Overview of SD-WAN Capabilities
Software-Defined WAN (SD-WAN) solutions replace traditional WAN routers and are agnostic to WAN transport technologies. SD-WAN provides dynamic, policy-based, application path selection across multiple WAN connections and supports service chaining for additional services such as WAN optimization and firewalls.
As organizations expand their operations across multiple branch locations, ensuring secure and streamlined connectivity becomes paramount. Deploying a secure branch network infrastructure involves complex configurations, which can be time-consuming and prone to configuration errors if not handled properly. However, organizations can overcome these challenges by leveraging the Cisco Secure Firewall Management Center (management center) and the Cisco Secure Firewall Threat Defense (threat defense) devices for a simplified and secure branch deployment.
In this guide, we explore the concept of simplifying secure branch deployment using a robust firewall solution. By integrating a secure firewall as a foundational component of the branch network architecture, organizations can establish a strong security baseline while simplifying the deployment process. This approach enables organizations to enforce unified security policies, optimize traffic routing, and ensure resilient connectivity.
Some of the SD-WAN capabilities supported on the Cisco Secure Firewall are:
-
Simplified management:
-
SD-WAN Wizard
-
SASE: Umbrella auto tunnel deployment
-
Dynamic VTI (DVTI) hub spoke topology simplification
-
-
Application awareness:
-
Direct Internet Access (DIA) for public cloud and guest user
-
Policy based routing (PBR) using applications as a match criteria
-
