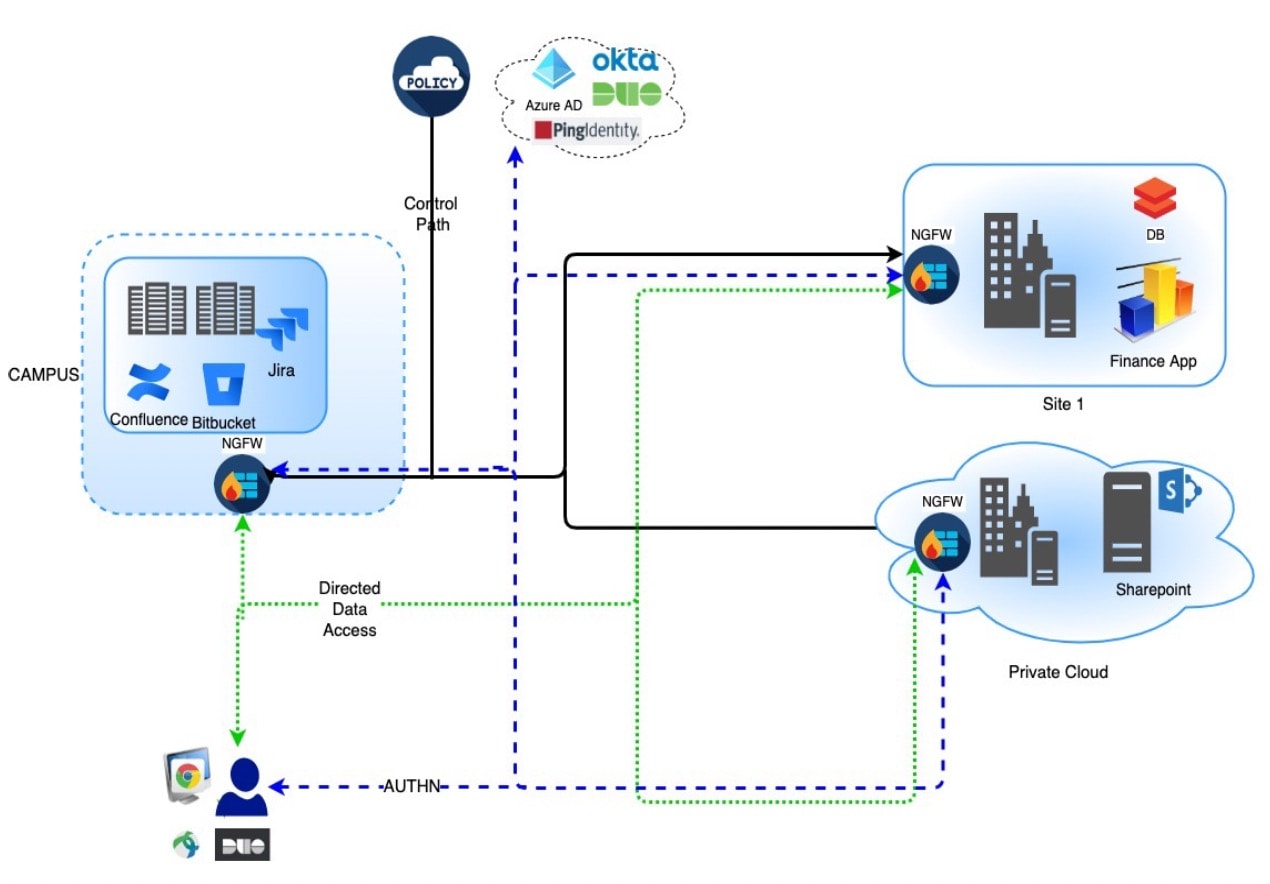
The Zero Trust Access feature is based on Zero Trust Network Access (ZTNA) principles. ZTNA is a zero trust security model that eliminates implicit trust. The model grants the least privilege access after verifying the user, the context of the request, and after analyzing the risk if access is granted.
Zero Trust Access allows you to authenticate and authorize access to protected web based resources and applications from inside (on-premise) or outside (remote) the network using an external SAML Identity Provider (IdP) policy.
The features are:
-
Supports multiple SAML based identity providers such as Duo, Azure AD, Okta, and other identity providers.
-
Client applications such as Cisco Secure Client are not required on the endpoint (client devices) for secure access.
-
Access and authentication is through the browser.
-
Supports only web applications (HTTPS).
-
Client device posture is supported through agents such as Duo Health, using which the posture of the device can be evaluated against a policy in Duo, and access can be provided based on the same. The same functionality can be performed in conjunction with third-party identity providers that support posture evaluation with their agents such as Okta or PingID.
-
Supports HTTP-Redirect SAML binding.
-
Supports Application Groups that make it easier to enable zero trust protection on a set of applications.
-
Leverages threat defense intrusion and malware protection on zero trust application traffic.
You can use the Secure Firewall Management Center web interface to create a Zero Trust Application Policy that allows you to define private applications and assign threat policies to them. The policy is application specific where the administrator decides the inspection levels based on the threat perception for that application.






 Feedback
Feedback