- Device Manager Help
- Configuring Cisco DCNM-SAN Server
- Configuring Authentication in Cisco DCNM-SAN
- Configuring Cisco DCNM-SAN Client
- Device Manager
- Configuring Performance Manager
- Configuring High Availability
- Configuring Trunking
- Configuring PortChannels
- Configuring N Port Virtualization
- Configuring Interfaces
- Configuration of Fibre Channel Interfaces
- Using the CFS Infrastructure
- Configuring SNMP
- Configuring Domain Parameters
- Configuring and Managing Zones
- Configuring FCoE
- Configuring Dense Wavelength Division Multiplexing
- Configuring and Managing VSANs
- Discovering SCSI Targets
- Configuring SAN Device Virtualization
- Configuring Fibre Channel Routing Services and Protocols
- Managing FLOGI, Name Server, FDMI, and RSCN Databases
- Configuring FICON
- Creating Dynamic VSANs
- Distributing Device Alias Services
- Configuring Advanced Fabric Features
- Configuring Users and Common Role
- Configuring Security Features on an External AAA Server
- Configuring Certificate Authorities and Digital Certificates
- Configuring FC-SP and DHCHAP
- Configuring Cisco TrustSec Fibre Channel Link Encryption
- Configuring FIPS
- Configuring IPv4 and IPv6 Access Control Lists
- Configuring IPsec Network Security
- Configuring Port Security
- Configuring Fabric Binding
- Configuring FCIP
- Configuring the SAN Extension Tuner
- Configuring iSCSI
- Configuring IP Services
- Configuring IP Storage
- Configuring IPv4 for Gigabit Ethernet Interfaces
- Configuring IPv6 for Gigabit Ethernet Interfaces
- Configuring SCSI Flow Services
- Configuring SCSI Flow Statistics
- Configuring Fibre Channel Write Acceleration
- Monitoring the Network
- Monitoring Performance
- Configuring Call Home
- Configuring System Message Logging
- Scheduling Maintenance Jobs
- Configuring RMON
- Configuring Fabric Configuration Server
- Monitoring Network Traffic Using SPAN
- Monitoring System Processes and Logs
- Configuring QoS
- Configuring Port Tracking
- Configuring FlexAttach Virtual pWWN
- Configuring Interface Buffers
- Verifying Ethernet Interfaces
- Information About Fabric Authentication
- DHCHAP
- DHCHAP Compatibility with Existing Cisco MDS Features
- About Enabling DHCHAP
- About DHCHAP Authentication Modes
- About the DHCHAP Hash Algorithm
- About the DHCHAP Group Settings
- About the DHCHAP Password
- About Password Configuration for Remote Devices
- About the DHCHAP Timeout Value
- Enabling FC-SP on ISLs
- Default Settings
- Configuring DHCAP
- Verifying FC-SP and DHCHAP Configuration
- Configuration Example for DHCHAP
Information About Fabric Authentication
Fibre Channel Security Protocol (FC-SP) capabilities provide switch-switch and host-switch authentication to overcome security challenges for enterprise-wide fabrics. Diffie-Hellman Challenge Handshake Authentication Protocol (DHCHAP) is an FC-SP protocol that provides authentication between Cisco MDS 9000 Family switches and other devices. DHCHAP consists of the CHAP protocol combined with the Diffie-Hellman exchange.
To authenticate through VFC ports, FC-SP peers use the port VSAN for communication. Hence, the port VSAN needs to be the same and active on both the peers to send and receive authentication messages.
All switches in the Cisco MDS 9000 Family enable fabric-wide authentication from one switch to another switch, or from a switch to a host. These switch and host authentications are performed locally or remotely in each fabric. As storage islands are consolidated and migrated to enterprise-wide fabrics new security challenges arise. The approach of securing storage islands cannot always be guaranteed in enterprise-wide fabrics.
For example, in a campus environment with geographically distributed switches someone could maliciously interconnect incompatible switches or you could accidentally do so, resulting in Inter-Switch Link (ISL) isolation and link disruption. This need for physical security is addressed by switches in the Cisco MDS 9000 Family (see Figure 31-1).
Figure 31-1 Switch and Host Authentication
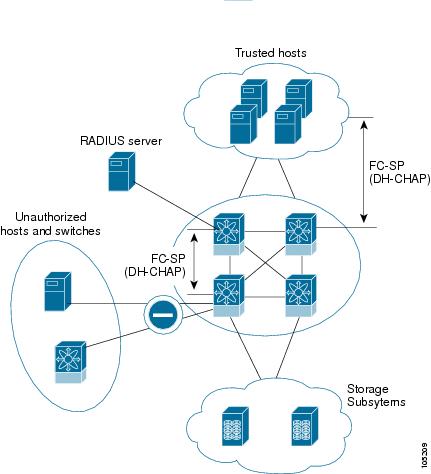