Local tunnel ID support for Umbrella
-
-
Increased usable bandwidth:
-
ECMP support for load balancing across multiple ISPs and VTIs
-
Application-based load balancing using PBR
-
-
High availability with near zero network downtime:
-
Dual ISP configuration
-
Optimal path selection based on application-based interface monitoring.
-
-
Secure Elastic Connectivity:
-
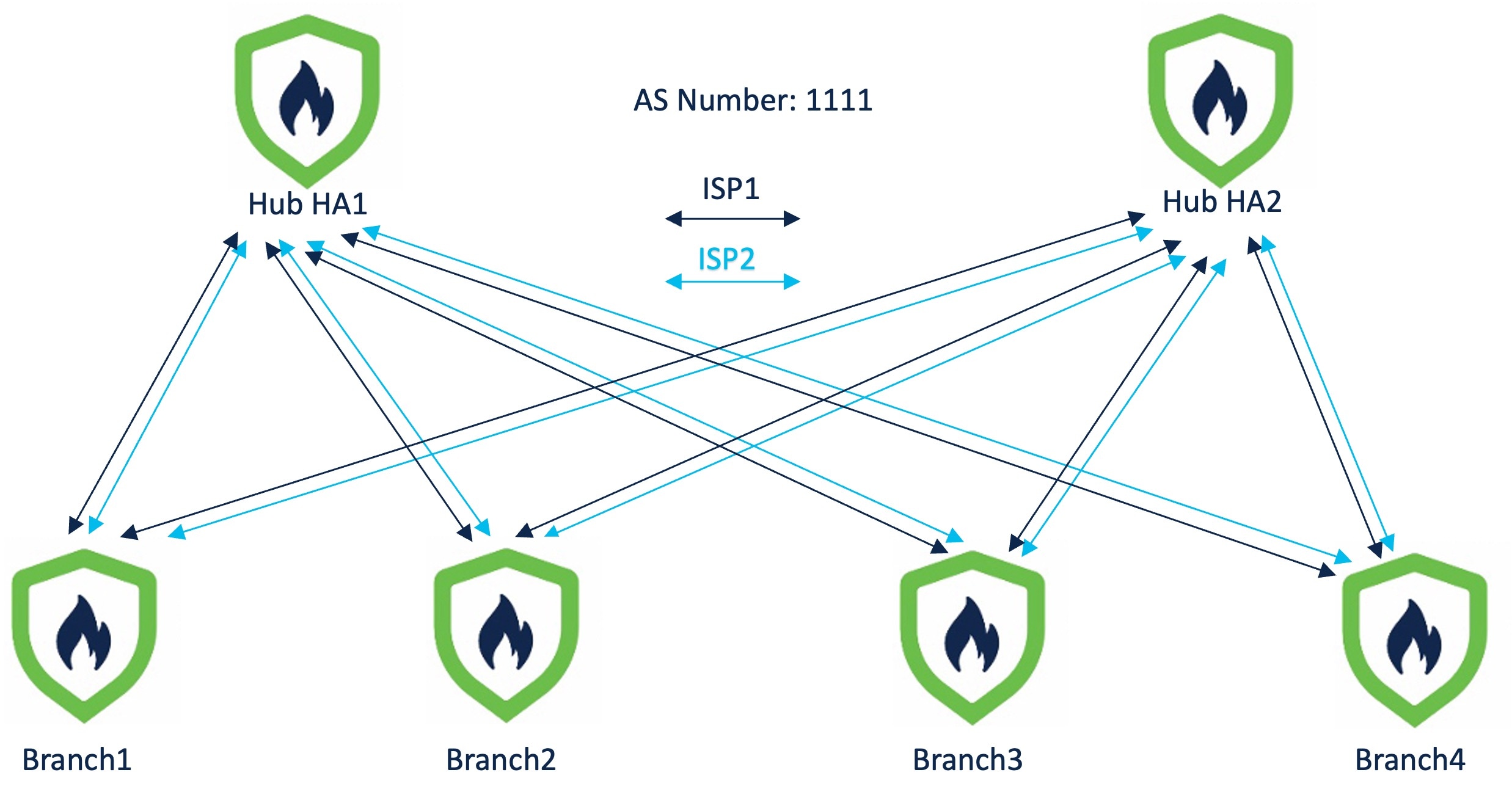
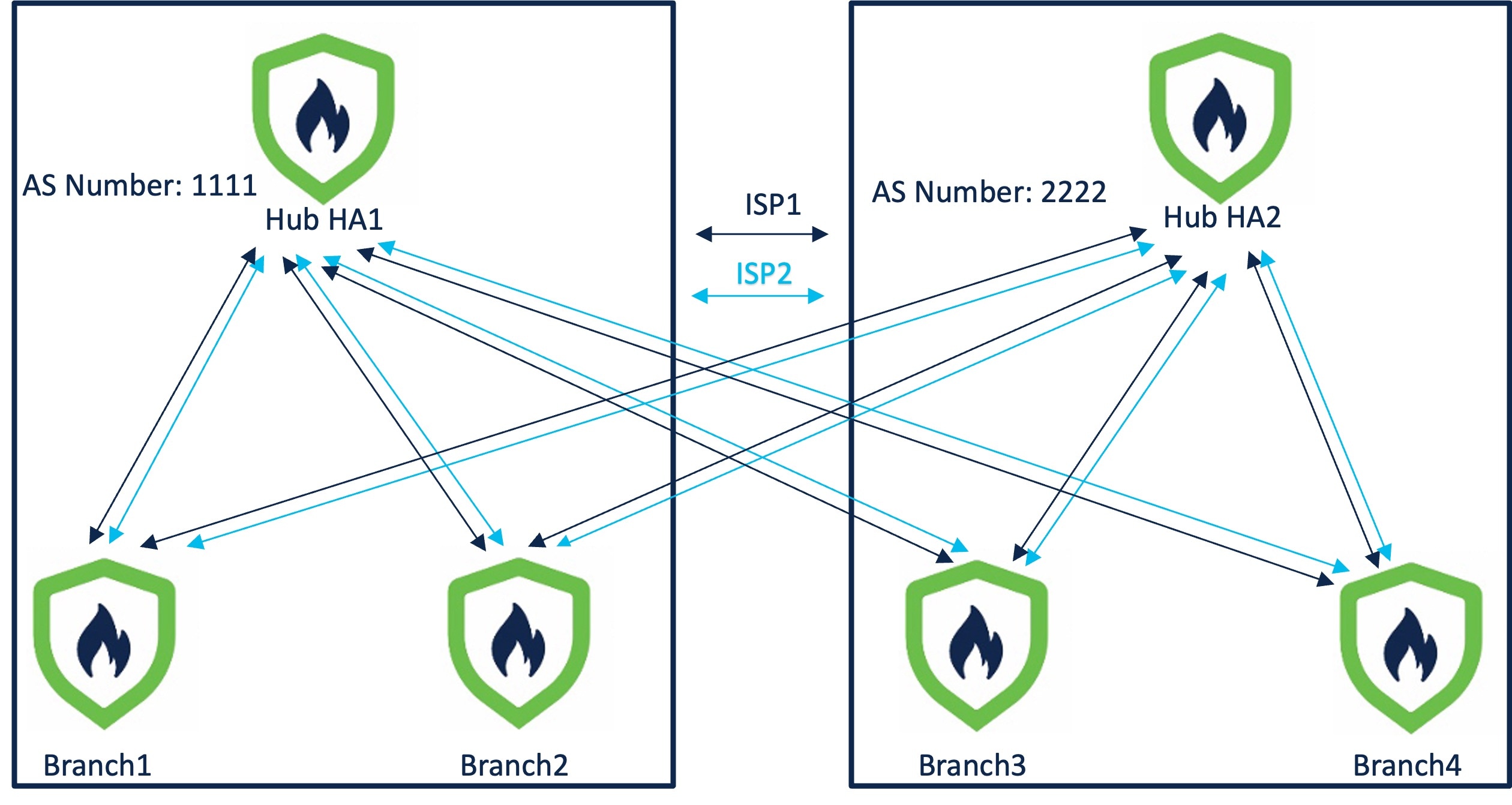
Route-based (VTI) VPN tunnels between headquarters (hub) and branches (spokes)
-
IPv4 and IPv6 BGP, IPv4 and IPv6 OSPF, and IPv4 EIGRP over VTI
-
DVTI hubs that support spokes with static or dynamic IP
-

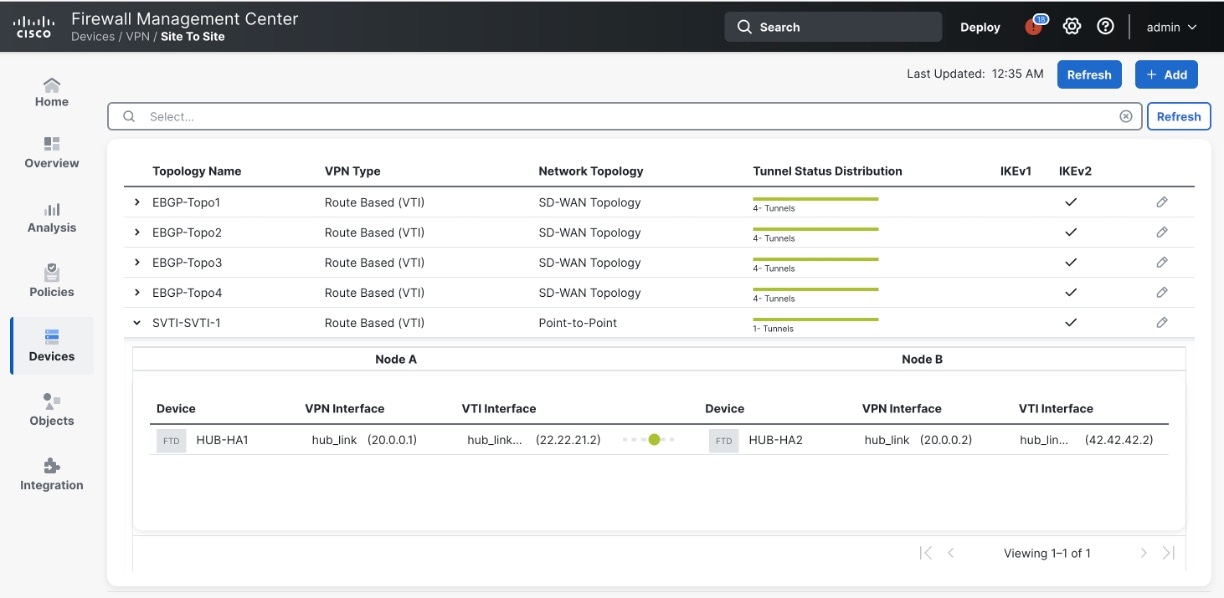

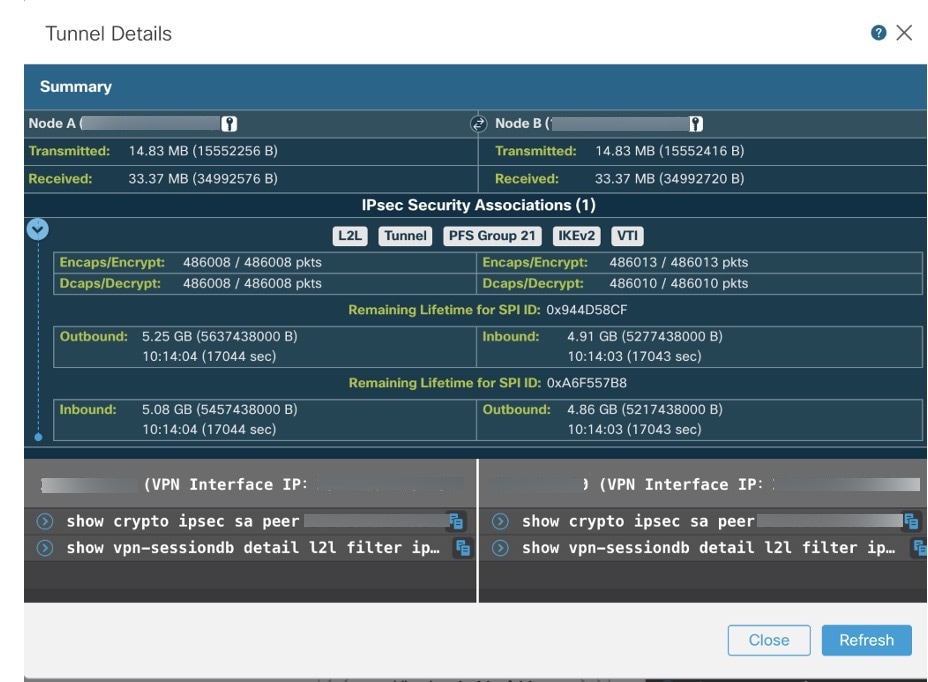
 ) icon. A pane with tunnel details and more actions appears.
) icon. A pane with tunnel details and more actions appears.

 Feedback
Feedback