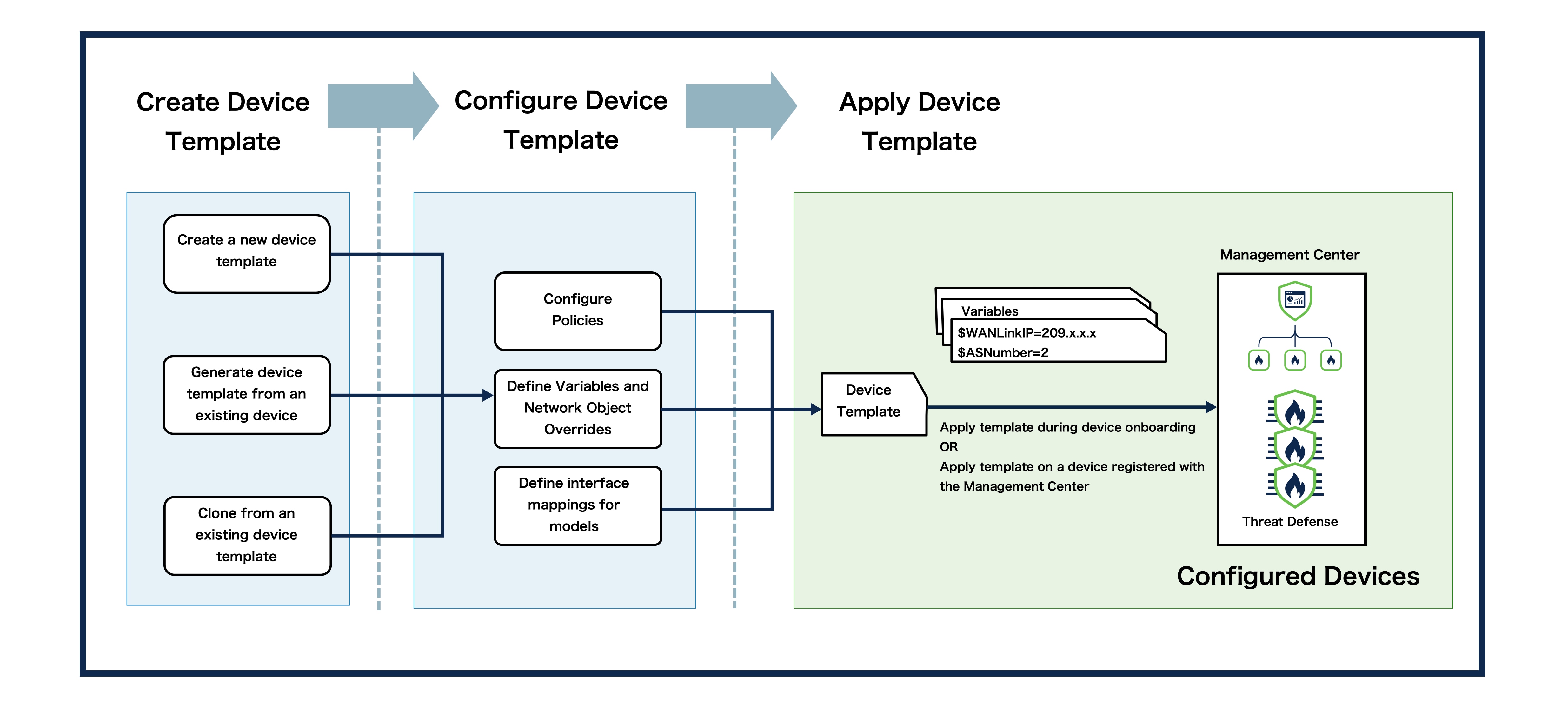
About Device Management using Device Templates
Device templates enable deployment of multiple branch devices with pre-provisioned initial device configurations. You can use device templates to perform bulk zero-touch provisioning of multiple devices, apply day 2 configuration changes to multiple devices with different interface configurations, and clone configuration parameters from existing devices. You can also register more than one device at a time with the Firewall Management Center using serial numbers.