Note Fibre Channel (FC) host bus adapters (HBAs) with appropriate firmware and drivers are required for host-switch authentication.
DHCHAP
DHCHAP is an authentication protocol that authenticates the devices connecting to a switch. Fibre Channel authentication allows only trusted devices to be added to a fabric, which prevents unauthorized devices from accessing the switch.

Note The terms FC-SP and DHCHAP are used interchangeably in this chapter.
DHCHAP is a mandatory password-based, key-exchange authentication protocol that supports both switch-to-switch and host-to-switch authentication. DHCHAP negotiates hash algorithms and DH groups before performing authentication. It supports MD5 and SHA-1 algorithm-based authentication.
Configuring the DHCHAP feature requires the ENTERPRISE_PKG license (see the Cisco MDS 9000 Family NX-OS Licensing Guide).
DHCHAP Compatibility with Existing Cisco MDS Features
This section identifies the impact of configuring the DHCHAP feature along with existing Cisco MDS features:
- PortChannel interfaces—If DHCHAP is enabled for ports belonging to a PortChannel, DHCHAP authentication is performed at the physical interface level, not at the PortChannel level.
- FCIP interfaces—The DHCHAP protocol works with the FCIP interface just as it would with a physical interface.
- Port security or fabric binding—Fabric binding policies are enforced based on identities authenticated by DHCHAP.
- VSANs—DHCHAP authentication is not done on a per-VSAN basis.
- High availability—DHCHAP authentication works transparently with existing HA features.
About Enabling DHCHAP
By default, the DHCHAP feature is disabled in all switches in the Cisco MDS 9000 Family.
You must explicitly enable the DHCHAP feature to access the configuration and verification commands for fabric authentication. When you disable this feature, all related configurations are automatically discarded.
About DHCHAP Authentication Modes
The DHCHAP authentication status for each interface depends on the configured DHCHAP port mode.
When the DHCHAP feature is enabled in a switch, each Fibre Channel interface or FCIP interface may be configured to be in one of four DHCHAP port modes:
- On—During switch initialization, if the connecting device supports DHCHAP authentication, the software performs the authentication sequence. If the connecting device does not support DHCHAP authentication, the software moves the link to an isolated state.
- Auto-Active—During switch initialization, if the connecting device supports DHCHAP authentication, the software performs the authentication sequence. If the connecting device does not support DHCHAP authentication, the software continues with the rest of the initialization sequence.
- Auto-Passive (default)—The switch does not initiate DHCHAP authentication, but participates in DHCHAP authentication if the connecting device initiates DHCHAP authentication.
- Off—The switch does not support DHCHAP authentication. Authentication messages sent to such ports return error messages to the initiating switch.

Note Whenever DHCHAP port mode is changed to a mode other than the Off mode, reauthentication is performed.
Table 31-1 identifies the switch-to-switch authentication behavior between two Cisco MDS switches in various modes.
About the DHCHAP Hash Algorithm
Cisco MDS switches support a default hash algorithm priority list of MD5 followed by SHA-1 for DHCHAP authentication.

Tip If you change the hash algorithm configuration, then change it globally for all switches in the fabric.

About the DHCHAP Group Settings
All switches in the Cisco MDS Family support all DHCHAP groups specified in the standard: 0 (null DH group, which does not perform the Diffie-Hellman exchange), 1, 2, 3, or 4.

Tip If you change the DH group configuration, change it globally for all switches in the fabric.
About the DHCHAP Password
DHCHAP authentication in each direction requires a shared secret password between the connected devices. To do this, you can use one of three approaches to manage passwords for all switches in the fabric that participate in DHCHAP.
- Approach 1—Use the same password for all switches in the fabric. This is the simplest approach. When you add a new switch, you use the same password to authenticate that switch in this fabric. It is also the most vulnerable approach if someone from the outside maliciously attempts to access any one switch in the fabric.
- Approach 2—Use a different password for each switch and maintain that password list in each switch in the fabric. When you add a new switch, you create a new password list and update all switches with the new list. Accessing one switch yields the password list for all switches in that fabric.
- Approach 3—Use different passwords for different switches in the fabric. When you add a new switch, multiple new passwords corresponding to each switch in the fabric must be generated and configured in each switch. Even if one switch is compromised, the password of other switches are still protected. This approach requires considerable password maintenance by the user.