When you register a device using basic initial configuration, you can apply limited configurations such as the access control policy and licenses. You must then configure other device settings such as interfaces, routing, and site-to-site VPN configurations individually after device registration. Device templates let you pre-configure these settings and more so you can apply them at the time of registration. Values that need to be unique per device, such as IP addresses, can be defined using variables and network object overrides that you define at registration.
You can also configure site-to-site VPN connections in a device template. These configurations define the site-to-site VPN topologies that a device should be a part of. The VPN configurations along with the other device template policies and configurations enable easy deployment of the branch device to your network. Device templates support the configuration of a device only as a spoke. A device can be part of multiple hub and spoke site-to-site VPN topologies.
After the configured device template is applied to a device, the variables are resolved, the protected network overrides are configured, and the device is added as a spoke in the specified VPN topology.
Methods to Register Devices using Templates
You can use device templates with the following methods to register the device on the Firewall Management Center and set up day 0 configuration:
-
Registration Key - You can register a single device by specifying the registration key and defining variables in the Firewall Management Center.
-
Serial Number - You can use zero-touch provisioning to register one or more devices by serial number. For serial number registration, define all variables and overrides in a CSV file that you upload.
Variables and Network Object Overrides
You can parameterize template configurations using variables and network object overrides.
A variable is an object type that is supported for template configurations. A variable in a template defines specific configuration values for a device. You can define values for these variables during device registration and during application of the template on the device. You can see the variable icon (x) for the fields that use a variable. The variables are displayed with a $ prefix to distinguish these values from the other values.
For information on supported variable types and creating variables, see Supported Variables and Add a Variable.
Network object overrides are similar to variables. But, these are used to provide override values for a network object. You can declare a list of network objects in the template and create network object overrides for these objects. You can then provide values for these network object overrides during the application of the template on the device. For example, if you define a host network object in a template, you can add a network object override before the application of the template on the device and then provide a relevant value during the application of the template on the device.
For more information on supported network objects and adding a network object override, see Supported Network Object Overrides and Add a Network Object Override.
Model Mapping
As interface configurations vary for different device models, the interface configurations in the template have to be copied to the target interfaces on the device. Model mapping enables you to define mapping of interfaces defined in the template to the interfaces of the required Firewall Threat Defense model. During application of the template on the device, the variables in the interface configurations are replaced with the values that you provide and copied to the mapped interfaces on the device. Note that you have to create the model mappings in the template before initiating application of the template on the device. For more information on setting up model mapping, see Add Model Mapping.
Templates and High Availablity
You can apply device templates on Firewall Threat Defense high-availability devices after device registration. High-availability-specific configurations are not supported in device templates. Any high-availability configurations and monitored interfaces that are already part of the target high-availability device pair configurations are not modified. You cannot map any template interfaces to failover interfaces.
You can generate a device template from a high-availability device pair. Template operations such as application of the template on a device, template generation, importing, and exporting of a template, can be performed only on the active unit. You cannot perform these operations on the standby unit.
Templates and Domains
Device templates can exist in any domain. If you are in the child domain, you have read-only access to the templates above you in the domain hierarchy. You can apply a template to a device from its domain or its parent domains. You can generate a template from a device and apply that template to a device in any domain in the domain hierarchy.
A domain hierarchy sample is given below along with a table displaying the supported device template application and generation scenarios.
Consider the following scenario:
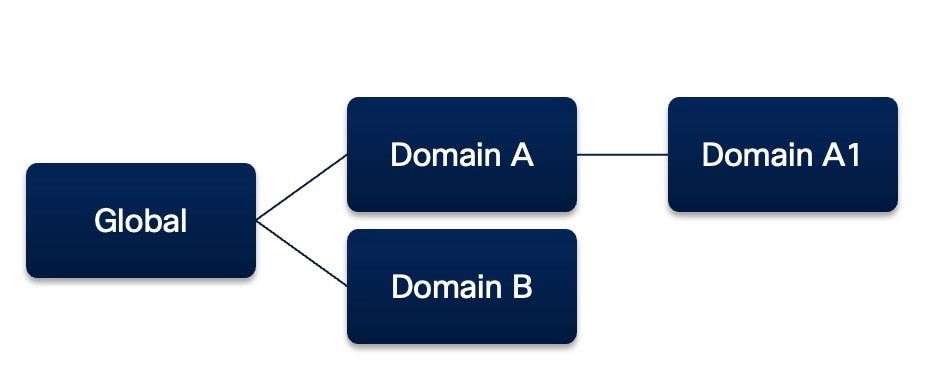
-
Domain A and B are child domains of the Global domain.