Note All passwords are restricted to 64 alphanumeric characters and can be changed, but not deleted.

Tip We recommend using RADIUS or TACACS+ for fabrics with more than five switches. If you need to use a local password database, you can continue to do so using Approach 3 and using the Cisco MDS 9000 Family DCNM-SAN to manage the password database.
About Password Configuration for Remote Devices
You can configure passwords in the local authentication database for other devices in a fabric. The other devices are identified by their device name, which is also known as the switch WWN or device WWN. The password is restricted to 64 characters and can be specified in clear text (0) or in encrypted text (7).

Note The switch WWN identifies the physical switch. This WWN is used to authenticate the switch and is different from the VSAN node WWN.
About the DHCHAP Timeout Value
During the DHCHAP protocol exchange, if the MDS switch does not receive the expected DHCHAP message within a specified time interval, authentication failure is assumed. The time ranges from 20 (no authentication is performed) to 1000 seconds. The default is 30 seconds.
When changing the timeout value, consider the following factors:
The same value must also be configured on all switches in the fabric.
Enabling FC-SP on ISLs
There is an ISL pop-up menu in DCNM-SAN called Enable FC-SP that enables FC-SP on switches at either end of the ISL. You are prompted for an FC-SP generic password, then asked to set FC-SP interface mode to ON for affected ports. Right-click an ISL and click Enable FC-SP to access this feature.