-
Domain A1 is the child domain of Domain A.
| Template Domain | Device Domain | Device Template Application/Generation Supported |
|---|---|---|
| Global | A1 | Yes |
| Global | B | Yes |
| A | A1 | Yes |
| A | B | No |
| B | A1 | No |
| B | B | Yes |
| A1 | A1 | Yes |
| A1 | B | No |
Domains and VPN Connections
-
You can define a template in a global or child/leaf domain. However, you can define a VPN topology only in a leaf domain.
-
You can configure VPN connections in a template for all domains. During template application, VPN connections are applied to the device only if the device is in the same domain as the VPN topology.
A domain hierarchy sample is given below along with a table displaying the supported device template application and generation scenarios.
Consider the following scenario:
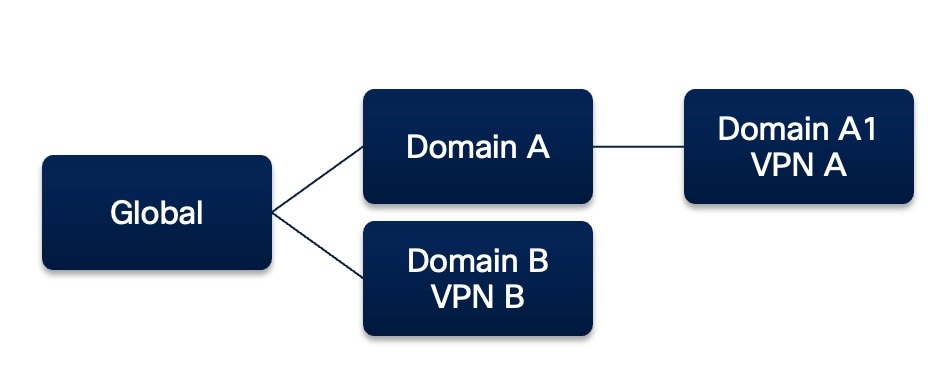
-
Domain A and B are child domains of the Global domain.
-
Domain A1 is the child domain of Domain A.
-
VPN A is part of Domain A1.
-
VPN B is part of Domain B.
| Template Domain |
VPN Topology in the Template |
Device Domain | Device Template Application/Generation Supported |
|---|---|---|---|
| Global |
VPN A VPN B |
A1 | No |
| Global |
VPN B |
B | Yes |
| A |
VPN A |
A1 | Yes |
| B |
VPN B |
A1 | No |
| B |
VPN B |
B | Yes |
| A1 |
VPN A |
A1 | Yes |
Validation of Template Configuration Before and After Application of Template on Device
Validation of template configuration is done before and after application of the template on the device.
The following validation checks are performed at the start of the task to apply the template on the device:
-
Ensure that the target device model and version are supported.
-
Cluster and container checks -The device must not be part of a cluster or multi-instance.
-
Model mapping validation - Model mapping for the target device model exists and is valid.
-
Sanity check of template parameter values. For example, two variables used as IP addresses of interfaces must not have the same value.
The following validation checks are performed at the end of the task to apply the template on the device to ensure that the applied configurations are valid:
-
Interface configuration validation. For example, variables used for the IP address fields of two or more interfaces must not have the same IP address values.
-
Routing policy validation. For example, the IPv4 address in BGP neighbor configurations must not overlap with the IP address of any interface.
If the validation checks that are done at the end of the task to apply the template on the device fail, any applied configurations are rolled back and the device is restored to it’s original state.







 Feedback
Feedback