Note FC-SP DHCHAP mode requires port-flap on both end of the ISL.
Default Settings
Table 31-2 lists the default settings for all fabric security features in any switch.
Configuring DHCAP
To configure DHCHAP authentication using the local password database, follow these steps:
Step 2 Identify and configure the DHCHAP authentication modes.
Step 3 Configure the hash algorithm and DH group.
Step 4 Configure the DHCHAP password for the local switch and other switches in the fabric.
Step 5 Configure the DHCHAP timeout value for reauthentication.
Step 6 Verify the DHCHAP configuration.
Enabling DHCHAP
To enable DHCHAP for a Cisco MDS switch, follow these steps:
To enable DHCHAP for a Cisco MDS switch , follow these steps:
Step 1 Expand Switches, expand Security and then select FC-SP.
The Control tab is the default. You see the FC-SP enable state for all switches in the fabric.
Step 2 Set the Command drop-down menu to enable for all switches that you want to enable FC-SP on.
Step 3 Click the Apply Changes icon to enable FC-SP and DHCHAP on the selected switches.
Configuring the DHCHAP Mode
To configure the DHCHAP mode for a particular interface, follow these steps:
To configure the DHCHAP mode for a particular interface, follow these steps:
Step 1 Expand Switches, expand Interfaces, and then select FC Physical.
You see the interface configuration in the Information pane.
Step 3 Set the Mode drop-down menu to the DHCHAP authentication mode you want to configure for that interface.
Step 4 Click the Apply Changes icon to save these DHCHAP port mode settings.
Configuring the DHCHAP Hash Algorithm
To configure the hash algorithm, follow these steps:
To configure the hash algorithm, follow these steps:
Step 1 Choose Switches > Security, and then select FC-SP.
Step 2 Click the General/Password tab.
You see the DHCHAP general settings mode for each switch.
Step 3 Change the DHCHAP HashList for each switch in the fabric.
Step 4 Click the Apply Changes icon to save the updated hash algorithm priority list.
Configuring the DHCHAP Group Settings
To change the DH group settings, follow these steps:
Prioritizes the use of DH group 2, 3, and 4 in the configured order. |
||
Reverts to the DHCHAP factory default order of 0, 4, 1, 2, and 3. |
To change the DH group settings, follow these steps:
Step 1 Expand Switches > Security, and then select FC-SP.
Step 2 Click the General/Password tab.
Step 3 Change the DHCHAP GroupList for each switch in the fabric.
Step 4 Click the Apply Changes icon to save the updated hash algorithm priority list.
Configuring DHCHAP Passwords for the Local Switch
To configure the DHCHAP password for the local switch, follow these steps:
To configure the DHCHAP password for the local switch, follow these steps:
Step 1 Expand Switches > Security, and then select FC-SP.
You see the FC-SP configuration in the Information pane.
Step 2 Click the Local Passwords tab.
Step 3 Click the Create Row icon to create a new local password.
You see the Create Local Passwords dialog box.
Step 4 (Optional) Check the switches that you want to configure the same local password on.
Step 5 Select the switch WNN and fill in the Password field.
Step 6 Click Create to save the updated password.
Configuring DHCHAP Passwords for Remote Devices
To locally configure the remote DHCHAP password for another switch in the fabric, follow these steps:
To locally configure the remote DHCHAP password for another switch in the fabric, follow these steps:
Step 1 Right-click an ISL and select Enable FC-SP from the drop-down list (see Figure 31-2).
You see the Enable FC-SP dialog box.
Figure 31-3 Enable FC-SP Dialog Box
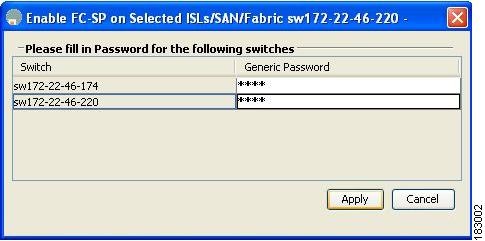
Step 2 Click Apply to save the updated password.
Configuring the DHCHAP Timeout Value
To configure the DHCHAP timeout value, follow these steps:
To configure the DHCHAP timeout value, follow these steps:
Step 1 Expand Switches > Security, and then select FC-SP.
You see the FC-SP configuration in the Information pane.
Step 2 Click the General/Password tab.
You see the DHCHAP general settings mode for each switch.
Step 3 Change the DHCHAP timeout value for each switch in the fabric.
Step 4 Click the Apply Changes icon to save the updated information.
Configuring DHCHAP AAA Authentication
You can individually set authentication options. If authentication is not configured, local authentication is used by default.
To configure the AAA authentication refer to the Chapter29, “Configuring Security Features on an External AAA Server” Follow these steps:
Verifying FC-SP and DHCHAP Configuration
To display FC-SP and DHCHAP configuration information, perform one of the following tasks:
Displays the FC-SP WWN of the Device Connected through a Specified Interface. |
|
Displays Hash Algorithm and DHCHAP Groups Configured for the Local Switch. |
|
For detailed information about the fields in the output from these commands, refer to the Cisco DC-OS Command Reference .
This section includes the following topics:
Displaying Protocol Security Information
Use the show fcsp commands to display configurations for the local database (see Example 31-1 through 31-6 ).
Example 31-1 Displays DHCHAP Configurations in FC Interfaces
Example 31-2 Displays DHCHAP Statistics for an FC Interface
Example 31-3 Displays the FC-SP WWN of the Device Connected through a Specified Interface
Example 31-4 Displays Hash Algorithm and DHCHAP Groups Configured for the Local Switch
Example 31-5 Displays the DHCHAP Local Password Database
Example 31-6 Displays the ASCII Representation of the Device WWN

Tip Use the ASCII representation of the device WWN (identified in bold in Example 31-6) to configure the switch information on RADIUS and TACACS+ servers.
Configuration Example for DHCHAP
This section provides the steps to configure the example illustrated in Figure 31-4.
Figure 31-4 Sample DHCHAP Authentication
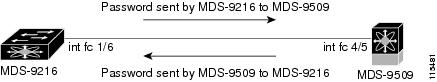
To configure the authentication setup shown in Figure 31-4, follow these steps:
Step 1 Obtain the device name of the MDS 9216 Switch in the fabric. The MDS 9216 Switch in the fabric is identified by the switch WWN.
Step 2 Explicitly enable DHCHAP in this switch.

Note When you disable DHCHAP, all related configurations are automatically discarded.
Step 3 Configure a clear text password for this switch. This password will be used by the connecting device.
Step 4 Configures a password for another switch in the fabric that is identified by the switch WWN device name.
Step 5 Enable the DHCHAP mode for the required Fibre Channel interface.

Note Whenever DHCHAP port mode is changed to a mode other than the Off mode, reauthentication is performed.
Step 6 Verify the protocol security information configured in this switch by displaying the DHCHAP local password database.
Step 7 Display the DHCHAP configuration in the Fibre Channel interface.
Step 8 Repeat these steps on the connecting MDS 9509 Switch.
You have now enabled and configured DHCHAP authentication for the sample setup in Figure 31-4.
 Feedback
Feedback